Azure Container Instances

Azure Container Instances is a fully managed serverless container service that enables you to deploy and manage containers in Azure without the need for virtual machines. It is ideal for event-driven applications, microservices, and batch processing workloads.
Log and metric types
For Azure Container Instances, you can collect the following logs and metrics:
- Audit Logs. The activity log contains subscription-level events that track operations for each Azure resource as seen from outside that resource. For more details, refer to the Azure Documentation.
- Resource Logs. Capture container creation, execution, and failure logs. Refer to the Microsoft Documentation to know about the schema for resource logs.
- Metrics. Metrics for Azure Container Instances are in the following namespace:
For more information on supported dimensions, refer to the Azure documentation.
Setup
- Set up application logs collection using fluent-bit sidecar container using the http output plugin and the tail input plugin. You must explicitly enable fluent-bit collection for each container group which you want to monitor.
- Metrics collection using our Azure Metrics Source.
Configure collector
Create a hosted collector if not already configured and tag the tenant_name field. You can get the tenant name using the instructions here. Make sure you create the required sources in this collector. 
Configure metrics collection
To set up the Azure Metrics source in Sumo Logic, refer to Azure Metrics Source.
Configure logs collection
Use existing resource group or create a new one for deploying Azure container instances.
- Create a hosted collector and tag the
tenant_namefield
- Configure an HTTP Source.
- Download and update the output_conf.yaml file with the following configurations:
- Inputs pipeline uses the tail input plugin. Update the path parameter value with the pattern specifying a specific log file or multiple ones through the use of common wildcards.
info
Multiple patterns separated by commas are also allowed.
- Outputs pipeline uses the http output plugin. Follow the below steps to update other outputs pipeline parameters:
- format. Data format by which you can send logs to Sumo Logic. By default, the format key will be assigned with json_lines.
- compress. Payload compression mechanism. By default, the compression is enabled and uses
gzip. - host. Update the host depending on your Sumo Logic Orgs deployment.
- tls. This field will be in on condition to enable the TLS support. By default, Sumo Logic only supports tls in on condition.
- tls.verify. This field will be in off condition to disable the certificate validation. By default, Sumo Logic only supports tls.verify in off condition.
- URI. Update the
[PrivateKey]with the path present in the HTTP source endpoint as configured in the Step 1. - header. Update the X-Sumo-Fields header and replace the following values to enrich the logs with additional metadata, which helps with panel queries.
resource_name. Name of the Azure container instances resource.resource_group. Name of the resource group where the Azure container instances resource is present. Ensure that you use the same resource group created in the prerequisite section.subscription_id. ID associated with a subscription where the Azure container instances resource is present.location. The region to which the Azure container instances resource name belongs to.
- Inputs pipeline uses the tail input plugin. Update the path parameter value with the pattern specifying a specific log file or multiple ones through the use of common wildcards.
- Create and push a custom fluentbit image using a Docker file and output_conf.yaml to any container repository.
- Download and update the logging-sidecar-deploy.yaml file with the following configurations:
- Update the
locationvalue with the region where the Azure container instances resource will be deployed. - Update the
namevalue with the name of the Azure container instances resource. Ensure that this value is same as theresource_namein theoutput_conf.yamlfile. - Update the
nginxcontainer with your own application image whose logs you want to collect. For example, in thelogging-sidecar-deploy.yamlfile we have used nginx application as an example whose log files are created in a shared volume (/var/log/nginx). - In the
fluentbitcontainer, replace the{custom-fluentbit-image-path}with the custom fluentbit image path that you created in the Step 2. - In the
imageRegistryCredentialsproperty, enter your image repository server, username, and password.
- Update the
- Deploy the logging-sidecar-deploy.yaml Azure template, refer to the Azure Documentation.
Activity logs (optional)
To collect activity logs, follow the instructions here. If you are already collecting activity logs for a subscription, you can skip this step.
Since this source includes logs from multiple regions, do not tag it with the location tag.
