Trend Micro Deep Security
The Trend Micro Deep Security app works with system and security events to monitor event history such as anti-malware, IPS, web reputation, firewall, integrity and log inspection events. The app analyzes security events from both on-premises and cloud-based Trend Micro Deep Security products.
Log types
There are two types of Deep Security events:
- System Events
- Security Events
For complete details on configuring your Deep Security system for use with Sumo Logic, see the White Paper, “Deep Security Integration with Sumo Logic”.
Collect on-premises logs for the Trend Micro Deep Security app
This section provides instructions for configuring on-prem log collection for the Trend Micro Deep Security app, as well as examples of relevant log and query samples.
Configure Collector and Sources
To collect logs for Deep Security, do the following:
- Configure a Installed Collector.
- Configure a Syslog Source.
When you configure the Syslog Sources, for Protocol, select UDP.
Configure Deep Security System Event Log Forwarding
For complete details on configuring your Deep Security system for use with Sumo Logic, see the White Paper, “Deep Security Integration with Sumo Logic”.
To forward Deep Security system events to Sumo Logic, do the following:
- In Deep Security, go to Administration > System Settings > SIEM.
- Configure SIEM:
- Forward System Events to a remote computer (via Syslog). Activate this check box.
- Hostname or IP address to which events should be sent. This is the hostname or IP address of the Sumo Logic Installed Collector.
- UDP port to which events should be sent. Enter 514.
- Syslog Facility. Select Local 0.
- Syslog Format. Select Common Event Format.
- Save your changes.
Configure the Policy
Now you must add the Syslog Source to your Policy configuration. Set the integration details at the Top (root/base) policy as follows:
- Go to Settings > SIEM.
- For Anti-Malware Event Forwarding, select Forward Events To: and Relay via the Manager.
- Hostname or IP address to which events should be sent. This is the hostname or IP address of the Sumo Logic Installed Collector.
- UPD port to which events should be sent. Enter 514.
- Syslog Facility. Select Local 1.
- Syslog Format. Select Common Event Format.
- For Web Reputation Event Forwarding, select Forward Events To: and Relay via the Manager.
- Hostname or IP address to which events should be sent. This is the hostname or IP address of the Sumo Logic Installed Collector.
- UPD port to which events should be sent. Enter 514.
- Syslog Facility. Select Local 1.
- Syslog Format. Select Common Event Format.
- Click Save.
Sample log messages
<142>Oct 2 16:41:16 CEF:0|Trend Micro|Deep Security Agent|9.6.3177|21|Unsolicited UDP|5|cn1=34 cn1Label=Host ID dvchost=workstation_tsiley TrendMicroDsTenant=Primary TrendMicroDsTenantId=0 act=Deny dmac=B0:B9:B9:F8:E7:8F smac=39:D2:AE:D6:1F:05 TrendMicroDsFrameType=IP src=130.202.140.130 dst=10.0.102.94 in=291 cs3= cs3Label=Fragmentation Bits proto=UDP spt=445 dpt=42 cnt=1
Sample queries
_sourceCategory=Trendmicro dst
| parse "CEF:0|*|*|*|*|*|*|*" as Device_Vendor,Device_Product,Device_Version,Signature_ID, Name, Severity, Extension
| where (signature_id >= 100 AND signature_id <= 199) OR signature_id = 20 OR signature_id = 21
| count Name
| top 5 Name by _count
Collect cloud-based logs for the Trend Micro Deep Security app
This section has instructions for collecting logs for the Trend Micro Deep Security using a Sumo Cloud Syslog source on a hosted collector.
Step 1: Create a Cloud Syslog source on a hosted collector
- Select an existing hosted collector, or create a new one.
- Add a Cloud Syslog source to the hosted collector.
- Give the source a name
- Enter a Source Category.
- Deselect the Enable Timestamp Parsing.
- Click Save.
- The Cloud Syslog Source Token will be generated. You'll supply this information as input to the Log Source Identifier, Server Name, and Server Port within Deep Security.
Supply this information as input to the Log Source Identifier: Server Name, and Server Port within Deep Security.
For Log Source Identifier field, use this format: Deep Security Manager [token from Cloud Syslog source]. Note the spaces with Deep Security Manager.
Step 2: Configure Sumo as a syslog server in Trend Micro Deep Security.
- In the Deep Security Manager console, select Policies > Common Objects.
- Expand the Other node in the left pane.
- Select Syslog Configurations.
- Select the New button to create a new configuration.
- Log Source Identifier. Enter a three word label, for example “Deep Security Manager” or “My Log Source”, followed by value that was shown in the Token field on the Cloud Syslog Source Token page (when you configured the Cloud Syslog Source above), surrounded by square brackets like this:
Deep Security Manager [token from Cloud Syslog source]. It's important that you use this format.Deep Security Managerfollowed by thetoken(for the Cloud Syslog Source) in square brackets like this:
Deep Security Manager [token from Cloud Syslog source] - Log Source Identifier. Enter a three word label, for example “Deep Security Manager” or “My Log Source”, followed by value that was shown in the Token field on the Cloud Syslog Source Token page (when you configured the Cloud Syslog Source above), surrounded by square brackets like this:
- Server Name. Enter the value that was shown in the Host field on the Cloud Syslog Source Token page when you configured the Cloud Syslog Source above.
