Vectra

The Vectra app offers comprehensive visibility into security threats detected across networks, cloud environments, and endpoints. It consolidates threat intelligence from multiple sources, categorizing detections by their severity, type, and behavior, while providing detailed contextual data to accelerate investigations. With interactive dashboards and targeted monitoring tools, security teams can track trends, pinpoint high-risk activities, and measure remediation effectiveness. By combining threat scoring, detection timelines, and enriched metadata, the app empowers proactive threat hunting, rapid incident response, and continuous improvement of security posture.
This app includes built-in monitors. For details on creating custom monitors, refer to the Create monitors for Vectra app.
Log types
This app uses Sumo Logic’s Vectra Source to collect detections from the Vectra platform.
Sample log message
{
"summary": {
"user_agents": [
"Microsoft Azure CLI",
"Microsoft Azure CLI"
],
"browser": [
"Chrome 138.0.0",
"Chrome"
],
"operating_system": [
"Linux",
"Linux"
],
"workloads": [
"Azure Resource Manager",
"AzureActiveDirectory"
],
"operations": [
"UserLoggedIn"
],
"src_ips": [
"80.117.40.124"
],
"description": "This account was seen using a scripting engine to access services in Azure AD which is unusual for the account. Unusual usage of scripting engines in Azure AD and Microsoft 365 can be indicative of a compromised account."
},
"data_source": {
"type": "o365",
"connection_name": "M365-Demo",
"connection_id": "s9s9c5cj"
},
"filtered_by_rule": false,
"src_account": {
"id": 1034,
"name": "O365:demolab.vectra.ai",
"url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/accounts/1034",
"threat": 30,
"certainty": 90,
"privilege_level": null,
"privilege_category": null
},
"threat": 70,
"last_timestamp": "2025-08-12T18:29:21Z",
"is_targeting_key_asset": false,
"sensor_name": "Vectra X",
"filtered_by_ai": false,
"id": 3586,
"c_score": 60,
"src_ip": null,
"assigned_date": null,
"filtered_by_user": false,
"is_custom_model": false,
"assigned_to": null,
"detection_category": "lateral_movement",
"note_modified_timestamp": null,
"created_timestamp": "2025-08-12T18:53:29Z",
"note": null,
"is_marked_custom": false,
"url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/detections/3586",
"state": "active",
"detection": "Azure AD Unusual Scripting Engine Usage",
"triage_rule_id": null,
"groups": [],
"category": "lateral_movement",
"first_timestamp": "2025-08-12T18:29:21Z",
"certainty": 60,
"t_score": 70,
"tags": [],
"note_modified_by": null,
"detection_url": "https://37373829274.cc1.portal.vectra.ai/api/v3.3/detections/3586",
"description": null,
"notes": [],
"detection_type": "Azure AD Unusual Scripting Engine Usage",
"custom_detection": null,
"sensor": "s9s9c5cj",
"targets_key_asset": false,
"is_triaged": false,
"src_host": null,
"type": "account",
"grouped_details": [
{
"workload": "Azure Resource Manager",
"user_agent": "Microsoft Azure CLI",
"operating_system": "Linux",
"browser": "Chrome 138.0.0",
"operations": [
"UserLoggedIn"
],
"operations_count": 1,
"src_ips": [
"80.117.40.124"
],
"first_timestamp": "2025-08-12T18:29:21Z",
"last_timestamp": "2025-08-12T18:29:21Z"
},
{
"workload": "AzureActiveDirectory",
"user_agent": "Microsoft Azure CLI",
"operating_system": "Linux",
"browser": "Chrome",
"operations": [
"UserLoggedIn"
],
"operations_count": 1,
"src_ips": [
"80.117.40.124"
],
"first_timestamp": "2025-08-12T18:29:21Z",
"last_timestamp": "2025-08-12T18:29:21Z"
}
]
}
Sample queries
_sourceCategory="Labs/Vectra"
| json "id","last_timestamp","first_timestamp","state","t_score","c_score","category","type","summary.operations[*]","grouped_details[*].src_ips[*]","detection_url","assigned_to","detection","certainty","src_account.id","src_account.name","src_account.url","src_account.threat","src_account.certainty" as id,last_timestamp,first_timestamp,state,t_score,c_score,category,type,operations,src_ips,detection_url,assigned_to,detection,certainty,src_account_id,src_account_name,src_account_url,src_account_threat,src_account_certainty nodrop
| if (t_score>=70,"critical",if(t_score>=41 and t_score<=69, "medium", if(t_score<=40,"low","unknown"))) as severity
// global filters
| where isNull(state) or state matches "{{state}}"
| where isNull(category) or category matches "{{category}}"
| where isNull(severity) or severity matches "{{severity}}"
| where isNull(type) or type matches "{{type}}"
| where isNull(certainty) or certainty matches "{{certainty}}"
// panel specific
| count by id
| count
Collection configuration and app installation
Depending on the set up collection method, you can configure and install the app in three ways:
- Create a new collector and install the app. Create a new Sumo Logic Cloud-to-Cloud (C2C) source under a new Sumo Logic Collector and later install the app, or
- Use an existing collector and install the app. Create a new Sumo Logic Cloud-to-Cloud (C2C) source under an existing Sumo Logic Collector and later install the app, or
- Use existing source and install the app. Use your existing configured Sumo Logic Cloud-to-Cloud (C2C) source and install the app.
