Threat Intel Quick Analysis

The Threat Intel Quick Analysis app correlates threat intelligence data with your own log data, providing security analytics that helps you to detect threats in your environment, while also protecting against sophisticated and persistent cyber-attacks. The Threat Intel Quick Analysis app scans selected logs for threats based on IP, URL, domain, SHA-256 hashes, and email.
Log types
The Threat Intel Quick Analysis app can be used for any type of logs, regardless of format. Ideal log sources should include IP, URL, domain, SHA-256 hashes, and/or email information.
Installing the Threat Intel Quick Analysis app
This app contains generic regex expressions and thus may not perform well at very large scale. Once you are familiar with Sumo Logic, you can apply performance optimization techniques as described in Threat Intel optimization. Alternatively, you can run this app on smaller and more specific data streams.
This section provides instructions on how to install the Threat Intel Quick Analysis app, and examples of each of dashboards. The preconfigured searches and dashboards provide easy-to-access visual insights into your data.
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Threat Intel optimization
The Threat Intel Quick Analysis app provides baseline queries. You can further optimize and enhance these queries for the log and events types being scanned for threats. To see the queries, open a dashboard in the app, click the three-dot kebab in the upper-right corner of the dashboard panel, and select Open in Log Search.
Use the following guidelines to customize your Threat Intel queries:
- Filter out unwanted logs before you use lookup operator
- Use keywords
- Use the where operator
- Use general search optimization rules
For example:
_sourceCategory=cylance "IP Address"
| parse regex "(?<ip_address>\b\d{1,3}\.\d{1,3}\.\d{1,3}\.\d{1,3})"
| where !isNull(ip_address)
| where ip_address != "0.0.0.0" and ip_address != "127.0.0.1"
| lookup type, actor, raw, threatlevel as malicious_confidence from sumo://threat/cs on threat=ip_address
Field Extraction Rule
Use Field Extraction Rules (FER) to parse fields from your log messages at the time the messages are ingested, which eliminates the need to parse fields at the query level. Use these parsed fields along with lookup operator.
- Create the FER For example, for Cylance Security Events, create and use the following Field Extraction Rule:
parse "Event Type: *, Event Name: *, Device Name: *, IP Address: (*, *), File Name: *, Path: *, Drive Type: *, SHA256: *, MD5: *, Status: *, Cylance Score: *, Found Date: *, File Type: *, Is Running: *, Auto Run: *, Detected By: *" as event_type,event_name,device_name,src_ip,dest_ip,file_name,path,drive_type,sha,md5,status,score,found,file_type,isRunning,autoRun,detected - Customize your query so you can use parsed fields from FER with the lookup operator, where src_ip is the parsed field from FER (see step # 1). For example:
| lookup type, actor, raw, threatlevel as malicious_confidence from sumo://threat/cs on threat=src_ip
| json field=raw "labels[*].name" as label_name nodrop
| replace(label_name, "\\/","->") as label_name
| replace(label_name, "\""," ") as label_name
| where type="ip_address" and !isNull(malicious_confidence)
| if (isEmpty(actor), "Unassigned", actor) as Actor
| count as threat_count by src_ip, malicious_confidence, Actor, _source, label_name
| sort by threat_count
Scheduled view
Use scheduled views with the threat lookup operator to find threats. Scheduled view reduces aggregate data down to the bare minimum, so they contain only the raw results that you need to generate your data. Queries that run against scheduled views return search results much faster because the data is pre-aggregated before the query is run. And a scheduled view query runs continuously, once per minute.
- Create a scheduled view. For example, for Cylance, create a scheduled view, cylance_threat:
_sourceCategory=cylance | lookup type, actor, raw, threatlevel as malicious_confidence from sumo://threat/cs on threat=src_ip
| json field=raw "labels[*].name" as label_name nodrop
| replace(label_name, "\\/","->") as label_name
| replace(label_name, "\""," ") as label_name
| where type="ip_address" and !isNull(malicious_confidence)
| if (isEmpty(actor), "Unassigned", actor) as Actor
| lookup latitude, longitude, country_code, country_name, region, city, postal_code, area_code, metro_code from geo://default on ip = src_ip
| count as threat_count by src_ip, malicious_confidence, Actor, _source, label_name, city, country_name, raw
- Now, you can run your Threat Intel query on top of this view:
_view=cylance_threat
| count by src_ip
JSON configuration object
malicious_confidence
Data Type: string
Description: Indicates a confidence level by which an indicator is considered to be malicious. For example, a malicious file hash may always have a value of high while domains and IP addresses will very likely change over time. The malicious confidence level is also represented under the labels list in the JSON data structure.
