Google Workspace User Inventory Source

The Google Workspace User Inventory source collects a list of users from the Google Workspace Users API. It securely stores the required authentication, scheduling, and state tracking information.
Data collected
| Polling Interval | Data |
|---|---|
| 24 hours | Users |
Setup
Vendor configuration
In this configuration, you will set up a Google Workspace User Inventory source account and configure it to be authorized and authenticated to use Google Workspace User Inventory. To set up a Google Workspace User Inventory account, you need to configure Google service account credentials. You may refer to the Google Documentation for more information.
Creating Service Account
To create service account credentials, follow the steps below:
- Navigate to the Google Console service account page.
- Log in with your credentials.
- Create a new project or select from the existing projects.
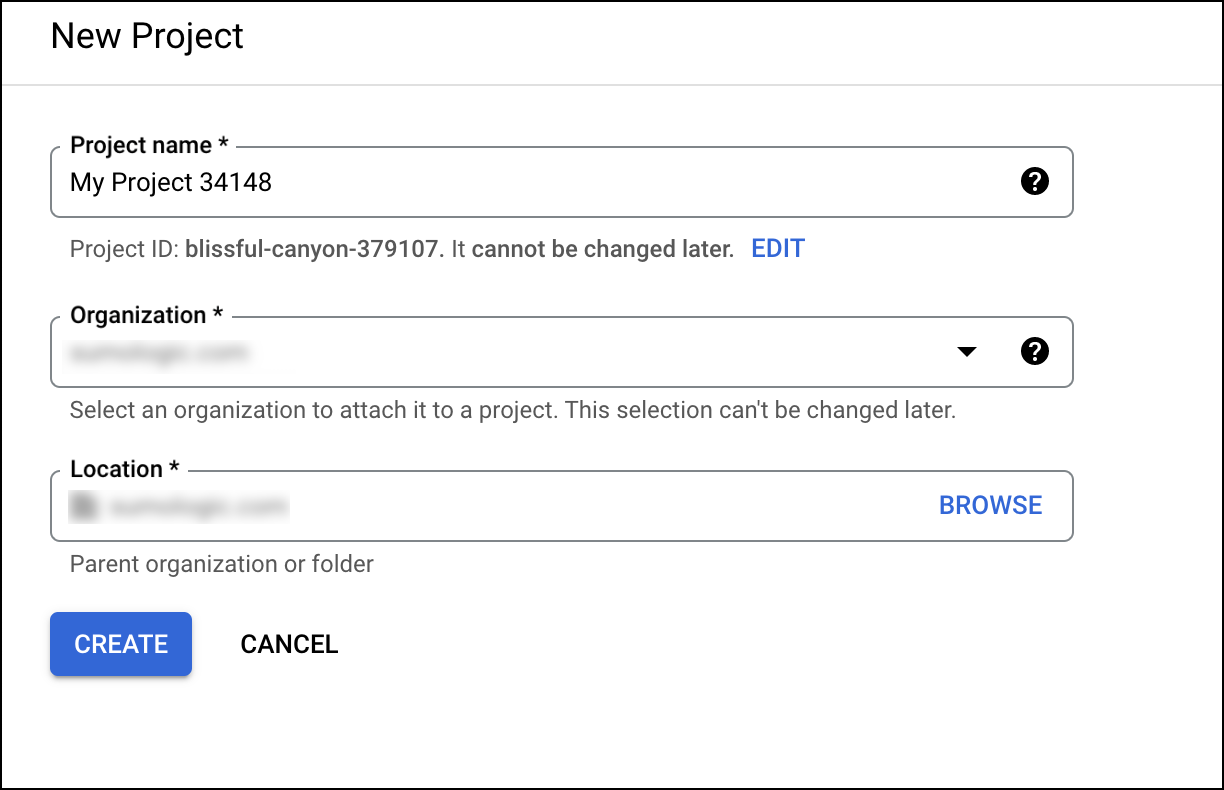
- Enable Admin SDK API to have an administrator access. To locate this setting, you can search for Admin SDK in the search bar. Then select the Enable button.
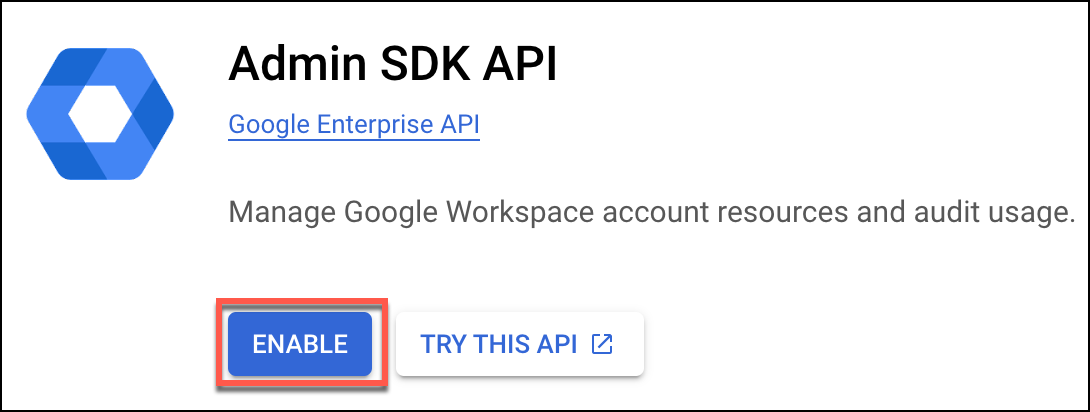
- You will be redirected to the Admin dashboard page. Select the Credentials option from the left navigation.
