Box

The Sumo Logic app for Box provides insight into user behavior patterns, monitors resources, and even tracks administrative activities. The app consists of three predefined Dashboards, providing visibility into your environment for real time analysis.
Log types
The Sumo Logic app for Box collects Box events, which are described in detail here.
Sample log messages
{
"source": {
"type": "user",
"id": "225980941",
"name": "First Last",
"login": "user@sumologic.com"
},
"created_by": {
"type": "user",
"id": "225980941",
"name": "First Last",
"login": "user@sumologic.com"
},
"created_at": "2016-12-15T11:08:58-08:00",
"event_id": "7988d00a-aca3-4454-9021-652477f4fa78",
"event_type": "LOGIN",
"ip_address": "1.1.1.1",
"type": "event",
"session_id": null,
"additional_details": null
}
{
"source": {
"type": "user",
"id": "262207389",
"name": "user",
"login": "luser@sumologic.com"
},
"created_by": {
"type": "user",
"id": "225980941",
"name": "first last",
"login": "user1@sumologic.com"
},
"created_at": "2016-12-14T16:09:33-08:00",
"event_id": "d82f1946-2c51-43fe-bfcc-3452f9e2f6ff",
"event_type": "DELETE_USER",
"ip_address": "1.1.1.1",
"type": "event",
"session_id": null,
"additional_details": null
}
Sample queries
_sourceCategory=box type "event_type" login
| json "created_at","ip_address","event_type","created_by.name","created_by.login" as messagetime,src_ip,event_type, src_user,src_login nodrop