Once an indicator has been marked with a malicious confidence level, it continues to have that confidence level value until updated by CrowdStrike. If you think there is a false positive, please file a Support ticket, and we'll work with CrowdStrike to investigate the IOC in question and update the threat details.
Values:
- high
- medium
- low
- unverified—This indicator has not been verified by a CrowdStrike Intelligence analyst or an automated system.
- null—Indicates that Sumo Logic has no information about the threat record.
published_date
Data Type: Timestamp in standard Unix time, UTC.
Description: This is the date the indicator was first published.
last_updated
Data Type: Timestamp in standard Unix time, UTC.
Description: This is the date the indicator was last updated in CrowdStrike internal database.
malware_family
Data Type: string
Description: Indicates the malware family an indicator has been associated with. An indicator may be associated with more than one malware family. The malware family list is also represented under the labels list in the JSON data structure.
kill_chain
Data Type: string
Description: The point in the kill chain at which an indicator is associated. The kill chain list is also represented under the labels list in the JSON data structure.
Values:
- reconnaissance—This indicator is associated with the research, identification, and selection of targets by a malicious actor.
- weaponization—This indicator is associated with assisting a malicious actor create malicious content.
- delivery—This indicator is associated with the delivery of an exploit or malicious payload.
- exploitation—This indicator is associated with the exploitation of a target system or environment.
- installation—This indicator is associated with the installation or infection of a target system with a remote access tool or other tool allowing for persistence in the target environment.
- c2 (Command and Control)—This indicator is associated with malicious actor command and control.
- actionOnObjectives—This indicator is associated with a malicious actor's desired effects and goals.
labels
Data Type: string
Description: The Intel Indicators API provides additional context around an indicator via the labels list. Some of these labels, such as malicious_confidence are accessible via the top-level data structure. All labels, including their associated timestamps, will be accessible via the labels list. The url string will look like: https://intelapi.crowdstrike.com/indicator/v1/search/labels?equal=DomainType/DynamicDNS.
| IOC Type | Values |
|---|---|
| DomainType |
|
| EmailAddressType |
EmailAddressType/DomainRegistrant—Email address has been supplied in the registration information for known malicious domains. EmailAddressType/SpearphishSender—Email address has been used to send spearphishing emails. |
| IntelNews: The Intel Flash Report ID an indicator is associated with (For example, IntelNews/NEWS-060520151900). | |
| IPAddressType |
|
| Status |
|
| Target | The activity associated with this indicator is known to target the indicated vertical sector, which could be any of the following:
|
| ThreatType |
|
Vulnerability | The CVE-XXXX-XXX vulnerability the indicator is associated with (e.g., https://intelapi.crowdstrike.com/indicator/v1/search/labels?equal=vulnerability/CVE-2012-0158). |
Viewing Threat Intel Quick Analysis dashboards
All dashboards include filters that you can use in Interactive Mode for further analysis of your Threat Intel Quick Analysis data. Because the Threat Intel Quick Analysis has the most bearing on recent threats, most panels are set to the 15 minute time range. You can adjust time ranges as needed.
Live mode and real-time queries are not supported for dashboards at this time.
Overview
See the frequency of Domain threats by Actor, Log Source, Malicious Confidence, and view trends over time.
