Microsoft Defender ATP

Version: 1.2
Updated: Jul 12, 2023
Microsoft Defender Advanced Threat Protection (ATP) is a product that enables preventive protection, post-breach detection, automated investigation and response. It is a complete security solution that:
- Is built-in to Windows 10 and uses a combination of Windows 10 and cloud services to catch suspicious endpoint behaviours.
- Automates alerts and remediation of complex threats in minutes.
- When used together with Microsoft 365, can share detection and exploration across devices, identities and information to speed up response and recovery.
- Requires no additional deployment or infrastructure and is always up to date.
Actions
- Fetch Investigation Package URI (Enrichment) - Retrieve a URI that allows downloading of an Investigation package.
- Get Machine Action Details (Enrichment) - Retrieve specific machine action by its ID.
- List Indicators (Enrichment) - Retrieve a collection of all active Indicators.
- List Machines (Enrichment) - Retrieves a collection of machines that have communicated with Microsoft Defender for Endpoint cloud.
- List Machine Actions (Enrichment) - Retrieves a collection of machine actions.
- Delete Indicator (Containment) - Delete an Indicator entity by ID.
- Isolate Machine (Containment) - Isolate a device from accessing external network.
- Release Machine From Isolation (Containment) - Undo isolation of a device.
- Run Antivirus Scan (Containment) - Initiate Microsoft Defender Antivirus scan on a device.
- Start Automated Investigation (Containment) - Start automated investigation on a device.
- Stop And Quarantine File (Containment) - Stop execution of a file on a device and delete it.
- Submit Indicator (Containment) - Submit or update new Indicator entity.
- Run Advanced Hunting Query (Custom) - Inspect unusual activity, detect possible threats and even respond to attacks.
- Collect Investigation Package (Scheduled) - Collect investigation package from a device.
Microsoft Defender ATP configuration
- Log in to Azure with a user that has the Global Administrator role. Navigate to Azure Active Directory > App registrations > New registration.
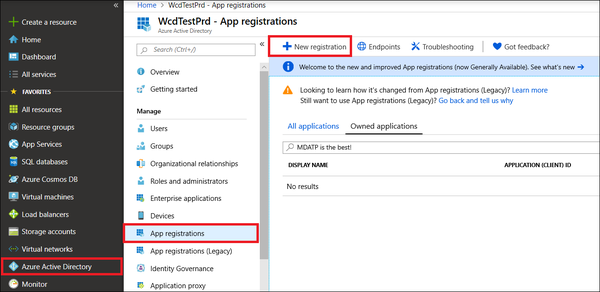
- Choose a name for your application, and then select Register. To enable your app to access Defender for Endpoint and assign it 'Read all alerts' permission, on your application page, select API Permissions > Add permission > APIs my organization uses, type WindowsDefenderATP, and then select WindowsDefenderATP.
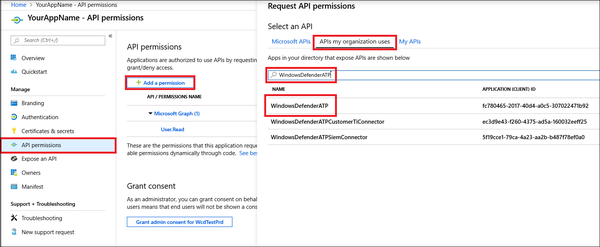
- Select the relevant permissions. For example, 'Read All Alerts'.
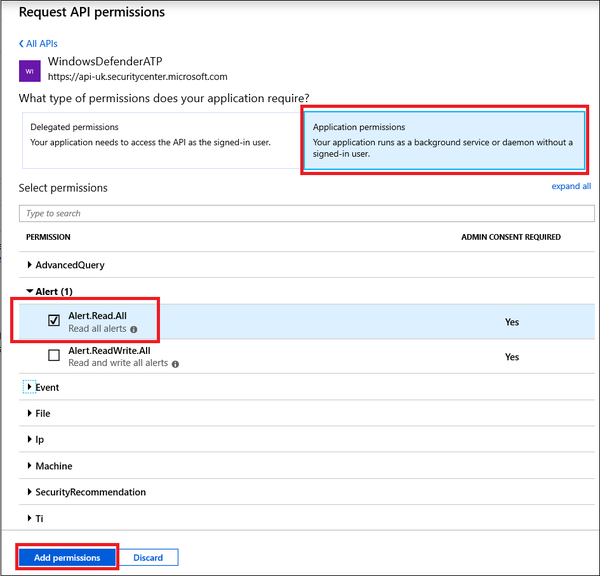
- All the permissions would be something like this.
