Sumo Logic Automation Tools

Version: 1.2
Updated: June 20, 2025
Sumo Logic Automation Tools simplifies Cloud SOAR playbooks with data processing and automation.
Actions
- Buffer (Custom) - Takes a JSON string or object and returns it as a JSON result. Helpful for dumping a JSON blob in string format and rendering in JSON format. See Buffer example.
- Data Transform (Custom) - Provides various functions to more easily transform data in a playbook. See Data Transfer example.
- Build JSON Object (Custom) - Provide the action with JSON key placeholder or string to build a new JSON object with the specified key/values. See Build JSON Object example.
- Build Signal Output (Custom) - Converts the Sumo Logic SIEM Signal JSON object to HTML or plain text with line breaks. See Build Signal Output example.
- Scaled Decimal to Percentage (Custom) - Converts a scaled decimal values between 0 and 1 into a percentage. See Scaled Decimal to Percentage.
Actions usage
Buffer
INPUT="MY EXAMPLE STRING"
OUTPUT = {
"data": "MY EXAMPLE STRING"
}
Data Transform
Split text
Splits a string into an array based on a delimiter and returns the specified element.
INPUT = {
"string_input": "MY,EXAMPLE,STRING",
"transform_function": "Split Text",
"transform_argument": ",",
"array_element": 1
}
OUTPUT = {
"result": "EXAMPLE"
}
Strip whitespace
Strips whitespace from the beginning and end of a string.
INPUT = {
"string_input": " MY EXAMPLE STRING ",
"transform_function": "Strip Whitespace"
"transform_argument": "MY"
}
OUTPUT = {
"result": "EXAMPLE STRING"
}
Trim leading whitespace
Trims leading whitespace from a string.
INPUT = {
"string_input": " MY EXAMPLE STRING",
"transform_function": "Lstrip"
}
OUTPUT = {
"result": "MY EXAMPLE STRING"
}
Trim trailing whitespace
Trims trailing whitespace from a string.
INPUT = {
"string_input": "MY EXAMPLE STRING ",
"transform_function": "Rstrip"
}
OUTPUT = {
"result": "MY EXAMPLE STRING"
}
Replace text
Replaces all occurrences of a string with another string.
INPUT = {
"string_input": "MY EXAMPLE STRING",
"transform_function": "Replace",
"transform_argument": "EXAMPLE",
"replace_argument": "REPLACED"
}
OUTPUT = {
"result": "MY REPLACED STRING"
}
Regex-based replacement
Replaces all occurrences of a regex pattern with another string.
INPUT = {
"string_input": "MY EXAMPLE STRING",
"transform_function": "Regex Replace",
"transform_argument": "EXAMPLE",
"replace_argument": "REPLACED"
}
OUTPUT = {
"result": "MY REPLACED STRING"
}
Add prefix and/or suffix
Adds a prefix and/or suffix to a string.
INPUT = {
"string_input": "EXAMPLE STRING",
"transform_function": "Prefix Suffix",
"prefix_argument": "MY ",
"suffix_argument": " STRING"
}
OUTPUT = {
"result": "MY EXAMPLE STRING"
}
Regex match
Matches a string against a regex pattern and returns the specified element.
INPUT = {
"string_input": "MY EXAMPLE STRING",
"transform_function": "Regex",
"transform_argument": "EXAMPLE"
"array_element": 0
}
OUTPUT = {
"result": "EXAMPLE"
}
Convert to uppercase
Converts a string to uppercase.
INPUT = {
"string_input": "my example string",
"transform_function": "Upper"
}
OUTPUT = {
"result": "MY EXAMPLE STRING"
}
Convert to lowercase
Converts a string to lowercase.
INPUT = {
"string_input": "MY EXAMPLE STRING",
"transform_function": "Lower"
}
OUTPUT = {
"result": "my example string"
}
Convert to title case
Converts a string to title case.
INPUT = {
"string_input": "my example string",
"transform_function": "Title"
}
OUTPUT = {
"result": "My Example String"
}
Capitalize first letter
Capitalizes the first letter of a string.
INPUT = {
"string_input": "my example string",
"transform_function": "Capitalize"
}
OUTPUT = {
"result": "My example string"
}
Encode as UTF-8
Encodes a string as UTF-8.
INPUT = {
"string_input": "Cafe",
"transform_function": "Encode UTF-8"
}
OUTPUT = {
"result": "b'Cafe\\xcc\\x81'"
}
Encode as ASCII
Encodes a string as ASCII.
INPUT = {
"string_input": a+b*c(d)e[f]",
"transform_function": "Encode ASCII"
}
OUTPUT = {
"result": "b'a+b*c(d)e[f]'"
}
Escape special characters
Escapes special characters in a string.