- Server Port. Enter the value that was shown in the Port field on the Cloud Syslog Source Token page when you configured the Cloud Syslog Source above.
- Transport. Leave "TLS" selected. To check your connection for TLS, see Troubleshooting in our Cloud Syslog Source article.
- Click OK.
Step 3: Forward system and security events to Sumo Logic
- In the Deep Security Manager console, select Policies.
- Double-click the policy you want to use for forwarding events.
- Go to Settings > Event Forwarding.
- Under Event Forwarding Frequency (from the Agent/Appliance), specify how often events are to be sent to Sumo Logic.
- Under Event Forwarding Configuration (from the Agent/Appliance), specify the syslog configuration to use for each protection module, choosing from the following options:
- Inherited (configuration name): The behavior is inherited from a parent policy or computer.
- None: Events are not forwarded.
- _Syslog (configuration name): Events are forwarded to the specified syslog configuration. To see details about the configuration or edit it, click Edit. The configuration must have Agents should forward logs set to "Via the Deep Security Manager".
- New: Enables you to define a new configuration (for details, see Define a syslog configuration.) The configuration must have Agents should forward logs set to "Via the Deep Security Manager".
- Click Save.
Verify configuration
Send System Events to confirm communication with Sumo Logic. There may be a 5-10 minute delay.
Installing the Trend Micro Deep Security app
To install the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Install App.
note
Sometimes this button says Add Integration.
- Click Next in the Setup Data section.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-installation
Once your app is installed, it will appear in your Installed Apps folder, and dashboard panels will start to fill automatically.
Each panel slowly fills with data matching the time range query received since the panel was created. Results will not immediately be available but will be updated with full graphs and charts over time.