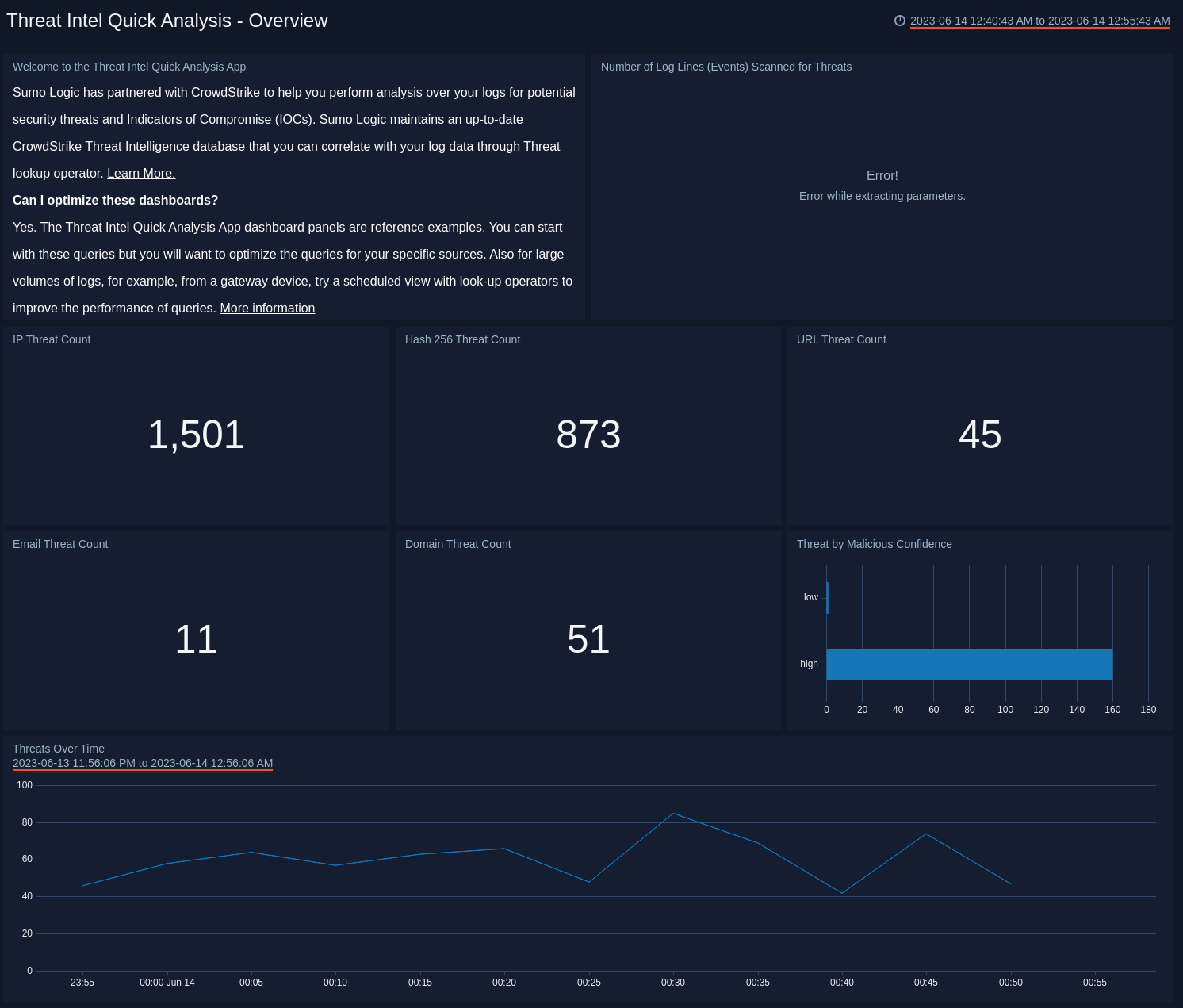
- Welcome to the Threat Intel Quick Analysis App. Informational panel to help you find information on working with the threat intelligence database.
- Number of Log Lines (Events) Scanned for Threats. Count of log lines scanned across all selected sources for the last 15 minutes.
- IP Threat Count. Count of threats related to malicious IPs, for the last 15 minutes.
- File Name Threat Count. Count of threats related to malicious file names, for the last 15 minutes.
- URL Threat Count. Count of threats related to malicious URLs, for the last 15 minutes.
- Email Threat Count. Count of threats related to malicious email addresses, for the last 15 minutes.
- Domain Threat Count. Count of threats related to malicious domains, for the last 15 minutes.
- Threats by Malicious Confidence. Qualifies all threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
Domain
See the frequency of Domain threats by Actor, Log Source, Malicious Confidence, and view trends over time.
