Azure Security - Advisor

The Azure Security - Advisor app provides security analysts visibility into Azure Advisor’s recommendations on security, reliability, operational excellence, and cost optimization. It helps organizations proactively address risks, improve the cloud infrastructure's resiliency, and optimize Azure resource use.
This app includes built-in monitors. For details on creating custom monitors, refer to Create monitors for Azure Security - Advisor app.
Log types
You can collect the following logs for the Azure Security - Advisor app:
- Security Recommendations
- Cost Recommendations
- Reliability Recommendations
- Operational Excellence Recommendations
Sample log messages
Recommendation
{
"schemaId": "azureMonitorCommonAlertSchema",
"data": {
"essentials": {
"alertId": "/subscriptions/11111111-1111-1111-1111-111111111/providers/Microsoft.AlertsManagement/alerts/c37da162-ef73-4621-7a47-7ad188fcf000",
"alertRule": "Sumo-Advisor Inegration",
"targetResourceType": "microsoft.containerservice/managedclusters",
"alertRuleID": "/subscriptions/11111111-1111-1111-1111-111111111/resourceGroups/AG-SUMO/providers/microsoft.insights/activityLogAlerts/Sumo-Advisor Inegration",
"severity": "Sev4",
"signalType": "Activity Log",
"monitorCondition": "Fired",
"targetResourceGroup": "k8sjkse-azure-k8stest",
"monitoringService": "Activity Log - Recommendation",
"alertTargetIDs": [
"/subscriptions/11111111-1111-1111-1111-111111111/resourcegroups/k8sjkse-azure-k8stest/providers/microsoft.containerservice/managedclusters/k8s-19-aks1-31-otc-dev-v4"
],
"configurationItems": [
"k8s-19-aks1-31-otc-dev-v4"
],
"originAlertId": "23e7e500-ff78-6080-4a77-a1eb7f77501c_72d226723d2a3bd9e51379e34ed380ef",
"firedDateTime": "2025-02-28T04:48:41.319118Z",
"description": "Sumo-Advisor Inegration",
"essentialsVersion": "1.0",
"alertContextVersion": "1.0",
"investigationLink": "https://portal.azure.com/#view/Microsoft_Azure_Monitoring_Alerts/Investigation.ReactView/alertId/%2fsubscriptions%2f11111111-1111-1111-1111-111111111%2fresourceGroups%2fk8sjkse-azure-k8stest%2fproviders%2fMicrosoft.AlertsManagement%2falerts%2fc37da162-ef73-4621-7a47-7ad188fcf000"
},
"alertContext": {
"channels": "Operation",
"claims": "{\"http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress\":\"Microsoft.Advisor\"}",
"caller": "Microsoft.Advisor",
"correlationId": "5b3ef3ba-39b3-450c-824c-c26101c26b99",
"eventSource": "Recommendation",
"eventTimestamp": "2025-02-28T04:40:12.4607874+00:00",
"httpRequest": "{\"clientIpAddress\":\"0.0.0.0\"}",
"eventDataId": "23e7e500-ff78-6080-4a77-a1eb7f77501c",
"level": "Informational",
"operationName": "Microsoft.Advisor/recommendations/available/action",
"operationId": "",
"properties": {
"recommendationSchemaVersion": "1.0",
"recommendationCategory": "HighAvailability",
"recommendationImpact": "High",
"recommendationName": "Enable Autoscaling for your system node pools",
"recommendationResourceLink": "https://portal.azure.com/#blade/Microsoft_Azure_Expert/RecommendationListBlade/source/ActivityLog/recommendationTypeId/70829b1a-272b-4728-b418-8f1a56432d33/resourceId/%2Fsubscriptions%2F11111111-1111-1111-1111-111111111%2Fresourcegroups%2Fk8sjkse-azure-k8stest%2Fproviders%2FMicrosoft.ContainerService%2FmanagedClusters%2Fk8s-19-aks1-31-otc-dev-v4",
"recommendationType": "70829b1a-272b-4728-b418-8f1a56432d33"
},
"status": "Active",
"subStatus": "",
"tenantId": "",
"submissionTimestamp": "2025-02-28T04:40:12.4607874+00:00",
"ReceivedTime": "2025-02-28T04:46:34+00:00",
"ingestionTime": "2025-02-28T04:46:37.5062562+00:00",
"Activity Log Event Description": "A new recommendation is available."