INPUT = {
"string_input": "a+b*c(d)e[f]",
"transform_function": "Escape String"
}
OUTPUT = {
"result": "a\\+b\\*c\\(d\\)e\\[f\\]"
}
Build JSON Object
Example:
{
"MY EXAMPLE KEY_1": "MY EXAMPLE VALUE",
"MY EXAMPLE KEY_2": "MY EXAMPLE VALUE",
"MY EXAMPLE KEY_3": ["MY EXAMPLE VALUE_1", "MY EXAMPLE VALUE_2"]
}
Input Fields For Every Key1, Key2, Key3
- JSON Key Placeholder -> MY EXAMPLE KEY_3
- JSON Value Placeholder -> (Whole JSON Object) eg . Any Action
output.raw
Output
{
"MY EXAMPLE KEY_3": ["MY EXAMPLE VALUE_1", "MY EXAMPLE VALUE_2"]
}
Build Signal Output
String input
- CASE 1: Input as
Get Insight V2 output.rawPreferred - CASE 2: Input as
Get Signal output.raw - CASE 3: Input as
Sumo Logic SIEM Signalas JSON
Output format type
- HTML with line breaks
- Plain Text With Line Breaks
Display time of timezone output
- List of Timezones
- Example:
America/New_York
Fields to exclude from output
- List Excluded Fields From Output
- Example:
field1, field2, field3
Fields to include from output
- List Included Fields From Output
- Example:
field1, field2, field3
INPUT example
{
"id": "07f3de36-4447-3c3b-a801-xxxxxx",
"readableId": "INSIGHT-00000",
"name": "Sumo Logic SIEM Signal",
"signals": [
{
"id": "38fd9c37-0df6-5333-86e5-xxxxxx",
"name": "Sumo Logic SIEM Signal",
"description": "This signal is triggered when a new process is created.",
"stage": "Execution",
"created": "2024-08-18T12:19:06.056000",
"timestamp": "2024-08-18T12:19:06.056000",
"severity": 1,
"recordCount": 1,
"recordTypes": [],
"contentType": "RULE",
"allRecords": [
{
"baseImage": "C:\\Program Files\\Rapid7\\Insight Agent\\components\\endpoint_broker\\",
"commandLine": "PowerShell \"$code = \\\"using System; using System.Linq; using System.Collections.Generic; using System.ComponentModel; using System.Runtime.InteropServices; using System.Security.Principal; using System.Text; namespace AuditEventPolicy { public class Collect { [DllImport(\\\"\\\"advapi32.dll\\\"\\\", SetLastError = false)] private static extern uint LsaClose(IntPtr ObjectHandle); [DllImport(\\\"\\\"advapi32.dll\\\"\\\", SetLastError = true)] private static extern uint LsaOpenPolicy( ref LSA_UNICODE_STRING SystemName, ref LSA_OBJECT_ATTRIBUTES ObjectAttributes, uint DesiredAccess, out IntPtr PolicyHandle); [DllImport(\\\"\\\"advapi32.dll\\\"\\\", SetLastError = false)] private static extern uint LsaNtStatusToWinError(uint status); [DllImport(\\\"\\\"advapi32.dll\\\"\\\")] private static extern uint LsaQueryInformationPolicy(IntPtr PolicyHandle, uint InformationClass, out IntPtr Buffer); internal const uint STATUS_SUCCESS = 0x00000000; internal const uint STATUS_ACCESS_DENIED = 0xC0000022; internal const uint STATUS_INSUFFICIENT_RESOURCES = 0xC000009A; internal const uint STATUS_INTERNAL_DB_ERROR = 0xC0000158; internal const uint STATUS_INVALID_HANDLE = 0xC0000008; internal const uint STATUS_INVALID_SERVER_STATE = 0xC00000DC; internal const uint STATUS_INVALID_PARAMETER = 0xC000000D; internal const uint STATUS_NO_SUCH_PRIVILEGE = 0xC0000060; internal const uint STATUS_OBJECT_NAME_NOT_FOUND = 0xC0000034; internal const uint STATUS_UNSUCCESSFUL = 0xC0000001; private static readonly Dictionary<uint, string> LsaNtStatusMessages = new Dictionary<uint, string>{ {STATUS_SUCCESS, \\\"\\\"The operation completed successfully.\\\"\\\"}, {STATUS_ACCESS_DENIED, \\\"\\\"Access is denied.\\\"\\\"}, {STATUS_INSUFFICIENT_RESOURCES, \\\"\\\"There are not enough system resources to complete the call.\\\"\\\"}, {STATUS_INTERNAL_DB_ERROR, \\\"\\\"The LSA database contains an internal inconsistency.\\\"\\\"}, {STATUS_INVALID_HANDLE, \\\"\\\"An object or RPC handle is not valid.\\\"\\\"}, {STATUS_INVALID_SERVER_STATE, \\\"\\\"The LSA server is currently disabled.