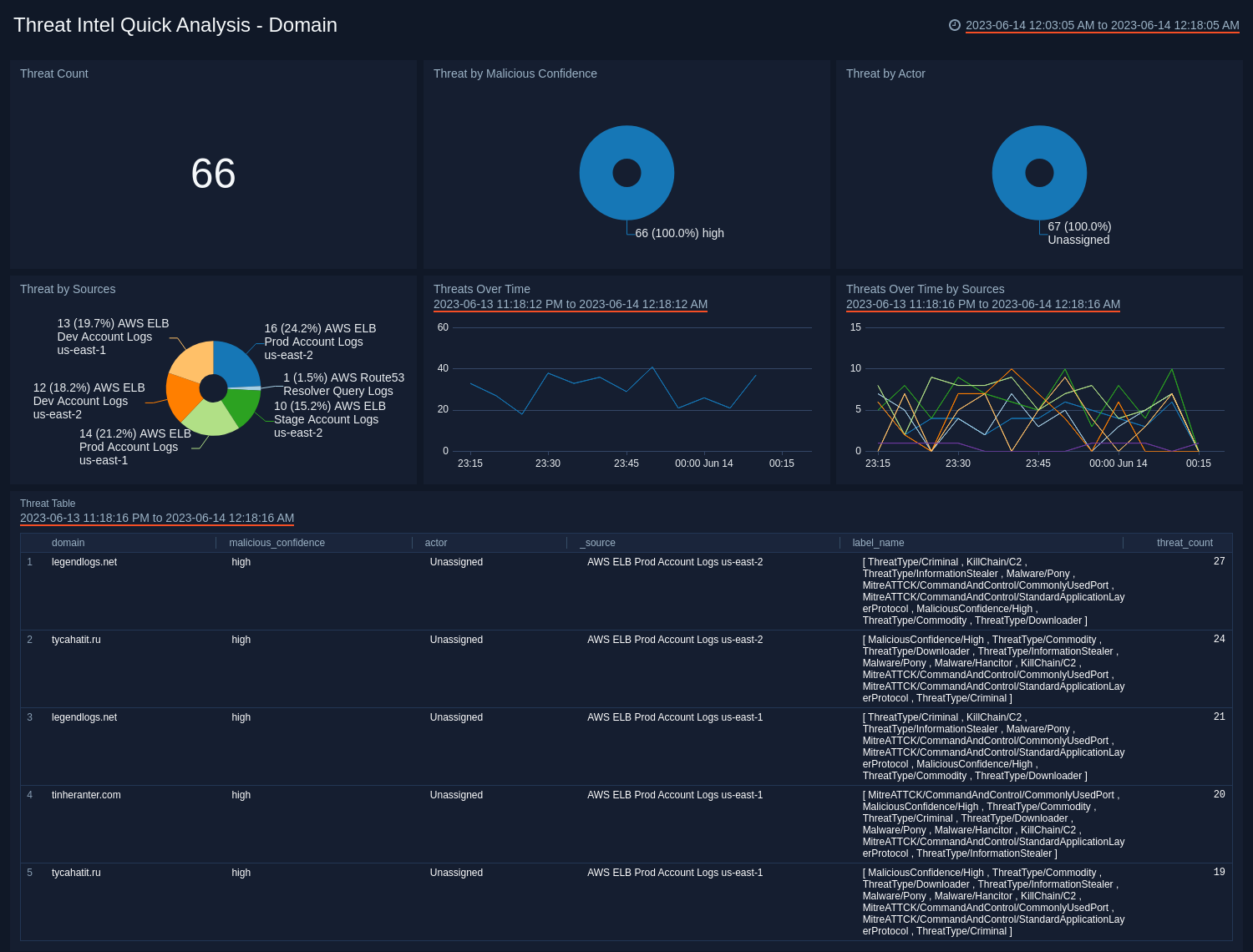
- Threat Count. Count of threats related to malicious domains, for the last 15 minutes.
- Threats by Malicious Confidence. Qualifies domain threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
- Threats by Actor. Count of threats related to malicious domains, broken down by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
- Threats by Sources. Count of threats related to malicious domains, broken by Sources, for the last 15 minutes.
- Threats Over Time. Trends of domain threats over time for the last 60 minutes.
- Threats Over Time by Sources. Trends of domain threats over time, broken by Sources for the last 60 minutes.
- Threats Table. Listing of all domain threats, including Malicious Confidence, Actors and Sources.
Email
See the frequency of Email threats by Actor, Log Source, Malicious Confidence, and view trends over time.
