CrowdStrike Falcon

Version: 1.18
Updated: Sept 30, 2025
The CrowdStrike Falcon integration allows you to pull and update Alerts/Incidents, and search Incidents/Devices/Alerts.
Actions
- Alerts CrowdStrike Falcon Daemon (Daemon) - Daemon to pull CrowdStrike Alerts.
- Close CrowdStrike Incident (Containment) - Close the state of the CrowdStrike Incident.
- Create Indicators (Containment) - Create the Indicators.
- Device Actions (Containment) - Take various actions on the hosts in your environment.
- Get Browser History (Enrichment) - Get user Browser history.
- Get Endpoint (Enrichment) - Get details on one or more hosts by providing agent IDs.
- Get Incident Info (Enrichment) - Get details for a specific Crowdstrike Incident.
- Get Indicators (Containment) - Get Indicators By IDs.
- Get User ID By Mail (Enrichment) - Search for a specific User ID with a given email address.
- Get IDP Device Info (Enrichment) - Retrieve detailed information about a devices from IDP. Requires IDP rights and relevant IDP-related API scopes.
- Incidents CrowdStrike Falcon Daemon (Daemon) - Daemon to pull CrowdStrike Incidents.
- List Endpoints (Enrichment) - Search for hosts in your environment by platform, hostname, IP.
- Query Devices By Filter (Enrichment) - Search for hosts in your environment by platform, hostname, IP, and other criteria.
- Retrieve Alert Details (Enrichment) - Get details for a specific CrowdStrike Alert.
- Search into Alerts (Enrichment) - Retrieves all Alerts IDs that match a given query.
- Search into Incidents (Enrichment) - Search for incidents by providing an FQL filter, sorting, and paging details.
- Update Alerts (Containment) - Perform actions on Alerts identified by composite ID(s) in request.
Category
EDR
Configure CrowdStrike Falcon in Automation Service and Cloud SOAR
Before you can use this automation integration, you must configure its authentication settings so that the product you're integrating with can communicate with Sumo Logic. For general guidance, see Configure Authentication for Automation Integrations.
How to open the integration's configuration dialog
- Access App Central and install the integration. (You can configure at installation, or after installation with the following steps.)
- Go to the Integrations page.
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar.
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations. - Select the installed integration.
- Hover over the resource name and click the Edit button that appears.
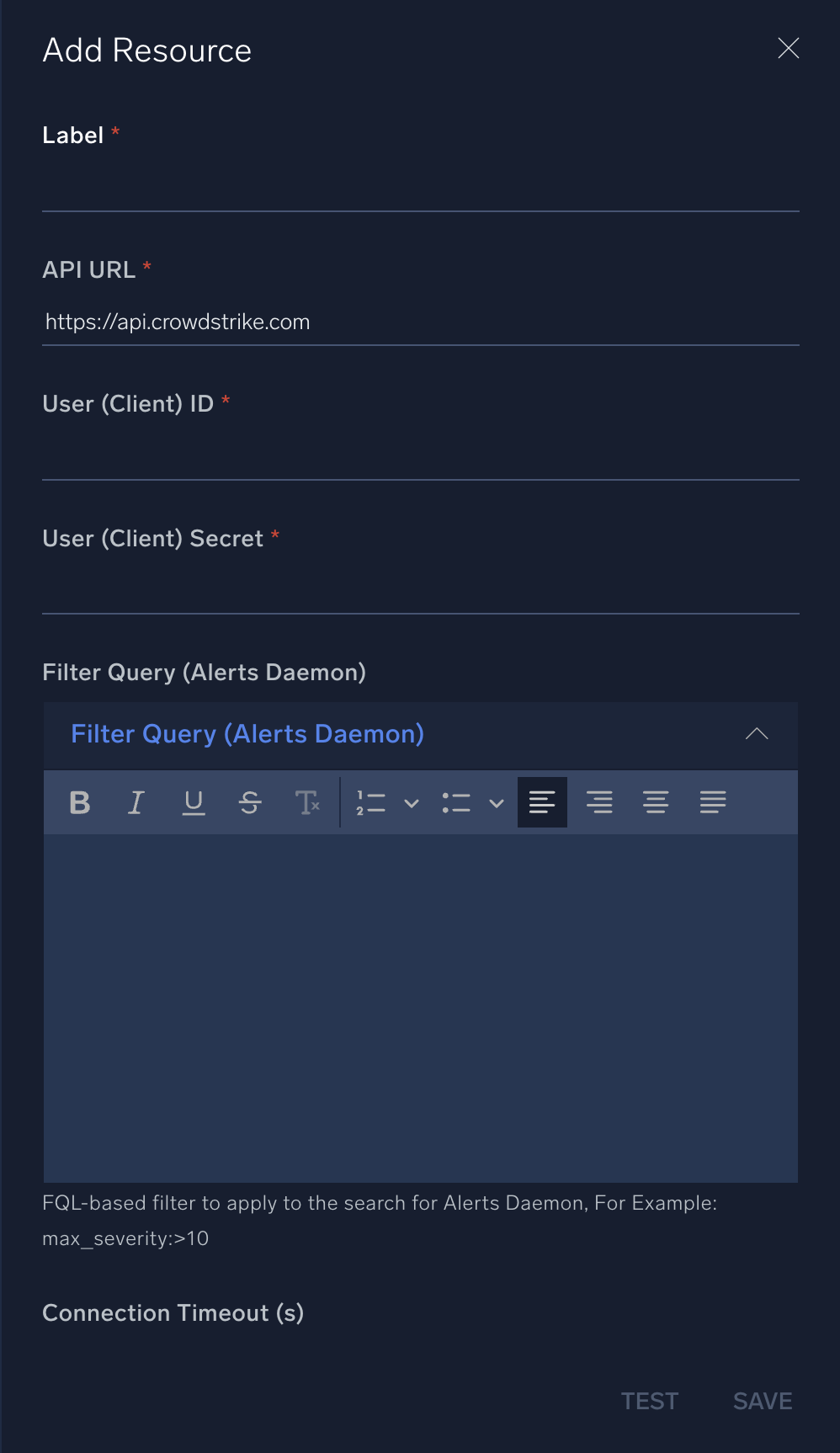
In the configuration dialog, enter information from the product you're integrating with. When done, click TEST to test the configuration, and click SAVE to save the configuration:
-
Label. Enter the name you want to use for the resource.
-
API URL. Enter your CrowdStrike Falcon API URL.
-
User (Client) ID. Enter the unique identifier of the API client. The client ID is visible from the API clients table in the Falcon console.
-