\\\"\\\"}, {STATUS_INVALID_PARAMETER, \\\"\\\"One of the parameters is not valid.\\\"\\\"}, {STATUS_NO_SUCH_PRIVILEGE, \\\"\\\"A specified privilege does not exist.\\\"\\\"}, {STATUS_OBJECT_NAME_NOT_FOUND, \\\"\\\"An object in the LSA policy database was not found.\\\"\\\"}, {STATUS_UNSUCCESSFUL, \\\"\\\"The requested operation was unsuccessful.\\\"\\\"}}; [Flags]public enum LsaPolicyAccessRights : uint{ POLICY_VIEW_LOCAL_INFORMATION = 0x00000001, POLICY_VIEW_AUDIT_INFORMATION = 0x00000002, POLICY_GET_PRIVATE_INFORMATION = 0x00000004, POLICY_TRUST_ADMIN = 0x00000008, POLICY_CREATE_ACCOUNT = 0x00000010, POLICY_CREATE_SECRET = 0x00000020, POLICY_CREATE_PRIVILEGE = 0x00000040, POLICY_SET_DEFAULT_QUOTA_LIMITS = 0x00000080, POLICY_SET_AUDIT_REQUIREMENTS = 0x00000100, POLICY_AUDIT_LOG_ADMIN = 0x00000200, POLICY_SERVER_ADMIN = 0x00000400, POLICY_LOOKUP_NAMES = 0x00000800, POLICY_NOTIFICATION = 0x00001000, POLICY_ALL_ACCESS = POLICY_VIEW_LOCAL_INFORMATION |POLICY_VIEW_AUDIT_INFORMATION |POLICY_GET_PRIVATE_INFORMATION |POLICY_TRUST_ADMIN |POLICY_CREATE_ACCOUNT |POLICY_CREATE_SECRET |POLICY_CREATE_PRIVILEGE |POLICY_SET_DEFAULT_QUOTA_LIMITS |POLICY_SET_AUDIT_REQUIREMENTS |POLICY_AUDIT_LOG_ADMIN |POLICY_SERVER_ADMIN |POLICY_LOOKUP_NAMES |POLICY_NOTIFICATION} [StructLayout(LayoutKind.Sequential)]internal struct LSA_UNICODE_STRING{ internal ushort Length; internal ushort MaximumLength; internal IntPtr Buffer; } [StructLayout(LayoutKind.Sequential)]internal struct LSA_OBJECT_ATTRIBUTES{ internal uint Length; internal IntPtr RootDirectory; internal IntPtr ObjectName; internal uint Attributes; internal IntPtr SecurityDescriptor; internal IntPtr SecurityQualityOfService; } public struct POLICY_AUDIT_EVENTS_INFO{ public bool AuditingMode; public IntPtr EventAuditingOptions; public Int32 MaximumAuditEventCount; } private static void HandleLsaNtStatus(uint ntStatusCode){ if (ntStatusCode == STATUS_SUCCESS){ return; } var winErrorCode = (int)(LsaNtStatusToWinError(ntStatusCode)); if (LsaNtStatusMessages.ContainsKey(ntStatusCode)){ throw new Win32Exception(winErrorCode, LsaNtStatusMessages[ntStatusCode]); } throw new Win32Exception(winErrorCode); } private static IntPtr GetLsaPolicyHandle(){ var systemName = new LSA_UNICODE_STRING(); var objectAttributes = new LSA_OBJECT_ATTRIBUTES{ Length = 0, RootDirectory = IntPtr.Zero, ObjectName = IntPtr.Zero, Attributes = 0, SecurityDescriptor = IntPtr.Zero, SecurityQualityOfService = IntPtr.Zero}; IntPtr lsaPolicyHandle; var ntStatus = LsaOpenPolicy(ref systemName, ref objectAttributes, (uint)(LsaPolicyAccessRights.POLICY_ALL_ACCESS), out lsaPolicyHandle); HandleLsaNtStatus(ntStatus); return lsaPolicyHandle; } public static Dictionary<string, int> GetAuditEventPolicy(){ var settings = new Dictionary<string, int>{ {\\\"\\\"System\\\"\\\", -1}, {\\\"\\\"Logon\\\"\\\", -1}, {\\\"\\\"Object Access\\\"\\\", -1}, {\\\"\\\"Privilege Use\\\"\\\", -1}, {\\\"\\\"Detailed Tracking\\\"\\\", -1}, {\\\"\\\"Policy Change\\\"\\\", -1}, {\\\"\\\"Account Management\\\"\\\", -1}, {\\\"\\\"Directory Service Access\\\"\\\", -1}, {\\\"\\\"Account Logon\\\"\\\", -1}}; var lsaPolicyHandle = GetLsaPolicyHandle(); try{ IntPtr outBuffer; uint policyType = 2; var ntStatus = LsaQueryInformationPolicy(lsaPolicyHandle, policyType, out outBuffer); if (ntStatus == STATUS_OBJECT_NAME_NOT_FOUND){ return settings; } HandleLsaNtStatus(ntStatus); var auditEventsInfo = Marshal.PtrToStructure<POLICY_AUDIT_EVENTS_INFO>(outBuffer); var values = new int[auditEventsInfo.MaximumAuditEventCount]; Marshal.Copy(auditEventsInfo.EventAuditingOptions, values, 0, auditEventsInfo.MaximumAuditEventCount); var categoryIndex = settings.Keys.ToArray(); for (int i = 0; i < values.Length; i++){ settings[categoryIndex[i]] = values[i]; } return settings; } finally{ var ntStatus = LsaClose(lsaPolicyHandle); HandleLsaNtStatus(ntStatus); } } } } \\\";$previousEncoding = [Console]::OutputEncoding;[Console]::OutputEncoding = [Text.Encoding]::UTF8;Add-Type -TypeDefinition $code -Language CSharp;@([AuditEventPolicy.Collect]::GetAuditEventPolicy()) | ConvertTo-Json;[Console]::OutputEncoding = $previousEncoding;\"",