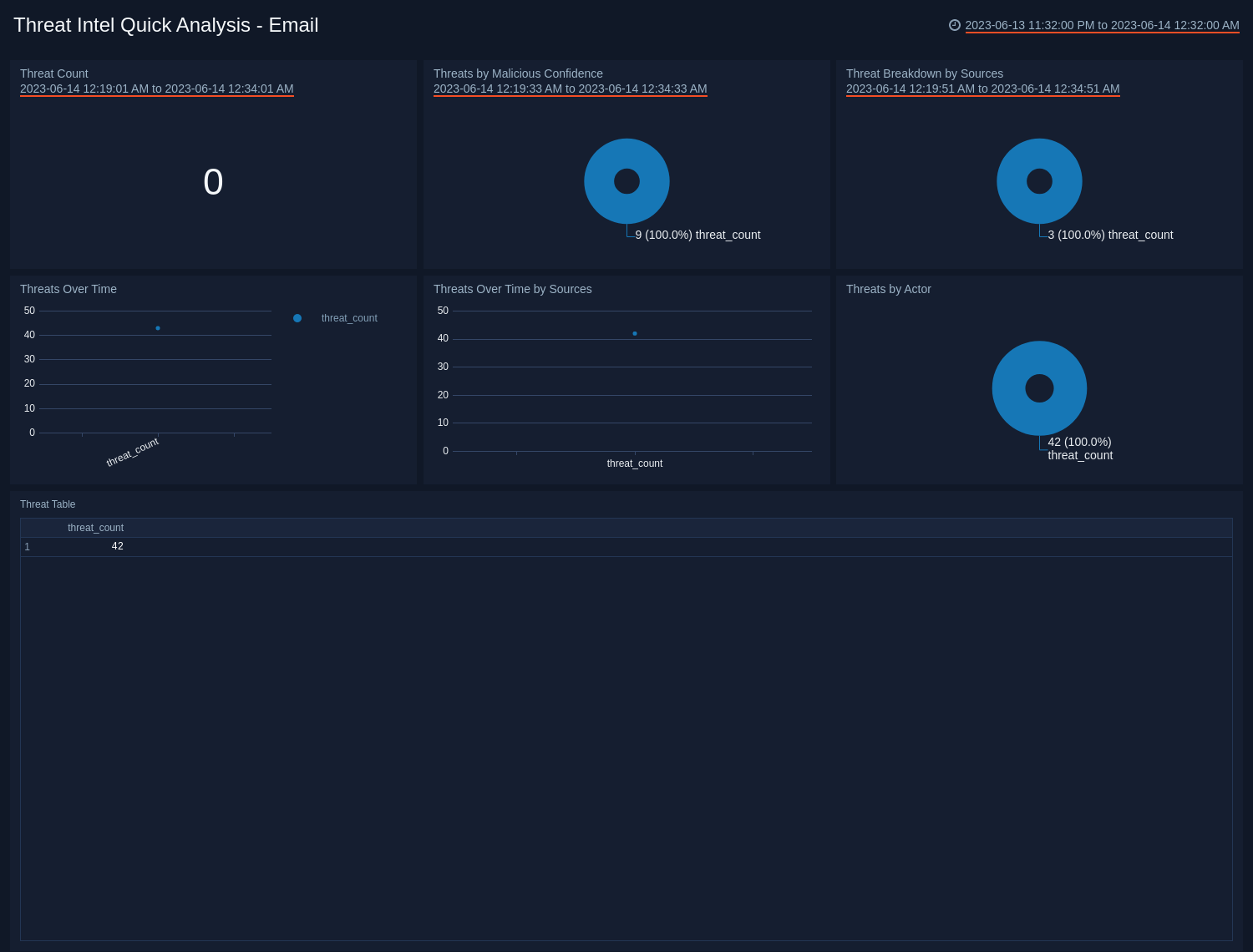
- Threat Count. Count of threats related to malicious emails addresses, for the last 15 minutes.
- Threats by Malicious Confidence. Qualifies email address threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
- Threat Breakdown by Sources. Count of threats related to malicious email addresses, broken by Sources, for the last 15 minutes.
- Threats Over Time. Trends of email address threats over time for the last 60 minutes.
- Threats Over Time by Sources. Trends of email address threats over time, broken by Sources for the last 60 minutes.
- Threats by Actor. Count of threats related to malicious email addresses, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
- Threats Table. Listing of all domain threats, including Malicious Confidence, Actors and Sources.
IP
See the frequency of IP threats by Actor, Log Source, Malicious Confidence, and view trends over time.
