1Password

1Password is a secure and convenient password manager for documents, credit card information, and addresses. The Sumo Logic app for 1Password enables you to monitor sign-in and item usage events within your 1Password account. It offers insights into failed and successful authentications, breaking down events by client applications, type, category, users, and geo-location, while also identifying outliers and analyzing threats related to sign-ins. Furthermore, the app provides in-depth tracking of critical security activities such as account activations, deletions, email changes, and group creations. It visualizes audit events by geographic location, highlights risky areas, and offers detailed logs of recent access activities and role changes. This app helps secure your 1Password vault by delivering comprehensive insights into user actions and threat intelligence on clients accessing shared vaults.
This app includes built-in monitors. For details on creating custom monitors, refer to Create monitors for 1Password app.
Log types
The 1Password app uses the following logs:
Sample log messages
Sign-in attempt Event
{
"uuid": "56YE2TYN2VFYRLNSHKPW5NVT5E",
"session_uuid": "A5K6COGVRVEJXJW3XQZGS7VAMM",
"timestamp": "2021-03-01T16:32:50-03:00",
"category": "firewall_failed",
"type": "continent_blocked",
"country": "France",
"details": {
"value": "Europe"
},
"target_user": {
"uuid": "IR7VJHJ36JHINBFAD7V2T5MP3E",
"name": "Wendy Appleseed",
"email": "wendy_appleseed@agilebits.com"
},
"client": {
"app_name": "1Password Extension",
"app_version": "20127",
"platform_name": "Chrome",
"platform_version": "string",
"os_name": "MacOSX",
"os_version": "10.15.6",
"ip": "13.227.95.22"
}
}
Item Usage Event
{
"uuid": "56YE2TYN2VFYRLNSHKPW5NVT5E",
"timestamp": "2020-06-11T16:32:50-03:00",
"used_version": 0,
"vault_uuid": "VZSYVT2LGHTBWBQGUJAIZVRABM",
"item_uuid": "SDGD3I4AJYO6RMHRK8DYVNFIDZ",
"user": {
"uuid": "4HCGRGYCTRQFBMGVEGTABYDU2V",
"name": "Wendy Appleseed",
"email": "wendy_appleseed@agilebits.com"
},
"client": {
"app_name": "1Password Extension",
"app_version": "20127",
"platform_name": "Chrome",
"platform_version": "string",
"os_name": "MacOSX",
"os_version": "10.15.6",
"ip": "13.227.95.22"
},
"action": "secure-copy"
}
Audit Events Log
{
"uuid": "56YE2TYN2VFYRLNSHKPW5NVT5E",
"timestamp": "2023-03-15T16:33:50-03:00",
"actor_uuid": "4HCGRGYCTRQFBMGVEGTABYDU2V",
"actor_details": {
"uuid:": "4HCGRGYCTRQFBMGVEGTABYDU2V",
"name": "Jeff Shiner",
"email": "jeff_shiner@agilebits.com"
},
"action": "join",
"object_type": "gm",
"object_uuid": "pf8soyakgngrphytsyjed4ae3u",
"aux_id": 9277034,
"aux_uuid": "K6VFYDCJKHGGDI7QFAXX65LCDY",
"aux_details": {
"uuid": "K6VFYDCJKHGGDI7QFAXX65LCDY",
"name": "Wendy Appleseed",
"email": "wendy_appleseed@agilebits.com"
},
"aux_info": "A",
"session": {
"uuid": "A5K6COGVRVEJXJW3XQZGS7VAMM",
"login_time": "2023-03-15T16:33:50-03:00",
"device_uuid": "lc5fqgbrcm4plajd8mwncv2b3u",
"ip": "192.0.2.254"
},
"location": {
"country": "Canada",
"region": "Ontario",
"city": "Toronto",
"latitude": 43.5991,
"longitude": -79.4988
}
}
Sample queries
_sourceCategory="1pw"
| json "type", "category", "timestamp", "details", "target_user.name", "target_user.email", "client.app_name", "client.app_version", "client.platform_name", "client.os_name", "client.os_version", "client.ip_address", "location.country", "location.region", "location.city" as type, category, timestamp, details, target_user_name, target_user_email, client_app_name, client_app_version, client_platform, client_os, client_os_version, client_ip, country, region, city
| where category matches "{{category}}" AND type matches "{{type}}" AND country matches "{{country}}" AND city matches "{{city}}" AND target_user_name matches "{{target_user_name}}" AND client_app_name matches "{{client_app_name}}" AND client_platform matches "{{client_platform}}" AND client_os matches "{{client_os}}"
| where category matches "*succ*"
| count by timestamp, target_user_name, type, category, details,client_app_name, client_app_version, client_platform, client_os, client_os_version, client_ip, country, region, city
_sourceCategory="1pw"
| json "type", "category", "timestamp", "details", "target_user.name", "target_user.email", "client.app_name", "client.app_version", "client.platform_name", "client.os_name", "client.os_version", "client.ip_address", "location.country", "location.region", "location.city" as type, category, timestamp, details, target_user_name, target_user_email, client_app_name, client_app_version, client_platform, client_os, client_os_version, client_ip, country, region, city
