Deploy to Multiple Accounts and Regions
This topic has instructions for deploying AWS Observability Solution to multiple AWS accounts and regions
using Stack Sets.
Given that we use an account alias, we recommend you use StackSets to automatically deploy the AWS CloudFormation template across all regions in one AWS account at a time. New AWS accounts can be added to an existing stack set.
Before you start
- If this is the first time you've deployed our AWS Observability solution, read the Before You Deploy topic for more information.
- Complete the prerequisites for StackSets as described in the AWS documentation.
Step 1: Open the CloudFormation template
- Sign in to the AWS Management console.
- Choose an option to invoke AWS CloudFormation Template:
- Click this URL to invoke the latest Sumo Logic AWS CloudFormation template.
- Download the AWS Observability Solution template (S3 link for CloudFormation template): https://sumologic-appdev-aws-sam-apps.s3.amazonaws.com/aws-observability-versions/v2.12.0/sumologic_observability.master.template.yaml to invoke the latest Sumo Logic AWS CloudFormation template.
noteIf you would like to download or inspect this or other versions of this template, see the Changelog.
- Select the AWS Region where you want to deploy the AWS CloudFormation template.
danger
This step is critical. If you do not select the correct region, you will deploy the solution in the wrong region.
- Proceed to Step 2 below.
Step 2: Sumo Logic access configuration
The below table displays the response to each prompt during Step 2.
| Prompt | Guideline |
|---|---|
| Sumo Logic Deployment Name | Enter au, ca, de, eu, jp, us2, fed, kr, or us1. See Sumo Logic Endpoints and Firewall Security for more information on Sumo Logic deployments. |
| Sumo Logic Access ID | Sumo Logic Access ID. See Create an access key for more information. |
| Sumo Logic Access Key | Sumo Logic Access Key. This key is used for Sumo Logic API calls. |
| Sumo Logic Organization ID | You can find your org on the Preferences page in the Sumo Logic UI. Your org ID will be used to configure the IAM Role for Sumo Logic AWS Sources. |
| Delete Sumo Logic Resources when stack is deleted | To delete collectors, sources and apps in Sumo Logic when the stack is deleted, set this parameter to "True". If this is set to "False", Sumo Logic resources are not deleted when the AWS CloudFormation stack is deleted. Deletion of updated resources will be skipped. |
Step 3: AWS account alias
The below table displays the response to each prompt during Step 3.
| Prompt | Guideline |
|---|---|
| Alias for your AWS account | Enter an account alias for the AWS environment from which you are collecting data. This alias should be something that makes it easy for you to identify what this AWS account is being used for (for example, dev, prod, billing, and marketplace). This name will appear in the metrics and logs and can be queried via the “account field”. Important: Account Aliases should be alphanumeric and cannot include special characters such as “-, $, _” etc. Leave this blank If you're using CloudFormation StackSets to deploy the solution in multiple AWS accounts. |
| S3 URL of a CSV file that maps AWS Account IDs to an Account Alias | This parameter is applicable only If you're using CloudFormation StackSets to deploy the solution in multiple AWS accounts. The S3 URL of the CSV file should have public read access when deploying or updating the solution. Enter the S3 URL of a CSV file which contains the mapping of AWS Account IDs to an Account Alias in the following format: accountid,alias For example: 1234567,dev 9876543,prod |
Step 4: Install Apps
Perform the following steps to install apps.
- Complete the prerequisites for StackSets as described in the AWS documentation.
- Install the apps by running the AWS CloudFormation Stack once in any given account and region. Use the configuration below to set up only app dashboards.
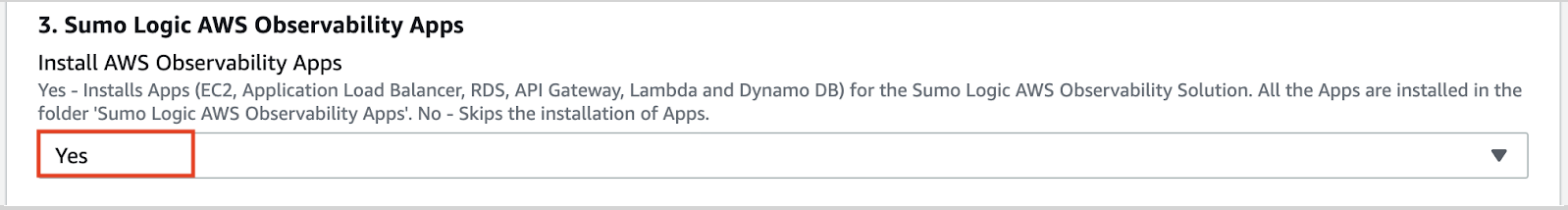
- Install AWS Observability Apps as Yes.