"cseSignal": {},
"day": 18,
"description": "A new process has been created",
"device_hostname": "sjcd1pwadiap001",
"device_hostname_raw": "SJCD1PWADIAP001.ihgint.global",
"fieldTags": {},
"fields": {
"EventData.ProcessId": "0x11f0",
},
}
],
"ruleId": "MATCH-S00198",
"entity": {
},
"artifacts": [],
"recordSearchDetails": null
}
]
}
OUTPUT example
HTML
{
"signals": [
"<b>Signal time:</b> 2024-08-18 12:19:06.056000+00:00<br/><b>Name:</b> Sumo Logic SIEM Signal<br/><b>Rule:</b> MATCH-S00198<br/><b>Stage:</b> Execution<br/><b>Entity Name:</b> <br/><b>baseImage:</b> C:\\\\Program Files\\\\Rapid7\\\\Insight Agent\\\\components\\\\endpoint_broker\\\\<br/><b>commandLine:</b> PowerShell '$code = 'using System; using System.Linq; using System.Collections.Generic; using System.ComponentModel; using System.Runtime.InteropServices; using System.Security.Principal; using System.Text; namespace AuditEventPolicy { public class Collect { [DllImport(''advapi32.dll'', SetLastError = false)] private static extern uint LsaClose(IntPtr ObjectHandle); [DllImport(''advapi32.dll'', SetLastError = true)] private static extern uint LsaOpenPolicy( ref LSA_UNICODE_STRING SystemName, ref LSA_OBJECT_ATTRIBUTES ObjectAttributes, uint DesiredAccess, out IntPtr PolicyHandle); [DllImport(''advapi32.dll'', SetLastError = false)] private static extern uint LsaNtStatusToWinError(uint status); [DllImport(''advapi32.dll'')] private static extern uint LsaQueryInformationPolicy(IntPtr PolicyHandle, uint InformationClass, out IntPtr Buffer); internal const uint STATUS_SUCCESS = 0x00000000; internal const uint STATUS_ACCESS_DENIED = 0xC0000022; internal const uint STATUS_INSUFFICIENT_RESOURCES = 0xC000009A; internal const uint STATUS_INTERNAL_DB_ERROR = 0xC0000158; internal const uint STATUS_INVALID_HANDLE = 0xC0000008; internal const uint STATUS_INVALID_SERVER_STATE = 0xC00000DC; internal const uint STATUS_INVALID_PARAMETER = 0xC000000D; internal const uint STATUS_NO_SUCH_PRIVILEGE = 0xC0000060; internal const uint STATUS_OBJECT_NAME_NOT_FOUND = 0xC0000034; internal const uint STATUS_UNSUCCESSFUL = 0xC0000001; private static readonly Dictionary<uint, string> LsaNtStatusMessages = new Dictionary<uint, string>{ {STATUS_SUCCESS, ''The operation completed successfully.''}, {STATUS_ACCESS_DENIED, ''Access is denied.''}, {STATUS_INSUFFICIENT_RESOURCES, ''There are not enough system resources to complete the call.''}, {STATUS_INTERNAL_DB_ERROR, ''The LSA database contains an internal inconsistency.''}, {STATUS_INVALID_HANDLE, ''An object or RPC handle is not valid.''}, {STATUS_INVALID_SERVER_STATE, ''The LSA server is currently disabled.''}, {STATUS_INVALID_PARAMETER, ''One of the parameters is not valid.''}, {STATUS_NO_SUCH_PRIVILEGE, ''A specified privilege does not exist.''}, {STATUS_OBJECT_NAME_NOT_FOUND, ''An object in the LSA policy database was not found.''}, {STATUS_UNSUCCESSFUL, ''The requested operation was unsuccessful.''