Use the Cloud-to-Cloud Integration for Vectra to create the source and use the same source category while installing the app. By following these steps, you can ensure that your Vectra app is properly integrated and configured to collect and analyze your Vectra data.
Create a new collector and install the app
To set up collection and install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- In the Set Up Collection section of your respective app, select Create a new Collector.
- Collector Name. Enter a Name to display the Source in the Sumo Logic web application. The description is optional.
- Timezone. Set the default time zone when it is not extracted from the log timestamp. Time zone settings on Sources override a Collector time zone setting.
- (Optional) Metadata. Click the +Add Metadata link to add a custom log Metadata Fields. Define the fields you want to associate, each metadata field needs a name (key) and value.
 A green circle with a checkmark is shown when the field exists and is enabled in the Fields table schema.
A green circle with a checkmark is shown when the field exists and is enabled in the Fields table schema. An orange triangle with an exclamation point is shown when the field doesn't exist, or is disabled in the Fields table schema. In this case, you'll see an option to automatically add or enable the nonexistent fields to the Fields table schema. If a field is sent to Sumo Logic but isn’t present or enabled in the schema, it’s ignored and marked as Dropped.
An orange triangle with an exclamation point is shown when the field doesn't exist, or is disabled in the Fields table schema. In this case, you'll see an option to automatically add or enable the nonexistent fields to the Fields table schema. If a field is sent to Sumo Logic but isn’t present or enabled in the schema, it’s ignored and marked as Dropped.
- Click Next.
- Configure the source as specified in the
Infobox above, ensuring all required fields are included. - In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Use an existing collector and install the app
To set up the source in the existing collector and install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- In the Set Up Collection section of your respective app, select Use an existing Collector.
- From the Select Collector dropdown, select the collector that you want to set up your source with and click Next.
- Configure the source as specified in the
Infobox above, ensuring all required fields are included. - In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Use an existing source and install the app
To skip collection and only install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- In the Set Up Collection section of your respective app, select Skip this step and use existing source and click Next.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Viewing the Vectra dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Most Next-Gen apps allow you to provide the scope at the installation time and are comprised of a key (
_sourceCategoryby default) and a default value for this key. Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the dataset queried by all panels. This eliminates the need to create multiple copies of the same dashboard with different queries.
