Azure Load Balancer

Azure Load Balancer is an Azure service that allows you to evenly distribute incoming network traffic across a group of Azure VMs or instances in a Virtual Machine Scale Set. This integration helps in monitoring inbound and outbound data throughput, outbound flows, and the application endpoint health of your Load Balancers.
Log and metric types
For Azure Load Balancer, you can collect the following logs and metrics:
- Load Balancer Health Event. These health event logs are emitted when any issues affecting your load balancer’s health and availability are detected. Learn more.
- Load Balancer Metrics. These metrics are available in Microsoft.Network/loadBalancers namespace.
For more information on supported metrics, refer to Azure documentation.
Setup
This app only supports load balancers of Standard and Gateway SKUs.
Azure service sends monitoring data to Azure Monitor, which can then stream data to Eventhub. Sumo Logic supports:
- Metrics collection using our Azure Metrics Source.
You must explicitly enable diagnostic settings for each Load Balancer you want to monitor. You can forward logs to the same event hub provided they satisfy the limitations and permissions as described here.
When you configure the event hubs source or HTTP source, plan your source category to ease the querying process. A hierarchical approach allows you to make use of wildcards. For example: Azure/LoadBalancer/Logs and Azure/LoadBalancer/Metrics.
Configure collector
Create a hosted collector if not already configured and tag the tenant_name field. You can get the tenant name using the instructions here. Make sure you create the required sources in this collector. 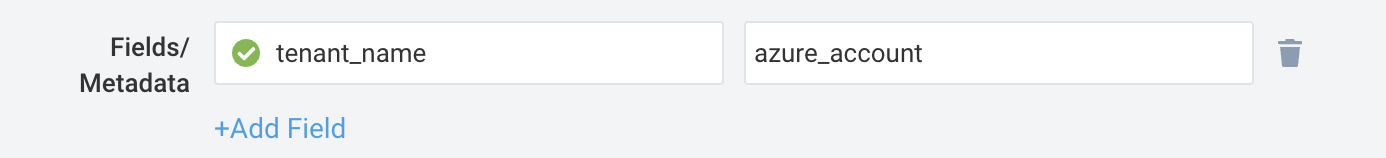
Configure metrics collection
To set up the Azure Metrics source in Sumo Logic, refer to Azure Metrics Source.
Configure logs collection
Diagnostic logs
In this section, you will configure a pipeline for shipping diagnostic logs from Azure Monitor to an Event Hub.
- To set up the Azure Event Hubs source in Sumo Logic, refer to the Azure Event Hubs Source for Logs.
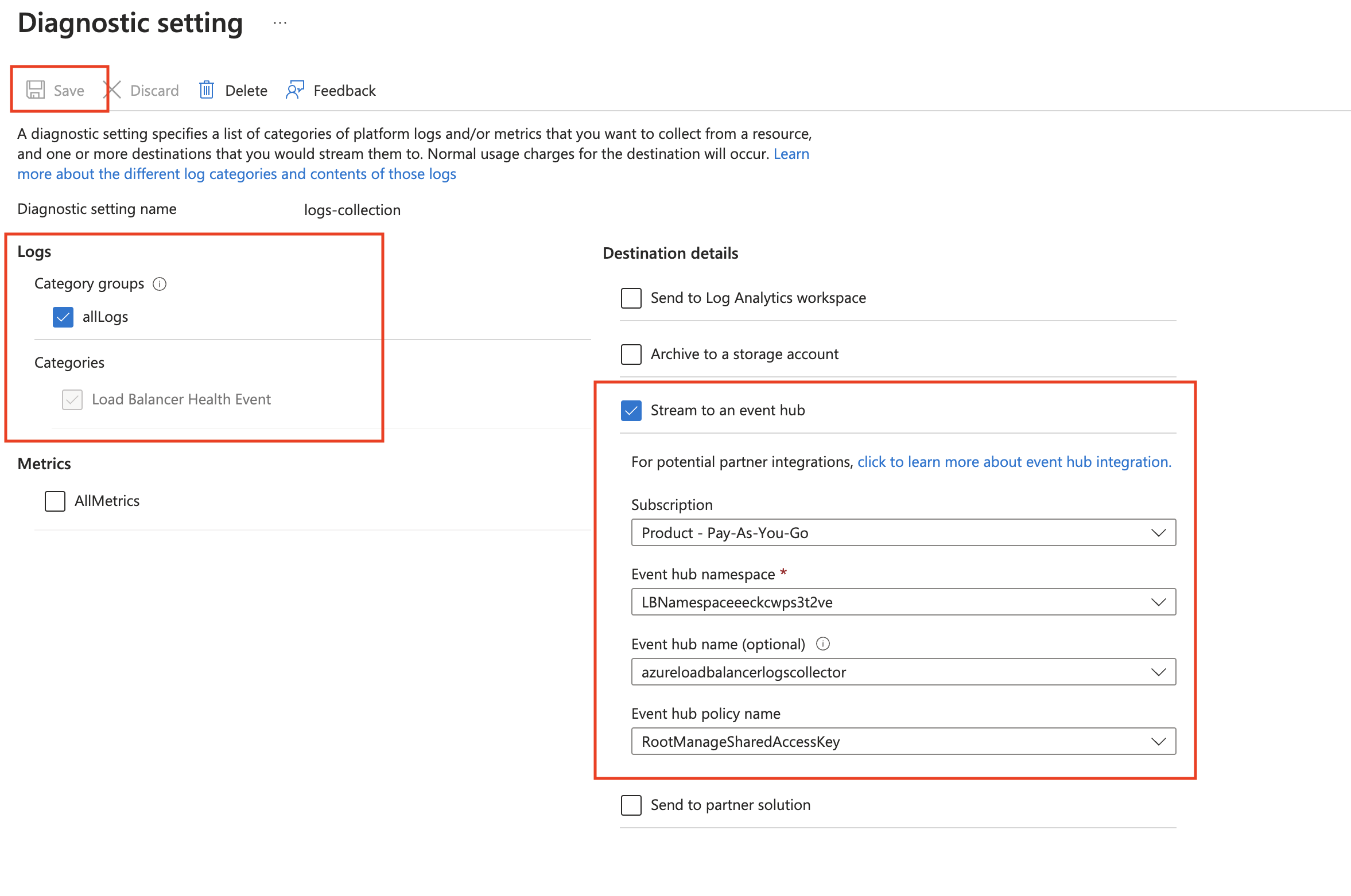
- To create the diagnostic settings in the Azure portal, refer to the Azure documentation. Perform the steps below for each Azure load balancer account that you want to monitor.
- Choose Stream to an event hub as the destination.
- Select
allLogs. - Use the Event Hub namespace and Event Hub name configured in the previous step in the destination details section. You can use the default policy
RootManageSharedAccessKeyas the policy name.
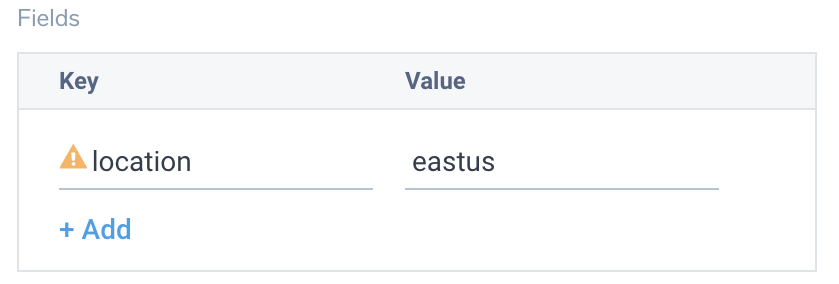
- Tag the location field in the source with the right location value.
Activity logs (optional)
To collect activity logs, follow the instructions here. If you are already collecting activity logs for a subscription, you can skip this step.
Since this source includes logs from multiple regions, do not tag it with the location tag.
Installing the Azure Load Balancer app
Now that you have set up data collection, install the Azure Load Balancer Sumo Logic app to use the pre-configured dashboards that provide visibility into your environment for real-time analysis of overall usage.