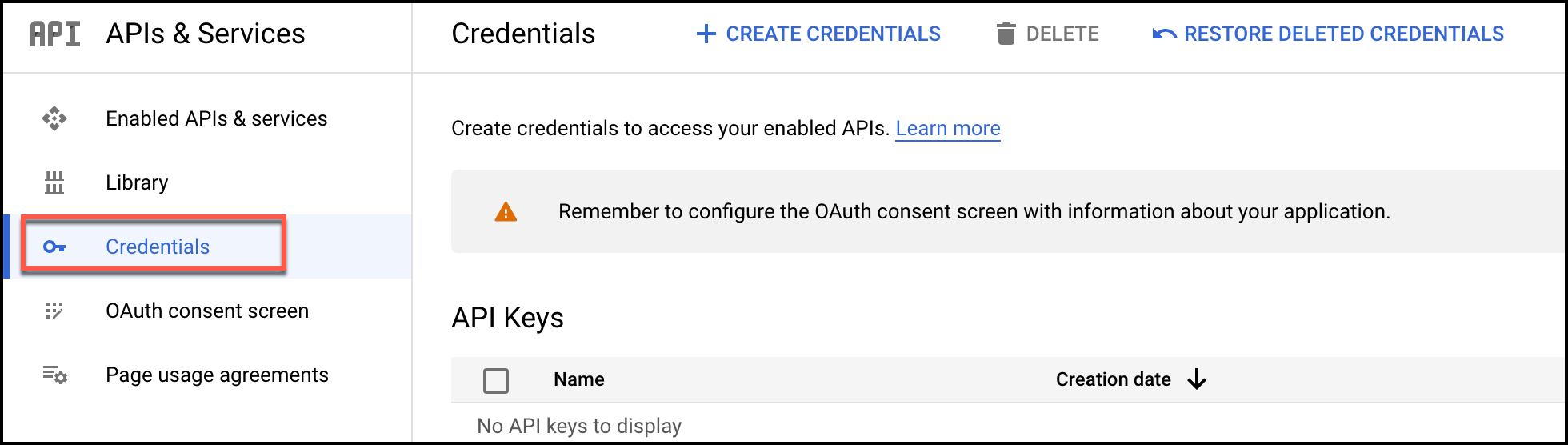
- Click the
 button at the menu bar of the Google Console page, and select Service account from the options that appear.
button at the menu bar of the Google Console page, and select Service account from the options that appear.
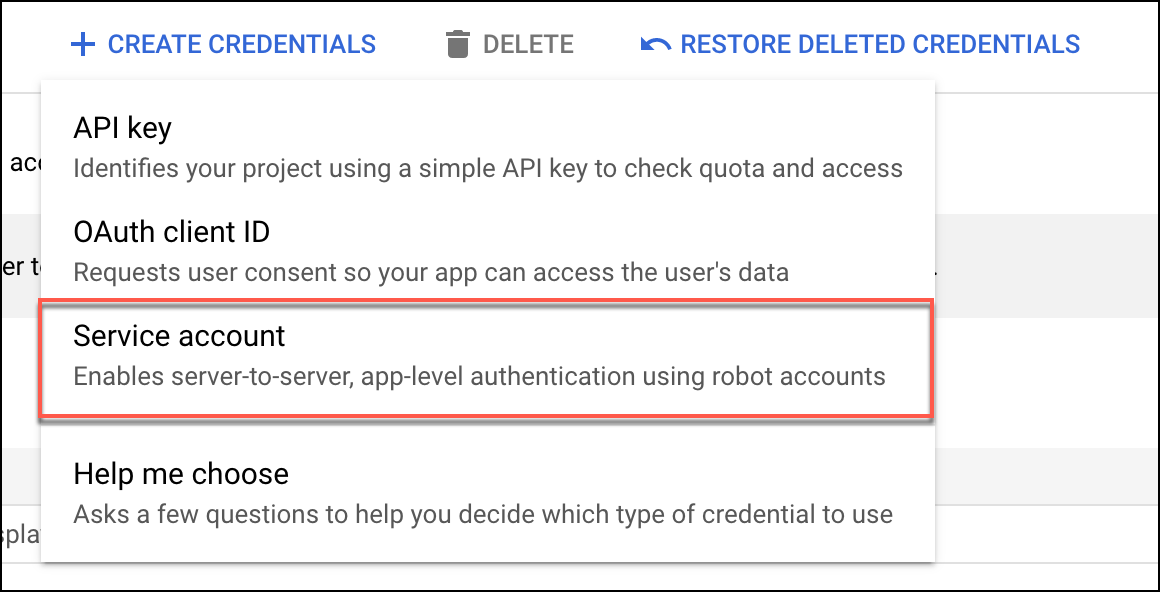
- After entering the service account details, you may leave the Optional fields and continue to click Done.