},
"customProperties": {
}
}
}
Sample queries
_sourceCategory=azure/advisor
| json field=_raw
"data.alertContext.properties.recommendationResourceLink", "data.essentials.alertId", "data.alertContext.level", "data.alertContext.properties.recommendationImpact", "data.alertContext.ReceivedTime", "data.alertContext.properties.recommendationName", "data.alertContext.properties.recommendationCategory", "data.essentials.targetResourceType", "data.essentials.targetResourceGroup", "data.alertContext.tenantId", "data.essentials.investigationLink" as recommendation_link, alert_id, severity, impact, recommendation_eval_date,display_name, category,affected_resource_type, affected_resource_name, tenant_id, azure_portal_link nodrop
| parse regex field=alert_id "subscriptions/(?<subscription_id>[a-f0-9\-]+)"
| replace(recommendation_eval_date,/(\.\d+Z)/, "") as recommendation_eval_date
| replace(recommendation_eval_date,"T", " ") as date
| tourl(recommendation_link,display_name) as recommendation
Setup
To send Azure Advisor events to Sumo Logic, you can configure the Azure Advisor’s alert with Action group as a webhook.
Step 1: Configure Sumo Logic HTTP source
Create Sumo Logic HTTP source and make a note of the HTTP URL.
Step 2: Create an Azure Advisor alert
Refer to Create Azure Advisor alerts in the Azure portal to configure an Azure Advisor alert for Sumo Logic. Sumo Logic recommends you to select the Category and impact level option in the Condition section while creating the alert.
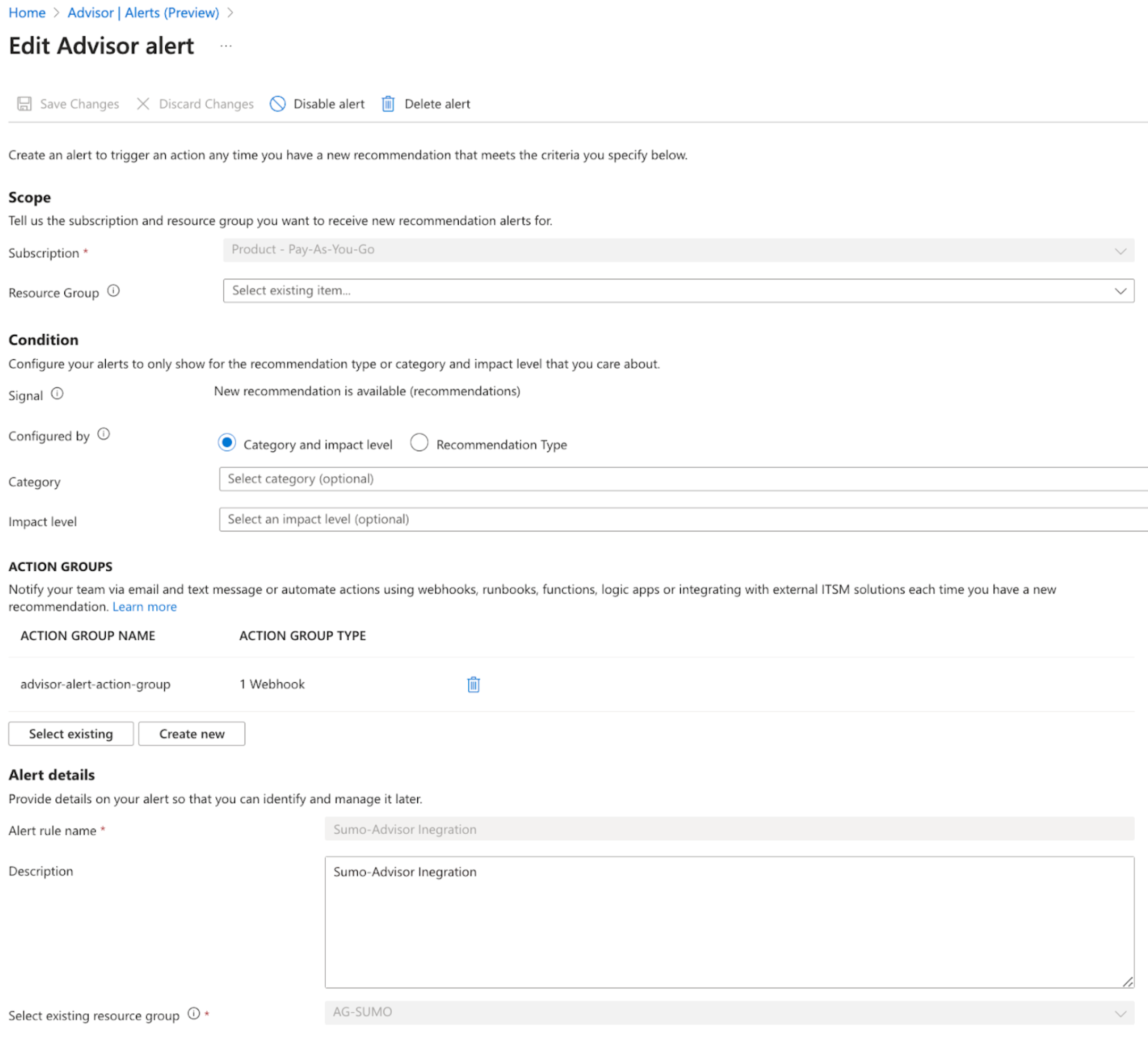
Step 3: Create an action group
Refer to Create an action group in the Azure portal to create an action group for the Azure Advisor alert in step 2.
Sumo Logic recommends you to select the Action type as Webhook and then provide the Sumo Logic HTTP Source URL that you collected from step 1.