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure App section of your respective app, complete the following field.
- Index. Specify value for _index if the collection is configured with custom partition. Learn more. Default value is set to
sumologic_default(default partition)
- Index. Specify value for _index if the collection is configured with custom partition. Learn more. Default value is set to
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
As part of the app installation process, the following fields will be created by default:
tenant_name. This field is tagged at the collector level. You can get the tenant name using the instructions here.location. The region to which the resource name belongs to.subscription_id. ID associated with a subscription where the resource is present.resource_group. The resource group name where the Azure resource is present.provider_name. Azure resource provider name (for example, Microsoft.Network).resource_type. Azure resource type (for example, storage accounts).resource_name. The name of the resource (for example, storage account name).service_type. Type of the service that can be accessed with a Azure resource.service_name. Services that can be accessed with an Azure resource (for example, in Azure Container Instances the service is Subscriptions).
Viewing the Azure Load Balancer dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Many of the Next-Gen apps allow you to provide the Index at the installation time and a default value for this key (sumologic_default). Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the data partition queried by all panels. This restricts the query scope of all the dashboard queries to a specific data partition.
Overview
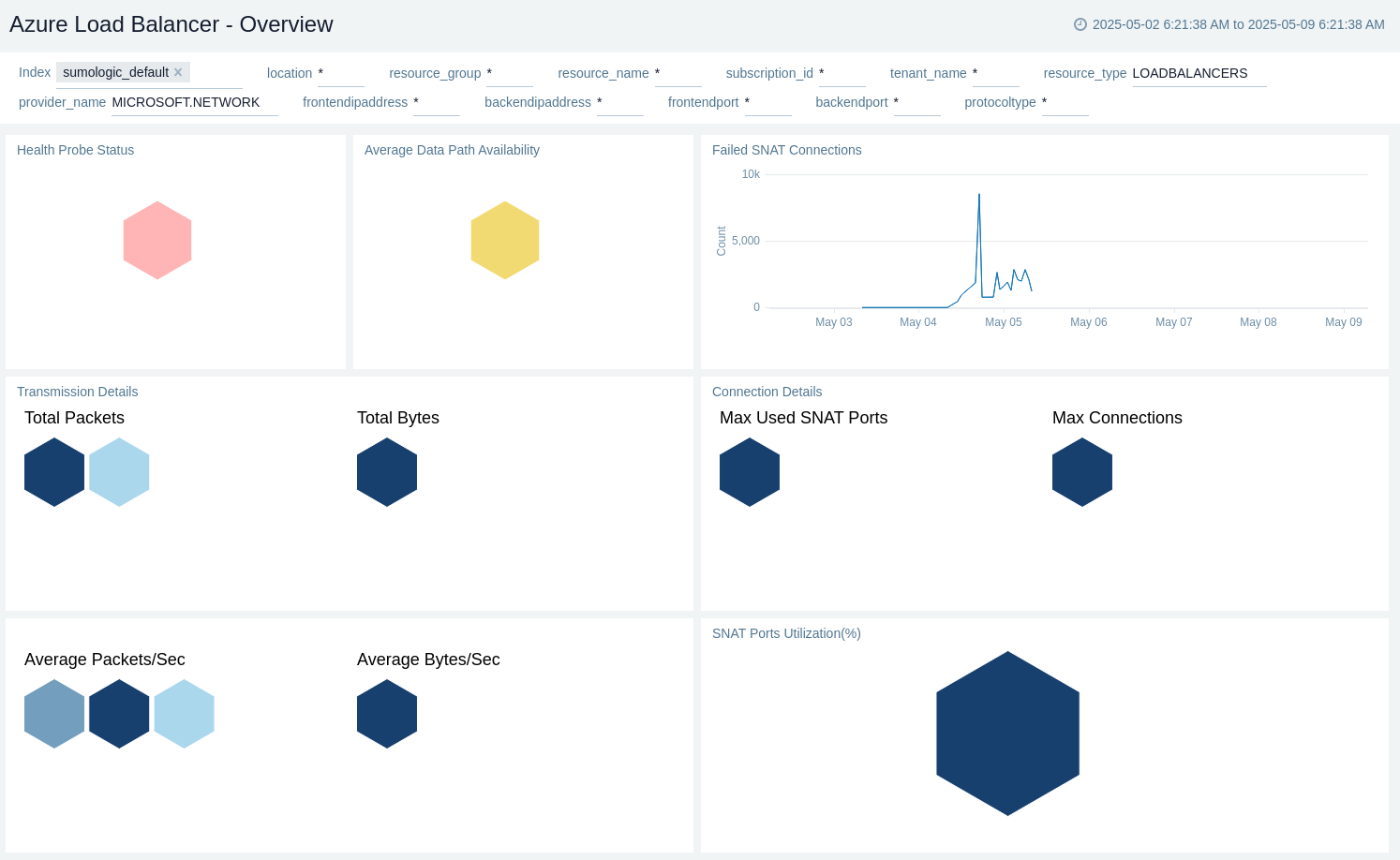
The Azure Load Balancer - Overview dashboard provides collective information on Health Probe Status, Average Data Path Availability, Transmission Details, Connection Details, and SNAT Ports Utilization(%).