}}; [Flags]public enum LsaPolicyAccessRights : uint{ POLICY_VIEW_LOCAL_INFORMATION = 0x00000001, POLICY_VIEW_AUDIT_INFORMATION = 0x00000002, POLICY_GET_PRIVATE_INFORMATION = 0x00000004, POLICY_TRUST_ADMIN = 0x00000008, POLICY_CREATE_ACCOUNT = 0x00000010, POLICY_CREATE_SECRET = 0x00000020, POLICY_CREATE_PRIVILEGE = 0x00000040, POLICY_SET_DEFAULT_QUOTA_LIMITS = 0x00000080, POLICY_SET_AUDIT_REQUIREMENTS = 0x00000100, POLICY_AUDIT_LOG_ADMIN = 0x00000200, POLICY_SERVER_ADMIN = 0x00000400, POLICY_LOOKUP_NAMES = 0x00000800, POLICY_NOTIFICATION = 0x00001000, POLICY_ALL_ACCESS = POLICY_VIEW_LOCAL_INFORMATION |POLICY_VIEW_AUDIT_INFORMATION |POLICY_GET_PRIVATE_INFORMATION |POLICY_TRUST_ADMIN |POLICY_CREATE_ACCOUNT |POLICY_CREATE_SECRET |POLICY_CREATE_PRIVILEGE |POLICY_SET_DEFAULT_QUOTA_LIMITS |POLICY_SET_AUDIT_REQUIREMENTS |POLICY_AUDIT_LOG_ADMIN |POLICY_SERVER_ADMIN |POLICY_LOOKUP_NAMES |POLICY_NOTIFICATION} [StructLayout(LayoutKind.Sequential)]internal struct LSA_UNICODE_STRING{ internal ushort Length; internal ushort MaximumLength; internal IntPtr Buffer; } [StructLayout(LayoutKind.Sequential)]internal struct LSA_OBJECT_ATTRIBUTES{ internal uint Length; internal IntPtr RootDirectory; internal IntPtr ObjectName; internal uint Attributes; internal IntPtr SecurityDescriptor; internal IntPtr SecurityQualityOfService; } public struct POLICY_AUDIT_EVENTS_INFO{ public bool AuditingMode; public IntPtr EventAuditingOptions; public Int32 MaximumAuditEventCount; } private static void HandleLsaNtStatus(uint ntStatusCode){ if (ntStatusCode == STATUS_SUCCESS){ return; } var winErrorCode = (int)(LsaNtStatusToWinError(ntStatusCode)); if (LsaNtStatusMessages.ContainsKey(ntStatusCode)){ throw new Win32Exception(winErrorCode, LsaNtStatusMessages[ntStatusCode]); } throw new Win32Exception(winErrorCode); } private static IntPtr GetLsaPolicyHandle(){ var systemName = new LSA_UNICODE_STRING(); var objectAttributes = new LSA_OBJECT_ATTRIBUTES{ Length = 0, RootDirectory = IntPtr.Zero, ObjectName = IntPtr.Zero, Attributes = 0, SecurityDescriptor = IntPtr.Zero, SecurityQualityOfService = IntPtr.Zero}; IntPtr lsaPolicyHandle; var ntStatus = LsaOpenPolicy(ref systemName, ref objectAttributes, (uint)(LsaPolicyAccessRights.POLICY_ALL_ACCESS), out lsaPolicyHandle); HandleLsaNtStatus(ntStatus); return lsaPolicyHandle; } public static Dictionary<string, int> GetAuditEventPolicy(){ var settings = new Dictionary<string, int>{ {''System'', -1}, {''Logon'', -1}, {''Object Access'', -1}, {''Privilige Use'', -1}, {''Detailed Tracking'', -1}, {''Policy Change'', -1}, {''Account Management'', -1}, {''Directory Service Access'', -1}, {''Account Logon'', -1}}; var lsaPolicyHandle = GetLsaPolicyHandle(); try{ IntPtr outBuffer; uint policyType = 2; var ntStatus = LsaQueryInformationPolicy(lsaPolicyHandle, policyType, out outBuffer); if (ntStatus == STATUS_OBJECT_NAME_NOT_FOUND){ return settings; } HandleLsaNtStatus(ntStatus); var auditEventsInfo = Marshal.PtrToStructure<POLICY_AUDIT_EVENTS_INFO>(outBuffer); var values = new int[auditEventsInfo.MaximumAuditEventCount]; Marshal.Copy(auditEventsInfo.EventAuditingOptions, values, 0, auditEventsInfo.MaximumAuditEventCount); var categoryIndex = settings.Keys.ToArray(); for (int i = 0; i < values.Length; i++){ settings[categoryIndex[i]] = values[i]; } return settings; } finally{ var ntStatus = LsaClose(lsaPolicyHandle); HandleLsaNtStatus(ntStatus); } } } } ';$previousEncoding = [Console]::OutputEncoding;[Console]::OutputEncoding = [Text.Encoding]::UTF8;Add-Type -TypeDefinition $code -Language CSharp;@([AuditEventPolicy.Collect]::GetAuditEventPolicy()) | ConvertTo-Json;[Console]::OutputEncoding = $previousEncoding;'<br/><b>day:</b> 18<br/><b>description:</b> A new process has been created<br/><b>device_hostname:</b> sjcd1pwadiap001<br/><b>device_hostname_raw:</b> SJCD1PWADIAP001.ihgint.global<br/><br/>"
]
}
Break Lines
{
"signals": [
