2023 Archive
This is an archive of 2023 Cloud SIEM release notes. To view the full archive, click here.
December 14, 2023 - Application Update
Minor changes and enhancements
-
[New] A new attribute section has been added to Signal and Insight details returned by the API endpoints
GET /signals/{id}andGET /insights/{id}. The section will include the log search string (along with start and end times) that you can use to retrieve the queried records for a given Signal. The stanza looks like this:"recordSearchDetails": {
"query": "{string}",
"queryStartTime": "{timestamp}",
"queryEndTime": "{timestamp}"
},
Bug fixes
- Some users were seeing duplicate schema tags (with an extra "s" at the end) in the UI.
- In some scenarios, the UI would react slowly when users attempted to enter comments for Insights.
- The UI was not properly enforcing the 100 character limit for rule names (and instead displaying an unknown error if the user attempted to set a rule name that was too long).
December 6, 2023 - Application Update
Automation Service Enhancements
The Automation Service has been updated to include several new enhancements:
- Containment action types are now supported. Typically, these actions will perform some sort of response or remediation action, such as resetting a user's password or blocking a domain on your firewall. Many integrations in App Central now include containment actions.
- User Choice nodes (and manual steps) are now supported. When executing a playbook if a user choice node is encountered, the execution will pause until a user selects an option. For example, after enrichment, a user could be asked whether to proceed with a containment action or to perform additional enrichment first. When a playbook is paused at a user choice node, the status of that playbook will say
Waiting user interaction. - In the initial release of the Automation Service, playbooks would not appear in the Create New Automation Cloud SIEM dialog unless they defined as type
CSE. This restriction has been lifted; all playbooks will now appear in the dropdown.
For full details, see the Automation Service documentation.
Minor Changes and Enhancements
- [New] Entity Groups now support second-level unnormalized attributes (
fields.<attribute>.<attribute>). - [New] Log Mappings can now be enabled or disabled via API using the
PUT /log-mappings/{*id*}/enabledendpoint. - [New] The
Record Countfield on Sumo Logic-provided Chain Rules can now be overridden (like other Rule fields).
Bug Fixes
- Users were unable to manually change the Criticality assigned to an Entity.
- Users were getting a 500 error when attempting to duplicate a rule.
Rule Expression Validation
When writing Rules and Rule Tuning Expressions, it's possible to write an expression that is syntactically correct (and passes validation) but that will still fail when executed. There are two specific cases we have identified:
- Using a non-normalized field that does not exist in the log records (schema fields will always exist)
- Introducing a type mismatch (that is, matching a string to an integer value)
If you test a Rule (from the Rules Details page), an error will be displayed in these cases, but the error is not obvious and not clear, and the normal editor validation does not catch these kinds of errors.
In addition, while the Cloud SIEM Rules engine does not generate runtime errors in these cases (there just isn't a match), the Log Search engine does generate errors and refuses to return any results in these cases.
A few weeks ago, we made a change to Signal and Insight detail pages, where for multi-signal Rules (such as Chain Rules), where we would attach a subset of rules on the details page and the user would have to go to the Queried Records tab to view any other potentially related records, we combined those views and began showing both the attached and queried records on the main page. Unfortunately, the way the new design worked, no records were displayed if the queried record log search failed.
As a result of these issues, we have made two changes:
- On the Rules Details page, if the test (a log search) returns an error, instead of saying "No Records Found," the screen will say, "Check the Rule/Tuning Expressions."
- On the Signal and Insight Details pages, all attached record(s) will be displayed even if the log search query cannot be completed.
Note that fixing the rule expression(s) will not fix any Signals or Insights that have already been generated; you will have to use the View in Log Search feature and manually fix the log search string to see the log records.
Other tips:
- A malformed tuning expression will affect any rule that it is associated with, whether provided by Sumo Logic or custom-written.
- We highly recommend using only schema fields in your rule and tuning expressions.
- Sumo Logic's parsers and mappers are updated weekly, so please contact Support if you need to add a mapping from the raw log format to the normalized schema.