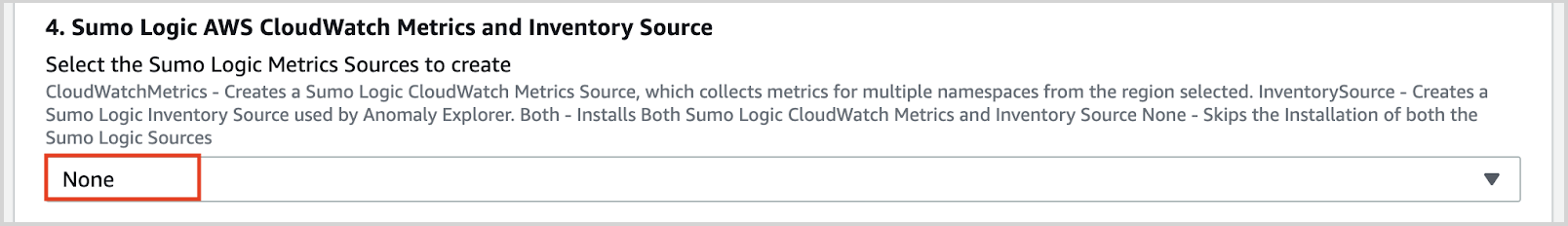
- Select the Sumo Logic Metrics Sources to create as None.
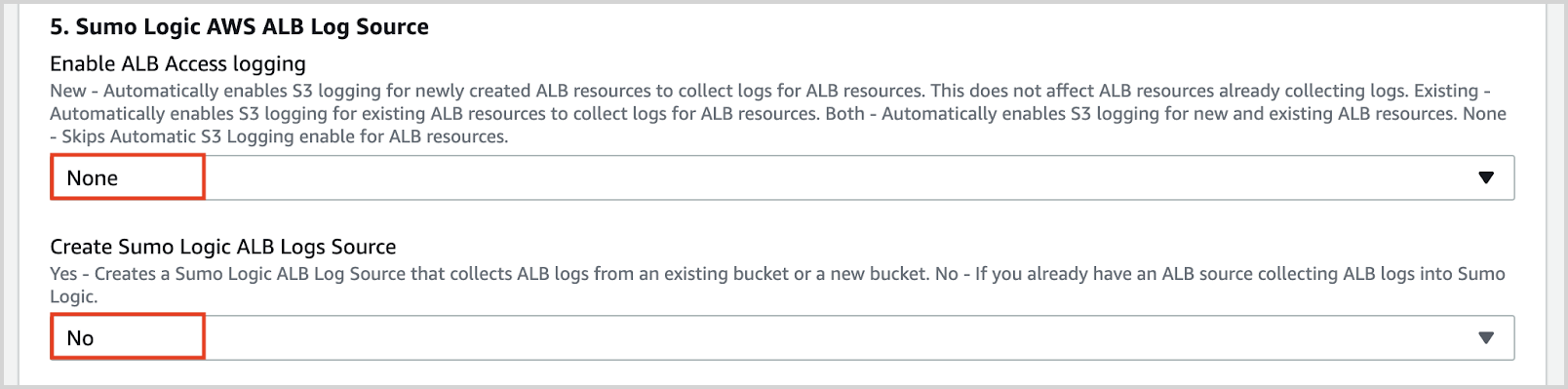
- Enable ALB Access logging as None and Create Sumo Logic ALB Logs Source as No.
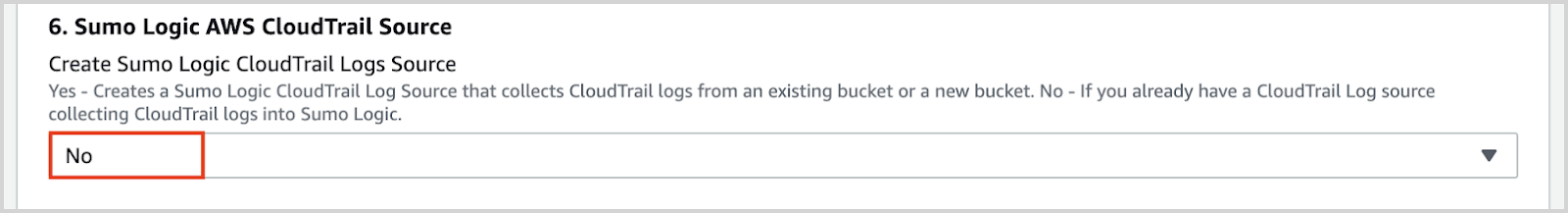
- Create Sumo Logic CloudTrail Logs Source as No.
- Select Sumo Logic CloudWatch Logs Source as None.