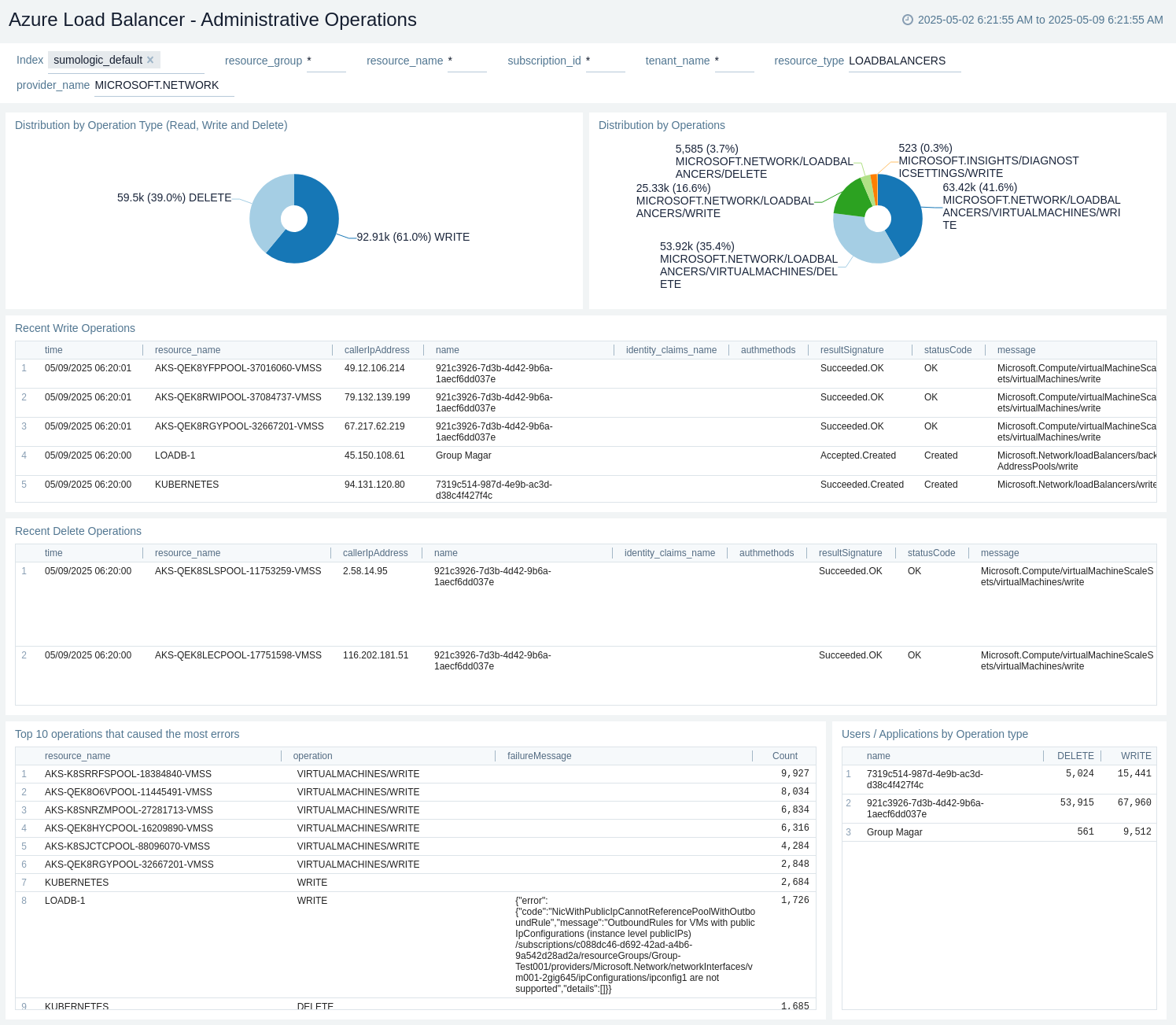
Administrative Operations
The Azure Load Balancer - Administrative Operations dashboard provides details like distribution by operation type, by operation, recent delete operations, top 10 operations that caused most errors, and users/applications by operation type.
Use this dashboard to:
- Identify top users performing administrative operations.
- View the top 10 operations that caused the most errors.
- View recent read, write, and delete operations.
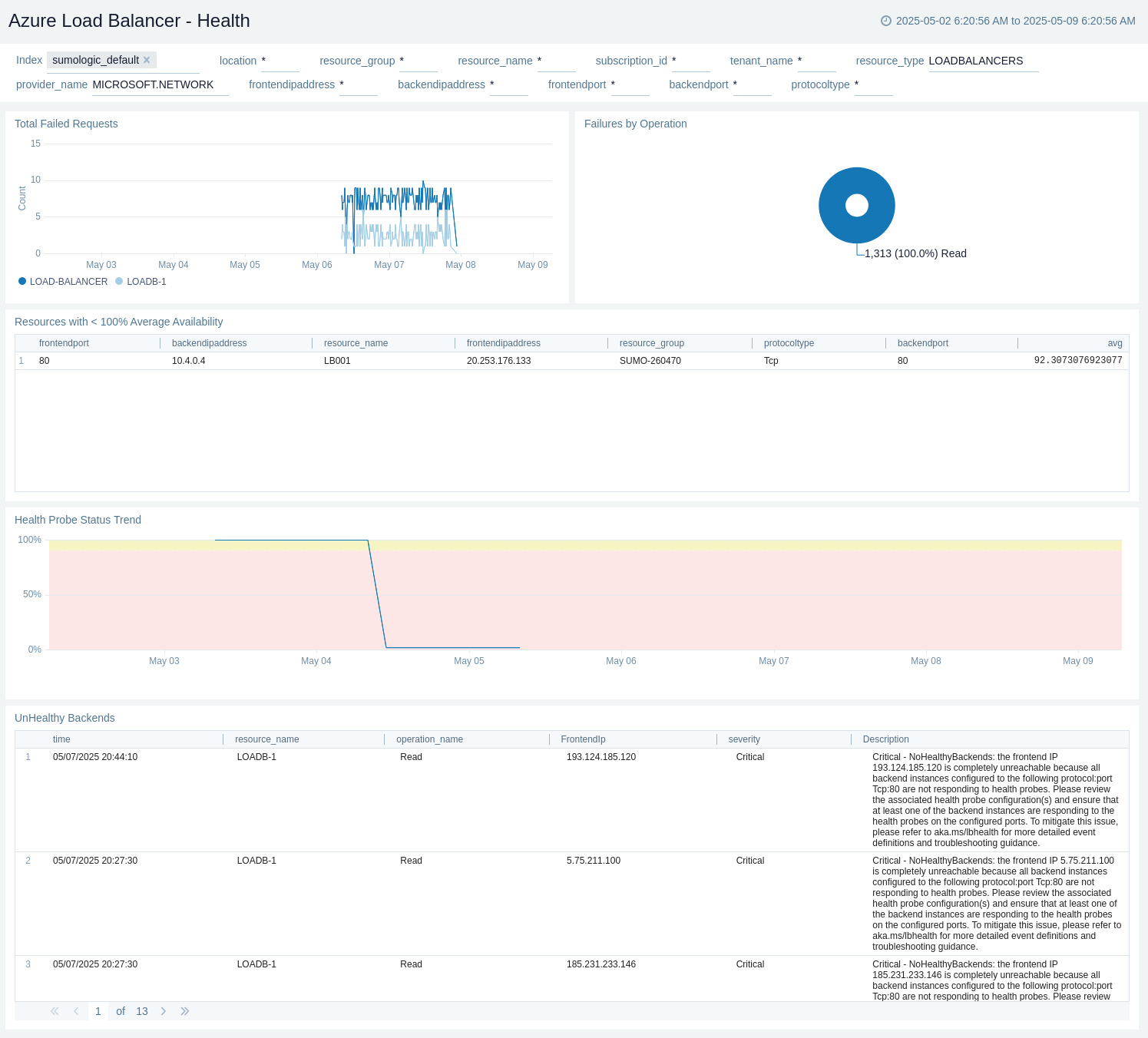
Health
The Azure Load Balancer - Health dashboard provides details like total failed requests, failures by operation, health probe status trends, and unhealthy backends.
Use this dashboard to:
- Identify failed requests and operations.