- Sumo Logic's schema is extensible, so please contact Support if there's a field you'd like to add.
- Links from the legend for the new Insights by Status panel on the HUD were not enabled properly.
November 13, 2023 - Content Release
This release includes the changes and enhancement enumerated below:
Rules
- [New] MATCH-S00894 HAR file creation observed on host
- HAR files contain session telemetry and network traffic. These file types are typically generated using the "developer tools" options on modern browsers like Chrome, Edge, or Firefox. These files may contain various sensitive data such as session keys, tokens, or cookies which may be extracted by a threat actor in order to access systems which the keys, tokens, or cookies in the HAR files have access to. Ensure that this operation is expected and ensure to sanitize the HAR file of any sensitive credential material.
Log Mappers
- [Updated] Microsoft Office 365 Exchange Mailbox Audit Events
- Maps client field to resource.
Parsers
- [Updated] /Parsers/System/Microsoft/Office 365
- Enhanced user agent parsing.
- [Updated] /Parsers/System/Microsoft/Windows-JSON-Open Telemetry
- Adds support for forthcoming format change and fixes event ID formulation breaking mapping.
November 2, 2023 - Content Release
This content release includes new out-of-the-box parsing and mapping support for Claroty xDome in CEF. Additionally, parser templates were updated to remove extraneous commenting in uncommented parser templates.
Log Mappers
- [New] (Claroty xDome) Alert
- [New] (Claroty xDome) Communications Events
- [New] (Claroty xDome) Vulnerability
Parsers
- [New] /Parsers/System/Claroty/Claroty xDome CEF
- [Updated] /Parsers/System/Parser Templates/CEF Template Commented
- [Updated] /Parsers/System/Parser Templates/JSON Template
- [Updated] /Parsers/System/Parser Templates/Key Value Pair Template
- [Updated] /Parsers/System/Parser Templates/Unstructured Template Commented
- [Updated] /Parsers/System/Parser Templates/Windows XML Template
- [Updated] /Parsers/System/Parser Templates/XML Template
November 1, 2023 - Application Update
Multi-Record Signal Changes
To improve the usability of the Signals user interface, we've changed the way that records are displayed on Signals generated by multi-record (Threshold, Chain, and Aggregation) Rules. Instead of attaching a sample set of records to the Signal and then providing a Queried Record tab to manually search for additional records, all records that were part of the Signal will be displayed in the UI. (As a result, the Queried Records tab has been removed from the UI.)
Behind the scenes, we will attach the first record directly to the Signal (in the API and sec_signal index, this is listed in the allRecords section). In the UI, the other records will be gathered via an automatic background log search. (In the API and shortly in the sec_signal index, any involved Entities - up to a maximum of 100 - will be included in a new involvedEntities section.)
In addition, the number of attached records has been removed from the Signals list view, since it will now always be 1.
This change will also bring an enhancement for Outlier Rule Signals. Previously those Signals would only show a single record, but with this change they will also show all related records as well.
This change has no effect on the Rules themselves; they will continue to operate as before.
Automation Service Audit Logging
The Automation Service has been updated to include support for Audit Logging. Events like updates to integrations and playbook execution will now be automatically logged to the standard Sumo Logic Audit Logging indices.
For full details, see the Cloud SOAR documentation (the Automation Service will log a subset of those events).
Bug Fixes
- In some cases, Insights would appear to be open after they had been closed/resolved.
October 26, 2023 - Content Release
This content release includes templates for creating Cloud SIEM parsers. There are two versions of each, one with comments that explain the purpose of each parser component, and “clean” versions that you can use to start quickly creating custom parsers. Further documentation on using these parsers will be available on Sumo Logic Docs in the coming weeks. Other changes in this release are enumerated below.
Rules
- [New] FIRST-S00047 First Seen ASN Associated with User for a Successful Azure AD Sign In Event
- This rule will trigger when a new ASN value is associated with a successful Entra ID sign-in event for a particular username since the baseline period. This may be suspicious activity as a user's IP address may change periodically, but typically users authenticate from a set of ASNs (one ASN value for their home network, another ASN value for their mobile device). A sign in with a new ASN not seen since the baseline period could be indicative of credential theft. Look at other events occurring for the user in question for the same time period to ascertain whether access was malicious or benign.