Installing the Azure Container Instances app
Now that you have set up data collection, install the Azure Container Instances Sumo Logic app to use the pre-configured dashboards that provide visibility into your environment for real-time analysis of azure resources.
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure App section of your respective app, complete the following field.
- Index. Specify value for _index if the collection is configured with custom partition. Learn more. Default value is set to
sumologic_default(default partition)
- Index. Specify value for _index if the collection is configured with custom partition. Learn more. Default value is set to
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
As part of the app installation process, the following fields will be created by default:
tenant_name. This field is tagged at the collector level. You can get the tenant name using the instructions here.location. The region to which the resource name belongs to.subscription_id. ID associated with a subscription where the resource is present.resource_group. The resource group name where the Azure resource is present.provider_name. Azure resource provider name (for example, Microsoft.Network).resource_type. Azure resource type (for example, storage accounts).resource_name. The name of the resource (for example, storage account name).service_type. Type of the service that can be accessed with a Azure resource.service_name. Services that can be accessed with an Azure resource (for example, in Azure Container Instances the service is Subscriptions).
Viewing the Azure Container Instances dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Many of the Next-Gen apps allow you to provide the Index at the installation time and a default value for this key (sumologic_default). Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the data partition queried by all panels. This restricts the query scope of all the dashboard queries to a specific data partition.
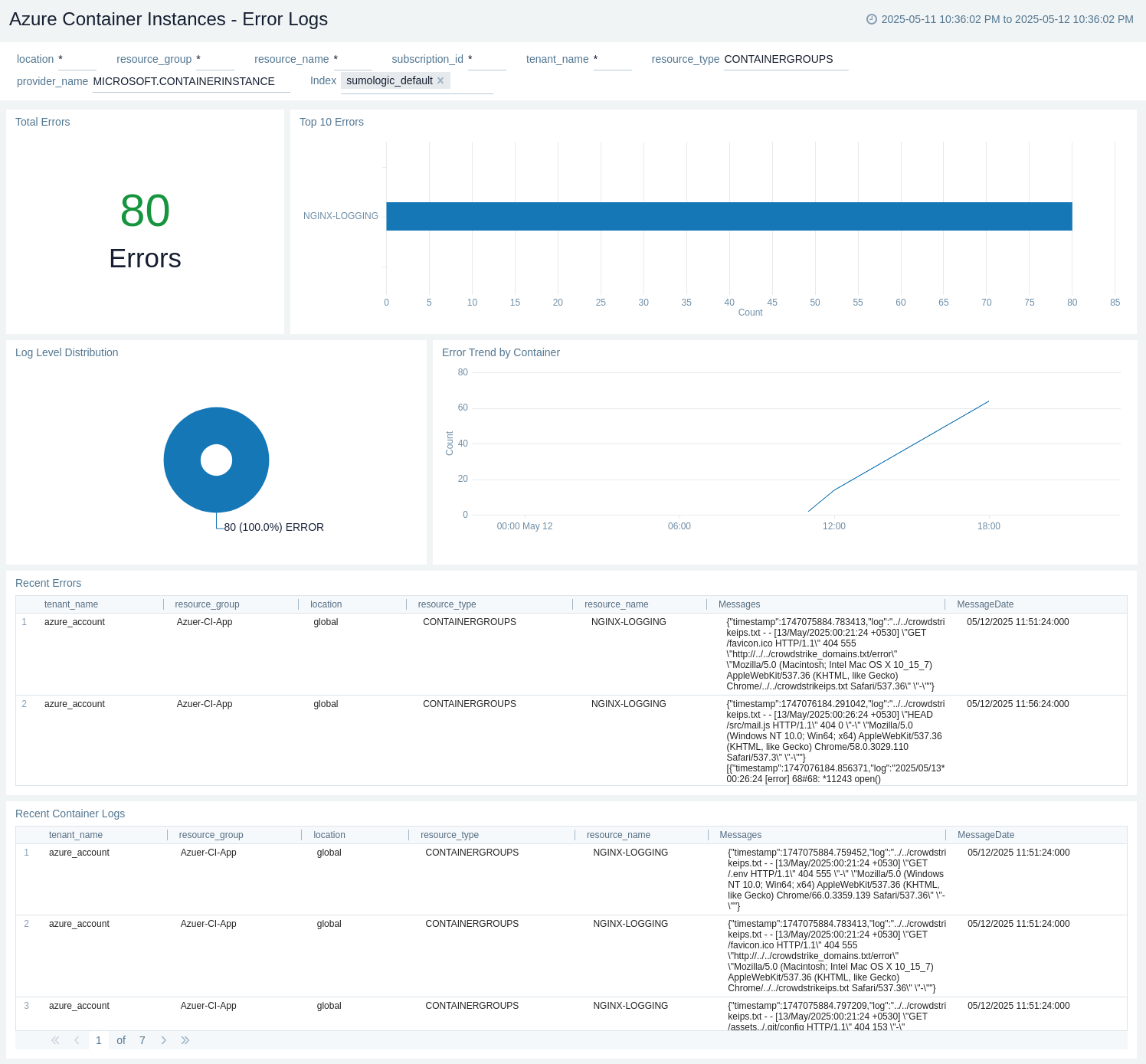
Error Logs
The Azure Container Instance - Error Logs dashboard provides detailed information on the container activity. This dashboard also provides comprehensive overview of Total Errors, Top 10 Errors bar chart, Log Level Error distribution, Error Trend by Container, and Recent Container Logs.