| where category matches "{{category}}" AND type matches "{{type}}" AND country matches "{{country}}" AND city matches "{{city}}" AND target_user_name matches "{{target_user_name}}" AND client_app_name matches "{{client_app_name}}" AND client_platform matches "{{client_platform}}" AND client_os matches "{{client_os}}"
| where !(category matches "*succ*")
| count by timestamp, target_user_name, type, category, details,client_app_name, client_app_version, client_platform, client_os, client_os_version, client_ip, country, region, city
_sourceCategory=1pw action
| json "timestamp", "user.name", "client.app_name", "client.platform_name", "client.platform_version", "client.os_name", "client.os_version", "client.ip_address", "location.country", "location.region", "location.city", "action", "vault_uuid", "item_uuid" as timestamp, user_name, client_app_name, client_platform, client_platform_version, client_os, client_os_version, client_ip, country, region, city, action, vault_uuid, item_uuid
| count by timestamp, user_name, client_app_name, client_platform, client_platform_version, client_os, client_os_version, client_ip, country, region, city, action, vault_uuid, item_uuid
_sourceCategory="app/"
| json "uuid", "object_type", "action", "actor_details.email", "aux_details.name", "aux_details.email", "aux_info" as uuid, object_type, action, actor_email, aux_name, aux_email, aux_info nodrop
//global filter
| where action matches "*"
| where object_type matches "*"
| where object_type in ("uva", "gva")
| count as frequency by _messageTime, actor_email, object_type, action, aux_name, aux_email, aux_info
| sort by _messageTime
| formatDate(_messageTime, "dd-MM-yyyy HH:mm:ss") as time
| fields time, actor_email, object_type, action, aux_name, aux_email, aux_info
| fields -_messageTime
Collection configuration and app installation
Depending on the set up collection method, you can configure and install the app in three ways:
- Create a new collector and install the app. Create a new Sumo Logic Cloud-to-Cloud (C2C) source under a new Sumo Logic Collector and later install the app, or
- Use an existing collector and install the app. Create a new Sumo Logic Cloud-to-Cloud (C2C) source under an existing Sumo Logic Collector and later install the app, or
- Use existing source and install the app. Use your existing configured Sumo Logic Cloud-to-Cloud (C2C) source and install the app.
Use the Cloud-to-Cloud Integration for 1Password to create the source and use the same source category while installing the app. By following these steps, you can ensure that your 1Password app is properly integrated and configured to collect and analyze your 1Password data.
Create a new collector and install the app
To set up collection and install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- In the Set Up Collection section of your respective app, select Create a new Collector.
- Collector Name. Enter a Name to display the Source in the Sumo Logic web application. The description is optional.
- Timezone. Set the default time zone when it is not extracted from the log timestamp. Time zone settings on Sources override a Collector time zone setting.
- (Optional) Metadata. Click the +Add Metadata link to add a custom log Metadata Fields. Define the fields you want to associate, each metadata field needs a name (key) and value.
 A green circle with a checkmark is shown when the field exists and is enabled in the Fields table schema.
A green circle with a checkmark is shown when the field exists and is enabled in the Fields table schema. An orange triangle with an exclamation point is shown when the field doesn't exist, or is disabled in the Fields table schema. In this case, you'll see an option to automatically add or enable the nonexistent fields to the Fields table schema. If a field is sent to Sumo Logic but isn’t present or enabled in the schema, it’s ignored and marked as Dropped.
An orange triangle with an exclamation point is shown when the field doesn't exist, or is disabled in the Fields table schema. In this case, you'll see an option to automatically add or enable the nonexistent fields to the Fields table schema. If a field is sent to Sumo Logic but isn’t present or enabled in the schema, it’s ignored and marked as Dropped.
- Click Next.