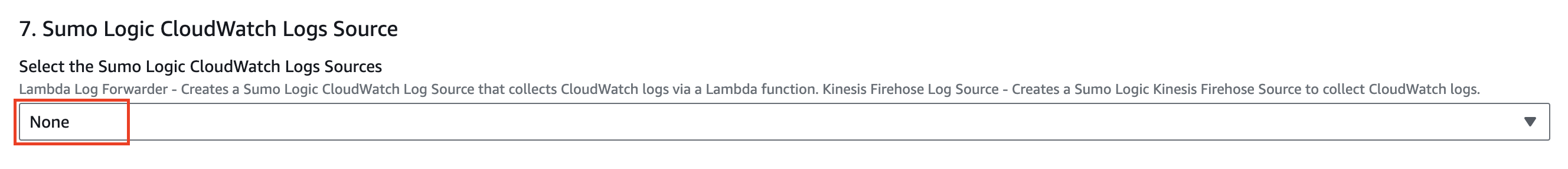
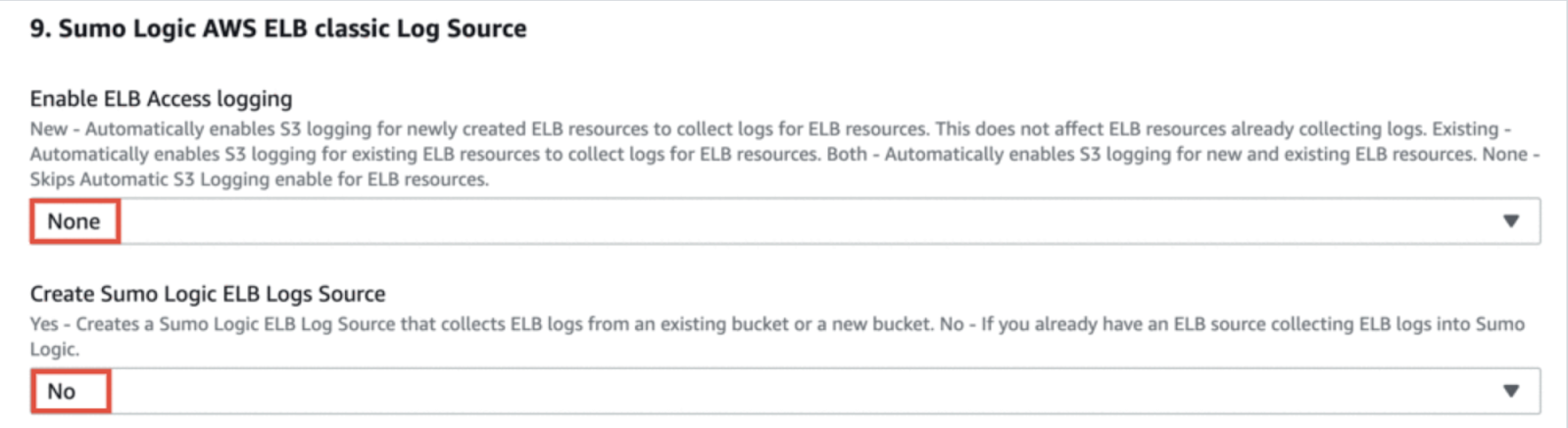
- Enable ELB Classic Access logging as None and Create Sumo Logic ELB Classic Logs Source as No.
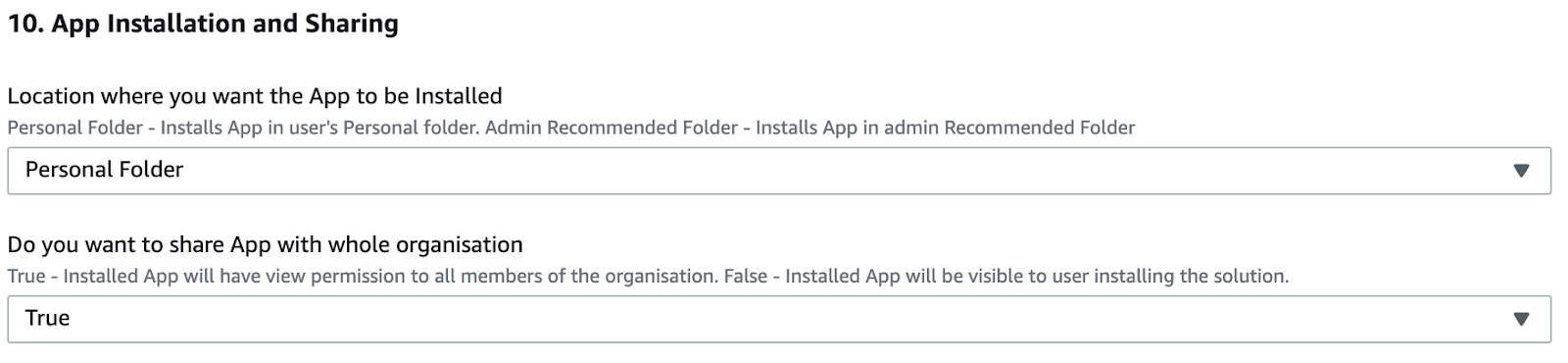
- Location where you want the App to be Installed as PersonalFolder. And for Do you want to share App with whole organization, set as True.
Step 5: Determine account aliases
If you are going to deploy the solution in multiple AWS accounts, we highly recommend that you prepare a CSV file that maps your AWS Account-ids to account aliases. These aliases should be something that makes it easy for you to identify what this AWS account is being used for (for example, dev, prod, billing, and marketplace). These names will appear in the Sumo Logic Explorer View, metrics, and logs and can be queried using the “account field”.
The following is an example of the CSV file format to use:
accountid,alias
234234234324,dev
214324324324,prod
Please upload this file to an Amazon S3 bucket and make it accessible to the account from where you are going to run the CloudFormation template.