Viewing Trend Micro Deep Security dashboards
All dashboards have a set of filters that you can apply to the entire dashboard. Use these filters to drill down and examine the data to a granular level.
- You can change the time range for a dashboard or panel by selecting a predefined interval from a drop-down list, choosing a recently used time range, or specifying custom dates and times. Learn more.
- You can use template variables to drill down and examine the data on a granular level. For more information, see Filtering Dashboards with Template Variables.
- Most Next-Gen apps allow you to provide the scope at the installation time and are comprised of a key (
_sourceCategoryby default) and a default value for this key. Based on your input, the app dashboards will be parameterized with a dashboard variable, allowing you to change the dataset queried by all panels. This eliminates the need to create multiple copies of the same dashboard with different queries.
Deep Security - Overview
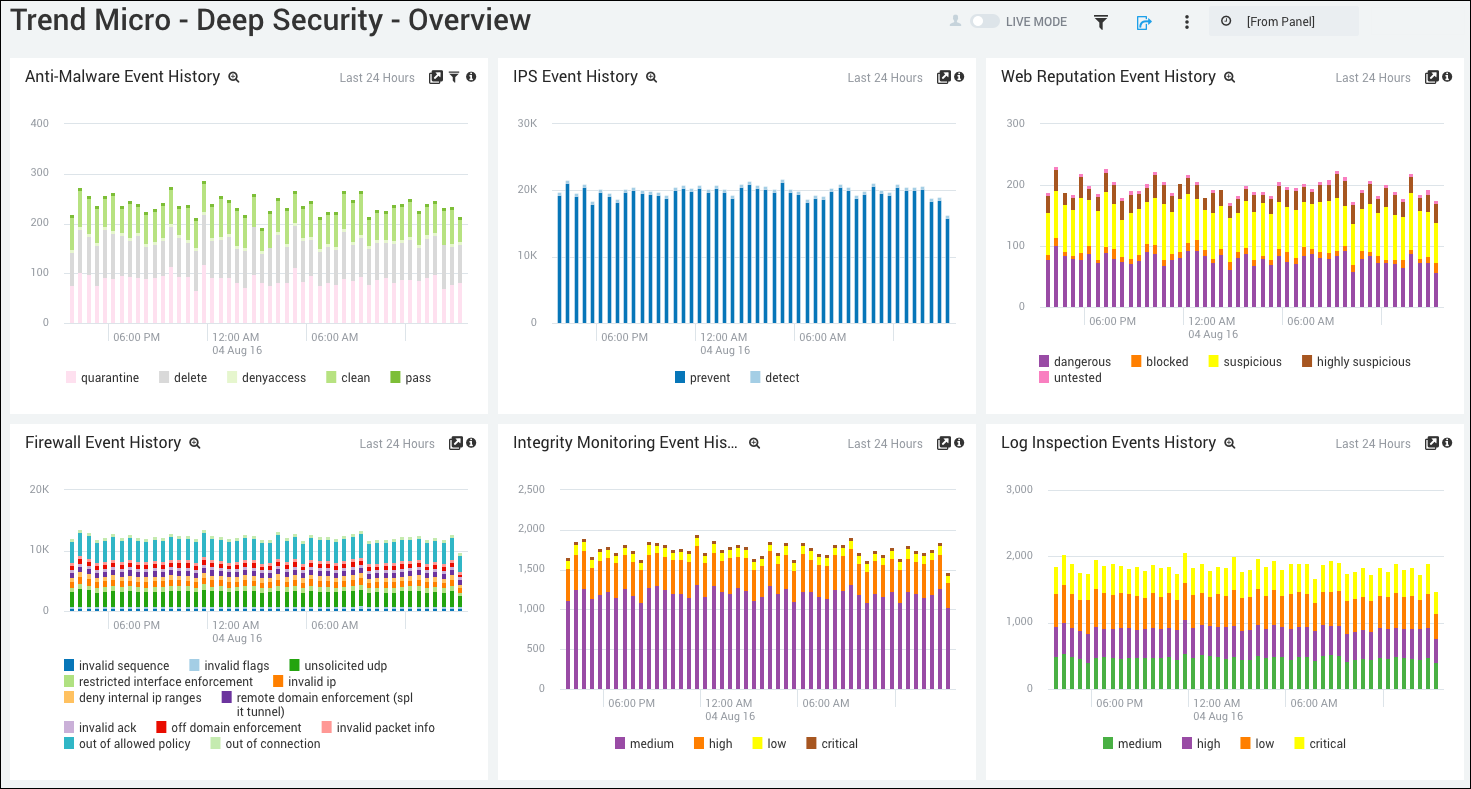
Anti-Malware Event History. Displays the number and types of anti-malware events in a stacked column chart on a timeline for the last 24 hours.
IPS Event History. Shows the number and types of IPS events in a stacked column chart on a timeline for the last 24 hours.
Web Reputation Event History. Provides details on the number and types of web reputation events in a stacked column chart on a timeline for the last 24 hours.
Firewall Event History. Displays the number and types of firewall events in a stacked column chart on a timeline for the last 24 hours.
Integrity Monitoring Event History. Shows the number and types of integrity monitoring events in a stacked column chart on a timeline for the last 24 hours.
Log Inspection Events History. Provides details on the number and types of log inspection events in a stacked column chart on a timeline for the last 24 hours.
Deep Security - Anti-Malware
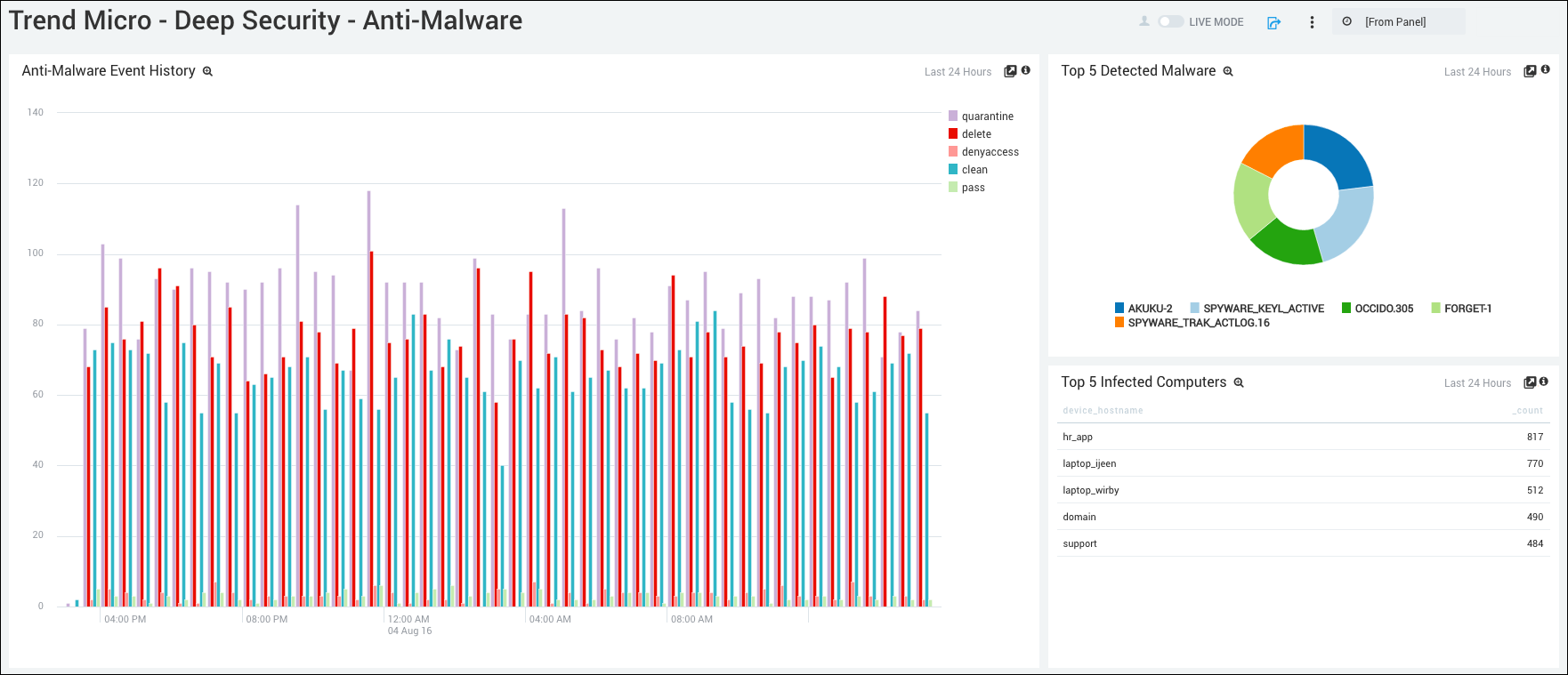
Anti-Malware Event History. Displays the number and type of anti-malware events in a column chart on a timeline for the last 24 hours.