- Configure the source as specified in the
Infobox above, ensuring all required fields are included. - In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Use an existing collector and install the app
To set up the source in the existing collector and install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- In the Set Up Collection section of your respective app, select Use an existing Collector.
- From the Select Collector dropdown, select the collector that you want to set up your source with and click Next.
- Configure the source as specified in the
Infobox above, ensuring all required fields are included. - In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Use an existing source and install the app
To skip collection and only install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- In the Set Up Collection section of your respective app, select Skip this step and use existing source and click Next.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Viewing 1Password dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Most Next-Gen apps allow you to provide the scope at the installation time and are comprised of a key (
_sourceCategoryby default) and a default value for this key. Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the dataset queried by all panels. This eliminates the need to create multiple copies of the same dashboard with different queries.
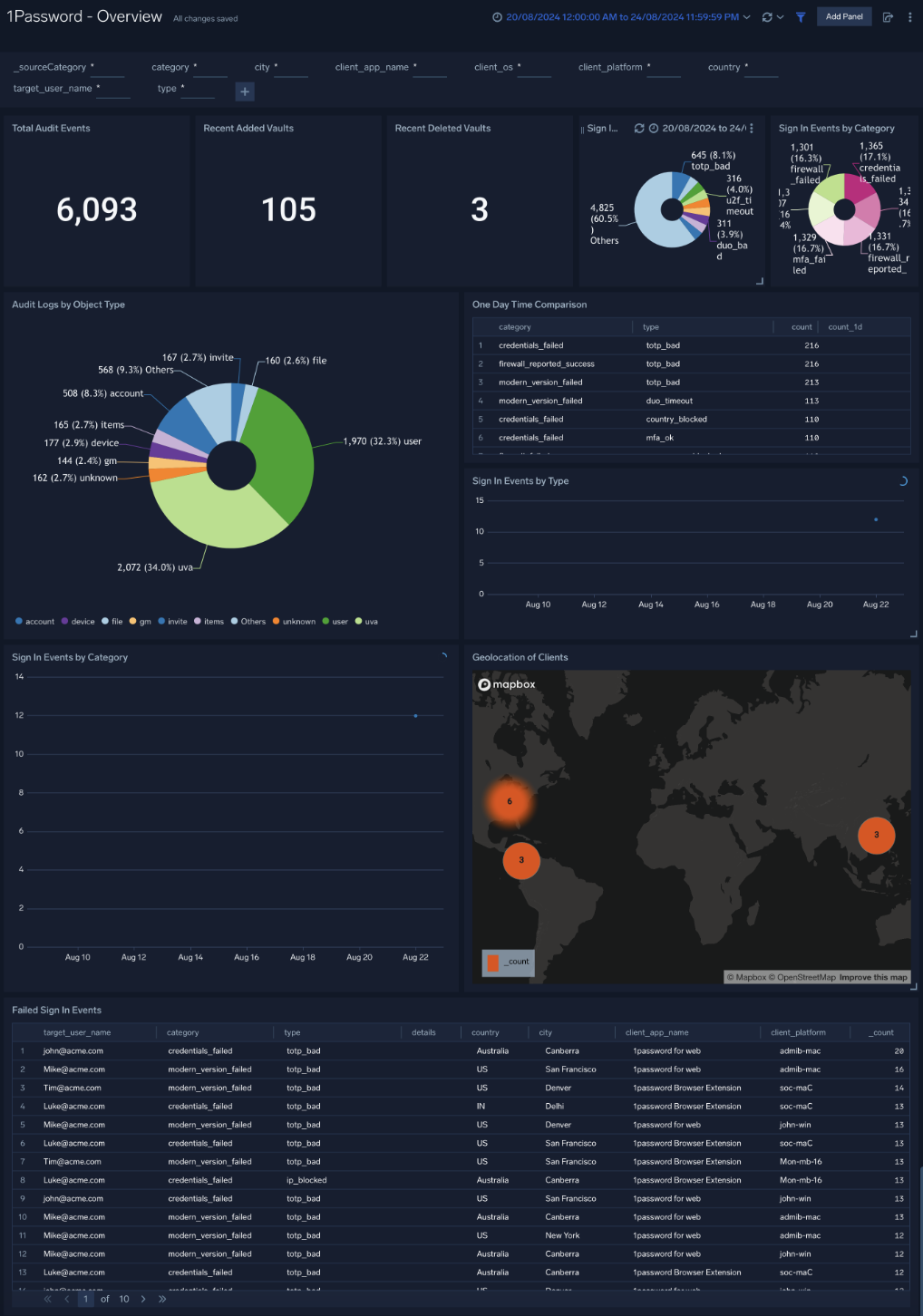
Overview
The 1Password - Overview provides an overview of 1Password events including events breakdown by type, category, geographic location, one-day time comparison of events, audit logs by audit type, and failed sign-in activity.