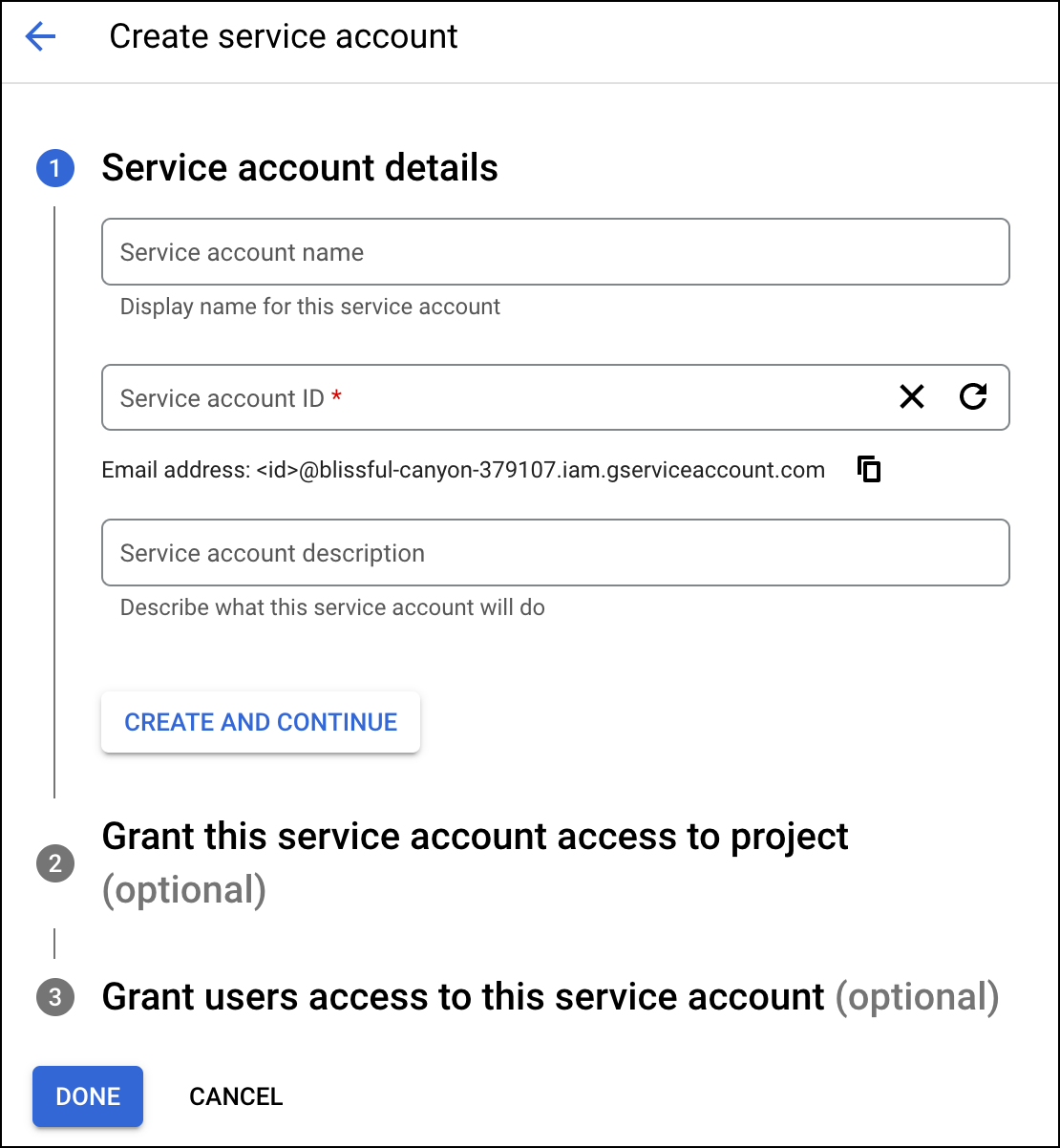
- To create JSON for the service account, you must create a key. Select the service account email to navigate to the Keys tab.
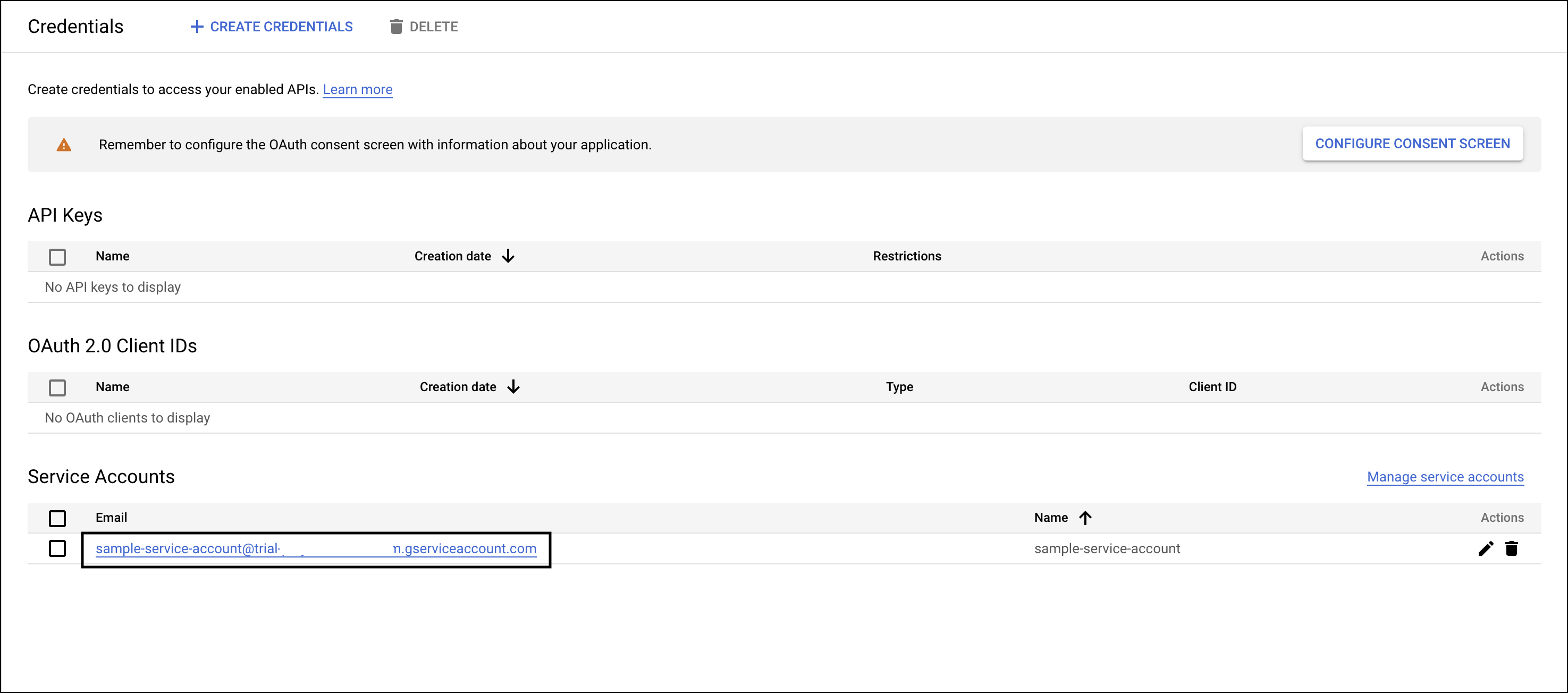 .
. - Click Keys tab on the same service account page.
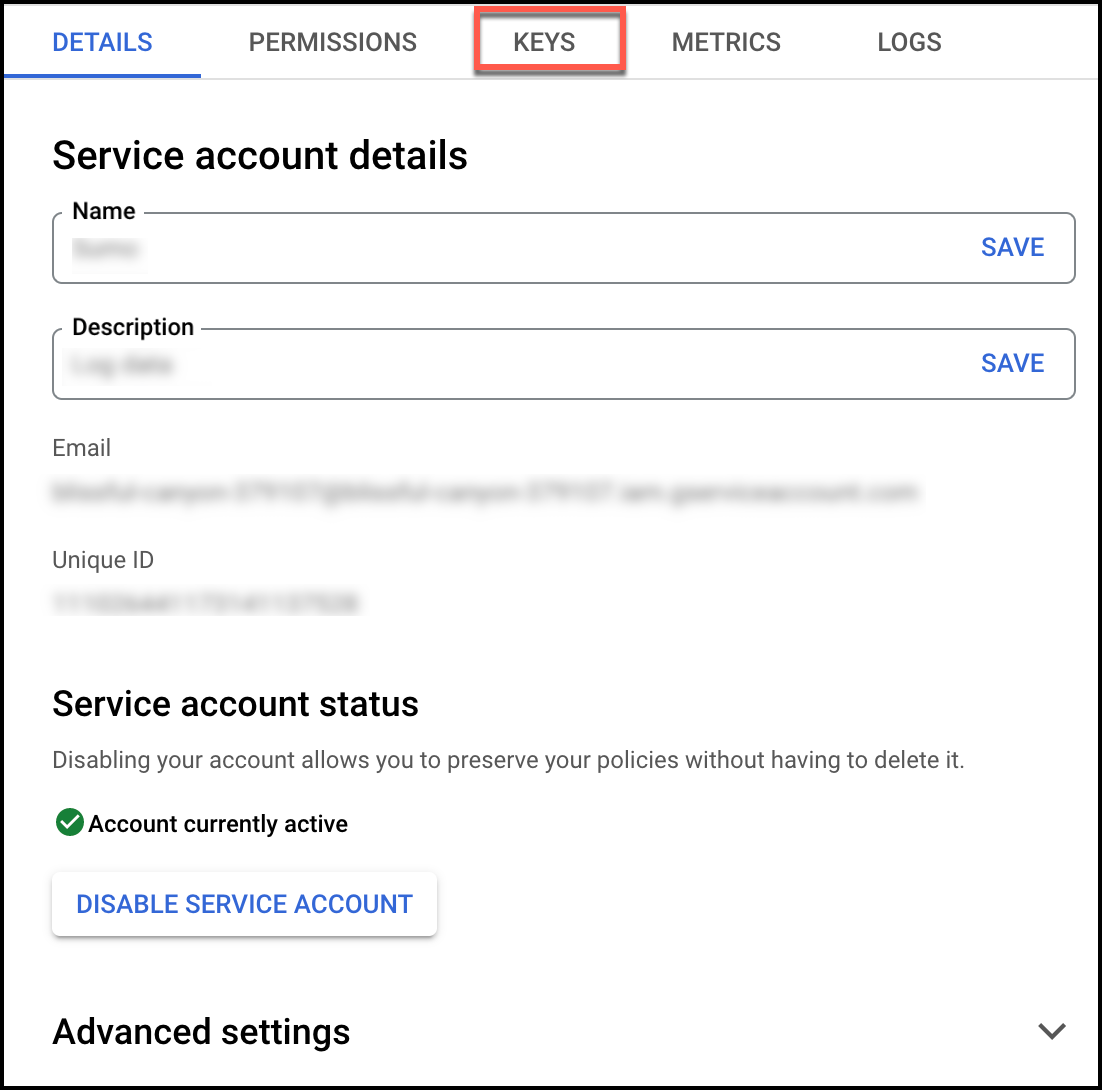