In case you do not provide a CSV file or if we detect that it does not have the right format, the AWS account-id will be used as the alias and this value will be used for the “account” field in Sumo Logic.
Use the AWS CloudFormation template with StackSets
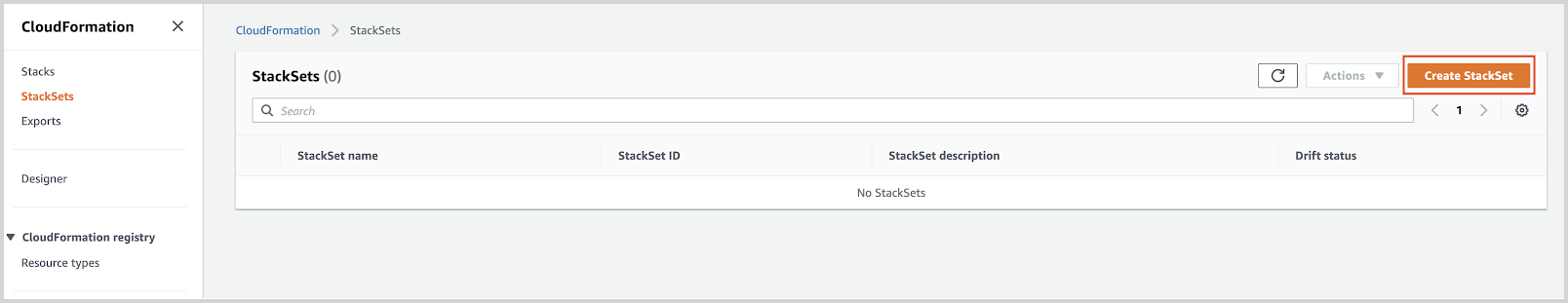
- Go to Stack Sets in your AWS account.
- Click Create StackSet.
- Paste the URL
https://sumologic-appdev-aws-sam-apps.s3.amazonaws.com/aws-observability-versions/v2.12.0/sumologic_observability.master.template.yamlin the Amazon S3 URL option and click Next. If you'd like to download or inspect this or other versions of this template, see the Changelog.
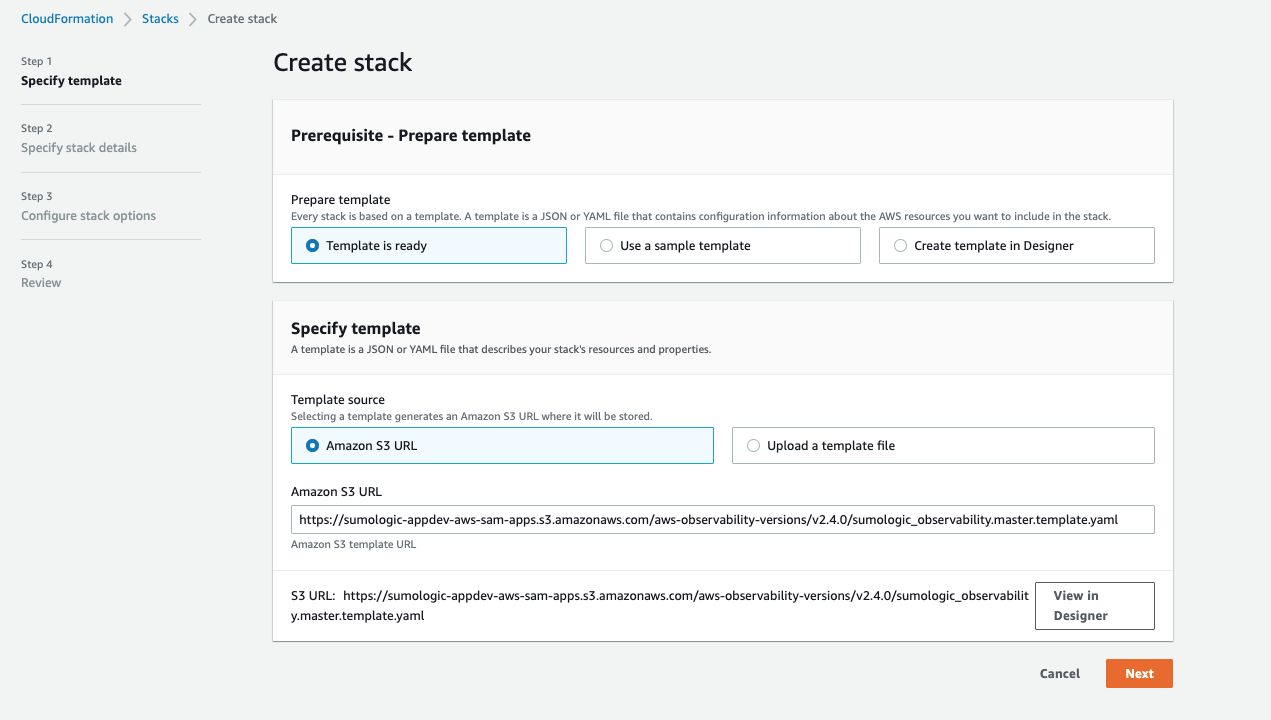
- Provide a StackSet Name and supply the values for each of the prompts listed as per instructions in the Deploy the AWS Observability Solution section with the following exception:
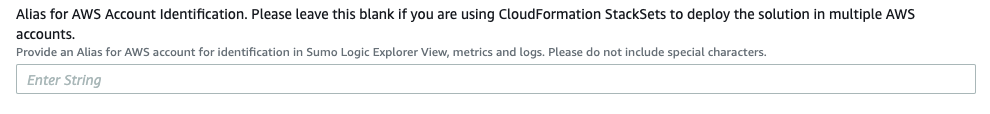
- Leave the field “Alias for AWS Account Identification” blank.
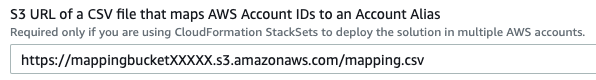
- Provide the S3 Object URL of a CSV file that maps AWS Account IDs to an Account Alias in Section 2 of the template “AWS Account Alias”.
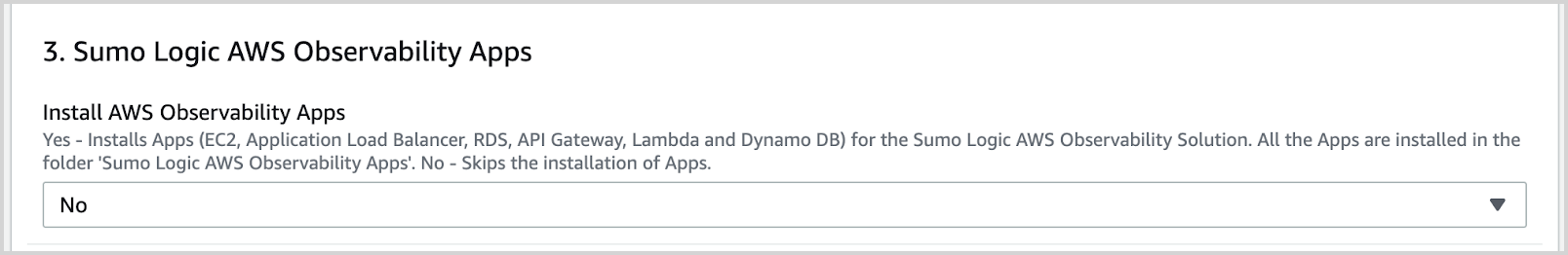
- Answer No in Section 3 of the template "Install AWS Observability Apps".
- Click Next.
- Leave the field “Alias for AWS Account Identification” blank.
- Add Tags, select the Administrator role defined in the prerequisites above, and click Next.
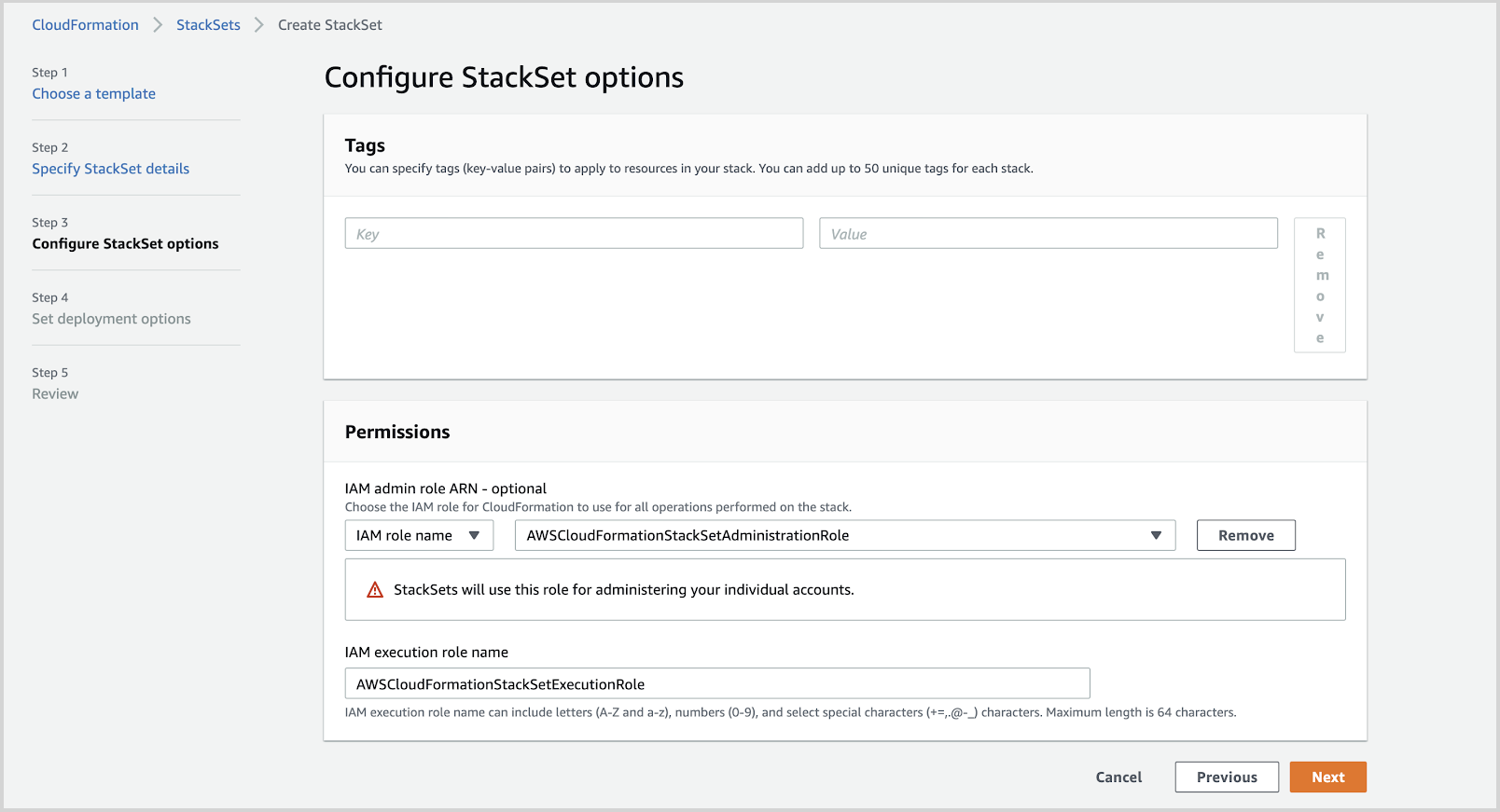
- Provide a single AWS account number only and select a list of regions in the account where you would like to deploy the AWS CloudFormation template as shown in the screenshot below:
- You will need to select all the regions in the current account where you would like to deploy the template.
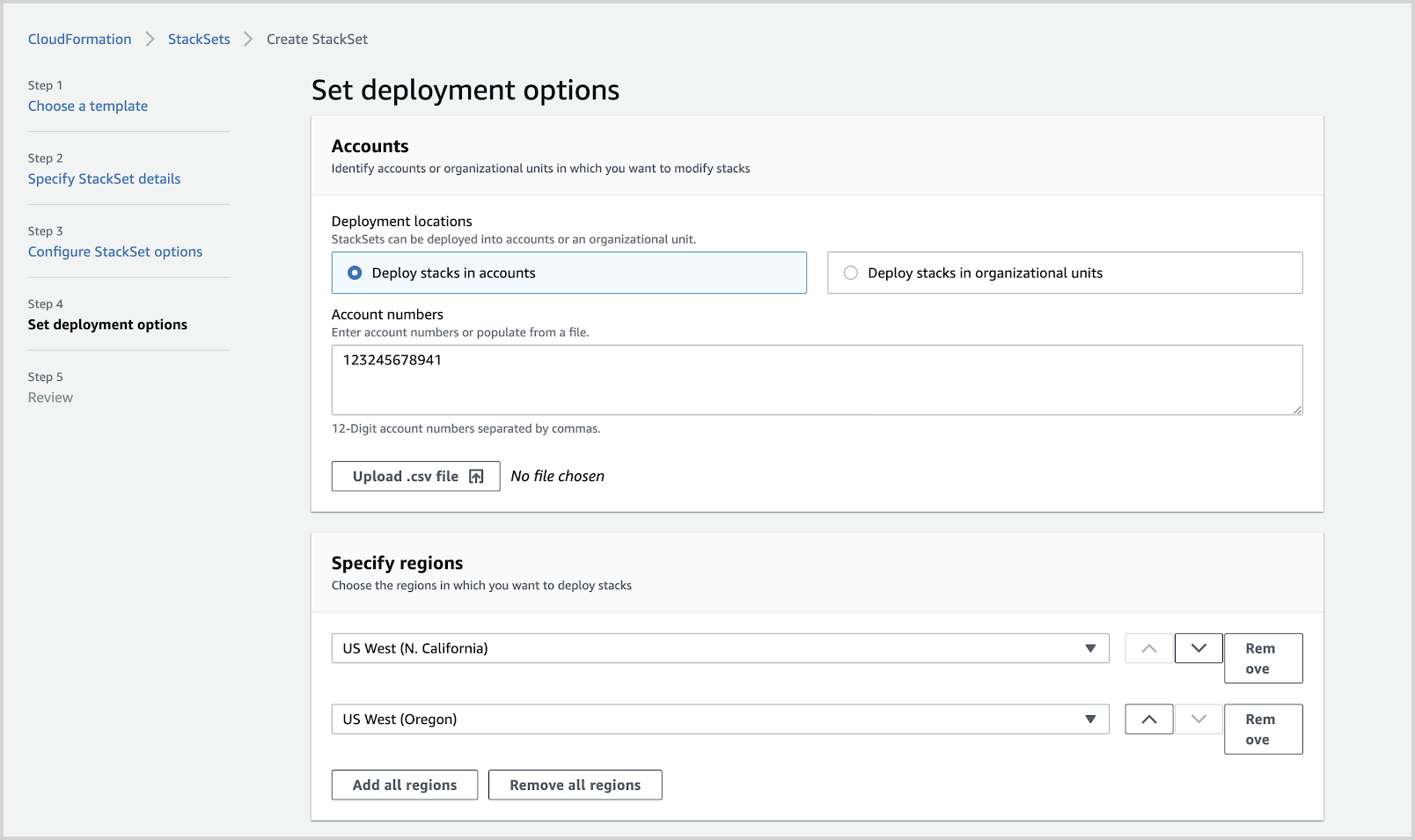
- You will need to select all the regions in the current account where you would like to deploy the template.