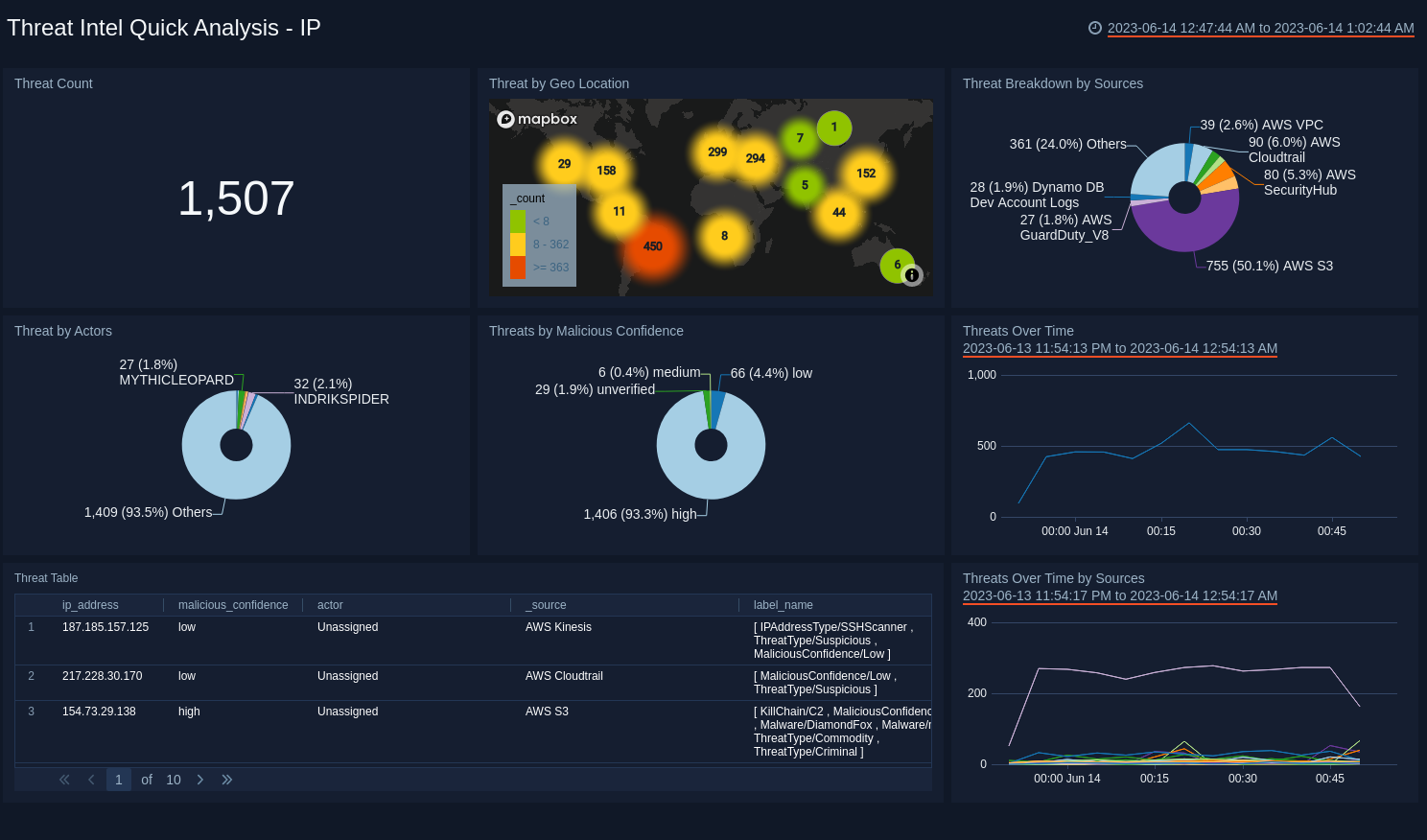
- Threat Count. Count of threats related to malicious IPs, for the last 15 minutes.
- Threats by Geo Location. Count of threats related to malicious IPs, broken by geo location, for the last 15 minutes.
- Threat Breakdown by Sources. Count of threats related to malicious IPs, broken by Sources, for the last 15 minutes.
- Threats by Malicious Confidence. Qualifies IP threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
- Threats by Actors. Count of threats related to malicious IPs, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
- Threats Over Time. Trends of IP threats over time for the last 60 minutes.
- Threats Table. Listing of all IP threats, including Malicious Confidence, Actors and Sources.
- Threats Over Time by Sources. Trends of IP threats over time, broken by Sources for the last 60 minutes.
URL
See the frequency of URL threats by Actor, Log Source, Malicious Confidence, and view trends over time.