- [New] FIRST-S00048 First Seen Azure Device Code Authentication from User
- Azure Device Code authentication can be utilized in phishing attacks. This specific rule looks for a user performing device code authentication to an Azure resource for the first time since the baseline period. If this action is not expected, it could be a sign of malicious activity. Examine the event for odd user agent values and look at what other actions the affected account is performing within the Azure estate.
- [Updated] MATCH-S00891 Azure OAUTH Application Consent from User
- Fixed mismatched description and summary fields
- [Updated] MATCH-S00832 Office 365 Inbox Rule Updated
- Added fix to exclude blank or null rules
Parsers
- [New] /Parsers/System/Parser Templates/CEF Template
- [New] /Parsers/System/Parser Templates/CEF Template Commented
- [New] /Parsers/System/Parser Templates/CSV Template
- [New] /Parsers/System/Parser Templates/CSV Template Commented
- [New] /Parsers/System/Parser Templates/JSON Template
- [New] /Parsers/System/Parser Templates/JSON Template Commented
- [New] /Parsers/System/Parser Templates/Key Value Pair Template
- [New] /Parsers/System/Parser Templates/Key Value Pair Template Commented
- [New] /Parsers/System/Parser Templates/LEEF Template
- [New] /Parsers/System/Parser Templates/LEEF Template Commented
- [New] /Parsers/System/Parser Templates/Unstructured Template
- [New] /Parsers/System/Parser Templates/Unstructured Template Commented
- [New] /Parsers/System/Parser Templates/Windows XML Template
- [New] /Parsers/System/Parser Templates/Windows XML Template Commented
- [New] /Parsers/System/Parser Templates/XML Template
- [New] /Parsers/System/Parser Templates/XML Template Commented
October 26, 2023 - Application Update
Enhanced Support for Custom Insight Statuses
Sumo Logic is pleased to announce two enhancements to Cloud SIEM related to custom Insight statuses.
First, the In Progress status can now be disabled (not deleted). Many customers create multiple statuses that all represent an "In Progress" state, so this option can help reduce confusion in those cases.
Second, while Cloud SIEM has long supported custom Insight statuses, Insights in any custom status have been reported together (as one group on the HUD or using the same color in other instances). To improve this experience, custom statuses can now be assigned a unique color:
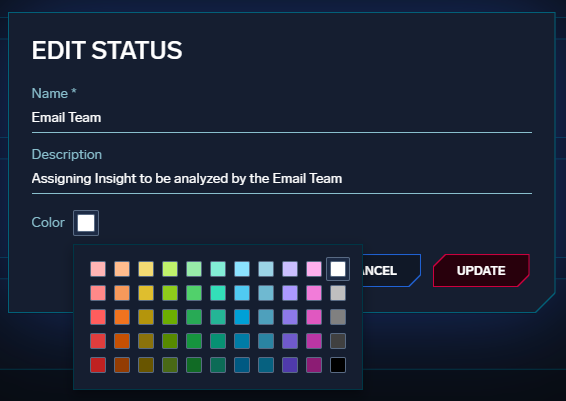
This color will be used wherever an Insight is displayed with that status (such as in the Insight list and board views). For existing custom statuses, the color will remain white (as it has been) until the configuration is changed.
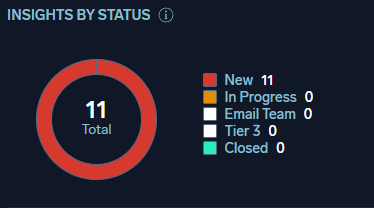
The HUD has been updated as well; for example, the Insights by Status widget has been updated to properly display each status instead of grouping custom statuses together:
A corresponding attribute (color) has also been added to the custom status API.
Minor Changes and Enhancements
- [New] Searches in Cloud SIEM (from the top menu bar) are now case-insensitive.
