SentinelOne

Version: 1.9
Updated: Mar 4, 2024
SentinelOne Endpoint Protection Platform (EPP) unifies prevention, detection, and response in a single, purpose-built agent powered by machine learning and automation. It provides prevention and detection of attacks across all major vectors, rapid elimination of threats with fully automated, policy-driven response capabilities, and complete visibility into the endpoint environment with full-context, real-time forensics.
Actions
- Hash Reputation (Enrichment)- Gather hash reputation information.
- Add Blacklist Items (Containment) - Add a wildcard hash to blacklist.
- Get Blacklist Items (Enrichment) - Get blacklisted hashes.
- Delete Blacklist Items (Containment) - Remove a wildcard hash from blacklist.
- Get Threats (Enrichment) - Get all Threats.
- List Group IDs (Enrichment) - List Group IDs on the system.
- List Agents (Enrichment) - Listagents.
- Get Sites (Enrichment) - Get sites.
- Get Activities (Enrichment) - Get last activities.
- Connect to Network (Containment) - Reconnects an endpoint to the network.
- Disconnect from Network (Containment) - Isolates an endpoint from the network.
- Get Alerts (Enrichment) - Fetches base Alerts from SentinelOne.
- Update Alert SentinelOne (Notification) - Updates the Analyst Verdict of an alert(s).
- Monitor Threat Status (Scheduled) - Scheduled action that exits when the status of a threat is “resolved” (timeout currently set to 12 hours).
- Update Threat (Notification) - Updates the Status and Analyst Verdict of a SentinelOne Threat Incident.
- SentinelOne Threats Daemon (Daemon) - automatically ingest SentinelOne Threats.
Category
XDR
Configure SentinelOne in Automation Service and Cloud SOAR
Before you can use this automation integration, you must configure its authentication settings so that the product you're integrating with can communicate with Sumo Logic. For general guidance, see Configure Authentication for Automation Integrations.
How to open the integration's configuration dialog
- Access App Central and install the integration. (You can configure at installation, or after installation with the following steps.)
- Go to the Integrations page.
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar.
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations. - Select the installed integration.
- Hover over the resource name and click the Edit button that appears.
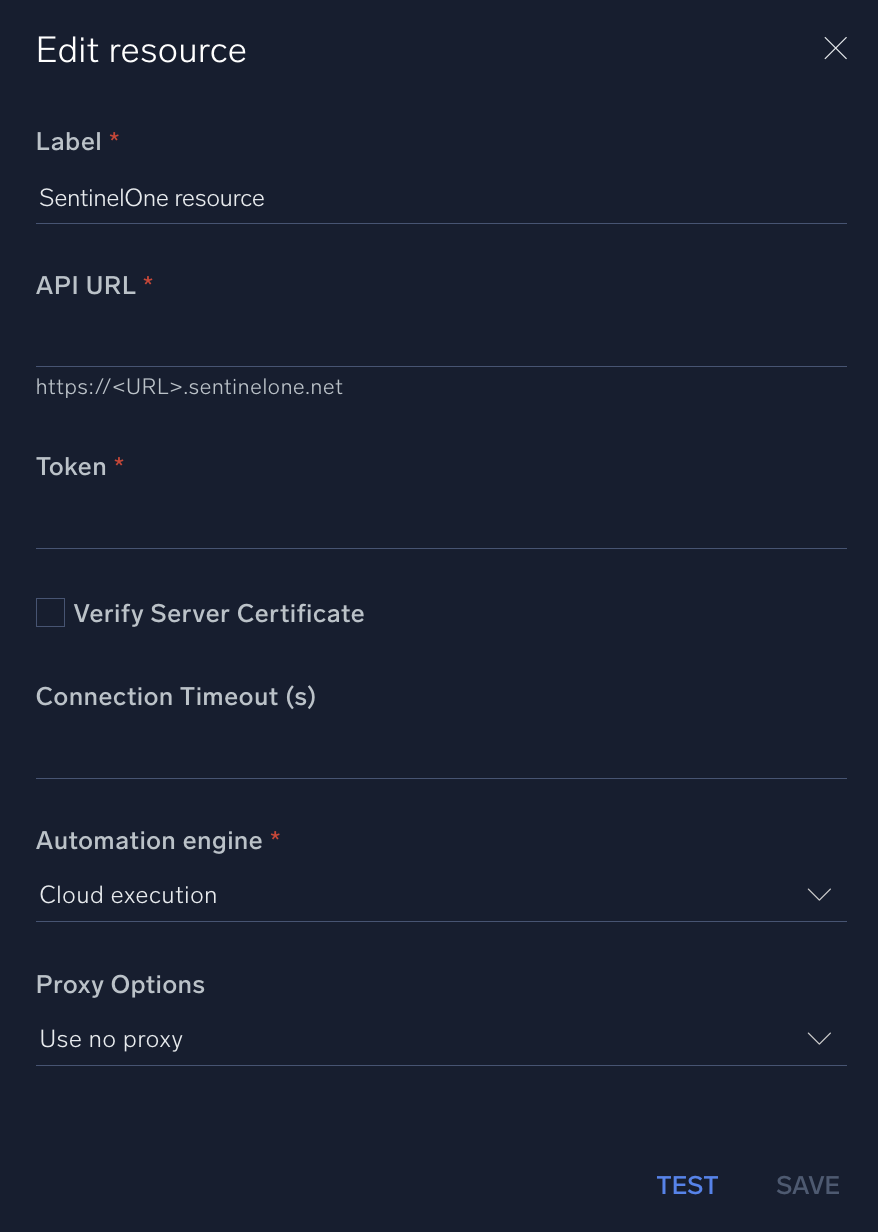
In the configuration dialog, enter information from the product you're integrating with. When done, click TEST to test the configuration, and click SAVE to save the configuration:
-
Label. Enter the name you want to use for the resource.
-
API URL. Enter your SentinelOne API URL, for example,
https://<URL>.sentinelone.net. -
Token. Enter your SentinelOne token.
-
Verify Server Certificate. Select to validate the server’s SSL certificate.
-
Connection Timeout (s). Set the maximum amount of time the integration will wait for a server's response before terminating the connection. Enter the connection timeout time in seconds (for example,
180). -
Automation Engine. Select Cloud execution for this certified integration. Select a bridge option only for a custom integration. See Cloud or Bridge execution.
-
Proxy Options. Select whether to use a proxy. (Applies only if the automation engine uses a bridge instead of cloud execution.)
- Use no proxy. Communication runs on the bridge and does not use a proxy.
- Use default proxy. Use the default proxy for the bridge set up as described in Using a proxy.
- Use different proxy. Use your own proxy service. Provide the proxy URL and port number.
For information about SentinelOne, see SentinelOne documentation.
Change Log
- March 26, 2021 - First upload
- July 19, 2022
- added default URL in the connector
- changed some labels in the connector
- August 30, 2022 - Added new actions:
- Connect to Network
- Disconnect from Network
- Get Alerts
- Update Alert SentinelOne
- Monitor Threat Status
- Update Threat
- SentinelOne Threats Daemon
- October 28, 2022 - Action Get Agents renamed to List Agents and refactored
- January 16, 2023 - Integration refactored
- January 30, 2023 - Updated Daemon
- SentinelOne Threats Daemon: refactored
- February 8, 2023 (v1.6)
- Updated Action: List Agents (Added IP field for filtering and Improved error handling)
- February 17, 2023 (v1.7)
- Updated Action: List Agents (Added Query field for Filtering)
- June 22, 2023 (v1.8) - Removed unnecessary spaces
- March 4, 2024 (v1.9) - Updated code for compatibility with Python 3.12