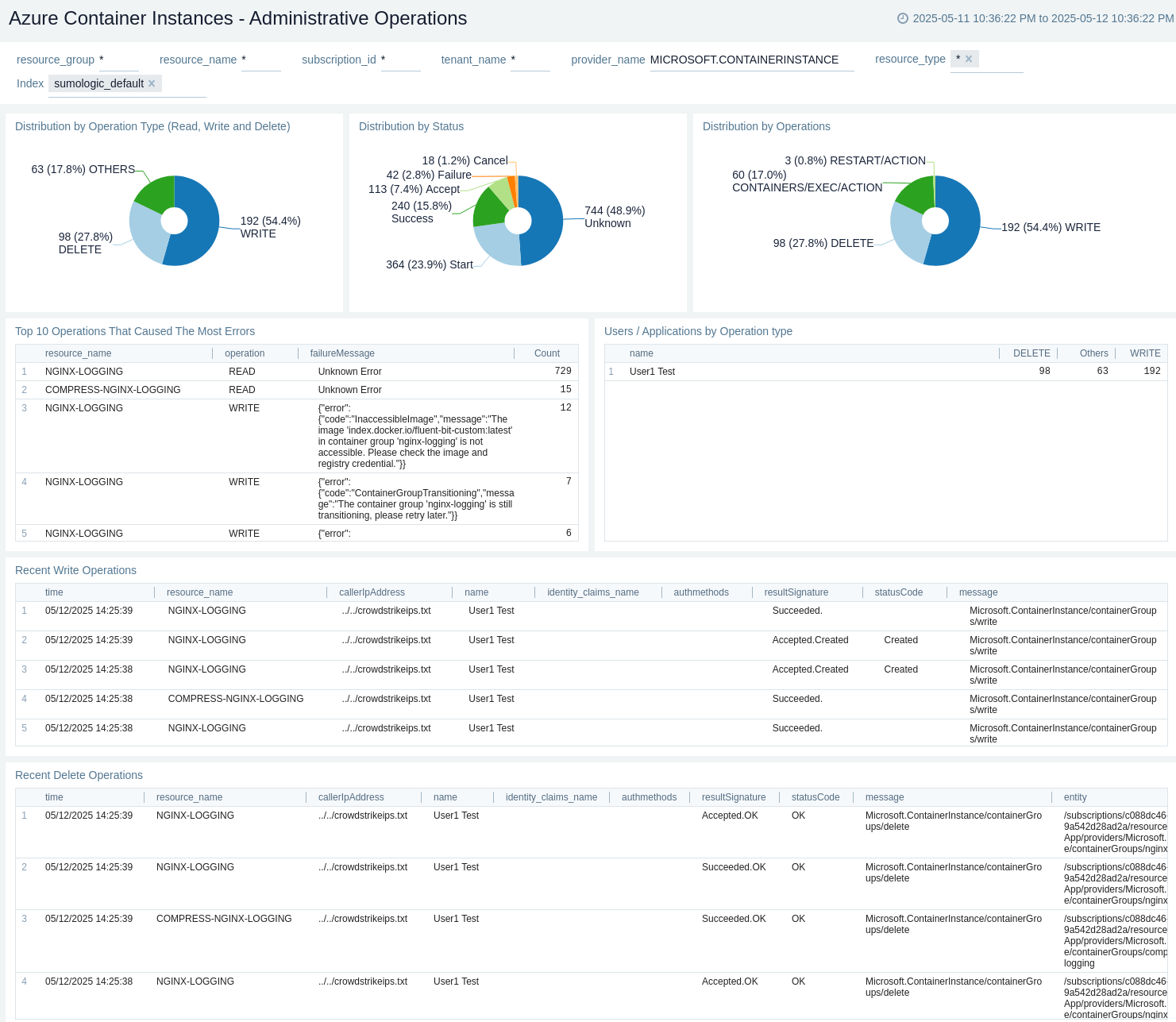
Administrative Operations
The Azure Container Instances - Administrative Operations dashboard provides details on the operational activities and status of your Azure Container Instances resources.
Use this dashboard to:
- Monitor the distribution of operation types and their success rates to ensure proper functioning of your Container Instances system.
- Identify potential issues by analyzing the top operations causing errors and correlating them with specific users or applications.
- Track recent write and delete operations to maintain an audit trail of changes made to your Azure Container Instances configuration.
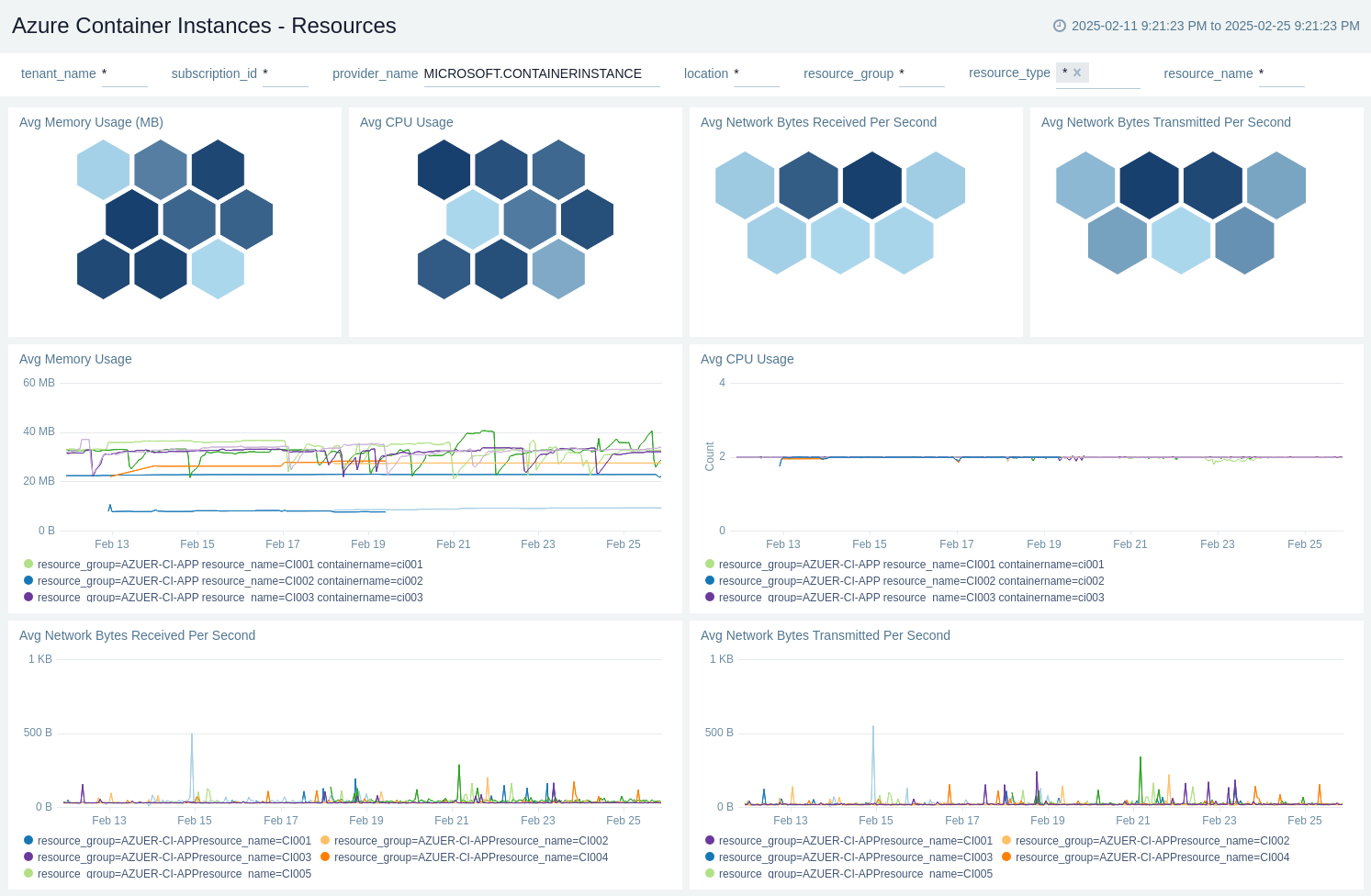
Resources
The Azure Container Instances - Resources dashboard shows average memory usage, avg CPU usage, and average network bytes received and transmitted per sec.
Use this dashboard to:
- Monitor Average Memory and CPU usage with it's trend.
- Monitor Average Received and Transmitted network bytes.
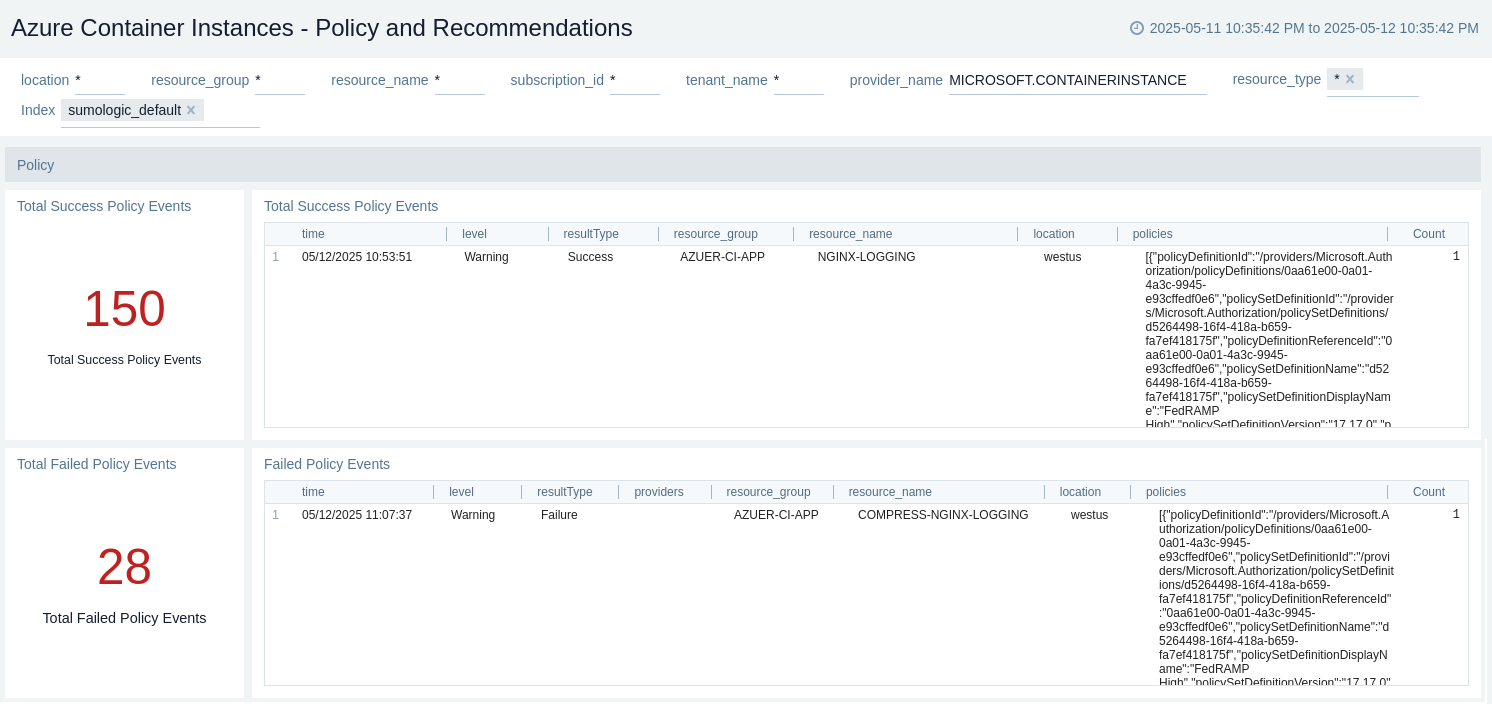
Policy and Recommendations
The Azure Container Instances - Policy and Recommendations dashboard provides details on policy events and recommendations for your Azure Container Instances resources.