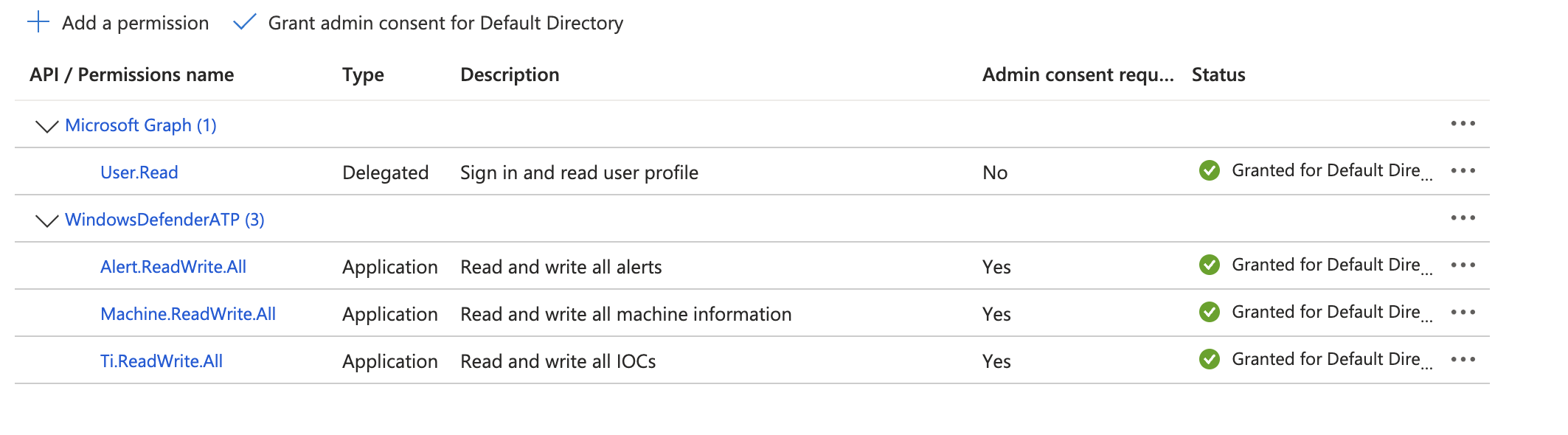
- Select Grant consent.

- Next, add a secret to the application. Select Certificates & secrets, add a description to the secret, and then select Add.
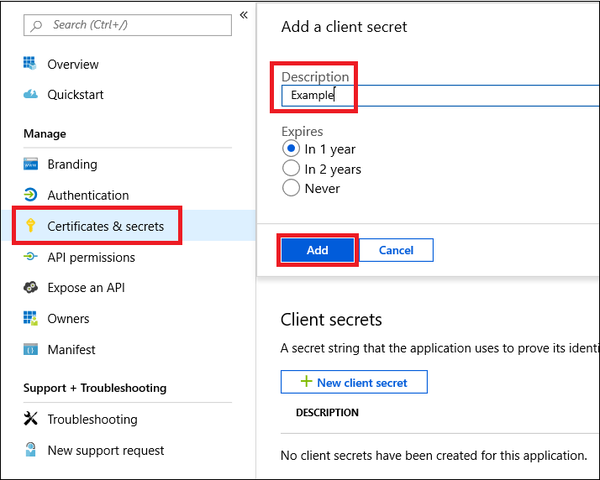
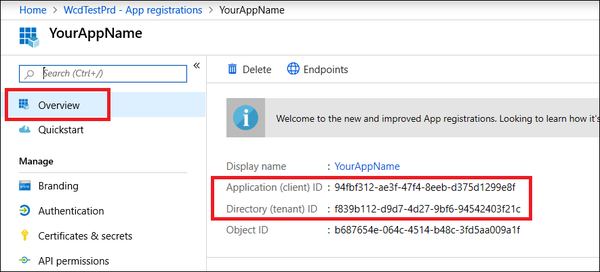
- Navigate to Overview, copy and save your application ID and your tenant ID.
Configure Microsoft Defender ATP in Automation Service and Cloud SOAR
Before you can use this automation integration, you must configure its authentication settings so that the product you're integrating with can communicate with Sumo Logic. For general guidance, see Configure Authentication for Automation Integrations.
How to open the integration's configuration dialog
- Access App Central and install the integration. (You can configure at installation, or after installation with the following steps.)
- Go to the Integrations page.
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar.