| json "source.name","source.login","source.type" as dest_user,dest_login, item_type nodrop
| where event_type="FAILED_LOGIN"
| count as EventCount by src_user,src_login,src_ip | top 10 src_user,src_login,src_ip by EventCount
Set up collection
To set up Cloud-to-Cloud Integration Box Source for the Box app, follow the instructions provided. These instructions will guide you through the process of creating a source using the Box Source category, which you will need to use when installing the app. By following these steps, you can ensure that your Box app is properly integrated and configured to collect and analyze your Box data.
Installing the Box app
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Viewing the Box dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Most Next-Gen apps allow you to provide the scope at the installation time and are comprised of a key (
_sourceCategoryby default) and a default value for this key. Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the dataset queried by all panels. This eliminates the need to create multiple copies of the same dashboard with different queries.
Collaborations and Shares
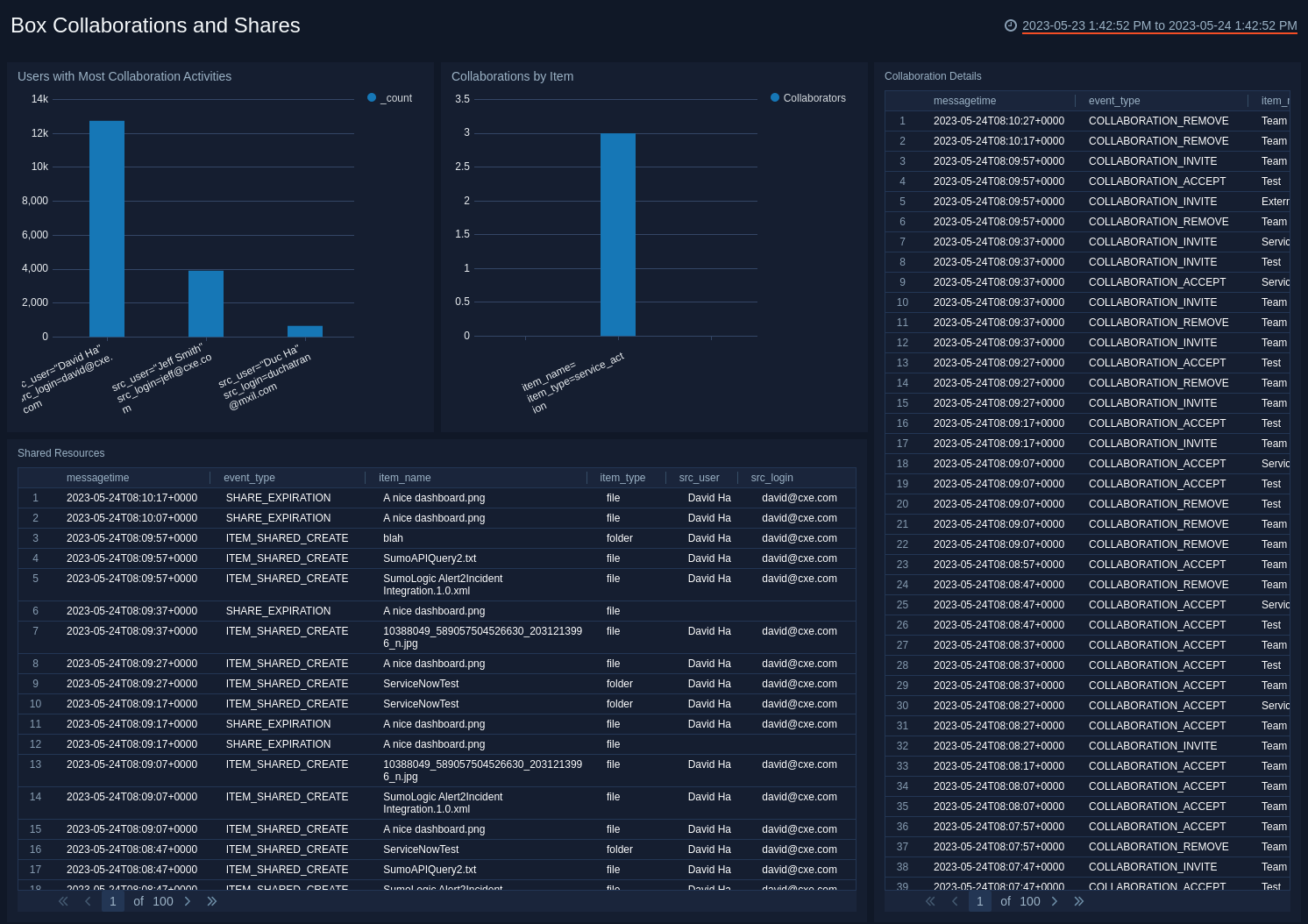
Users with Most Collaboration Activities. Shows the top users with the most collaboration activities and displays them as a column chart for the last 24 hours.
Collaborations by Item. Top items invoked in collaboration activities, displayed as a column chart for the last 24 hours.