- Detect when all backend instances in a pool are not responding to the configured health probes.
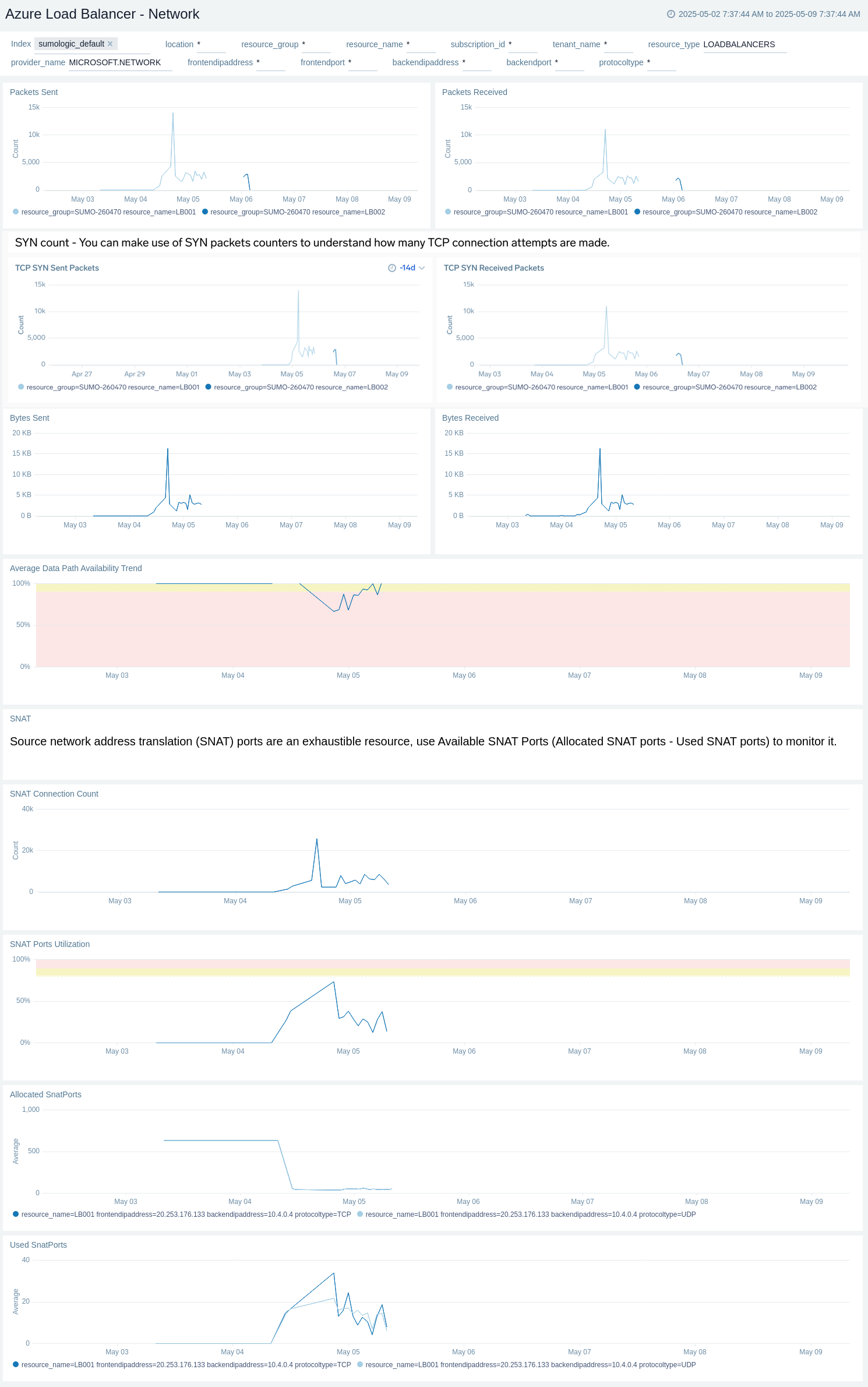
Network
The Azure Load Balancer - Network dashboard provides details like Packets Transmitted by the Load Balancer, TCP SYN packets by the Load Balancer, Bytes Transmitted by the Load Balancer, Average Data Path Availability Trend, SNAT Connection Count, SNAT Ports Utilization, Allocated SnatPorts, and Used SnatPorts.
Use this dashboard to:
- Detect high utilization of allocated ports.
- Detect when there is less data path availability than expected due to platform issues.
- Monitor data transmission (packets and bytes) through your load balancers.
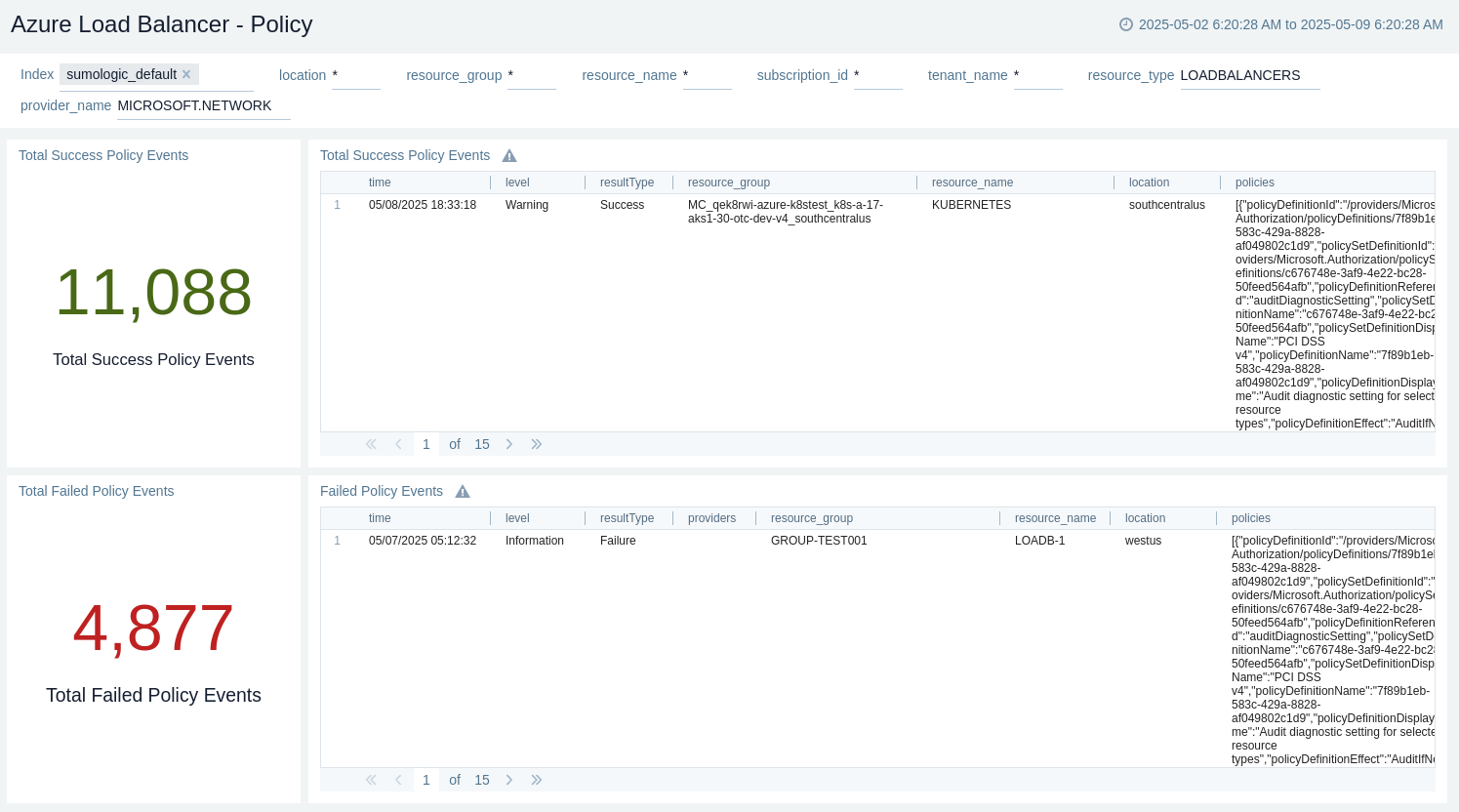
Policy
The Azure Load Balancer - Policy dashboard provides details like total success policy events, success policy events, total failed policy events, and failed policy events.