Overview
The Vectra - Overview dashboard offers a consolidated, real-time summary of all detected threats, enabling security teams to quickly assess the current threat landscape. It breaks down detections by severity(critical, medium, low), category, type, and resolution state, providing both counts and visual distributions. Time-based trend charts reveal spikes or patterns in threat activity, while geo-location maps identify where hosts are operating, including those in embargoed regions that may pose compliance risks. Additional panels highlight the top-impacted users, frequently targeted operations, and relevant detection sources, with direct links for in-depth investigation. This dashboard serves as the central entry point for monitoring threats, understanding scope, and prioritizing security actions.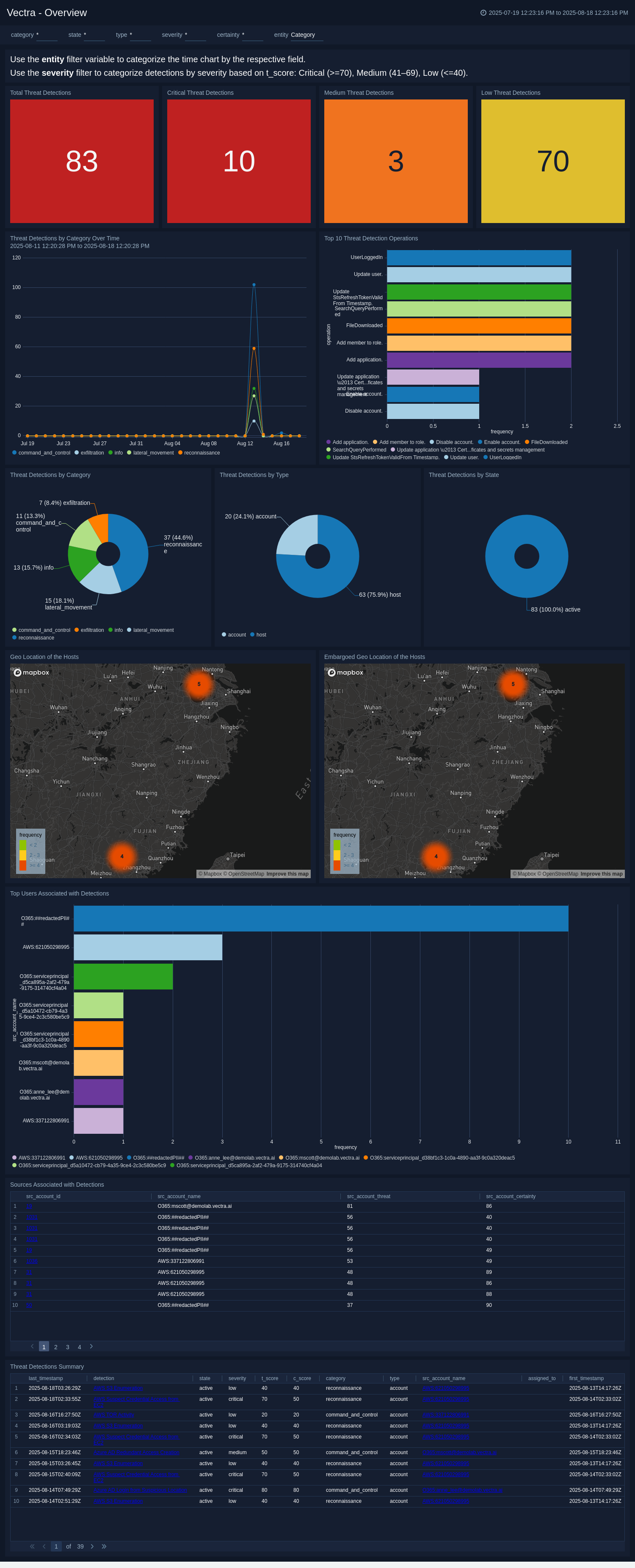
Security
The Vectra - Security dashboard focuses on advanced and high-severity threats that require immediate attention. It highlights critical threat detections, command-and-control activities, and account-based privilege escalation attempts, as well as anomalies in Azure AD operations. Persistent threats are tracked with metrics on time-to-remediation, enabling teams to assess response efficiency. Each panels are designed to surface patterns that indicate targeted attacks, lateral movement, or ongoing compromise attempts. By consolidating these high-priority insights, the dashboard helps security analysts quickly isolate urgent incidents, understand attack context, and coordinate effective containment and remediation strategies.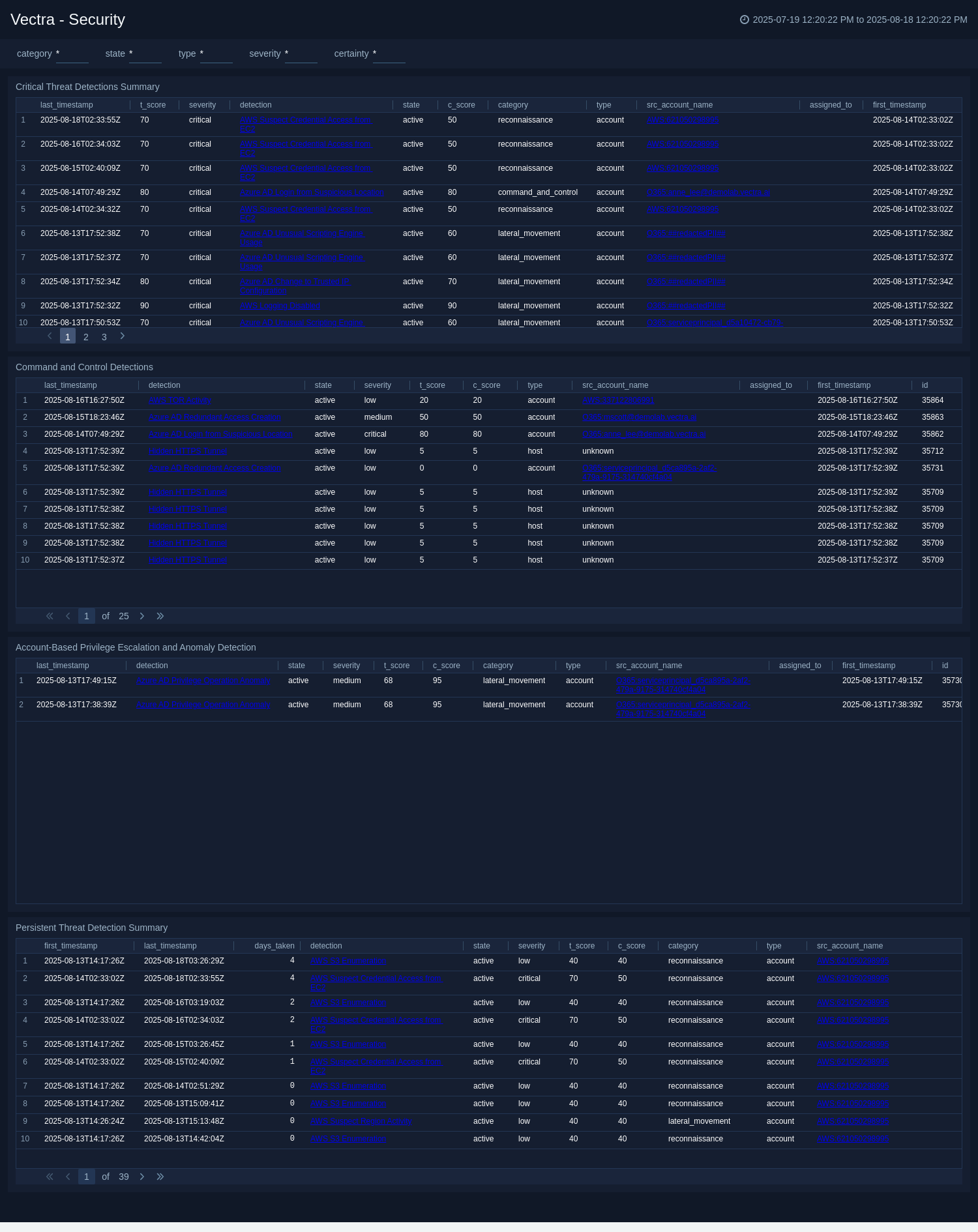
Create monitors for the Vectra app
From your App Catalog:
- From the Sumo Logic navigation, select App Catalog.
- In the Search Apps field, search for and then select your app.
- Make sure the app is installed.
- Navigate to What's Included tab and scroll down to the Monitors section.
- Click Create next to the pre-configured monitors. In the create monitors window, adjust the trigger conditions and notifications settings based on your requirements.
- Scroll down to Monitor Details.
- Under Location click on New Folder.
note
By default, monitor will be saved in the root folder. So to make the maintenance easier, create a new folder in the location of your choice.
- Enter Folder Name. Folder Description is optional.
tip
Using app version in the folder name will be helpful to determine the versioning for future updates.
- Click Create. Once the folder is created, click on Save.
Vectra alerts
| Name | Description | Trigger Type (Critical / Warning / MissingData) | Alert Condition |
|---|---|---|---|
Critical Threat Detections | This alert is triggered when one or more threat detections with a threat score above 70 are identified. These detections indicate the most severe security risks and necessitate immediate investigation and remediation to prevent potential compromise or damage. | Critical | Count > 0 |
Upgrading/Downgrading the Vectra app (Optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Vectra app (Optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.