Installing the Azure Security - Advisor app
This section shows you how to install the Azure Security - Advisor app for Sumo Logic.
To install the app:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- On the next configuration page, under Select Data Source for your App, complete the following fields:
- Data Source. Select one of the following options:
- Choose Source Category and select a source category from the list; or
- Choose Enter a Custom Data Filter, and enter a custom source category beginning with an underscore. For example,
_sourceCategory=MyCategory.
- Folder Name. You can retain the existing name or enter a custom name of your choice for the app.
- All Folders (optional). The default location is the Personal folder in your Library. If desired, you can choose a different location and/or click New Folder to add it to a new folder.
- Data Source. Select one of the following options:
- Click Next.
- Look for the dialog confirming that your app was installed successfully.
Post-installation
Once your app is installed, it will appear in your Personal folder or the folder that you specified. From here, you can share it with other users in your organization. Dashboard panels will automatically start to fill with data matching the time range query received since you created the panel. Results won't be available immediately, but within about 20 minutes, you'll see completed graphs and maps.
Viewing the Azure Security - Advisor dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Most Next-Gen apps allow you to provide the scope at the installation time and are comprised of a key (
_sourceCategoryby default) and a default value for this key. Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the dataset queried by all panels. This eliminates the need to create multiple copies of the same dashboard with different queries.