- From Add Key dropdown, select Create new key. At the prompt, select JSON and click Create to create a key
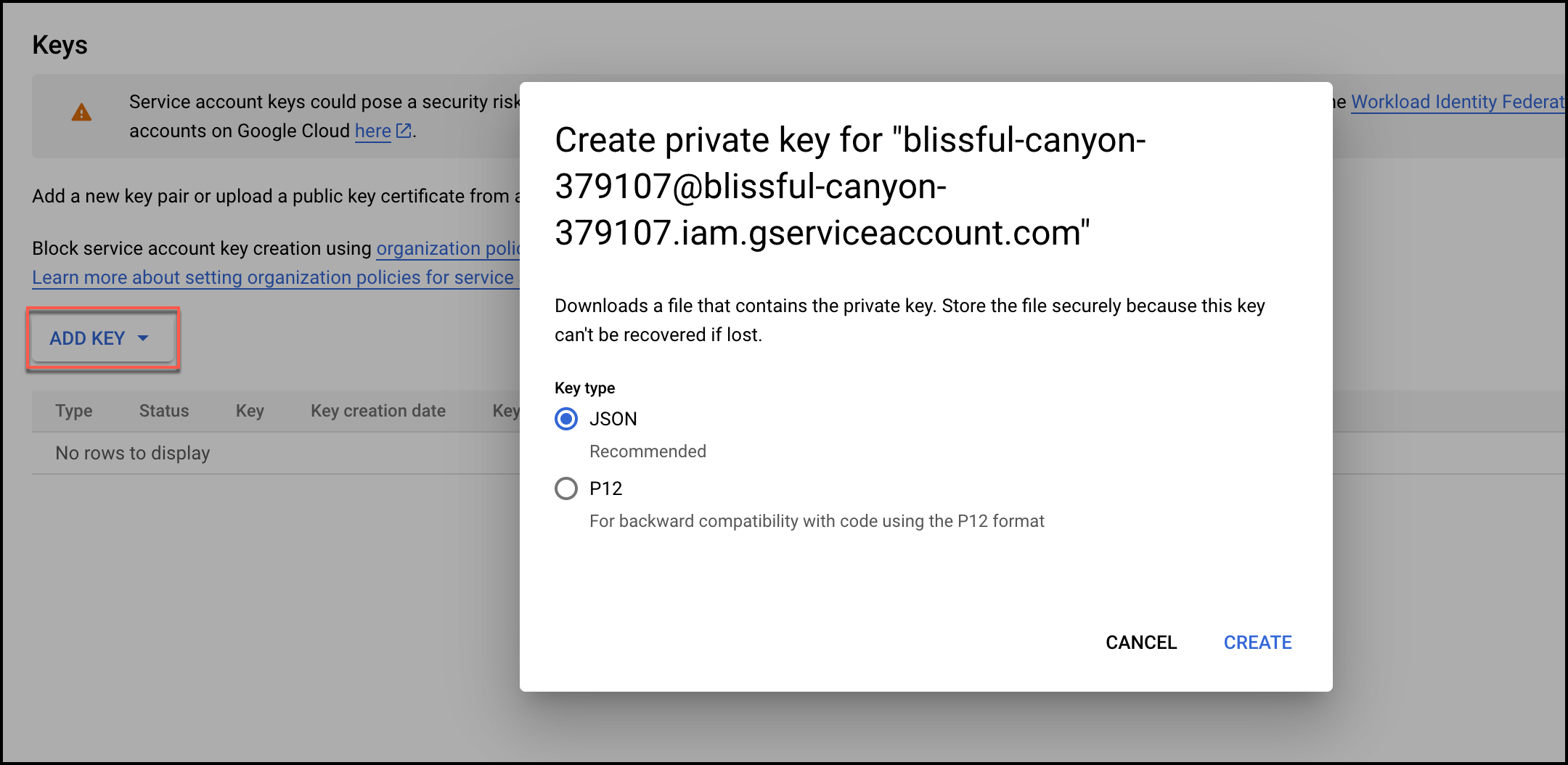
- JSON for the service account is automatically downloaded. Use this JSON file while configuring the Google Workspace User Inventory source.
Domain-wide Delegation
To add domain-wide delegation to your service account using the client ID or Key generated in above section, follow the steps below:
- Navigate to the Google Console service account page.
- Select your service account.
- Go to Advanced settings section.
- Under Domain-wide delegation, find your service account's Client ID. Click
to copy the client ID value to your clipboard.