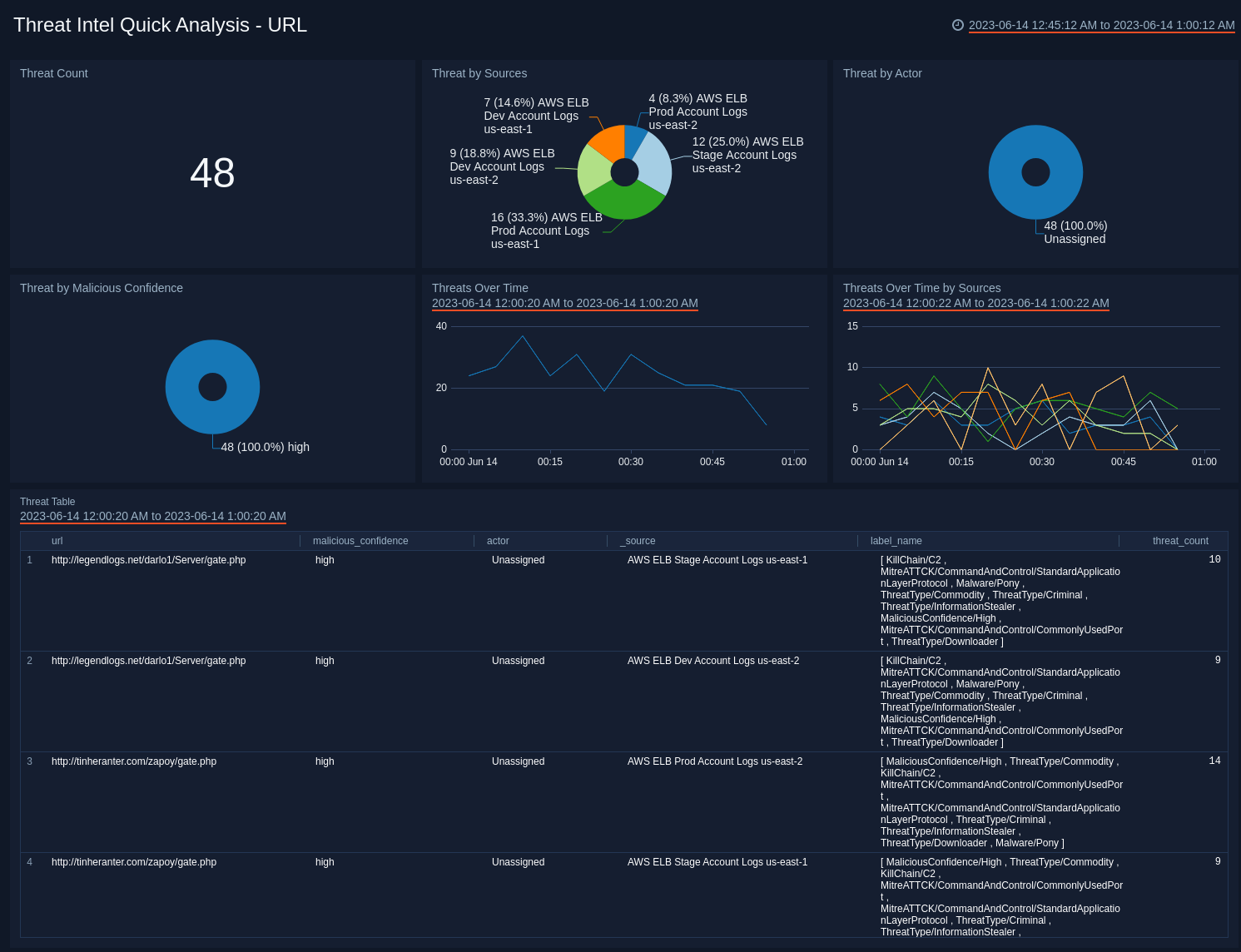
- Threat Count. Count of threats related to malicious URLs, for the last 15 minutes.
- Threats by Sources. Count of threats related to malicious URLs, broken by Sources, for the last 15 minutes.
- Threats by Actors. Count of threats related to malicious URLs, broken by Actors, for the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
- Threats by Malicious Confidence. Qualifies URLP threats into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine.
- Threats Over Time. Trends of URL threats over time for the last 60 minutes.
- Threats Over Time by Sources. Trends of URL threats over time, broken by Sources for the last 60 minutes.
- Threat Table. Listing of threats identified by URL, including information on Malicious Confidence, Actors, Source, and count.
Hash 256
See the frequency of SHA-256 threats by Actor, Log Source, Malicious Confidence, and view trends over time.