- [New] Custom match list columns now support unnormalized attributes (like
fields.foo) - [New] The records search page in Cloud SIEM now includes a link to view the equivalent search in the Log Analytics Platform log search page.
- [Updated] When a comment is added to an Insight by an Action from the Automation Service, it will be attributed to a system user called "Automation Service".
Bug Fixes
- The Insight data forwarded to the Automation Service did not include the full set of attributes for attached Signals.
- Some hostnames in CrowdStrike FDR inventory sources were not getting normalized properly.
- Entity Groups were being applied to the wrong Entity types.
- Duplicate audit log entries for Insights were being created. (Note that while this has been resolved, the duplicate entries have not been removed from customer audit logs.)
- When entering closing an Insight, users can enter comments and the UI will suggest content based on comment history. These suggestions were broken and have been reset.
- When configuring Entity Groups, the UI was not allowing users to specify unnormalized inventory attributes (like
fields.foo).
October 18, 2023 - Application Update
Legacy Signal Forwarding Deprecation
Since July 2022, Signals generated by Cloud SIEM are automatically saved in a standardized sec_signal index. This special partition is similar to the existing sec_record indices in that, unlike data retained using the legacy Signal Forwarding feature, it is stored in a format that supports keyword search, nested attributes, and other standard log search features.
The new index is automatically generated and retained for a period of 2 years at no additional cost for all Cloud SIEM customers.
As a result, the optional legacy Signal Forwarding feature in Cloud SIEM will be deprecated on November 15, 2023. Existing data will not be deleted, but new Signals generated after that date will no longer be forwarded using that feature and the option will no longer be available. (Signals will continue to be forwarded automatically to sec_signal.) Customers leveraging data forwarded using the legacy feature to generate dashboards (or for other use cases) will need to modify those applications to use the new sec_signal index before then. Note that the content of the sec_signal index is not identical to the content in data forwarded using the legacy option.
October 11, 2023 - Content Release
This content release contains rules mostly pertaining to Microsoft Azure OAUTH Application Registration, NSG, and Key Vault services. Pertinent to CVE-2023-38545 and CVE-2023-38546, this release also includes a new rule (FIRST-S00040 described below) to aid in detecting unusual cURL tool usage by a user as it may pertain to exploitation of these vulnerabilities.
Rules
- [New] MATCH-S00891 Azure OAUTH Application Consent from User
- A user has consented to application permissions.
- [New] CHAIN-S00017 Change of Azure MFA Method followed by Risky SignIn
- This alert looks for an Azure MFA authentication method change, followed by a risky sign in detected by Azure within a six hour time period for the same user account.
- [New] FIRST-S00044 First Seen AppID Generating
MailIItemsAccessed Eventfrom User- This alert looks at a first seen application ID accessing an Office 365/Exchange mail box item. The
MailItemsAccessedmay not always be enabled within an Entra/Azure/Office 365 tenant and is dependent on Microsoft licensing requirements. See the following guide from CISA for additional information on this event type and investigation steps: https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-193a.
- This alert looks at a first seen application ID accessing an Office 365/Exchange mail box item. The
- [New] FIRST-S00046 First Seen Client Generating
MailIItemsAccessedEvent from User- This alert looks at a First Seen client accessing an Office 365/Exchange mail box item. The
MailItemsAccessedmay not always be enabled within an Entra/Azure/Office 365 tenant and is dependent on Microsoft licensing requirements. See the following guide from CISA for additional information on this event type and investigation steps: https://www.cisa.gov/news-events/cybersecurity-advisories/aa23-193a.
- This alert looks at a First Seen client accessing an Office 365/Exchange mail box item. The
- [New] FIRST-S00040 First Seen cURL execution from User
- First Seen execution of cURL by a user from a device. The cURL tool is designed to retrieve files using various internet protocols in a programmatic manner; it is often abused by threat actors to download various files as part of broader executions. If this usage of cURL comes from an unexpected user, it is recommended that the command line value be reviewed and the URL which was used as part of cURL command be investigated.
- [New] MATCH-S00888 Microsoft Teams External Access Enabled
- Microsoft Teams External Access has been enabled; this setting allows any users that are external to your Teams/Office organization to message users that are within your Teams/Office organization. If this setting change is unplanned or unexpected it is recommended that this activity be reviewed. Microsoft Teams provides administrators the ability to allow only specific external domains to message users within the organization. Look for Office 365 events with the
MessageSentorMemberAddedevent names in order to gain more detail as to what users were invited to which Teams channels, if any.
- Microsoft Teams External Access has been enabled; this setting allows any users that are external to your Teams/Office organization to message users that are within your Teams/Office organization. If this setting change is unplanned or unexpected it is recommended that this activity be reviewed. Microsoft Teams provides administrators the ability to allow only specific external domains to message users within the organization. Look for Office 365 events with the
- [New] MATCH-S00889 Microsoft Teams Guest Access Enabled
- Microsoft Teams Guest Access has been enabled globally; this setting allows any users that are external to your Teams/Office organization to be invited into your Teams/Office organization. If this setting change is unplanned or unexpected it is recommended that this activity be reviewed. MIcrosoft Teams provides administrators the ability to allow only specific guest actions to take place within the Teams/Office organization.
- [New] MATCH-S00890 Owner Added to Azure Service Principal
- An owner was added to an Azure service principal. Threat actors may add owners to Azure service principals for privilege escalation or persistence avenues. Ensure this action is expected and approved.
- [New] MATCH-S00893 Secret Added to Azure Service Principal
- Secrets can be added to Azure Service Principals as a persistence mechanism. The
properties.targetResources.1.modifiedProperties.1.newValuefield will have details regarding the secret or certificate added.
- Secrets can be added to Azure Service Principals as a persistence mechanism. The
- [New] MATCH-S00892 Value Added to Azure NSG Group
- This alert looks for a value being added to an Azure Network Security Group (NSG) successfully. Depending on the environment, other Azure services such as Azure Firewall may provide egress and ingress controls. Ensure this activity is authorized and expected. The raw data for the event contains the exact values being modified.