Top 5 Detected Malware. Shows the top 5 types of malware detected in a pie chart for the last 24 hours.
Top 5 Infected Computers. Lists the top 5 infected computers in a table chart by device host name and count for the last 24 hours.
Deep Security - Firewall
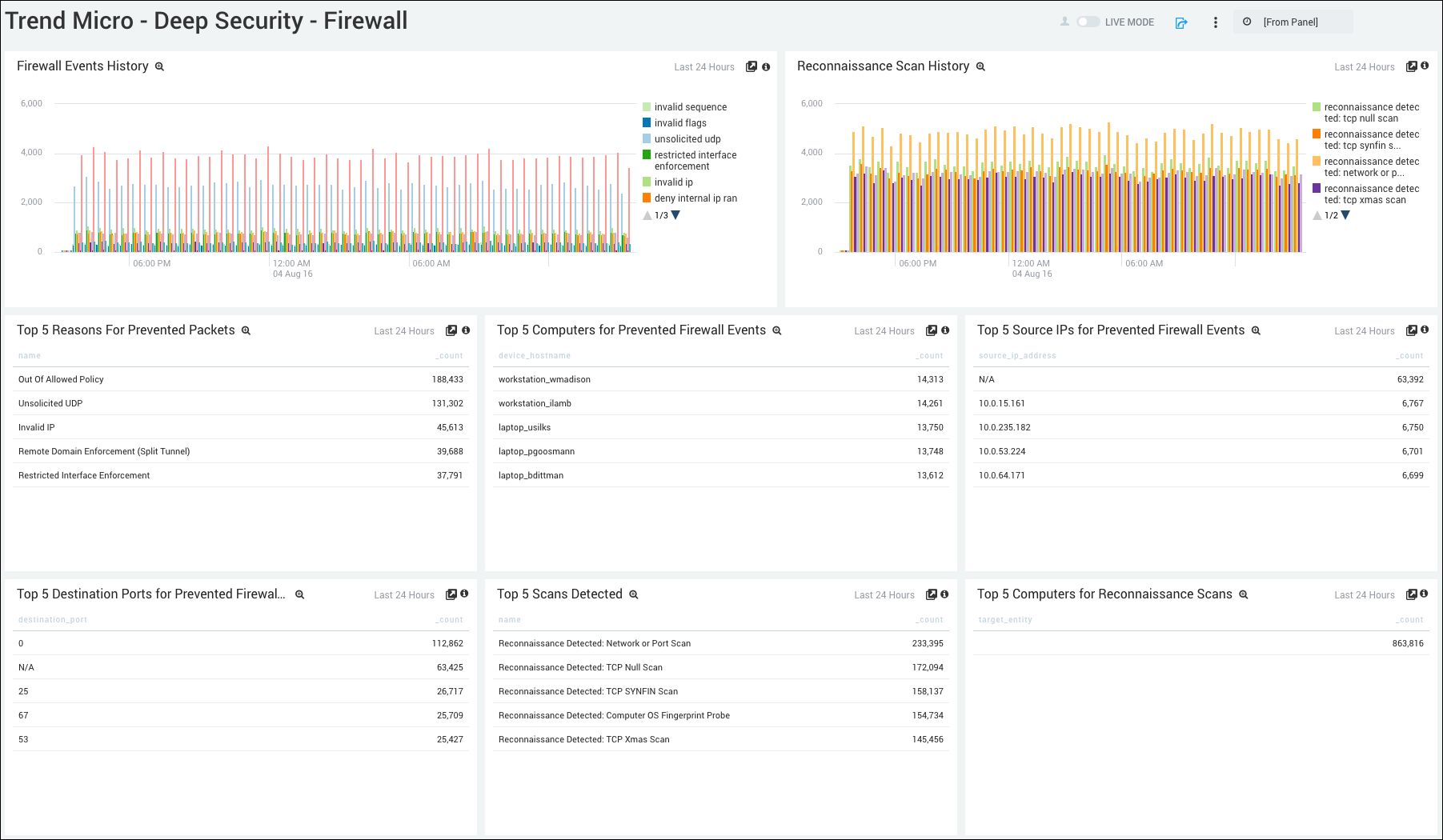
Firewall Events History. Displays the number and type of firewall events in a column chart on a timeline for the last 24 hours.