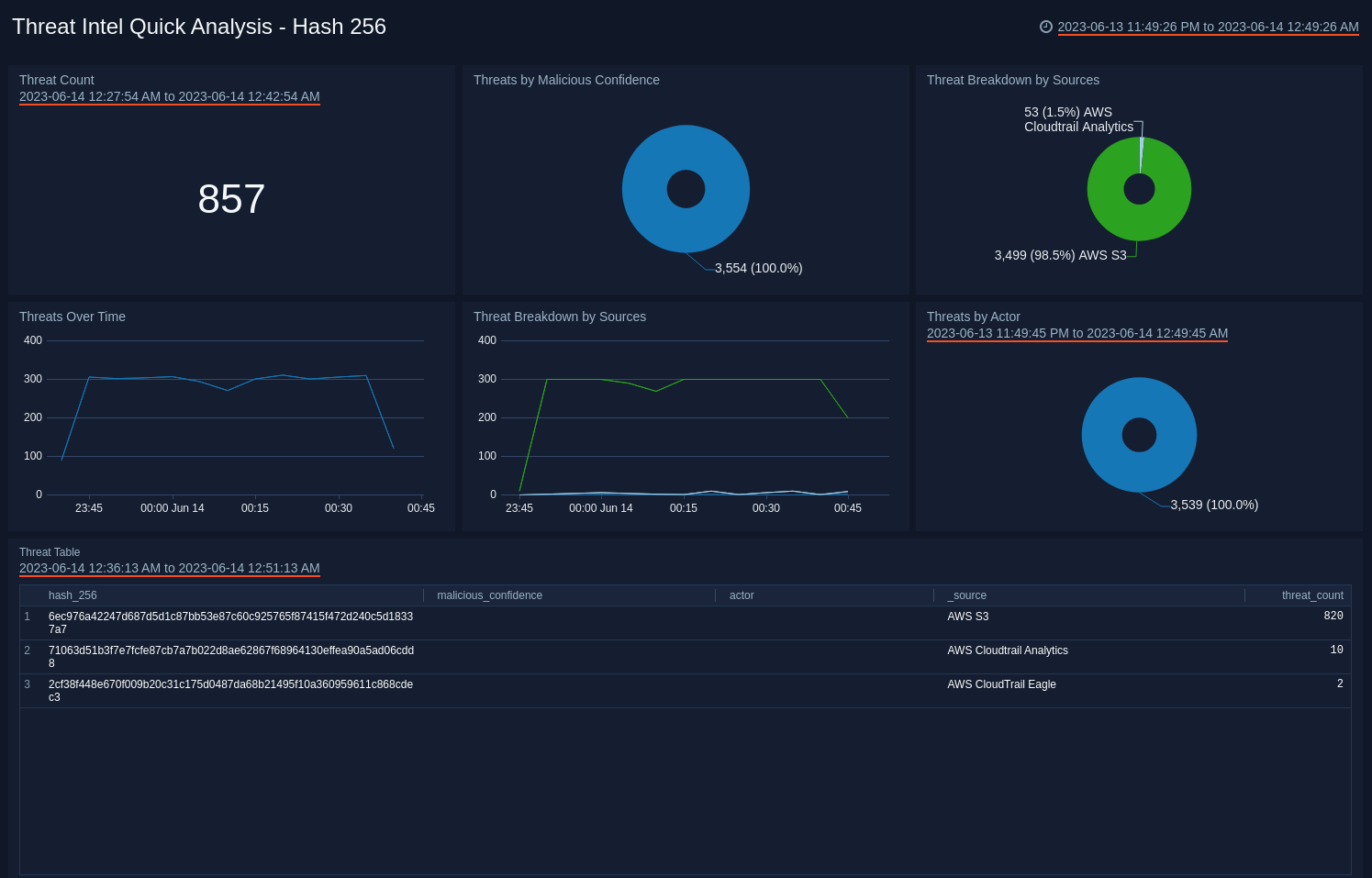
- Threat Count. Count of total SHA-256 threats over the last 15 minutes.
- Threats by Malicious Confidence. Qualifies SHA-256 threats for the last 60 minutes into High, Medium, Low, Unverified, according to Sumo Logic's machine learning engine and displayed as a pie chart.
- Threat Breakdown by Sources. Pie chart of SHA-256 threats over the last 60 minutes broken down by source.
- Threats Over Time. Line chart of the number of SHA-256 threats over the last 60 minutes.
- Threat Breakdown by Source. Line chart of the number of SHA-256 threats over the last 60 minutes, broken down by source.
- Threats by Actor. Identifies Actors, if any, that can be attributed to SHA-256 threats over the last 15 minutes. Actors are identified individuals, groups or nation-states associated to threats.
- Threat Table. Aggregation Table of SHA-256 threats over the last 15 minutes.
Upgrading the Threat Intel Quick Analysis app (Optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Threat Intel Quick Analysis app (optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.