October 2, 2023 - Application Update
MITRE ATT&CK® Threat Coverage Explorer
We are excited to announce a new feature in Cloud SIEM, the MITRE ATT&CK® Threat Coverage Explorer. This interactive tool gives you the ability to see how Rules, Signals, and log sources map to adversary actions using the MITRE ATT&CK® Matrix for Enterprise.
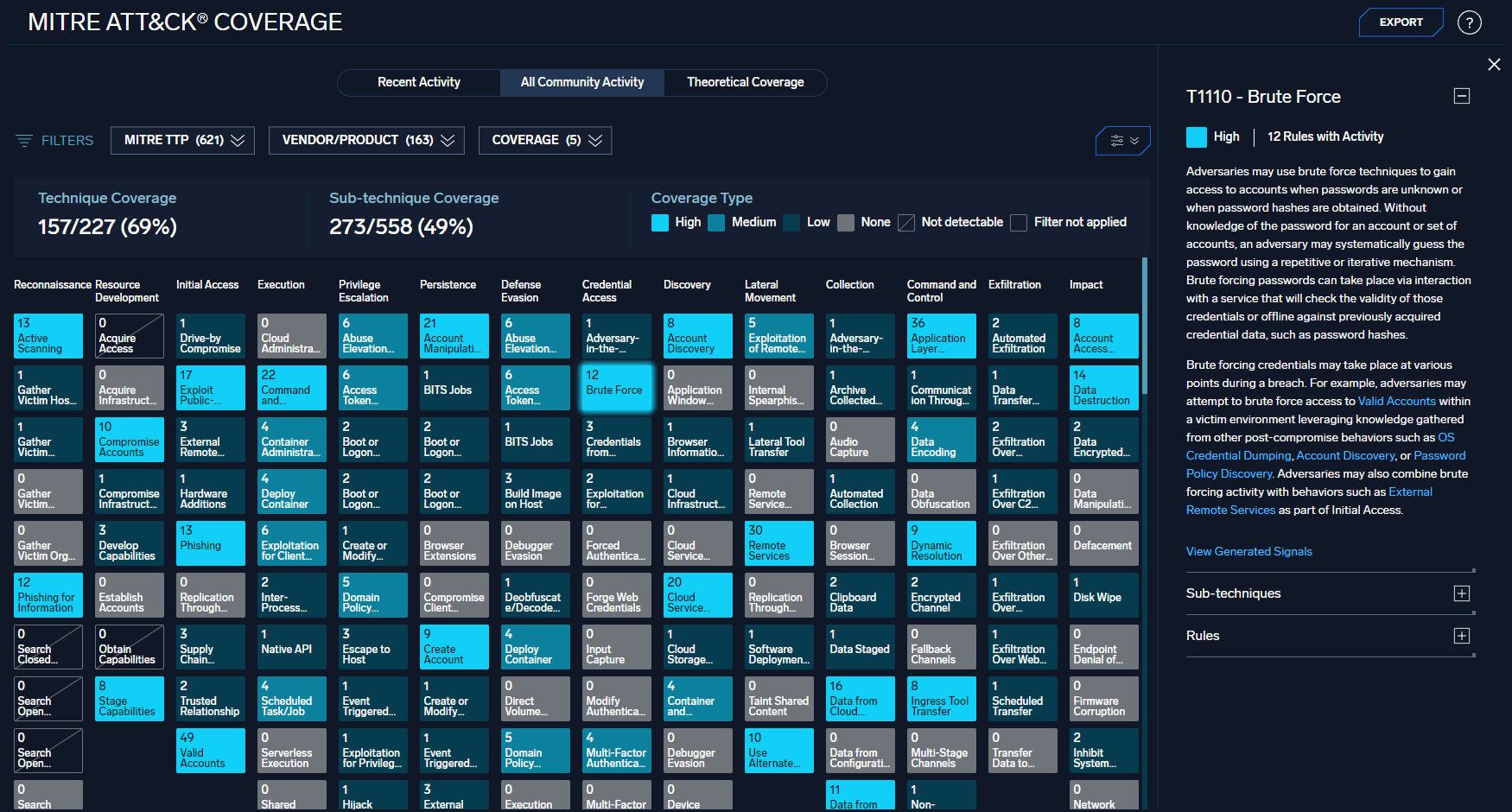
The MITRE Explorer can be used to identify gaps in coverage and understand the impact of specific log sources and Rules to the overall threat coverage and value of Cloud SIEM.
The tool can be accessed in the Content Menu. It supports three different views:
- Recent Activity - Your environment's actual coverage (Rules that generated Signals) over the past six months
- All Community Activity - All Cloud SIEM customers' anonymized and aggregated coverage over the past six months.
- Theoretical Coverage - Potential coverage if all rules are enabled and all log sources are connected.
The MITRE Explorer uses the built-in MITRE tactic, technique, and sub-technique tags to track coverage, so if custom Rules are tagged appropriately, they will also be included.
Clicking on a technique will open a detailed view which describes the technique (and any included sub-techniques) and lists the Rules and Signals that match.
The view is filterable by tactic, technique, and sub-technique, as well as log source and coverage level. There are multiple view options so the display can be customized, and the data can be exported in MITRE's JSON format so it can be combined with data from other tools to view your total coverage. There is also an API to retrieve coverage data and the JSON content.
For more details on how to use the MITRE Explorer, check out the online documentation.
Minor Changes and Enhancements
- [New] When viewing Insight details, users can now select multiple Signals and remove them from the Insight with a single click.
- [New] When viewing Entity inventory data, unnormalized fields with millisecond-based timestamps are now automatically converted to human-readable format when possible.
- [New] Tag schemas and context actions can now be managed via Terraform. See the API documentation for details.
Bug Fixes
- The ability to add items to a Match List via Terraform was not working properly.
- Timestamps on the Entity Timeline were using different time zones.
- A UI error was preventing users from overriding some fields on First Seen and Outlier Rules.