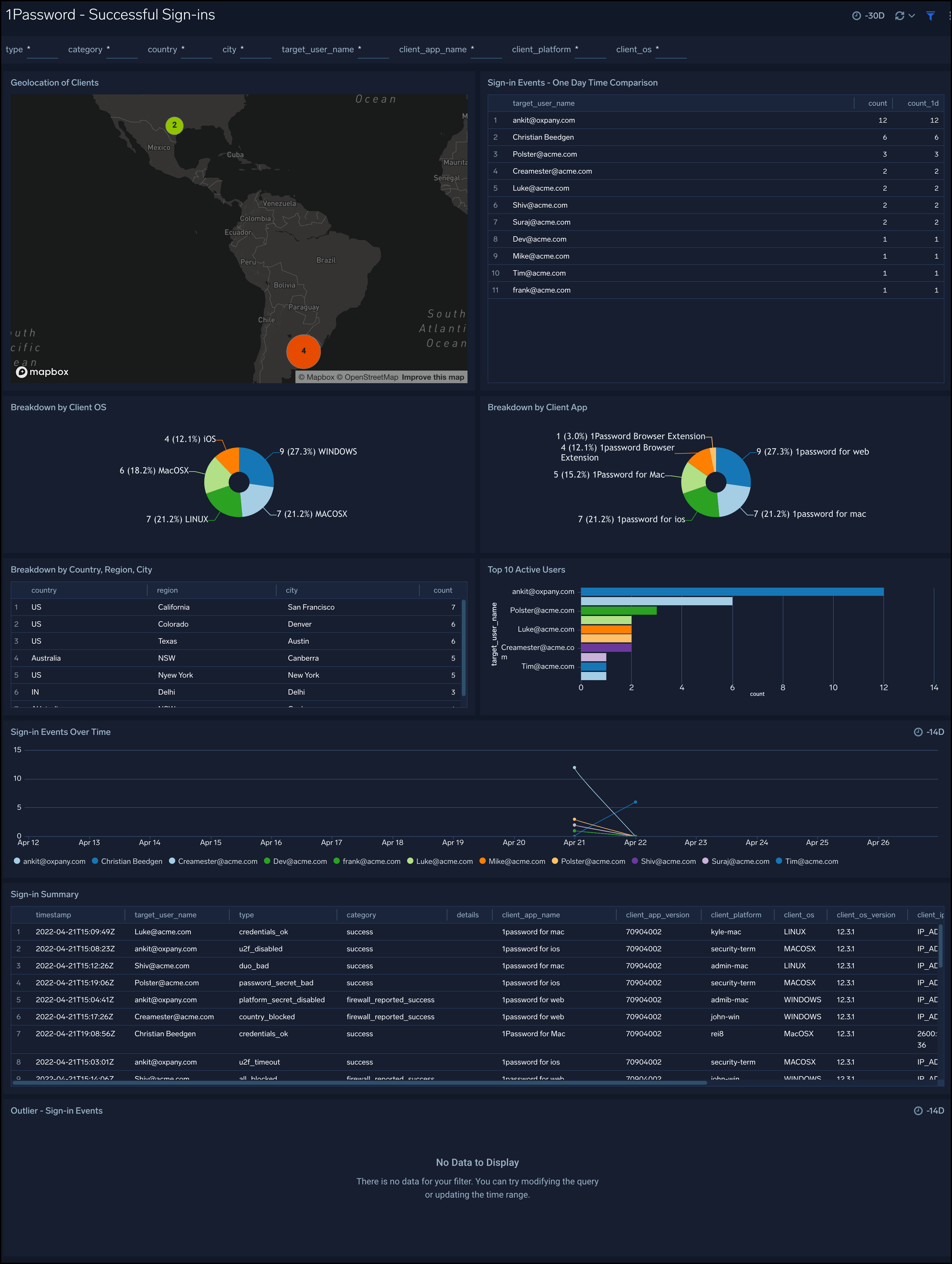
Successful Sign-ins
The 1Password - Successful Sign-ins dashboard provides geographic location of successful sign-in events, one-day time comparison of events, breakdown of events by Category, Type, Users, Country, State, and City.