"Signal time: 2024-08-18 12:19:06.056000+00:00\\nSignal Name: Sumo Logic SIEM Signal\\nRule: MATCH-S00198\\nStage: Execution\\nEntity Name: \\nbaseImage: C:\\\\Program Files\\\\Rapid7\\\\Insight Agent\\\\components\\\\endpoint_broker\\\\\\ncommandLine: PowerShell '$code = 'using System; using System.Linq; using System.Collections.Generic; using System.ComponentModel; using System.Runtime.InteropServices; using System.Security.Principal; using System.Text; namespace AuditEventPolicy { public class Collect { [DllImport(''advapi32.dll'', SetLastError = false)] private static extern uint LsaClose(IntPtr ObjectHandle); [DllImport(''advapi32.dll'', SetLastError = true)] private static extern uint LsaOpenPolicy( ref LSA_UNICODE_STRING SystemName, ref LSA_OBJECT_ATTRIBUTES ObjectAttributes, uint DesiredAccess, out IntPtr PolicyHandle); [DllImport(''advapi32.dll'', SetLastError = false)] private static extern uint LsaNtStatusToWinError(uint status); [DllImport(''advapi32.dll'')] private static extern uint LsaQueryInformationPolicy(IntPtr PolicyHandle, uint InformationClass, out IntPtr Buffer); internal const uint STATUS_SUCCESS = 0x00000000; internal const uint STATUS_ACCESS_DENIED = 0xC0000022; internal const uint STATUS_INSUFFICIENT_RESOURCES = 0xC000009A; internal const uint STATUS_INTERNAL_DB_ERROR = 0xC0000158; internal const uint STATUS_INVALID_HANDLE = 0xC0000008; internal const uint STATUS_INVALID_SERVER_STATE = 0xC00000DC; internal const uint STATUS_INVALID_PARAMETER = 0xC000000D; internal const uint STATUS_NO_SUCH_PRIVILEGE = 0xC0000060; internal const uint STATUS_OBJECT_NAME_NOT_FOUND = 0xC0000034; internal const uint STATUS_UNSUCCESSFUL = 0xC0000001; private static readonly Dictionary<uint, string> LsaNtStatusMessages = new Dictionary<uint, string>{ {STATUS_SUCCESS, ''The operation completed successfully.''}, {STATUS_ACCESS_DENIED, ''Access is denied.''}, {STATUS_INSUFFICIENT_RESOURCES, ''There are not enough system resources to complete the call.''}, {STATUS_INTERNAL_DB_ERROR, ''The LSA database contains an internal inconsistency.''}, {STATUS_INVALID_HANDLE, ''An object or RPC handle is not valid.''}, {STATUS_INVALID_SERVER_STATE, ''The LSA server is currently disabled.''}, {STATUS_INVALID_PARAMETER, ''One of the parameters is not valid.''}, {STATUS_NO_SUCH_PRIVILEGE, ''A specified privilege does not exist.''}, {STATUS_OBJECT_NAME_NOT_FOUND, ''An object in the LSA policy database was not found.''}, {STATUS_UNSUCCESSFUL, ''The requested operation was unsuccessful.''}}; [Flags]public enum LsaPolicyAccessRights : uint{ POLICY_VIEW_LOCAL_INFORMATION = 0x00000001, POLICY_VIEW_AUDIT_INFORMATION = 0x00000002, POLICY_GET_PRIVATE_INFORMATION = 0x00000004, POLICY_TRUST_ADMIN = 0x00000008, POLICY_CREATE_ACCOUNT = 0x00000010, POLICY_CREATE_SECRET = 0x00000020, POLICY_CREATE_PRIVILEGE = 0x00000040, POLICY_SET_DEFAULT_QUOTA_LIMITS = 0x00000080, POLICY_SET_AUDIT_REQUIREMENTS = 0x00000100, POLICY_AUDIT_LOG_ADMIN = 0x00000200, POLICY_SERVER_ADMIN = 0x00000400, POLICY_LOOKUP_NAMES = 0x00000800, POLICY_NOTIFICATION = 0x00001000, POLICY_ALL_ACCESS = POLICY_VIEW_LOCAL_INFORMATION |POLICY_VIEW_AUDIT_INFORMATION |POLICY_GET_PRIVATE_INFORMATION |POLICY_TRUST_ADMIN |POLICY_CREATE_ACCOUNT |POLICY_CREATE_SECRET |POLICY_CREATE_PRIVILEGE |POLICY_SET_DEFAULT_QUOTA_LIMITS |POLICY_SET_AUDIT_REQUIREMENTS |POLICY_AUDIT_LOG_ADMIN |POLICY_SERVER_ADMIN |POLICY_LOOKUP_NAMES |POLICY_NOTIFICATION} [StructLayout(LayoutKind.Sequential)]internal struct LSA_UNICODE_STRING{ internal ushort Length; internal ushort MaximumLength; internal IntPtr Buffer; } [StructLayout(LayoutKind.Sequential)]internal struct LSA_OBJECT_ATTRIBUTES{ internal uint Length; internal IntPtr RootDirectory; internal IntPtr ObjectName; internal uint Attributes; internal