Advisor Security Recommendations
The Azure Security - Advisor Security Recommendations dashboard provides security analysts with insights into security recommendations from Azure Advisor, categorized by severity (high, medium, low) to help prioritize risks. It highlights affected resource types and assets, enabling quick identification of vulnerabilities. A trend analysis graph visualizes recommendation patterns over time, tracking improvements and recurring risks. The Top Action Plan section lists prioritized recommendations with timestamps and affected resources for efficient remediation. Additionally, a summary of recommendations offers a broader view of risks across Azure services, helping security teams enhance their security posture and mitigate vulnerabilities.
Advisor Cost Recommendations
The Azure Security - Advisor Cost Recommendations dashboard provides security analysts with cost optimization strategies for Azure, helping identify idle and underutilized resources to reduce cloud spending. It categorizes recommendations by impact level, highlighting priority areas for cost-saving actions. The Affected Resources panel identifies services, such as compute disks, that may benefit from resizing or deallocation. A timeline visualization tracks cost recommendations over time to monitor trends and assess optimization effectiveness. The Cost Recommendation Summary details recommendations, their impact, and associated resources, aiding informed decision-making. This dashboard helps maintain financial efficiency while ensuring optimal resource utilization in Azure.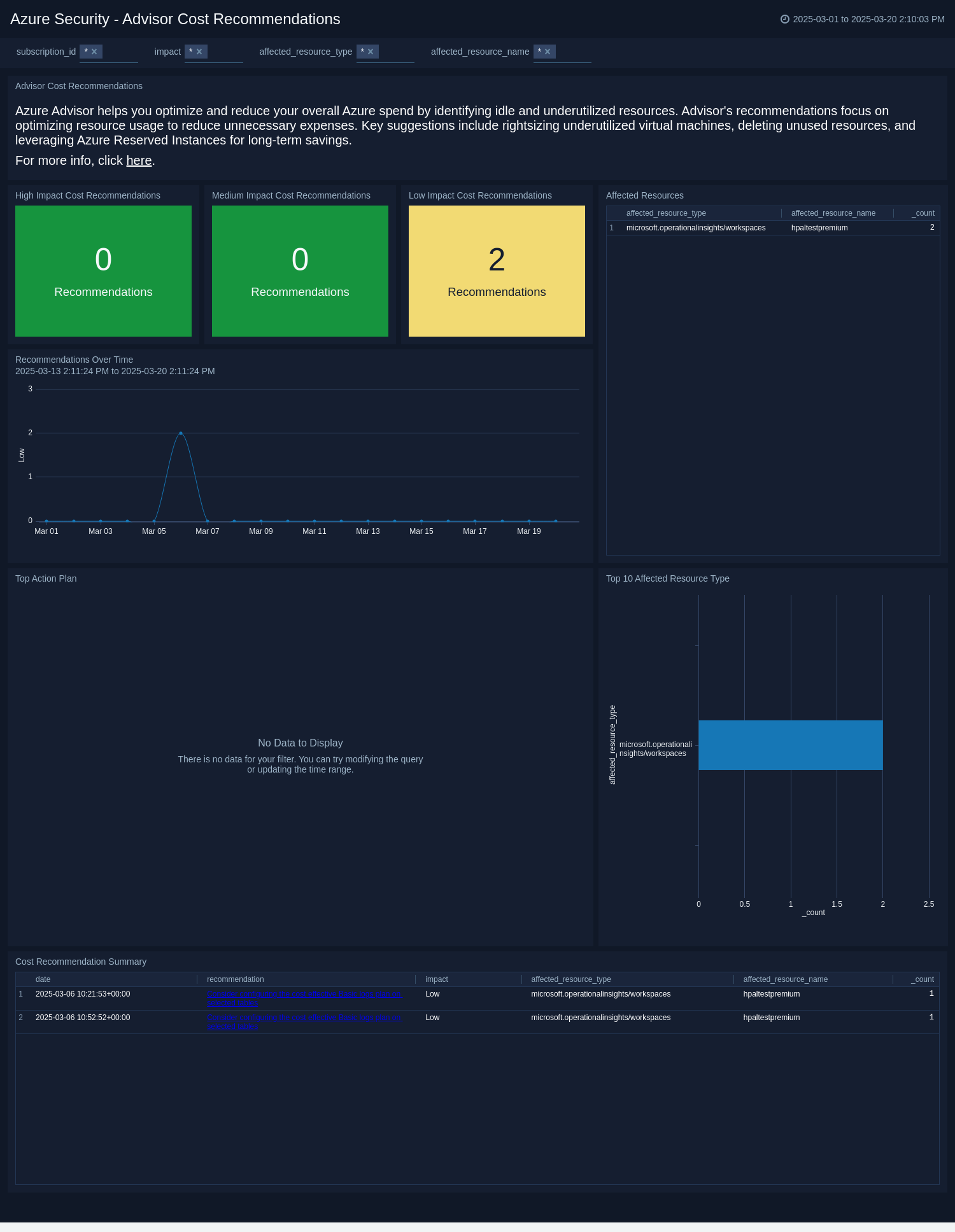
Advisor Reliability Recommendations
The Azure Security - Advisor Reliability Recommendations dashboard provides security analysts with insights into reliability risks affecting business-critical applications. It categorizes recommendations by severity (high, medium, low) to help prioritize reliability concerns. The dashboard highlights affected resource types and assets for quick identification of infrastructure issues. A timeline visualization tracks recommendation trends, offering insights into recurring risks. The Top Action Plan section lists prioritized recommendations with timestamps and affected resources for efficient remediation. Additionally, the Security Recommendation Summary provides an overview of reliability risks across Azure services. This dashboard helps security teams enhance system resilience, minimize downtime, and ensure optimal application performance. 
Advisor Operational Excellence Recommendations