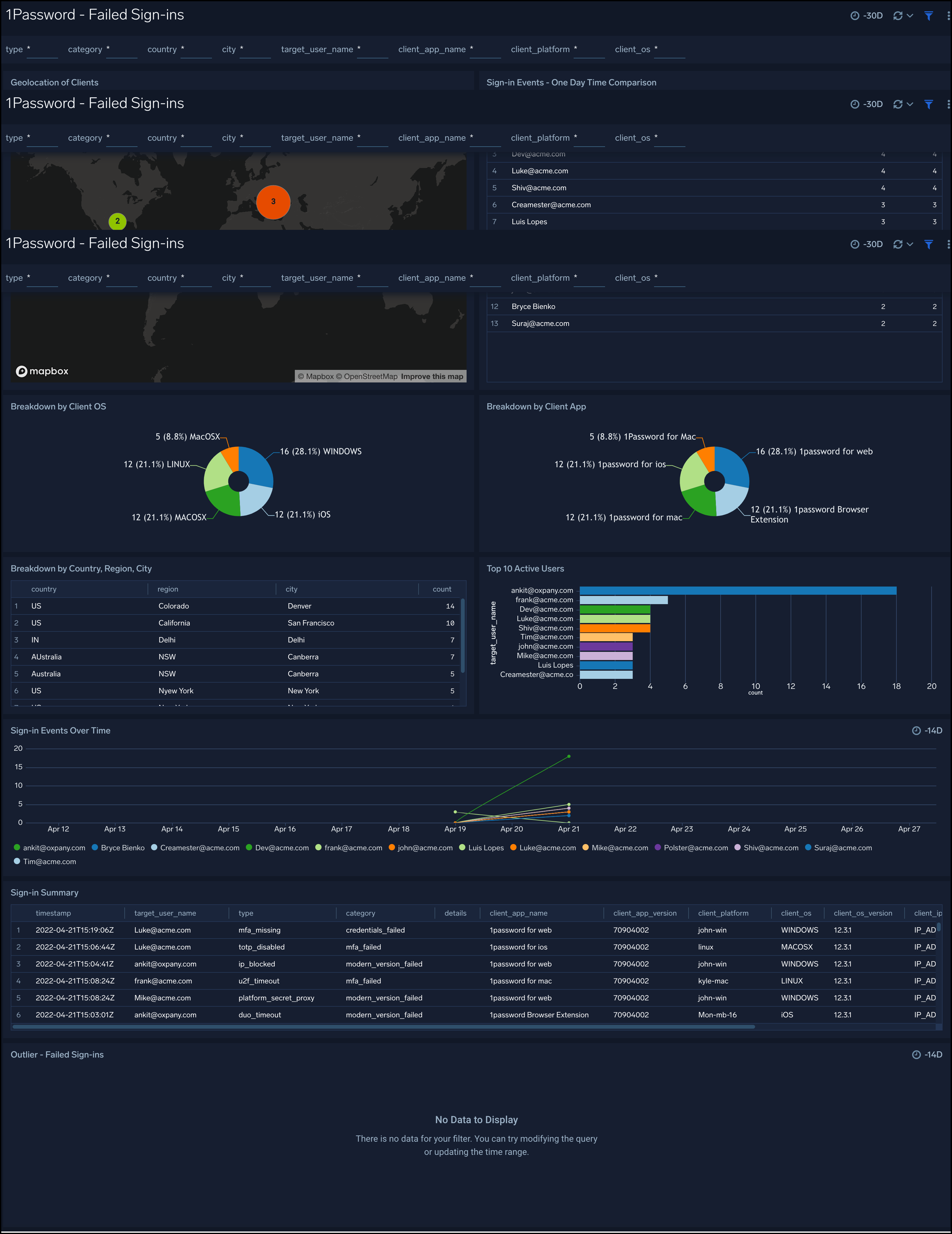
Failed Sign-ins
The 1Password - Failed Sign-ins dashboard provides geographic location of failed events, one-day time comparison of events, breakdown of events by Category, Type, Users, Country, State, and City.