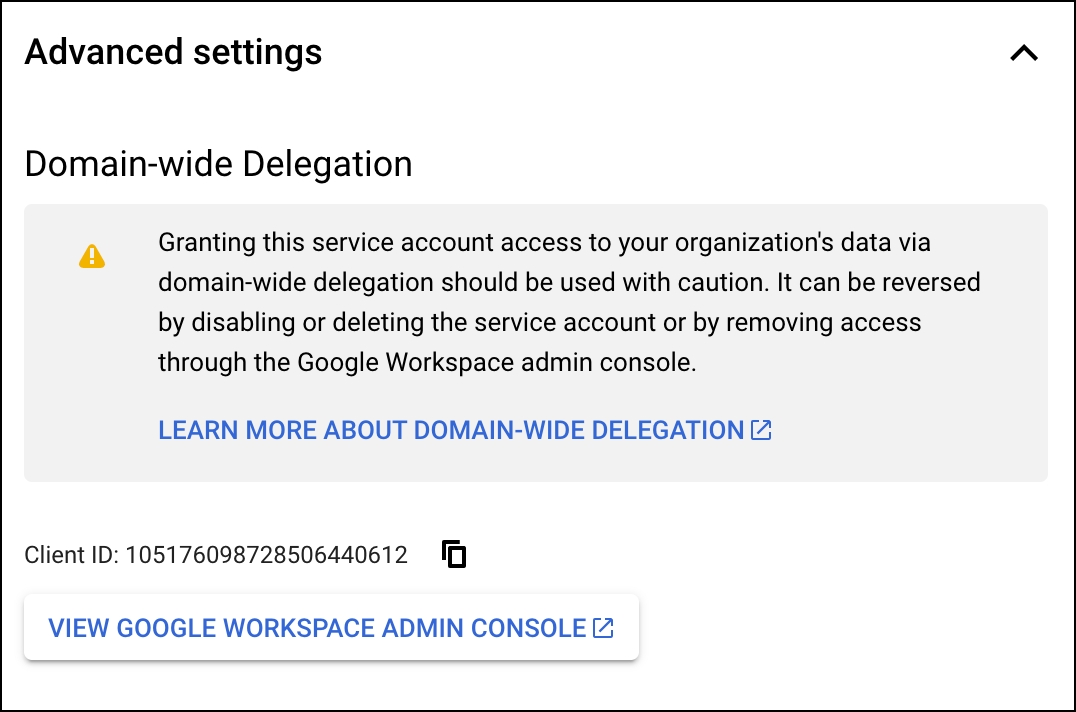
- If you have super administrator access to the relevant Google Workspace account, click View Google Workspace Admin Console, then sign in using a super administrator user account and continue following the steps in the section below.
If you do not have super administrator access to the relevant Google Workspace account, contact a super administrator for that account and send them your service account's Client ID and list of OAuth Scopes so they can complete the following steps in the Admin console.
Adding OAuth Scope
OAuth Scope enables delegated access to a user's resources on a service, such as Google, without exposing the user's credentials to the third-party application. By adding the necessary OAuth scopes, you are specifying the level of access the service account has to your resources, while also ensuring security and privacy.
- From the Google admin console, go to Security section, then click API Controls.
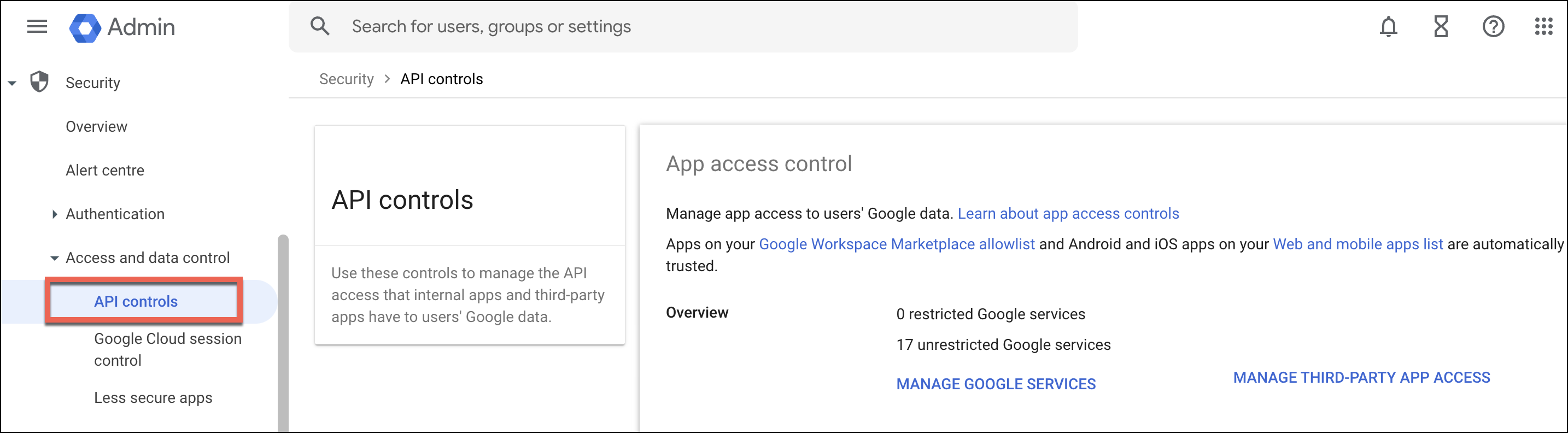
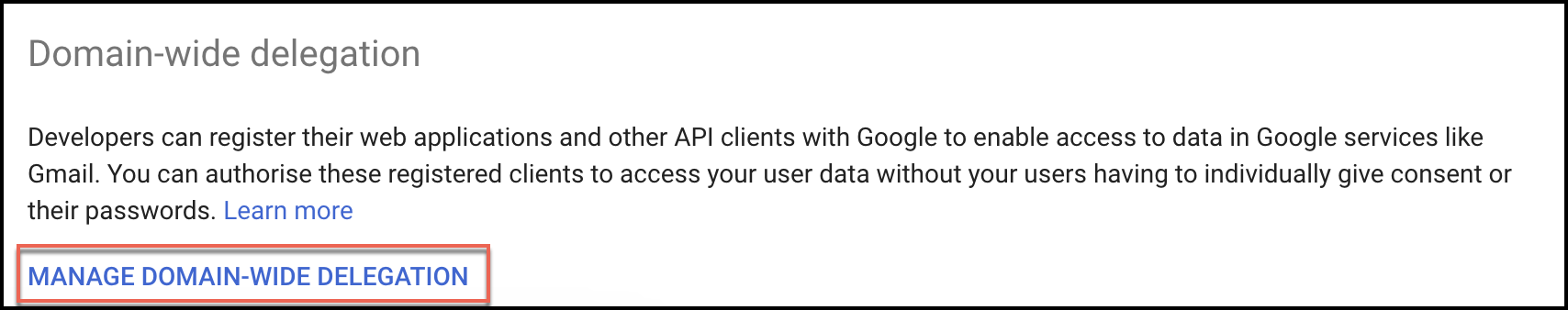
- To add the OAuth scopes, locate the settings under Manage Domain Wide Delegation section.