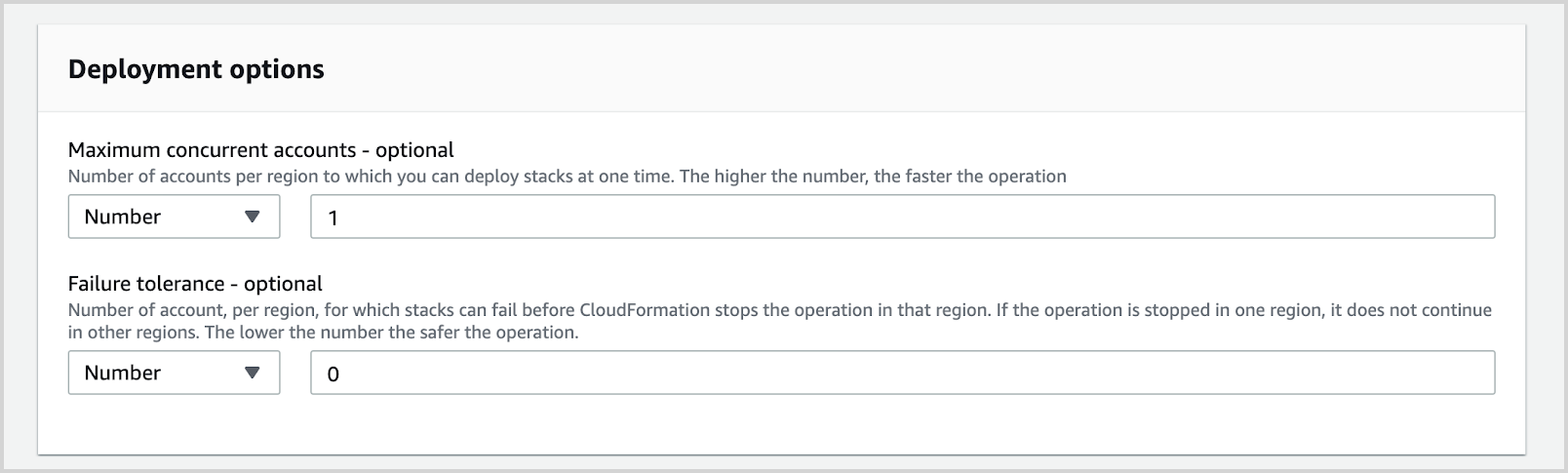
- Increasing the Maximum concurrent actions to be more than 1 is not recommended and can cause your stack set deployment to fail. Stack sets should be deployed one at a time, sequentially. Click Next.
- Review the details, select the capabilities and click Submit.
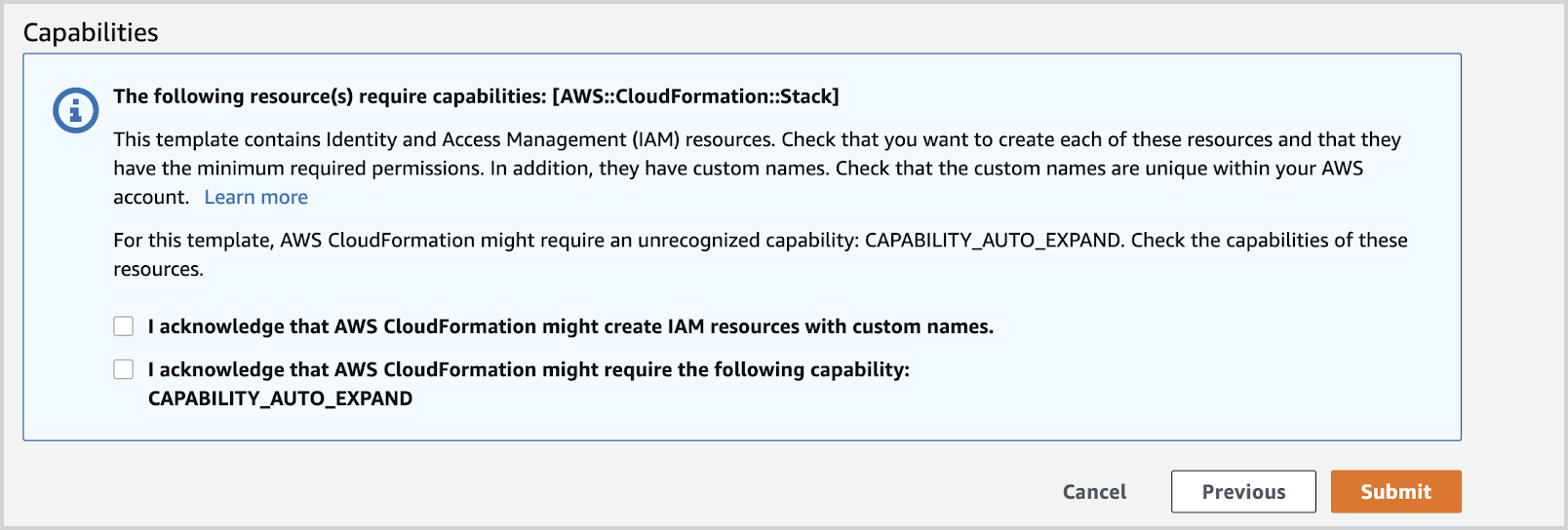
- Once you hit submit, the AWS CloudFormation template will execute in the provided account and regions sequentially.