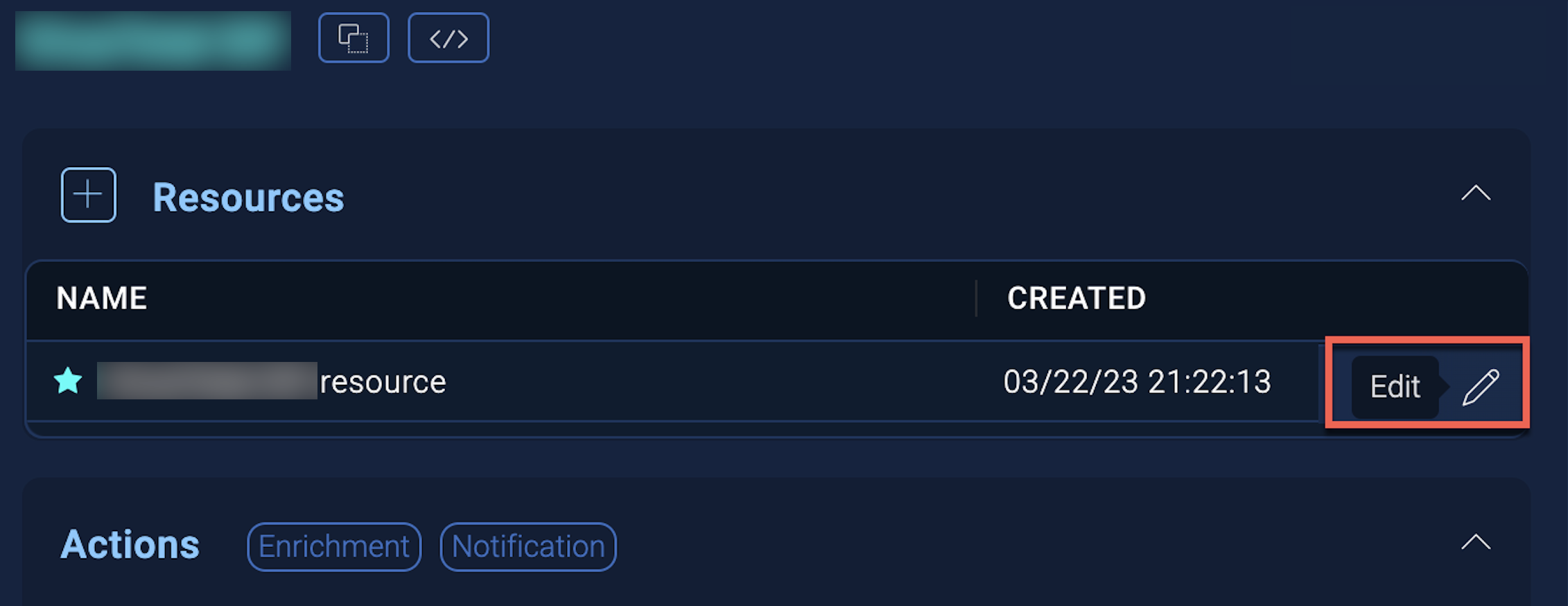
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations. - Select the installed integration.
- Hover over the resource name and click the Edit button that appears.
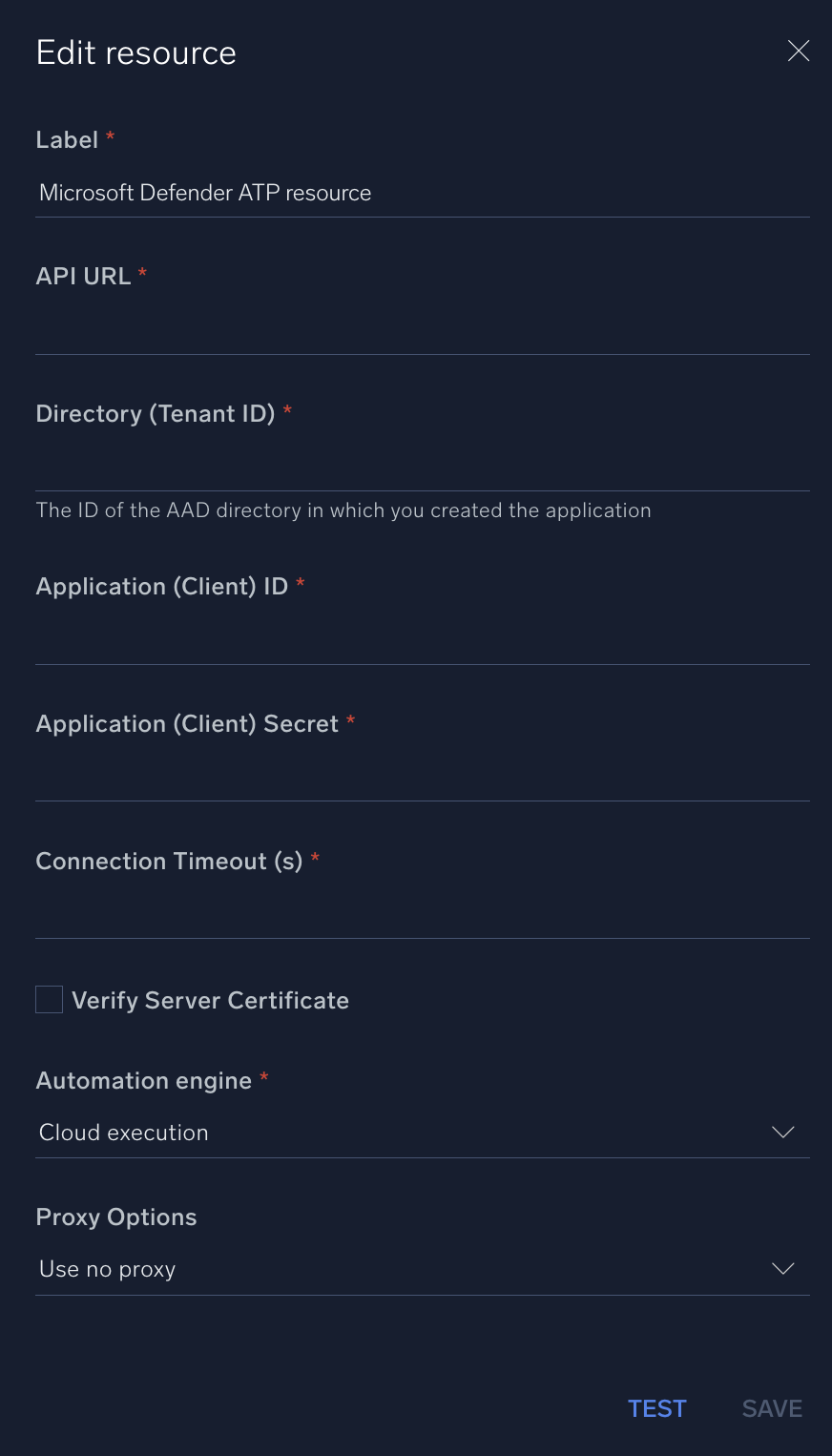
In the configuration dialog, enter information from the product you're integrating with. When done, click TEST to test the configuration, and click SAVE to save the configuration:
-
Label. Enter the name you want to use for the resource.
-
API URL. Enter the Microsoft Defender API URL for the server that is closer to your geo location:
api-us.securitycenter.microsoft.com*api-eu.securitycenter.microsoft.comapi-uk.securitycenter.microsoft.com
-
Directory (Tenant ID). Enter the tenant ID you copied earlier.
-
Application (Client) ID. Enter the client ID you copied earlier.
-
Application (Client) Secret. Enter the client secret you copied earlier.
-
Connection Timeout (s). Set the maximum amount of time the integration will wait for a server's response before terminating the connection. Enter the connection timeout time in seconds (for example,
180). -
Verify Server Certificate. Select to validate the server’s SSL certificate.
-
Automation Engine. Select Cloud execution for this certified integration. Select a bridge option only for a custom integration. See Cloud or Bridge execution.
-
Proxy Options. Select whether to use a proxy. (Applies only if the automation engine uses a bridge instead of cloud execution.)
- Use no proxy. Communication runs on the bridge and does not use a proxy.
- Use default proxy. Use the default proxy for the bridge set up as described in Using a proxy.
- Use different proxy. Use your own proxy service. Provide the proxy URL and port number.
For information about Microsoft Defender for Endpoint (formerly Defender ATP), see Microsoft Defender for Endpooint documentation.
Change Log
- December 15, 2022 - First upload
- May 4, 2021 - Actions updated: actions accept md5 hash
- January 4, 2023
- New Actions
- Fetch Investigation Package URI
- List Machines
- Start Automated Investigation
- Run Advanced Hunting Query
- Collect Investigation Package
- Modified Actions
- Get Machine Action Details
- List Indicators
- List Machine Actions
- Delete Indicator
- Isolate Machine
- Release Machine From Isolation
- Run Antivirus Scan
- Stop And Quarantine File
- Submit Indicator
- New Actions
- July 12, 2023 (v1.2) - Changed fields visibility