User (Client) Secret. Enter the secret code for the API client, equivalent to a password. The secret is only visible to you at the time the API client is created. After that, it is not retrievable. If your client secret is ever lost, you can reset it to generate a new one.
-
Filter Query (Alerts Daemon). Enter the FQL-based filter to apply to the search for the Alerts daemon, for example,
max_severity:>10 -
Connection Timeout (s). Set the maximum amount of time the integration will wait for a server's response before terminating the connection. Enter the connection timeout time in seconds (for example,
180). -
Verify Server Certificate. Select to validate the server’s SSL certificate.
-
Automation Engine. Select Cloud execution for this certified integration. Select a bridge option only for a custom integration. See Cloud or Bridge execution.
-
Proxy Options. Select whether to use a proxy. (Applies only if the automation engine uses a bridge instead of cloud execution.)
- Use no proxy. Communication runs on the bridge and does not use a proxy.
- Use default proxy. Use the default proxy for the bridge set up as described in Using a proxy.
- Use different proxy. Use your own proxy service. Provide the proxy URL and port number.
For information about CrowdStrike Falcon, see CrowdStrike documentation.
Change Log
- June 3, 2021 - First upload
- July 8, 2022 - Added new action
- Device Actions
- November 10, 2022 - Added new action:
- Get Browser History
- January 31, 2020 - Action updated: Get Report Summary
- December 30, 2022 - Action updated
- Detections CrowdStrike Falcon Daemon (Added FQL-based filter and Pagination to Daemon)
- February 17, 2023 - Refactoring
- February 23, 2023 (v1.3)
- List Endpoints: Updated API Endpoint
- Incidents CrowdStrike Falcon Daemon: Duplicate Removed
- March 7, 2023 (v1.4)
- List Endpoints: Updated Fields Hints
- March 21, 2023 (v1.5) - Logo updated
- July 12, 2023 (v1.8) - Changed fields visibility
- March 4, 2024 (v1.9) - Updated code for compatibility with Python 3.12
- October 16, 2024 (v1.10) - Added new actions
- Create Indicators
- Get Indicators
- November 28, 2024 (v1.12) - Added new actions
- Update Alerts
- Search into Alerts
- Alerts CrowdStrike Falcon Daemon
- February 21, 2025 (v1.13) - Added new action
- Get IDP Device Info
- April 23, 2025 (v1.14) - Updated the Integration
- Refactored the code to improve performance and maintainability.
- June 3, 2025 (v1.15) - Updated the Integration
- Resolved timeout issues across all actions, including daemons and enrichment queries, for improved stability and performance.
- June 5, 2025 (v1.16) - Added new actions
- Retrieve Alert Details
- July 4, 2025 (v1.17) - Added new action
- Query Devices By Filter
- Sept 30, 2025 (v1.18) - CrowdStrike has deprecated Detections-based APIs, and these actions have now been replaced with Alerts-based actions to align with the latest API updates. Please migrate to the Alerts actions to ensure continued functionality.
- Deprecated Actions:
- Update Detections
- Search into Detections
- Detections CrowdStrike Falcon Daemon
- Replacement Actions:
- Update Alerts
- Search into Alerts
- Alerts CrowdStrike Falcon Daemon
- Deprecated Actions: