CIS AWS Foundations Benchmark

The Center for Internet Security (CIS) is a 501(c)(3) organization dedicated to enhancing the cyber-security readiness and response among public and private sector entities. Utilizing its strong industry and government partnerships, CIS combats evolving cyber-security challenges on a global scale and helps organizations adopt key best practices to achieve immediate and effective defenses against cyber attacks.
The CIS AWS Foundations Benchmark is a set of security configuration best practices for AWS. These industry-accepted best practices go beyond the high-level security guidance already available, providing AWS users with clear, step-by-step implementation and assessment procedures.
The Sumo Logic for CIS AWS Foundations Benchmark App maps to Section 3 (Monitoring) of the CIS AWS Benchmarks Foundation recommendations. Using the pre-configured alerts and dashboards, customers are able to alert on and gain operational visibility into their AWS security posture.
Log types
The Sumo Logic App for CIS AWS Foundations Benchmark uses CloudTrail logs. For details on the specifics of which attributes are used, refer to Section 3 (Monitoring) of the CIS AWS Benchmarks Foundation.
Collecting logs for the CIS AWS Foundation Benchmark App
Configure Collector and Source
The CIS AWS Foundation Benchmark App ingests AWS CloudTrail data. To collect logs for the CIS AWS Foundation Benchmark App, perform the following steps:
- Add a Sumo Logic Hosted Collector to your Sumo Logic Org.
- Configure an AWS CloudTrail Source.
- Set your
_sourceCategory(example:aws/cloudtrail).