Add more accounts to the same Stack Set
- Select Add new stacks to StackSet.
- In ‘Set deployment options’, Enter the account number and regions you want to deploy the stack.
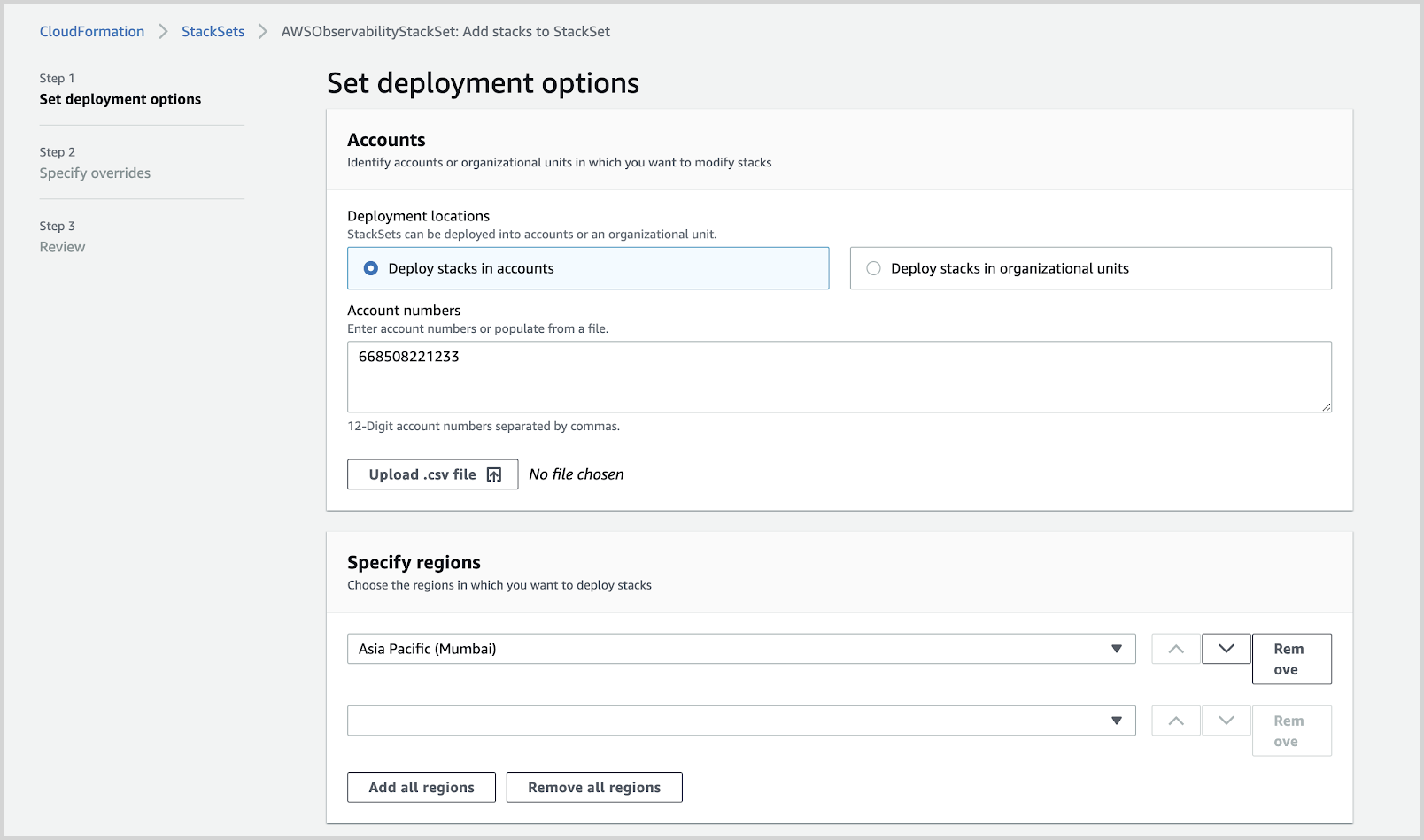
- Verify the S3 mapping file contains the mapping for the new Account ID.
- Review the details, select the capabilities, and click Submit.