Use this dashboard to:
- Monitor the success and failure rates of policy events to ensure proper configuration and compliance.
- Track and analyze recent recommendations to improve the performance and security of your Azure Container Instances setup.
- Identify trends in policy events and recommendations over time to proactively address potential issues.
Create monitors for Azure Container Instances
From your App Catalog:
- From the Sumo Logic navigation, select App Catalog.
- In the Search Apps field, search for and then select your app.
- Make sure the app is installed.
- Navigate to What's Included tab and scroll down to the Monitors section.
- Click Create next to the pre-configured monitors. In the create monitors window, adjust the trigger conditions and notifications settings based on your requirements.
- Scroll down to Monitor Details.
- Under Location click on New Folder.
note
By default, monitor will be saved in the root folder. So to make the maintenance easier, create a new folder in the location of your choice.
- Enter Folder Name. Folder Description is optional.
tip
Using app version in the folder name will be helpful to determine the versioning for future updates.
- Click Create. Once the folder is created, click on Save.
Azure Container Instances alerts
These alerts are metric based and will work for all Azure Container Instances.
| Alert Name | Description | Alert Condition | Recover Condition |
|---|---|---|---|
Azure Container Instances - Memory Usage | This alert is triggered when memory usage is greater than 20 MB. Also warning alert is triggered when the memory usage exceeds 15 MB. | Data volume > 20MB | Data volume < = 20MB |
Azure Container Instances - CPU Usage | This alert is triggered when CPU usage is greater than 100 milicore. Also warning alert is triggered when the CPU usage exceeds 90 millicore. | millicores > 100 | millicores < = 100 |
Upgrade/Downgrade the Azure Container Instances app (optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Azure Container Instances app (optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.
Troubleshooting
Metrics collection via Azure Metrics Source
To troubleshoot metrics collection via Azure Metrics Source, follow the instructions in Troubleshooting Azure Metrics Source.