Installing the CIS AWS Foundations Benchmark App
Now that you have configured CIS AWS Foundation Benchmark, install the Sumo Logic App for CIS AWS Foundation Benchmark to take advantage of the preconfigured searches and dashboards to analyze your data.
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
For context regarding the CIS AWS Foundation Benchmark App, check out this blog where we describe the monitoring controls.
Viewing the CIS AWS Foundations Benchmark Dashboards
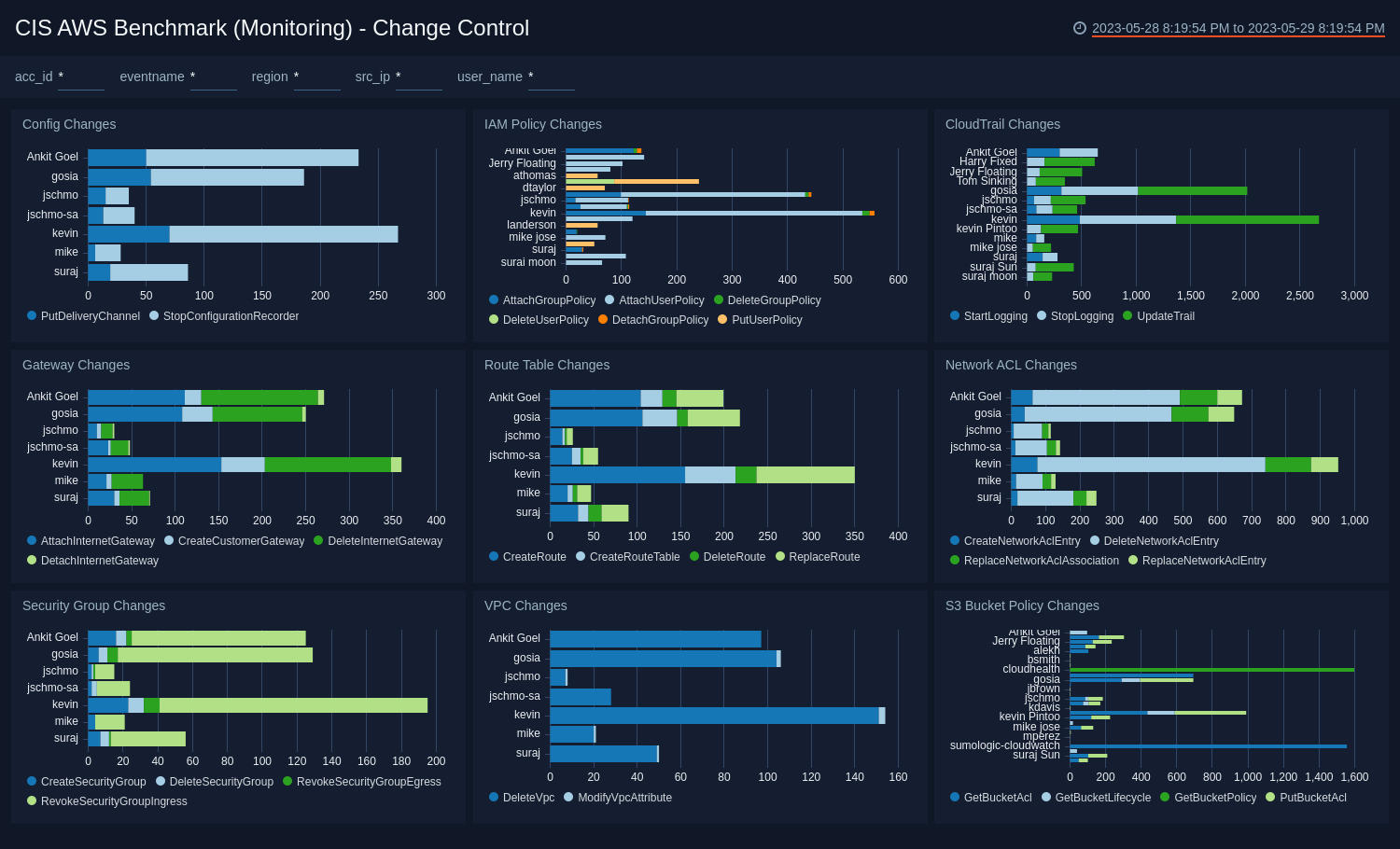
CIS AWS Foundations Benchmark App - Change Control
This Change Control Dashboard includes filters that you can use in Interactive Mode to further analyze your data.
Config Changes. Shows the count of configuration changes done by each user for the last 24 hours.
IAM Policy Changes. Shows the count of IAM policy changes done by each user for the last 24 hours.
CloudTrail Changes. Shows the count of CloudTrail changes done by each user for the last 24 hours.
Gateway Changes. Shows the count of Gateway changes done by each user for the last 24 hours.
Route Table Changes. Shows the count of Route Table changes done by each user for the last 24 hours.
Network ACL Changes. Shows the count of Network ACL changes done by each user for the last 24 hours.
Security Group Changes. Shows the count of Security Group changes done by each user for the last 24 hours.
VPC Changes. Shows the count of VPC changes done by each user for the last 24 hours.
S3 Bucket Policy Changes. Shows the count of S3 Bucket Policy changes done by each user for the last 24 hours.
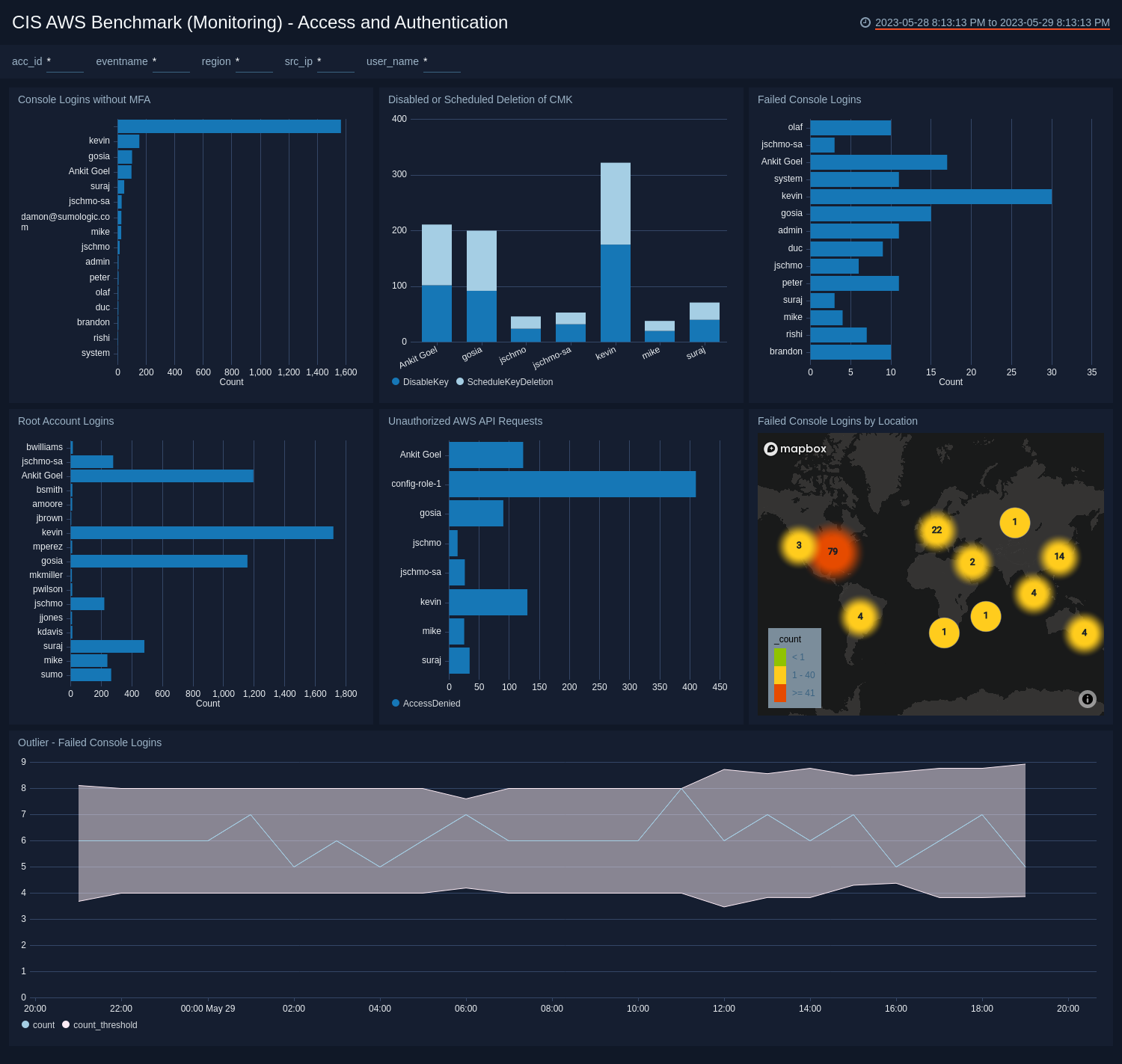
CIS AWS Foundations Benchmark App - Access and Authentication
This Access and Authentication Dashboard includes filters that you can use in Interactive Mode to further analyze your data.
Console Logins without MFA. All users must be using multi-factor authentication. This Panel show the count of logins that are not using MFA, by user, for the last 24 hours.
Disabled and Scheduled Deletion of CMK. Shows the count of CMKs that are disabled or scheduled to be deleted, by user, for the last 24 hours.
Failed Console Logins. Shows the count of failed logins by user, for the last 24 hours.
Root Account Logins. Shows the count of "root" account logins, by user, for the last 24 hours.
Unauthorized AWS API Requests. Shows the count of unauthorized API requests, by user, for the last 24 hours.
Failed Console Logins by Location. Shows the count of failed logins by location, for the last 24 hours.
Outlier - Failed Console Logins. Identifies failed console logins outside of 3 standard deviations, for the last 24 hours.