IntPtr SecurityDescriptor; internal IntPtr SecurityQualityOfService; } public struct POLICY_AUDIT_EVENTS_INFO{ public bool AuditingMode; public IntPtr EventAuditingOptions; public Int32 MaximumAuditEventCount; } private static void HandleLsaNtStatus(uint ntStatusCode){ if (ntStatusCode == STATUS_SUCCESS){ return; } var winErrorCode = (int)(LsaNtStatusToWinError(ntStatusCode)); if (LsaNtStatusMessages.ContainsKey(ntStatusCode)){ throw new Win32Exception(winErrorCode, LsaNtStatusMessages[ntStatusCode]); } throw new Win32Exception(winErrorCode); } private static IntPtr GetLsaPolicyHandle(){ var systemName = new LSA_UNICODE_STRING(); var objectAttributes = new LSA_OBJECT_ATTRIBUTES{ Length = 0, RootDirectory = IntPtr.Zero, ObjectName = IntPtr.Zero, Attributes = 0, SecurityDescriptor = IntPtr.Zero, SecurityQualityOfService = IntPtr.Zero}; IntPtr lsaPolicyHandle; var ntStatus = LsaOpenPolicy(ref systemName, ref objectAttributes, (uint)(LsaPolicyAccessRights.POLICY_ALL_ACCESS), out lsaPolicyHandle); HandleLsaNtStatus(ntStatus); return lsaPolicyHandle; } public static Dictionary<string, int> GetAuditEventPolicy(){ var settings = new Dictionary<string, int>{ {''System'', -1}, {''Logon'', -1}, {''Object Access'', -1}, {''Privilige Use'', -1}, {''Detailed Tracking'', -1}, {''Policy Change'', -1}, {''Account Management'', -1}, {''Directory Service Access'', -1}, {''Account Logon'', -1}}; var lsaPolicyHandle = GetLsaPolicyHandle(); try{ IntPtr outBuffer; uint policyType = 2; var ntStatus = LsaQueryInformationPolicy(lsaPolicyHandle, policyType, out outBuffer); if (ntStatus == STATUS_OBJECT_NAME_NOT_FOUND){ return settings; } HandleLsaNtStatus(ntStatus); var auditEventsInfo = Marshal.PtrToStructure<POLICY_AUDIT_EVENTS_INFO>(outBuffer); var values = new int[auditEventsInfo.MaximumAuditEventCount]; Marshal.Copy(auditEventsInfo.EventAuditingOptions, values, 0, auditEventsInfo.MaximumAuditEventCount); var categoryIndex = settings.Keys.ToArray(); for (int i = 0; i < values.Length; i++){ settings[categoryIndex[i]] = values[i]; } return settings; } finally{ var ntStatus = LsaClose(lsaPolicyHandle); HandleLsaNtStatus(ntStatus); } } } } ';$previousEncoding = [Console]::OutputEncoding;[Console]::OutputEncoding = [Text.Encoding]::UTF8;Add-Type -TypeDefinition $code -Language CSharp;@([AuditEventPolicy.Collect]::GetAuditEventPolicy()) | ConvertTo-Json;[Console]::OutputEncoding = $previousEncoding;'\\nday: 18\\ndescription: A new process has been created\\ndevice_hostname: sjcd1pwadiap001\\ndevice_hostname_raw: SJCD1PWADIAP001.ihgint.global\\n\\n"
]
}
Scaled Decimal to Percentage
INPUT = "1"
OUTPUT = {
"cs_val": "100"
}
INPUT = "0.1"
OUTPUT = {
"cs_val": "10"
}
INPUT = "0.01"
OUTPUT = {
"cs_val": "1"
}
INPUT = ".5"
OUTPUT = {
"cs_val": "50"
}
Configure Sumo Logic Automation Tools in Automation Service and Cloud SOAR
Before you can use this automation integration, you must configure its authentication settings so that the product you're integrating with can communicate with Sumo Logic. For general guidance, see Configure Authentication for Automation Integrations.
How to open the integration's configuration dialog
- Access App Central and install the integration. (You can configure at installation, or after installation with the following steps.)
- Go to the Integrations page.
Classic UI. In the main Sumo Logic menu, select Automation and then select Integrations in the left nav bar.
New UI. In the main Sumo Logic menu, select Automation > Integrations. You can also click the Go To... menu at the top of the screen and select Integrations. - Select the installed integration.
- Hover over the resource name and click the Edit button that appears.