- Click Add new.
- In the Client ID field, paste the client ID you copied in step 5 of the Creating Service Account section.
- In the OAuth Scopes field, enter a comma-delimited list of the scopes required by your application.
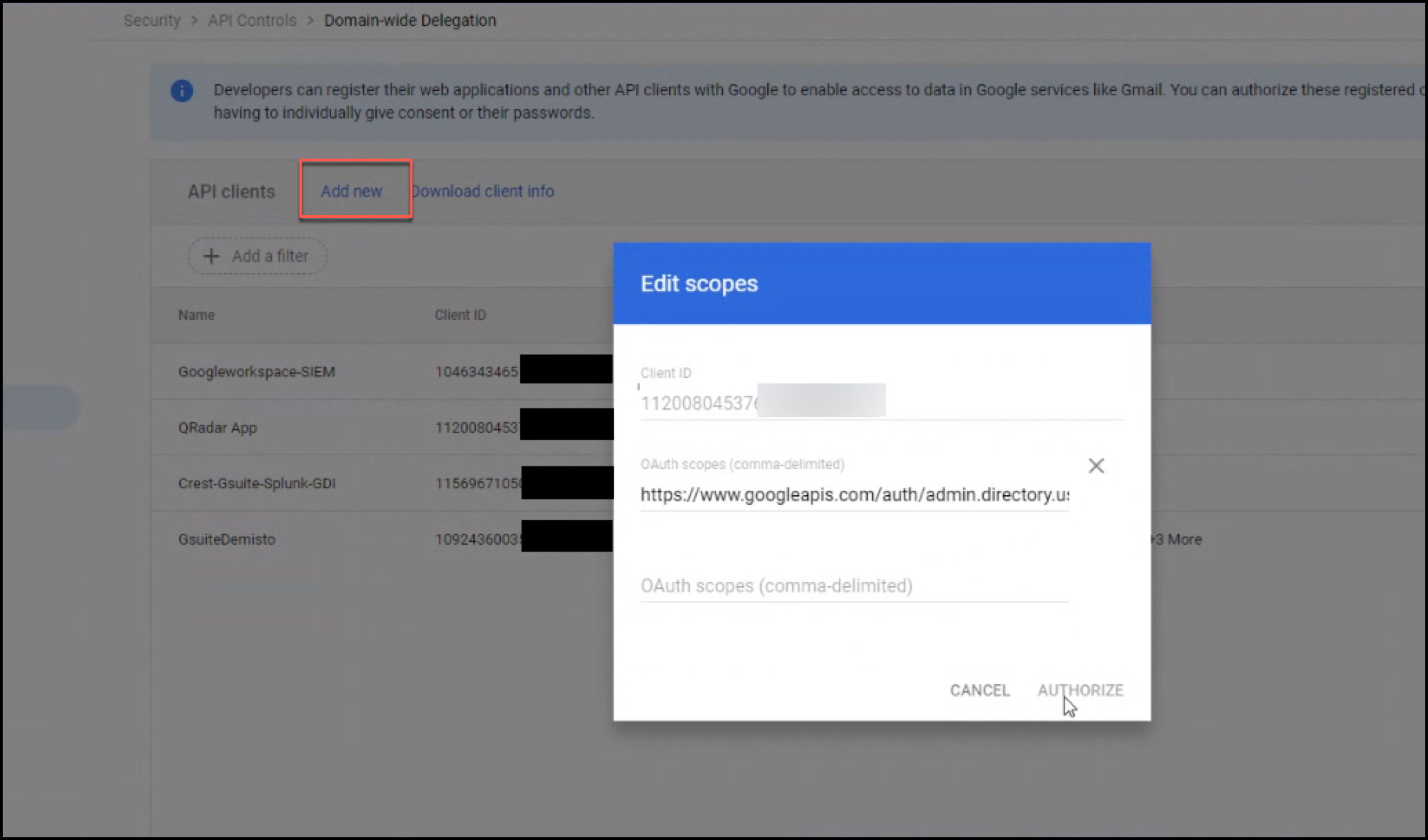 .
.
You can add any of the following OAuth scopes. Note the ones you select, you'll need to provide them when configuring the Sumo Logic Google Workspace Source.
https://www.googleapis.com/auth/admin.directory.user
https://www.googleapis.com/auth/admin.directory.user.readonly
https://www.googleapis.com/auth/cloud-platform
To ensure that you are authorized to fetch the users' details, it is recommended to add an OAuth scope to your Google Workspace service account. Adding the appropriate OAuth scope(s) maintains security and privacy for your users.