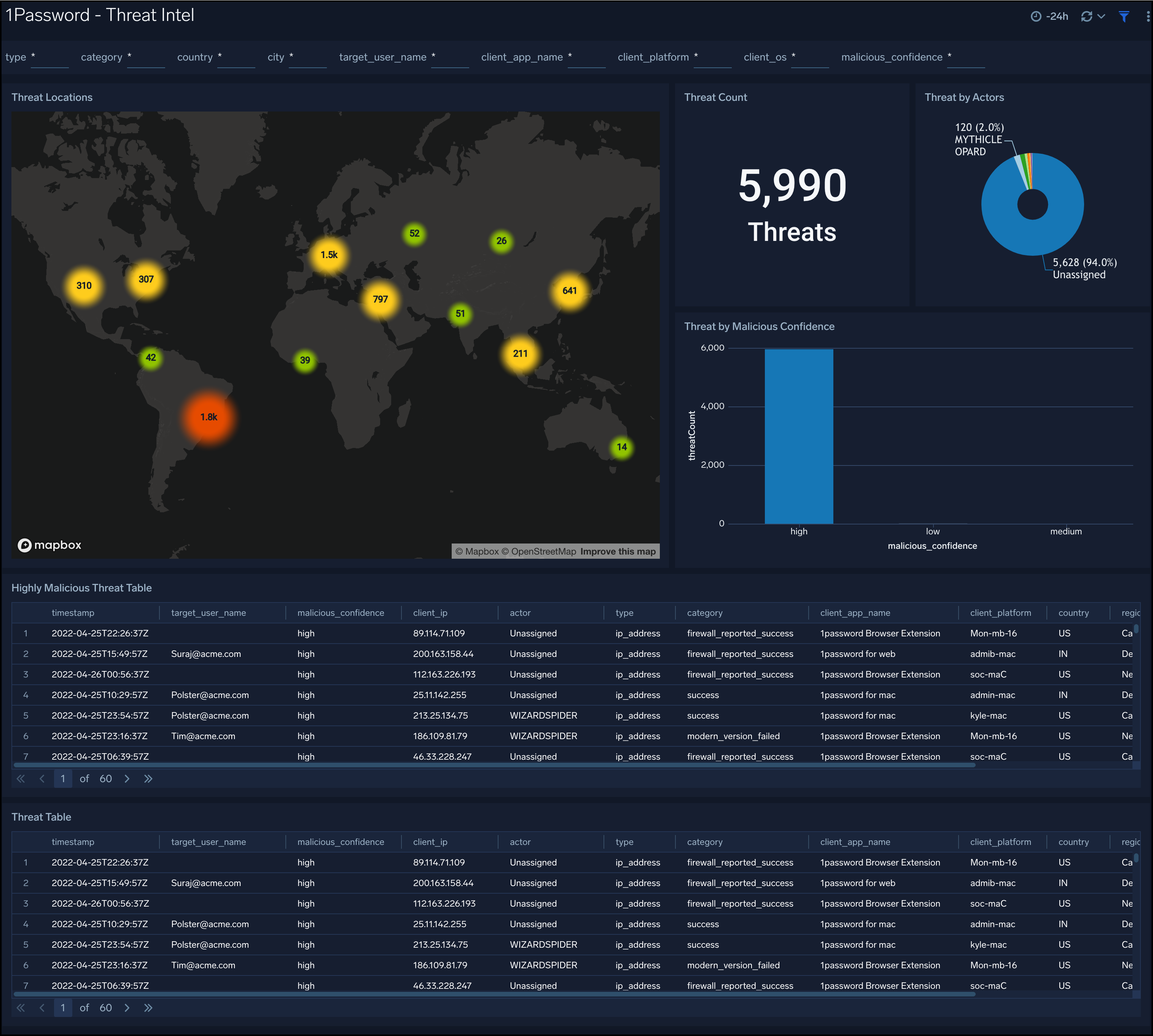
Threat Intel
The 1Password - Threat Intel dashboard provides high-level views of threats throughout your 1Password Service. Dashboard panels display visual graphs and detailed information on Threats by the client, target user, source app, platform, threats by actors, and threats by malicious confidence.
