Ingest Signal Sciences WAF Data into Cloud SIEM
To ingest Signal Sciences data into Cloud SIEM:
- Configure an HTTP Logs and Metrics source on a collector. When you configure the source, do the following:
- Select the Forward to SIEM option in the source configuration UI. This will ensure all logs for this source are forwarded to Cloud SIEM.
- Make note of the Source Category. You'll supply it in a later step.
- After saving the source, click the Show URL link and make note of the HTTP source URL. You'll supply it in a later step.
- Configure Signal Sciences WAF to send log messages to the Sumo Logic platform:
- Go to the SigSci Site Tools > Integrations in the SigSci dashboard.
- Click Add for Generic Webhook.
- Paste the HTTP source URL from the previous step into the Webhook URL field and click Add. For more information on Generic Webhooks refer to the Generic Webhooks page in Fastly help.
- Configure a Sumo Logic Ingest Mapping in Cloud SIEM for the source category assigned to the source. The mapping tells Cloud SIEM the information it needs to select the right mapper to process messages that have been tagged with that source category.
- New UI. In the main Sumo Logic menu select Cloud SIEM, and then under Cloud SIEM Integrations select Ingest Mappings. You can also click the Go To... menu at the top of the screen and select Ingest Mappings. Classic UI.
In the top Cloud SIEM menu select Configuration, and then under Integrations select Sumo Logic. - On the Ingest Mappings tab, click + Add Ingest Mapping.
- On the Add Ingest Mapping popup:
- Source Category. Enter the category you assigned to the HTTP source you created earlier.
- Format. Enter JSON.
- Vendor. Enter SignalSciences.
- Product. Enter WAF.
- Event ID. Enter .*
- Click Create to save the mapping.
- New UI. In the main Sumo Logic menu select Cloud SIEM, and then under Cloud SIEM Integrations select Ingest Mappings. You can also click the Go To... menu at the top of the screen and select Ingest Mappings. Classic UI.
- To verify that your logs are successfully making it into Cloud SIEM:
- New UI. In the main Sumo Logic menu select Cloud SIEM, and then under Cloud SIEM Integrations select Log Mappings. You can also click the Go To... menu at the top of the screen and select Log Mappings.
Classic UI. In the top Cloud SIEM menu select Configuration, and then under Incoming Data select Log Mappings. - On the Log Mappings page search for "Signal Sciences" and check the Records columns.
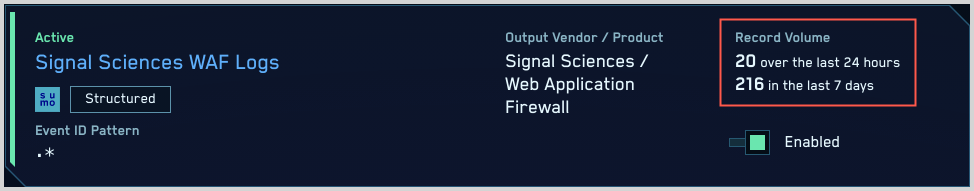
- For a more granular look at the incoming records, you can also search the Sumo Logic platform for Signal Sciences WAF security records:
_index=sec_record* and metadata_product = "Signal Sciences"
- New UI. In the main Sumo Logic menu select Cloud SIEM, and then under Cloud SIEM Integrations select Log Mappings. You can also click the Go To... menu at the top of the screen and select Log Mappings.