Learn more about OAuth scopes:
Source configuration
When you create a Google User Inventory source, you add it to a Hosted Collector. Before creating the Source, identify the Hosted Collector you want to use or create a new Hosted Collector. For instructions, see Configure a Hosted Collector.
To configure a Google Workspace User Inventory source:
- Classic UI. In the main Sumo Logic menu, select Manage Data > Collection > Collection.
New UI. In the Sumo Logic top menu select Configuration, and then under Data Collection select Collection. You can also click the Go To... menu at the top of the screen and select Collection. - On the Collectors page, click Add Source next to a Hosted Collector.
- Select Google Workspace: User Inventory.
- Enter a Name to display for the Source in the Sumo web application. The description is optional.
- (Optional) For Source Category, enter any string to tag the output collected from the Source. Category metadata is stored in a searchable field called
_sourceCategory. - Forward to SIEM. Check the checkbox to forward your data to Cloud SIEM so it becomes part of User Inventory. note
Select Forward to SIEM only if you have Cloud SIEM installed.
- (Optional) Fields. Click the +Add Field link to define the fields you want to associate, each field needs a name (key) and value.
A green circle with a check mark is shown when the field exists in the Fields table schema.
An orange triangle with an exclamation point is shown when the field doesn't exist in the Fields table schema. In this case, an option to automatically add the nonexistent fields to the Fields table schema is provided. If a field is sent to Sumo that does not exist in the Fields schema it is ignored, known as dropped.
- The Delegated User Email is the email address of the user you want to call the API on behalf of. This user should have the necessary permissions to view the details of other users in your Google Workspace domain, such as an Admin role. At a minimum, the user should have the
Users:Read permission. Learn more about Domain-Wide Delegation of Authority: - Google Workspace Credentials. You can authenticate your service account credentials directly by uploading a JSON file credentials instead of breaking down the file into different sections for the UI schema. Click Upload and select the JSON file that you downloaded in the Service Account Credentials section.
- Provide the same Scope you defined for your service account during the Adding OAuth Scope above.
- The Query Parameter for Collecting User Data section provides two options, Customer or Domain Parameter. See the Directory API documentation from Google for details.
- Customer ID. The unique ID for the customer's Google Workspace account. In the case of a multi-domain account, to fetch all groups for a customer, fill this field instead of domain. You can also use the
my_customeralias to represent your account'scustomerId. ThecustomerIdis also returned as part of the Users resource. - Domain. The domain name. Use this field to get fields from only one domain. To return all domains for a customer account, use the
customerquery parameter instead.
- Customer ID. The unique ID for the customer's Google Workspace account. In the case of a multi-domain account, to fetch all groups for a customer, fill this field instead of domain. You can also use the
- Processing Rules for Logs. (Optional) Configure any desired filters, such as allowlist, denylist, hash, or mask, as described in Create a Processing Rule.
- When you are finished configuring the Source, click Save.
Metadata fields
| Field | Value | Description |
|---|---|---|
_siemVendor | Google | Set when Forward To SIEM is checked. |
_siemProduct | Workspace | Set when Forward To SIEM is checked. |
_siemDataType | Inventory | Set when Forward To SIEM is checked and specific to the API collected. |
JSON schema
Sources can be configured using UTF-8 encoded JSON files with the Collector Management API. See how to use JSON to configure Sources for details.
| Parameter | Type | Value | Required | Description |
|---|---|---|---|---|
| schemaRef | JSON Object | {"type":"Google Workspace User Inventory"} | Yes | Define the specific schema type. |
| sourceType | String | "Universal" | Yes | Type of source. |
| config | JSON Object | Configuration object | Yes | Source type specific values. |
Configuration Object
| Parameter | Type | Required | Default | Description | Example |
|---|---|---|---|---|---|
| name | String | Yes | null | Type a desired name of the source. The name must be unique per Collector. This value is assigned to the metadata field _source. | "mySource" |
| description | String | No | null | Type a description of the source. | "Testing source" |
| category | String | No | null | Type a category of the source. This value is assigned to the metadata field _sourceCategory. See best practices for details. | "mySource/test" |
| fields | JSON Object | No | null | JSON map of key-value fields (metadata) to apply to the Collector or Source. Use the boolean field _siemForward to enable forwarding to SIEM. | {"_siemForward": false, "fieldA": "valueA"} |
| clientEmail | String | Yes | null | Provide the Client Email you got in the JSON file after you created service account credentials | |
| delegatedUserEmail | String | Yes | null | Provide the super-administrator email address for the domain that granted access to the service account you created. | |
| credentialsJson | String | Yes | null | Authentication service account's credentials to access Google Workspace Platform. | |
| scope | String | Yes | null | Provide the same Scope you defined for your service account | |
| queryParam | Boolean | No | true | By default, the Customer parameter is selected with a CustomerID value of my_customer. To assign a different CustomerID provide the customerID parameter. Set to false to use the Domain parameter. You need to provide the domain parameter when false. | |
| customerID | String | No | my_customer | The unique ID for the customer's Google Workspace account. | |
| domain | String | No | (except when queryParam is set to false.) | The domain name. Use this field to get fields from only one domain. |
JSON example
loading...
Terraform example
loading...
FAQ
Click here for more information about Cloud-to-Cloud sources.