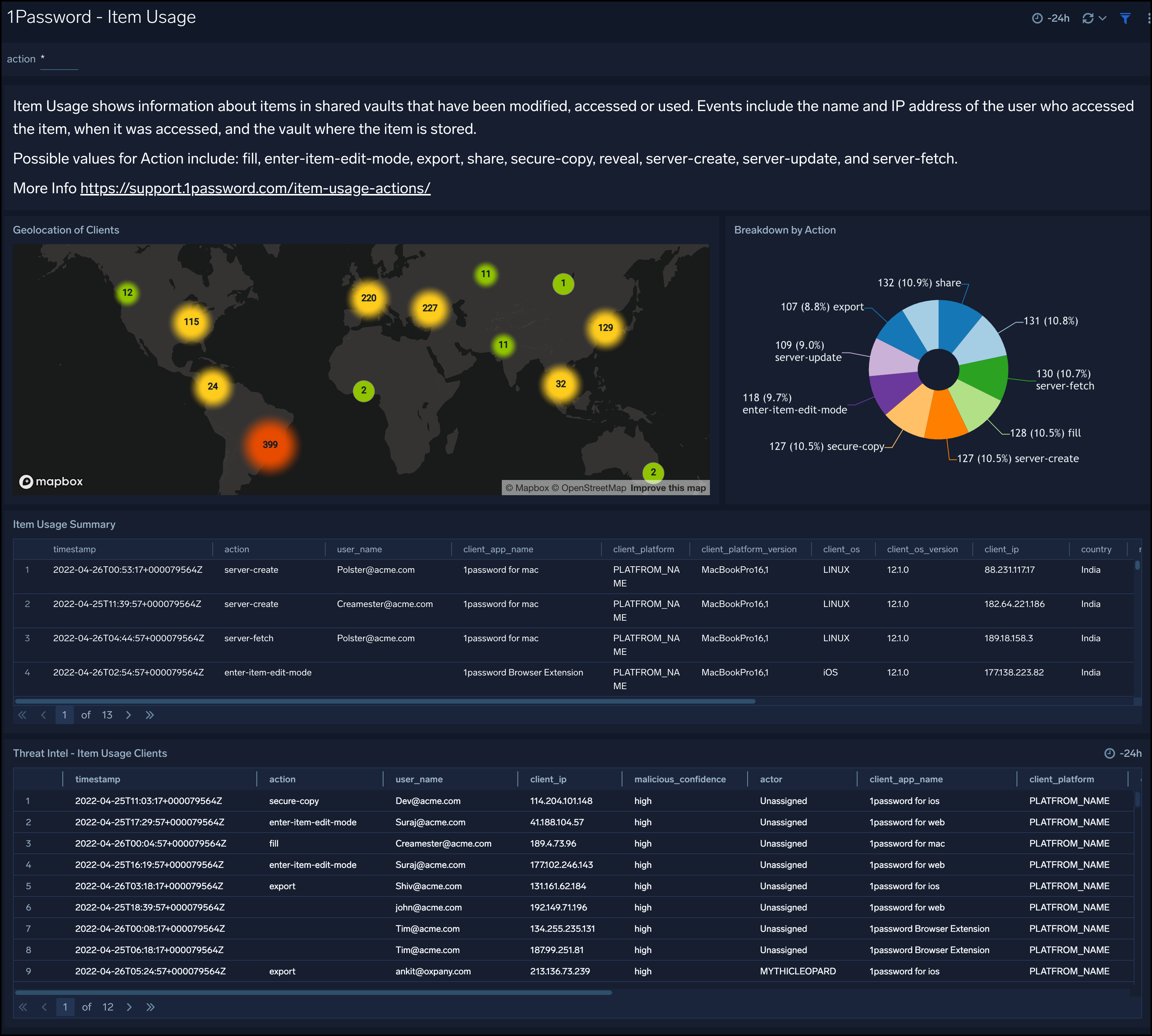
Item Usage
The 1Password - Item Usage dashboard shows information about items in shared vaults that have been modified, accessed, or used. This dashboard provides you geo-locations of clients who accessed items in the shared vault, it also provides threat intel analysis of client IPs to secure your vault access.