The Azure Security - Advisor Operational Excellence Recommendations dashboard provides security analysts with insights into optimizing process workflows, enhancing resource manageability, and enforcing deployment best practices. It categorizes recommendations by impact (medium and low) to help prioritize improvements for streamlining cloud operations. The Affected Resources panel highlights impacted services, with a focus on Azure Kubernetes Service (AKS) clusters. A timeline visualization tracks trends in recommendations over time, offering a historical perspective on operational issues. The Recommendation Summary details specific recommendations and associated resources for targeted action. This dashboard helps security teams improve system reliability and maintain efficient cloud operations.
Create monitors for the Azure Security - Advisor app
From your App Catalog:
- From the Sumo Logic navigation, select App Catalog.
- In the Search Apps field, search for and then select your app.
- Make sure the app is installed.
- Navigate to What's Included tab and scroll down to the Monitors section.
- Click Create next to the pre-configured monitors. In the create monitors window, adjust the trigger conditions and notifications settings based on your requirements.
- Scroll down to Monitor Details.
- Under Location click on New Folder.
note
By default, monitor will be saved in the root folder. So to make the maintenance easier, create a new folder in the location of your choice.
- Enter Folder Name. Folder Description is optional.
tip
Using app version in the folder name will be helpful to determine the versioning for future updates.
- Click Create. Once the folder is created, click on Save.
Azure Security - Advisor alerts
| Name | Description | Trigger Type (Critical / Warning / MissingData) | Alert Condition |
|---|---|---|---|
High Impact Alert | This alert is triggered when new high-impact advisories are generated, enabling security analysts to take immediate action to mitigate risks and maintain system integrity. The High Impact alert for Azure Advisor in Sumo Logic detects security, reliability, operational, or cost-related recommendations classified as high impact. These recommendations indicate critical risks that could significantly affect the security, performance, or efficiency of your Azure environment. | Critical | Count > 0 |
Upgrade/Downgrade the Azure Security - Advisor app (optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Azure Security - Advisor app (optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.
Troubleshooting
HTTP Logs and Metrics Source used by Azure Functions
To troubleshoot metrics collection, follow the instructions in Collect Metrics from Azure Monitor > Troubleshooting metrics collection.