Import YARA Rules
This section has instructions for importing YARA rules from GitHub into Cloud SIEM.
YARA rules are an open source framework for identifying malware. Cloud SIEM runs YARA rules against files uploaded by the network sensor. When a file matches a YARA rule, Cloud SIEM creates a special record which results in a “file analysis” signal being created. Once you’ve imported rules, Cloud SIEM will sync with the repository no less than every hour.
To import YARA rules:
- Classic UI. In the top menu select Content > File Analysis.
New UI. In the main Sumo Logic menu, select Cloud SIEM > File Analysis. You can also click the Go To... menu at the top of the screen and select File Analysis. - Click Add Source.
- On the Add New Source popup, click Create in the GitHub tile.
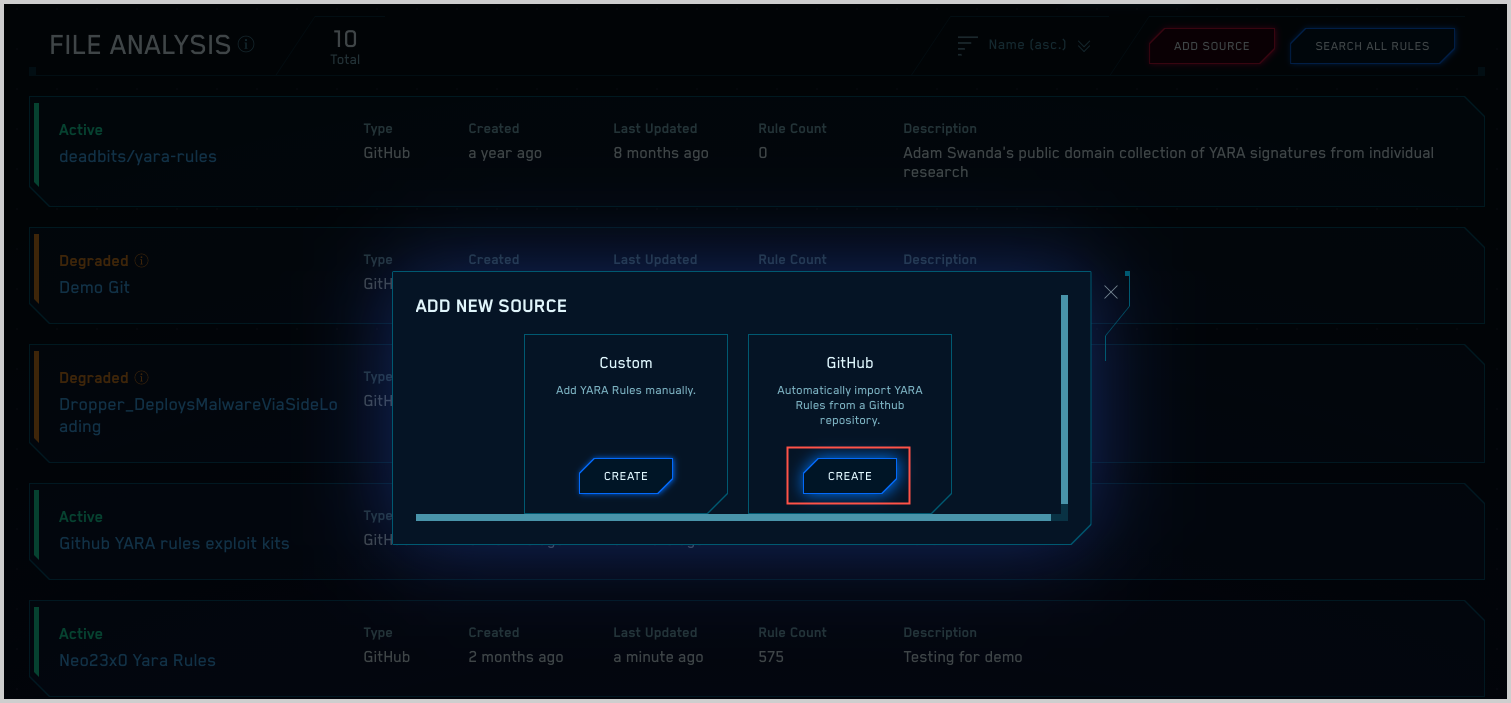
- The Add New Source popup updates.
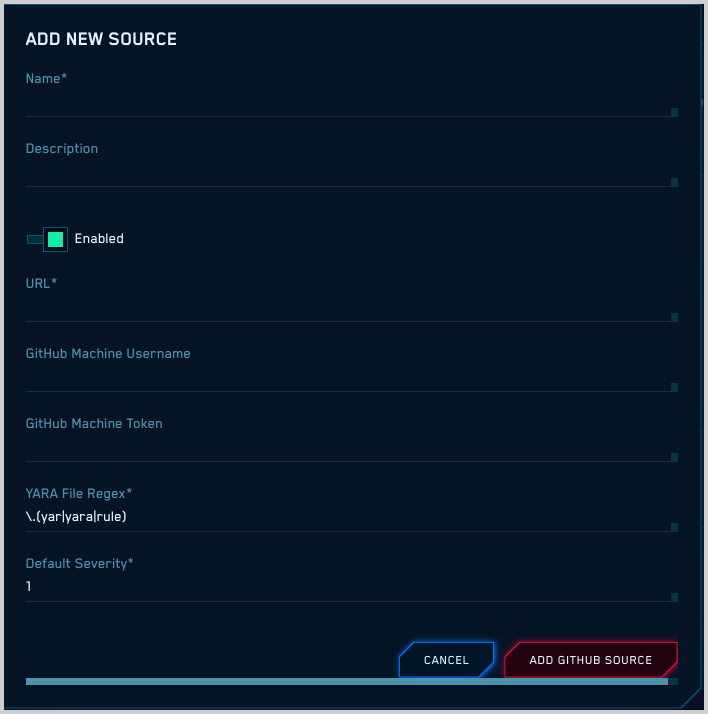
- Name. Enter a display name for the rule set to be imported.
- Description. Describe the rule set.
- Enabled. If you want Cloud SIEM to apply to rules upon import, leave the toggle set to Enabled. Otherwise, change it to Disabled.
- URL. Enter the URL of the GitHub repository that contains the rules.
- GitHub Machine Username. Enter a username if the repository is private.
- GitHub Machine Token. Enter a token if the repository is private.
- YARA file Regex. The regex in this field is matched to rule names in the repository. The default regex will match rule files whose file extension is
.yar,.yara, or.rule. - Default Severity. Enter the severity to be assigned when the signal is created.