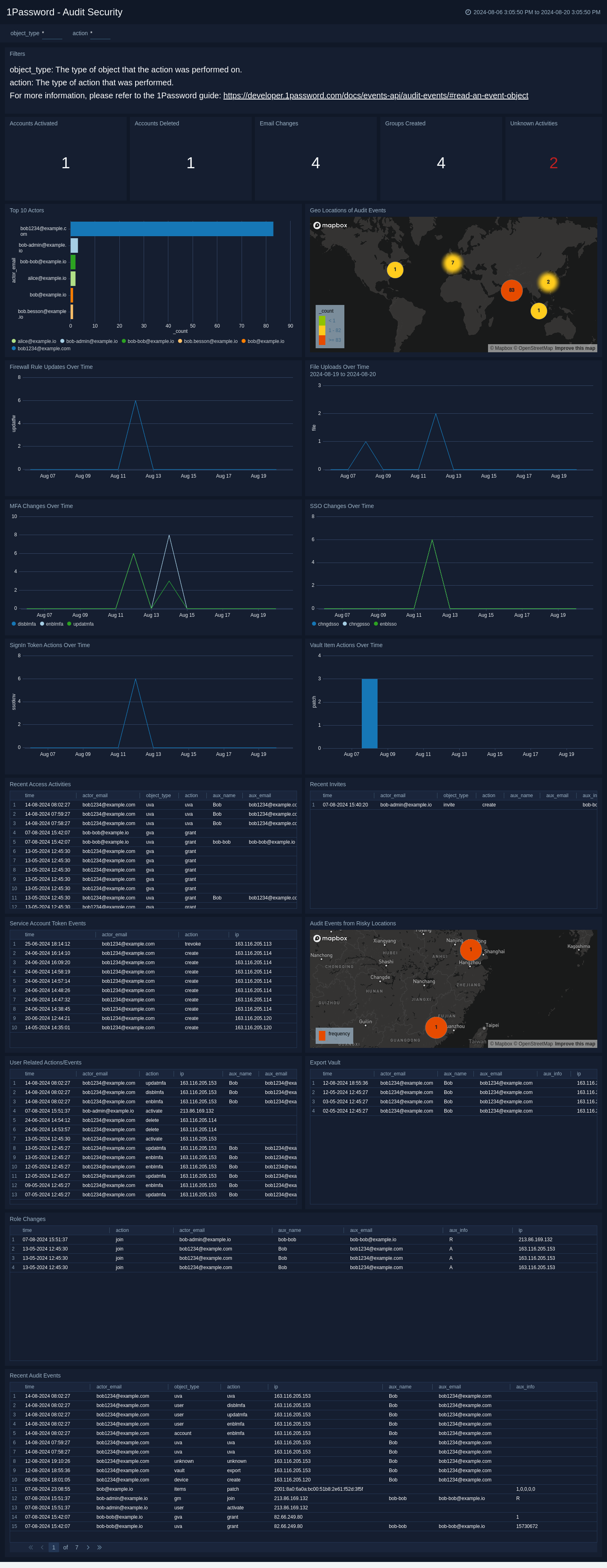
Audit Security
The 1Password - Audit Security dashboard provides a comprehensive view of security-related activities and monitors critical user activities by tracking key metrics such as account activations, deletions, email changes, and group creations. This dashboard helps you visualize the geographical distribution of audit events and highlights top actions, risky locations, and changes to security configurations like MFA and SSO. It includes detailed logs of recent access activities, role changes, and service account token events, ensuring comprehensive oversight of security events. This dashboard is essential for quick identification and rectification of potential security threats in 1Password.
Create monitors for 1Password app
From your App Catalog:
- From the Sumo Logic navigation, select App Catalog.
- In the Search Apps field, search for and then select your app.
- Make sure the app is installed.
- Navigate to What's Included tab and scroll down to the Monitors section.
- Click Create next to the pre-configured monitors. In the create monitors window, adjust the trigger conditions and notifications settings based on your requirements.
- Scroll down to Monitor Details.
- Under Location click on New Folder.
note
By default, monitor will be saved in the root folder. So to make the maintenance easier, create a new folder in the location of your choice.
- Enter Folder Name. Folder Description is optional.
tip
Using app version in the folder name will be helpful to determine the versioning for future updates.
- Click Create. Once the folder is created, click on Save.
1Password alerts
| Name | Description | Trigger Type (Critical / Warning / MissingData) | Alert Condition |
|---|---|---|---|
Privileged vault and group access control changes | This alert is fired when there are changes to privileged vault and group access control. | Critical | Count > 0 |
Login Exceeds Set Parameters | This alert is fired when the user tries login activities from more than one location. | Critical | Count > 1 |
Grant User Vault Access | This alert is fired when the user is granted access to a vault. | Critical | Count > 0 |
Changes to a User's MFA settings | This alert is fired when a user makes changes in the MFA settings. | Critical | Count > 5 |
Audit Events from Risky Locations | This alert is fired when an audit event is registered from an embargo location (Afghanistan, China, Cuba, North Korea, Iran, Libya, Nigeria, Sudan, Syria, and Yemen). | Critical | Count > 0 |
1Password tenant-level Changes | This alert is fired when changes are made to firewall rules, SSO settings, or a user sets up their 1Password account to unlock with SSO. | Critical | Count > 0 |
Upgrade/Downgrade the 1Password app (Optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the 1Password app (Optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.