Collaboration Details. Displays Box collaboration event information details in an aggregation table with columns for message time, event type, item name, source user, and source login for the last 24 hours.
Shared Resources. Displays the details of shared resources such as message time, event type, item name, item type, source user, and source login in an aggregation table for the last 24 hours.
Resource Access
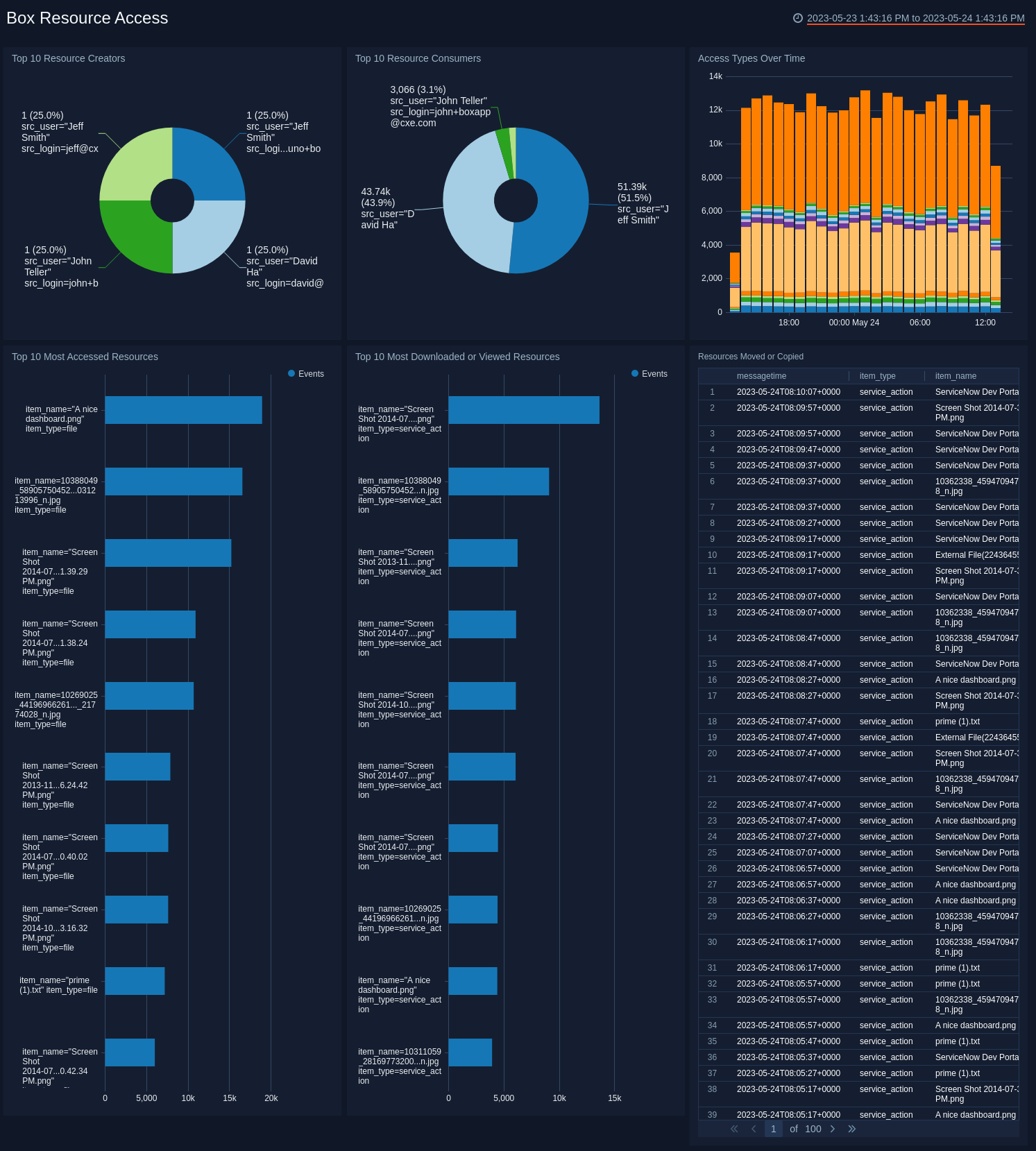
Top 10 Resource Creators. Displays the top 10 resource creators by showing details of Box upload or create events by user and count as a pie chart for the last 24 hours.
Top 10 Resource Consumers. Provides information on the top 10 resource consumers by showing Box download or preview events by user and event count as a pie chart for the last 24 hours.
Access Types Over Time. Shows access event types by count as a stacked column chart using timeslices of one hour on a timeline for the last 24 hours.
Top 10 Most Accessed Resources. Lists the top 10 most accessed resources by name in a bar chart for the last 24 hours.
Top 10 Most Downloaded or Viewed Resources. Lists the top 10 most downloaded or viewed resources by name in a bar chart for the last 24 hours.
Resources Moved or Copied. Displays details on resources that have been copied or moved such as message time, item type, item name, event type, source login, and source user in an aggregation table for the last 24 hours.