Reconnaissance Scan History. Shows the number and type of reconnaissance scan events in a column chart on a timeline for the last 24 hours.
Top 5 Reasons for Prevented Packets. Lists the top 5 reasons why packets were prevented in a table chart by device host name and count for the last 24 hours.
Top 5 Computers for Prevented Firewall Events. Displays the top 5 computers that had prevented firewall events in a table chart by device host name and count for the last 24 hours.
Top 5 Source IDs for Prevented Firewall Events. Shows the top 5 computers that had prevented firewall events in a table chart by source IP address and count for the last 24 hours.
Top 5 Destination Ports for Prevented Firewall Events. Provides details on the top 5 destination ports that had prevented firewall events in a table chart by destination port and count for the last 24 hours.
Top 5 Scans Detected. Displays the top 5 scans detected in a table chart by name and count for the last 24 hours.
Top 5 Computers for Reconnaissance Scans. Shows the top 5 computers for reconnaissance scans in a table chart by target entry and count for the last 24 hours.
Deep Security - Integrity Monitoring
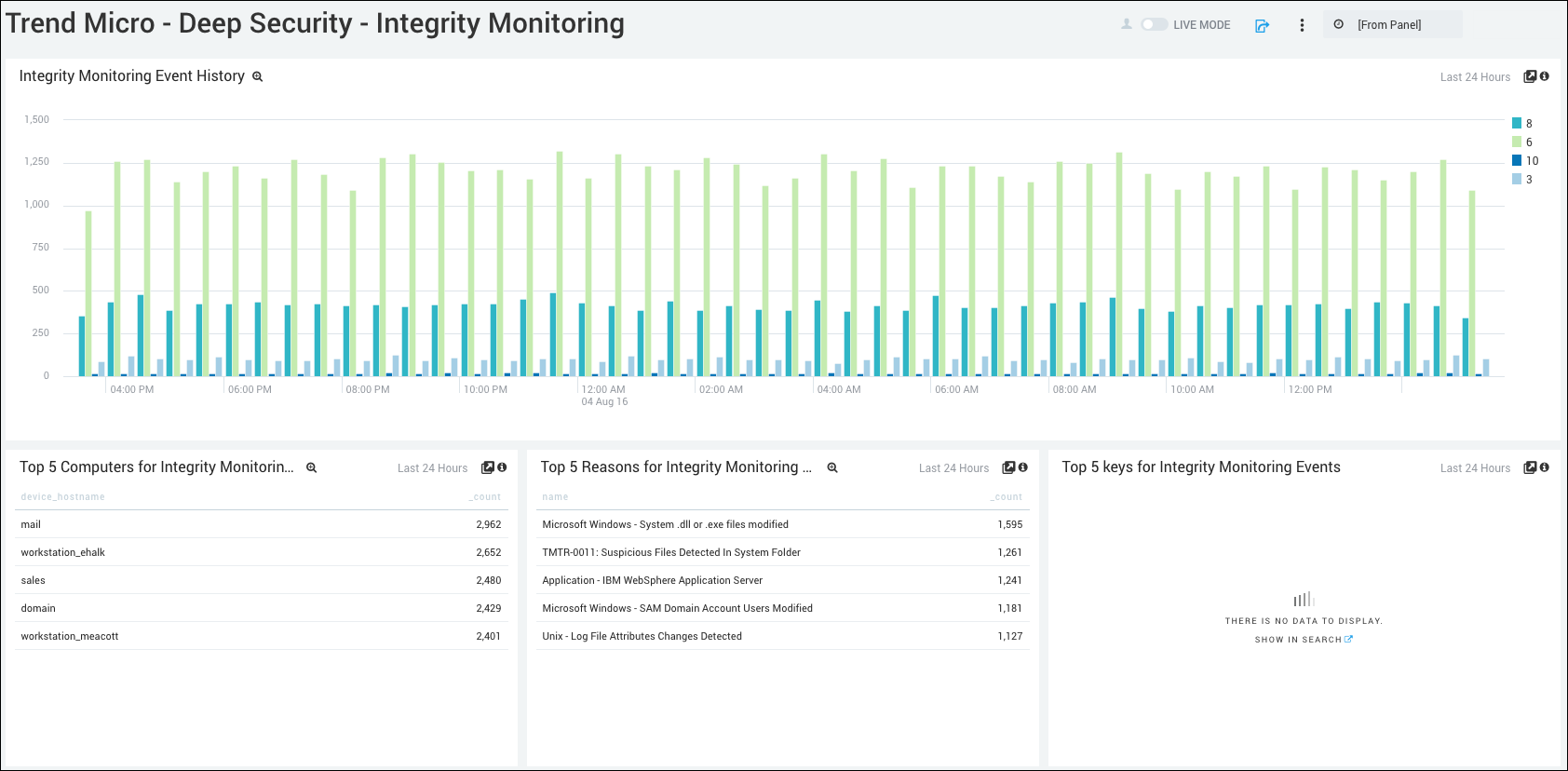
Integrity Monitoring Event History. Displays the number and type of integrity monitoring events in a column chart on a timeline for the last 24 hours.