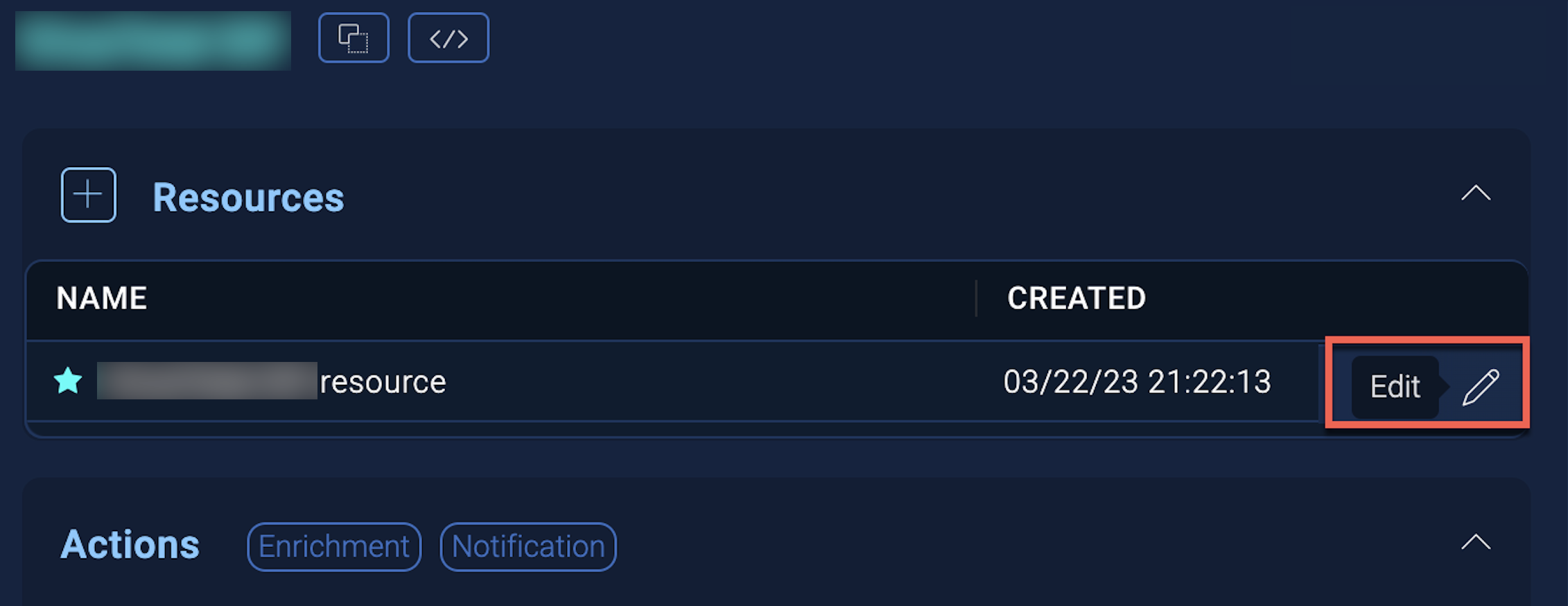
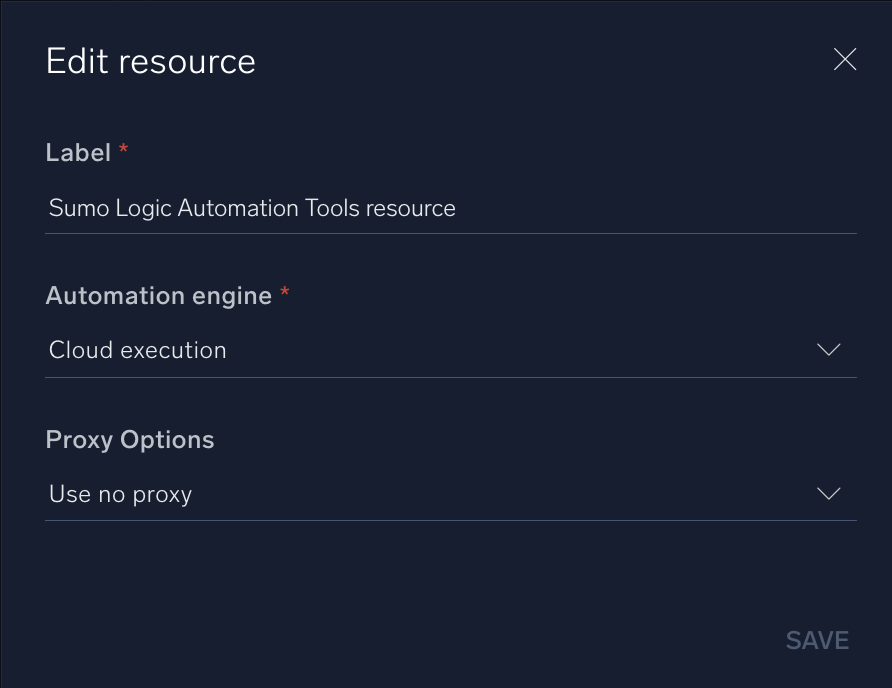
In the configuration dialog, enter information from the product you're integrating with. When done, click TEST to test the configuration, and click SAVE to save the configuration:
-
Label. Enter the name you want to use for the resource.
-
Automation Engine. Select Cloud execution for this certified integration. Select a bridge option only for a custom integration. See Cloud or Bridge execution.
-
Proxy Options. Select whether to use a proxy. (Applies only if the automation engine uses a bridge instead of cloud execution.)
- Use no proxy. Communication runs on the bridge and does not use a proxy.
- Use default proxy. Use the default proxy for the bridge set up as described in Using a proxy.
- Use different proxy. Use your own proxy service. Provide the proxy URL and port number.
No authentication configuration is needed. Sumo Logic Automation Tools executes without additional authentication.
Change log
- Nov 11, 2024 - Beta version released.
- May 23, 2025 - Introduced the new "Scaled Decimal to Percentage" action, which converts a scaled decimal value into a percentage.
- June 20, 2025 - Removed
%sign from the output.