User Monitoring
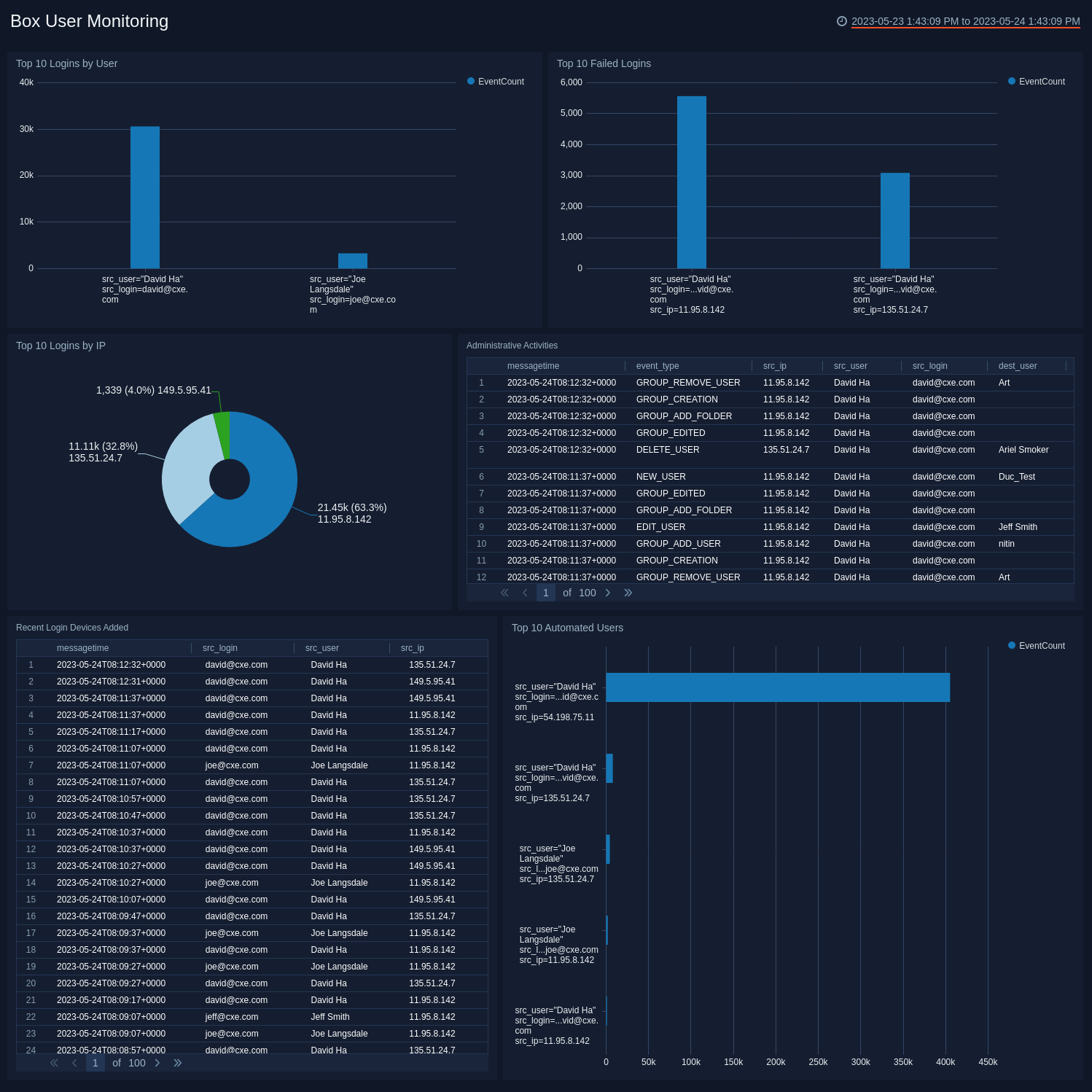
Top 10 Logins by User. Displays details about the top 10 users with the most logins, such as source user, source login, and event count in an aggregation table for the last 24 hours.
Top 10 Logins by IP. Shows the top 10 IP addresses that logged into the account in a pie chart for the last 24 hours.
Top 10 Failed Logins. Provides details on failed logins by user and event count in a column chart for the last 24 hours.
Administrative Activities. Displays administrative details such as message time, event type, source IP address, source user, source login, destination user, and destination login in an aggregation table for the last 24 hours.
Recent Login Devices Added. Reports details on recently added login devices such as message time, source login, source user, and source IP address in an aggregation table for the last 24 hours.
Top 10 Automated Users. Displays information on top automated users by user and event count in a column chart for the last 24 hours. Automated users are devices or applications that login through a user account.
Upgrade/Downgrade the Box app (Optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Box app (Optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.