Top 5 Computers for Integrity Monitoring Events. Shows the top 5 computers that had integrity monitoring events in a table chart by device host name and count for the last 24 hours.
Top 5 Reasons for Integrity Monitoring Events. Lists the top 5 reasons for integrity monitoring events in a table chart by name and count for the last 24 hours.
Top 5 Keys for Integrity Monitoring Events. Displays the top 5 keys for integrity monitoring events in a table chart for the last 24 hours.
Deep Security - Intrusion Prevention
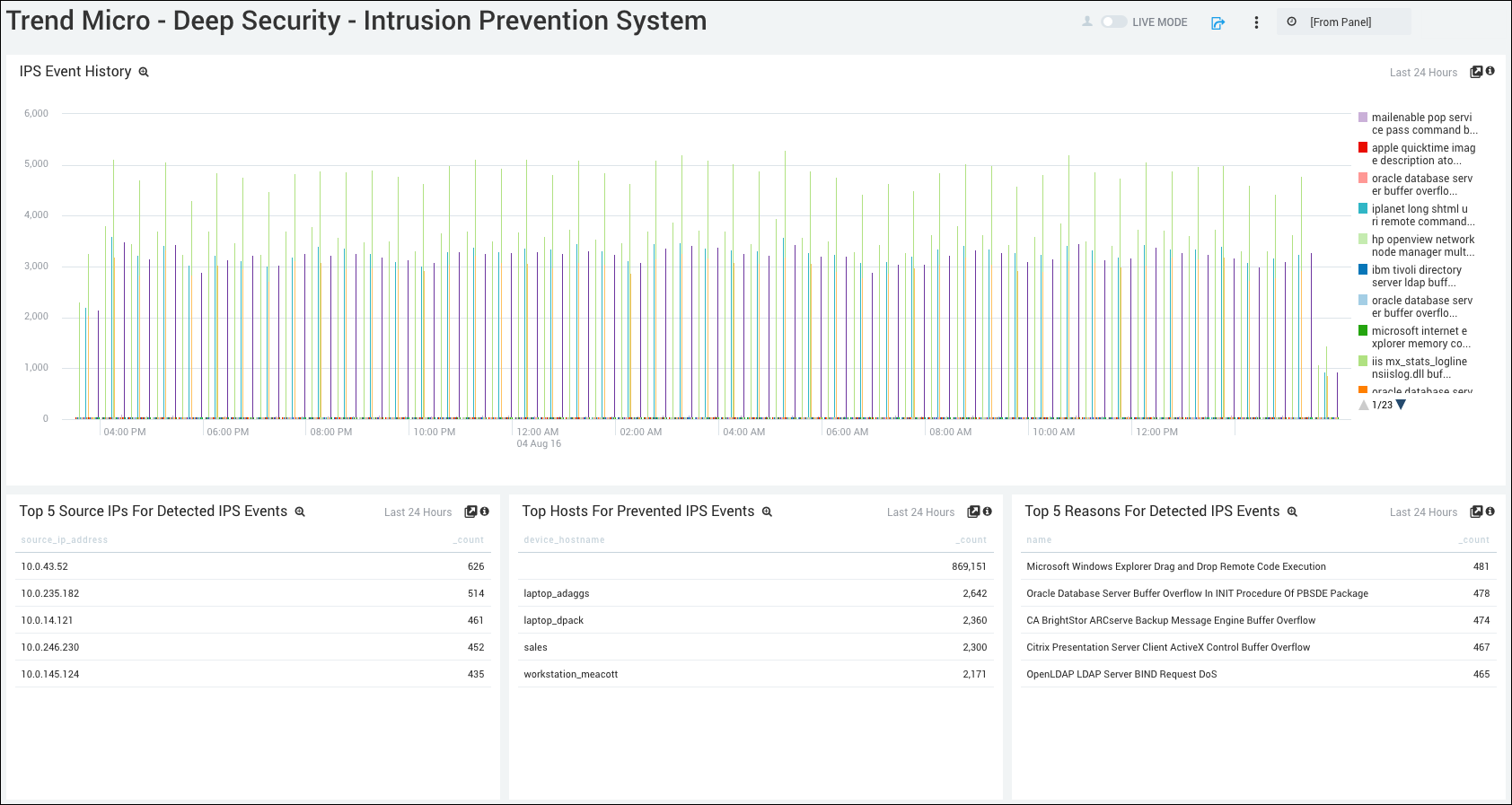
IPS Event History. Displays the number and type of intrusion prevention events in a column chart on a timeline for the last 24 hours.
Top 5 Source IPs for Detected IPS Events. Lists the top 5 Source IPs for detected intrusion prevention events in a table chart by source IP and count for the last 24 hours.
Top Hosts for Prevented IPS Events. Shows the top 5 hosts for prevented intrusion events in a table chart by device host name and count for the last 24 hours.