Use this dashboard to:
- Monitor policy events with warnings and errors.
- View recent failed policy events.
Create monitors for Azure Load Balancer
From your App Catalog:
- From the Sumo Logic navigation, select App Catalog.
- In the Search Apps field, search for and then select your app.
- Make sure the app is installed.
- Navigate to What's Included tab and scroll down to the Monitors section.
- Click Create next to the pre-configured monitors. In the create monitors window, adjust the trigger conditions and notifications settings based on your requirements.
- Scroll down to Monitor Details.
- Under Location click on New Folder.
note
By default, monitor will be saved in the root folder. So to make the maintenance easier, create a new folder in the location of your choice.
- Enter Folder Name. Folder Description is optional.
tip
Using app version in the folder name will be helpful to determine the versioning for future updates.
- Click Create. Once the folder is created, click on Save.
Azure Load Balancer alerts
These alerts are metric based and will work for all Azure Load Balancers.
| Alert Name | Alert Description and Conditions | Alert Condition | Recover Condition |
|---|---|---|---|
Azure Load Balancer - Data Path Availability | This alert is triggered when Data Path Availability is less than 100%. | percentage < 100 | percentage >= 100 |
Azure Load Balancer - Health Probe Status | This alert is triggered when Health Probe Status is less than 100%. | percentage < 100 | percentage >= 100 |
Azure Load Balancer - SNAT Connection Count | This alert is triggered when SNAT Connection count less than 1000. Also Working alert is triggered when SNAT Connection count less than 800. | Count < 1000 | Count >= 1000 |
Azure Load Balancer - Used SNAT Ports | This alert is triggered when Used SNAT Ports count less than 900. Also Working alert is triggered when Used SNAT Ports count less than 800. | Count < 900 | Count >= 900 |
Upgrade/Downgrade the Azure Load Balancer app (Optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Azure Load Balancer app (Optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.
Troubleshooting
Metrics collection via Azure Metrics Source
To troubleshoot metrics collection via Azure Metrics Source, follow the instructions in Troubleshooting Azure Metrics Source.
Additional resources
- Blog: Azure monitoring and troubleshooting
- Glossary: Microsoft Azure