Top 5 Reasons for Detected IPS Events. Displays the top 5 reasons for detected intrusion prevention events in a table chart by name and count for the last 24 hours.
Deep Security - Log Inspection
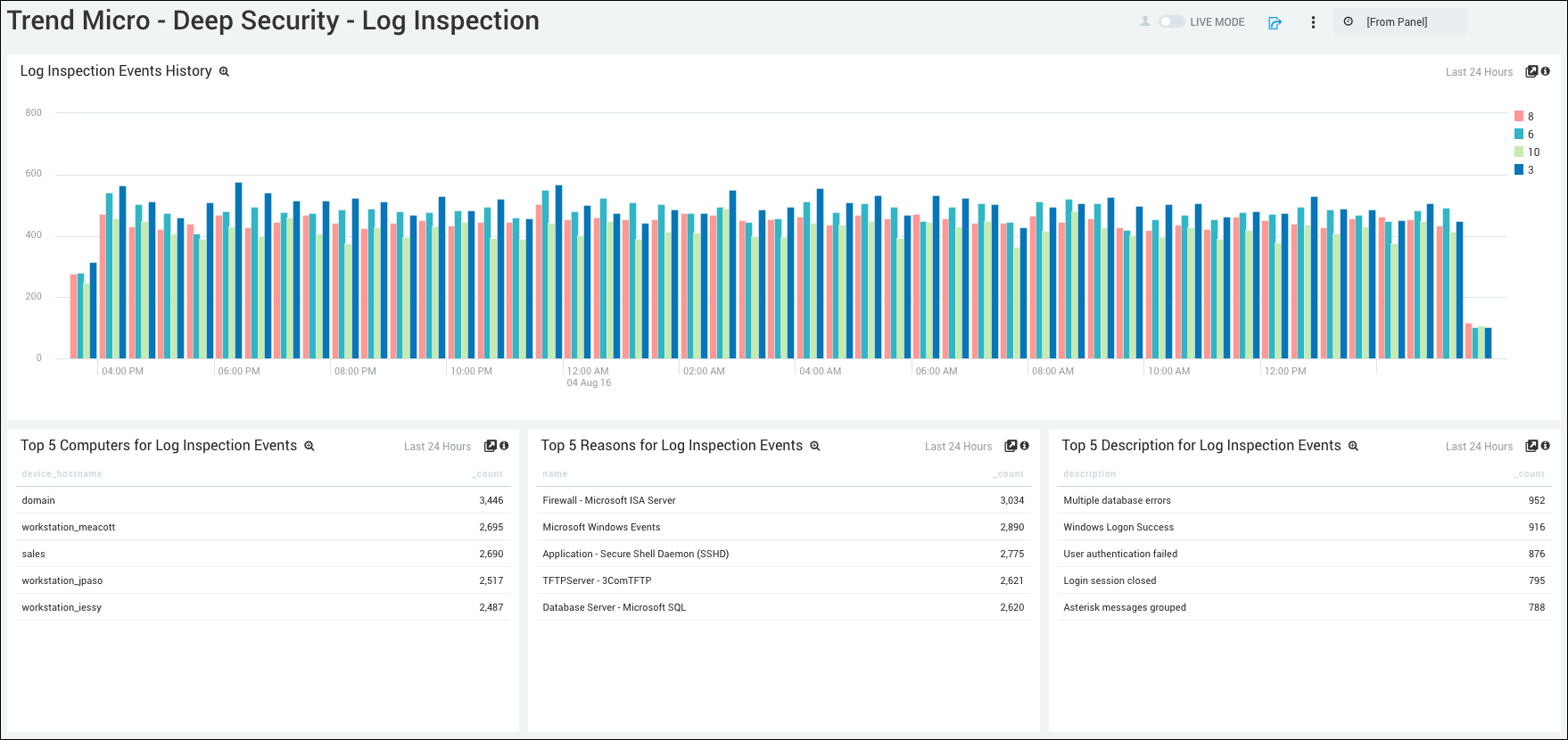
Log Inspection Events History. Displays the number and type of log inspection events in a column chart on a timeline for the last 24 hours.
Top 5 Computers for Log Inspection Events. Lists the top 5 computers for log inspection events in a table chart by device host name and count for the last 24 hours.
Top 5 Reasons for Log Inspection Events. Shows the top 5 reasons for log inspection events in a table chart by device host name and count for the last 24 hours.
Top 5 Descriptions for Log Inspection Events. Displays the top 5 descriptions for log inspection events in a table chart by device host name and count for the last 24 hours.
Deep Security - Web Reputation
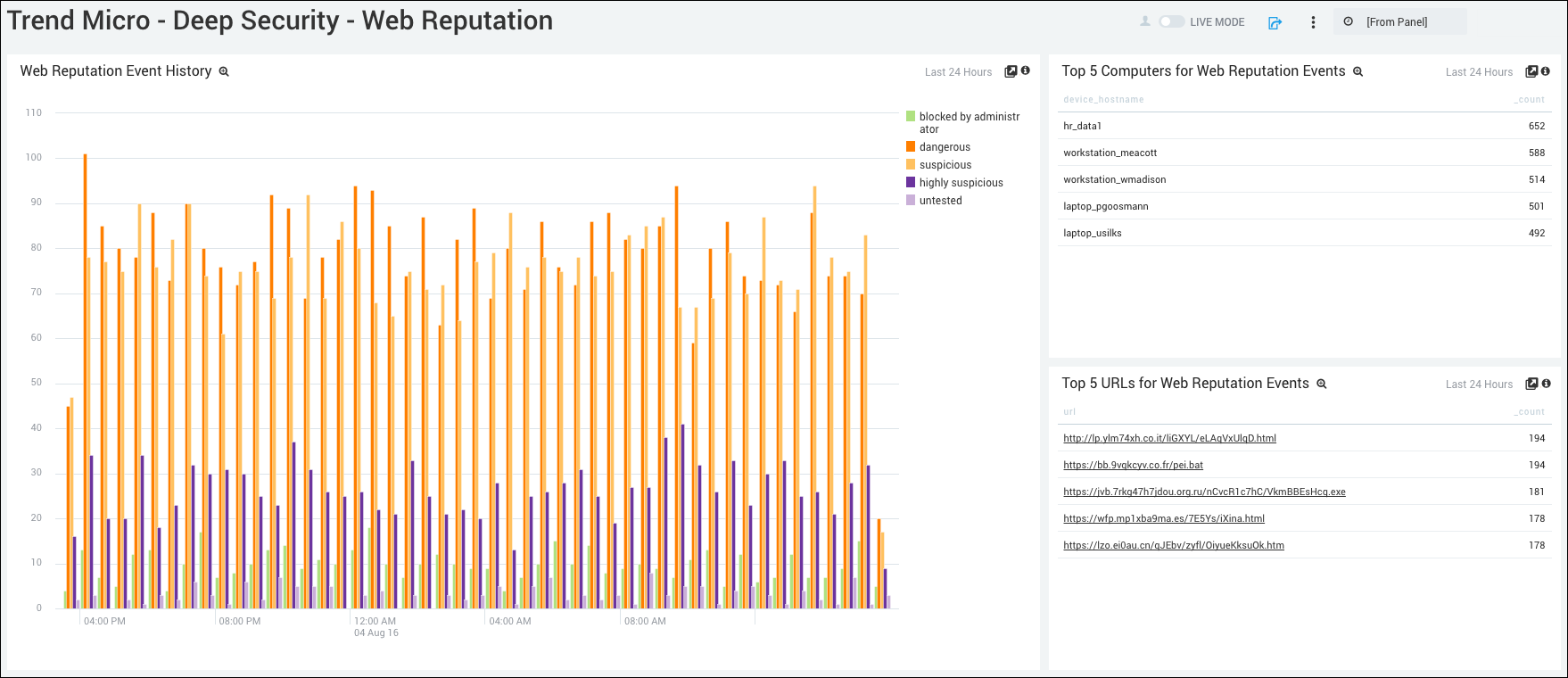
Web Reputation Event History. Displays the number and type of web reputation events in a column chart on a timeline for the last 24 hours.
Top 5 Computers for Web Reputation Events. Shows the top 5 computers that have had web reputation events by device host name and count for the last 24 hours.
Top 5 URLs for Web Reputation Events. Lists the top 5 URLs that have had web reputation events by URL and count for the last 24 hours.
Filters
The Sumo Logic app for Trend Micro - Deep Security provides the following filters:
- file
- severity
- signature_id
Upgrade/Downgrade the Trend Micro Deep Security app (Optional)
To update the app, do the following:
Next-Gen App: To install or update the app, you must be an account administrator or a user with Manage Apps, Manage Monitors, Manage Fields, Manage Metric Rules, and Manage Collectors capabilities depending upon the different content types part of the app.
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
Optionally, you can identify apps that can be upgraded in the Upgrade available section. - To upgrade the app, select Upgrade from the Manage dropdown.
- If the upgrade does not have any configuration or property changes, you will be redirected to the Preview & Done section.
- If the upgrade has any configuration or property changes, you will be redirected to the Setup Data page.
- In the Configure section of your respective app, complete the following fields.
- Field Name. If you already have collectors and sources set up, select the configured metadata field name (eg _sourcecategory) or specify other custom metadata (eg: _collector) along with its metadata Field Value.
- Click Next. You will be redirected to the Preview & Done section.
Post-update
Your upgraded app will be installed in the Installed Apps folder and dashboard panels will start to fill automatically.
See our Release Notes changelog for new updates in the app.
To revert the app to a previous version, do the following:
- Select App Catalog.
- In the Search Apps field, search for and then select your app.
- To version down the app, select Revert to < previous version of your app > from the Manage dropdown.
Uninstalling the Trend Micro Deep Security app (Optional)
To uninstall the app, do the following:
- Select App Catalog.
- In the 🔎 Search Apps field, run a search for your desired app, then select it.
- Click Uninstall.