September 22, 2023 - Content Release
This content release includes new parsing, mapping, and passthrough rule support for Qualys Vulnerability Data as well as changes enumerated below.
Rules
- [New] MATCH-S00887 Port Forwarding Enabled via Visual Studio Code
- A local port has been forwarded and made available for external connectivity utilizing the Visual Studio Code port forwarding feature
Log Mappers
- [New] Qualys Vulnerability Data
- [Updated] Windows - Security - 4886
- Adds alternate fields for user_username and device_hostname
- [Updated] Windows - Security - 4887
- Adds alternate fields for user_username and device_hostname
Parsers
- [New] /Parsers/System/Qualys/Qualys Vulnerability Data
September 21, 2023 - Application Update
Entity Groups Inventory Enhancements
We are happy to announce some important enhancements to the Entity Group feature in Cloud SIEM.
With this release, Entity Groups can now use any attribute available in your inventory data - including non-normalized attributes. (Previously, only the group attribute was available.) Non-normalized attributes can be used by adding the fields. prefix.
In addition, the release introduces the ability to auto-set schema tag values on matching Entities based on the value of a given inventory attribute. In this example, any user Entity that has a value for location in inventory data will have that value set in a tag (such as Location:Austin).
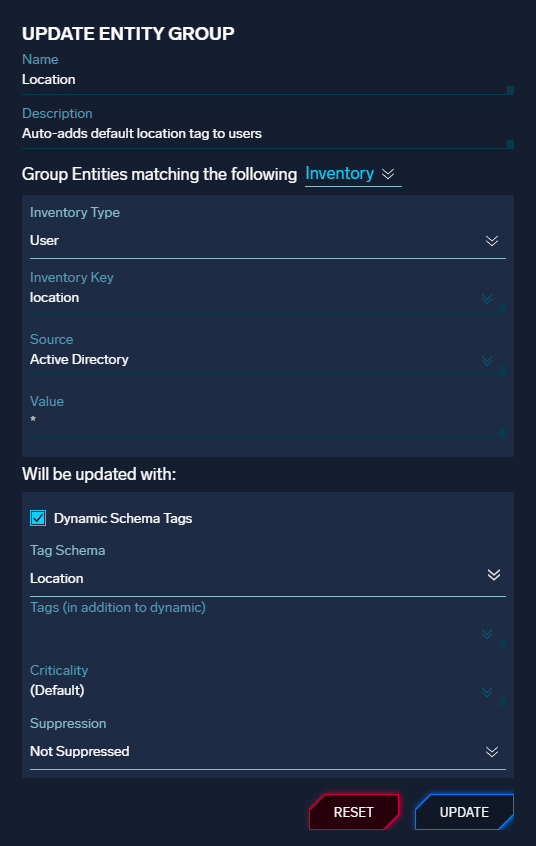
When using dynamic schema tags, you can still set static tags, criticality, and suppression state.
These two enhancements will reduce the number of Entity Groups needed to properly configure your Entities automatically and will automate a more complete and accurate set of Entity attributes, improving Rule and Analyst efficiency.
There much more information about Entity Groups and these enhancements in the online documentation.
Bug Fixes
- Multiple entries were being added to the audit log when some Insights were created.
- Some Insights were not getting enriched with VirusTotal using the direct integration.
- Time-to-live was temporarily considered a mandatory attribute for match lists.
September 11, 2023 - Application Update
Automation Service
Sumo Logic is excited to announce that the Automation Service for Cloud SIEM is now generally available for all Cloud SIEM customers. The Automation Service uses Cloud SOAR capabilities -- without needing Cloud SOAR itself -- to allow you to define and automate smart actions, including enrichments and notifications. These actions can be automatically triggered when certain events occur in Cloud SIEM, helping you to quickly investigate, understand, and react to potential security threats.
You can interact with the service through automations, which execute playbooks. Playbooks are composed of one or more actions with a workflow that could include parallel actions and logic steps. Actions are defined as part of integrations with specific internal and external applications. Sumo Logic provides hundreds of integrations, actions, and playbooks out of the box that you can use and customize. You can also create your own.
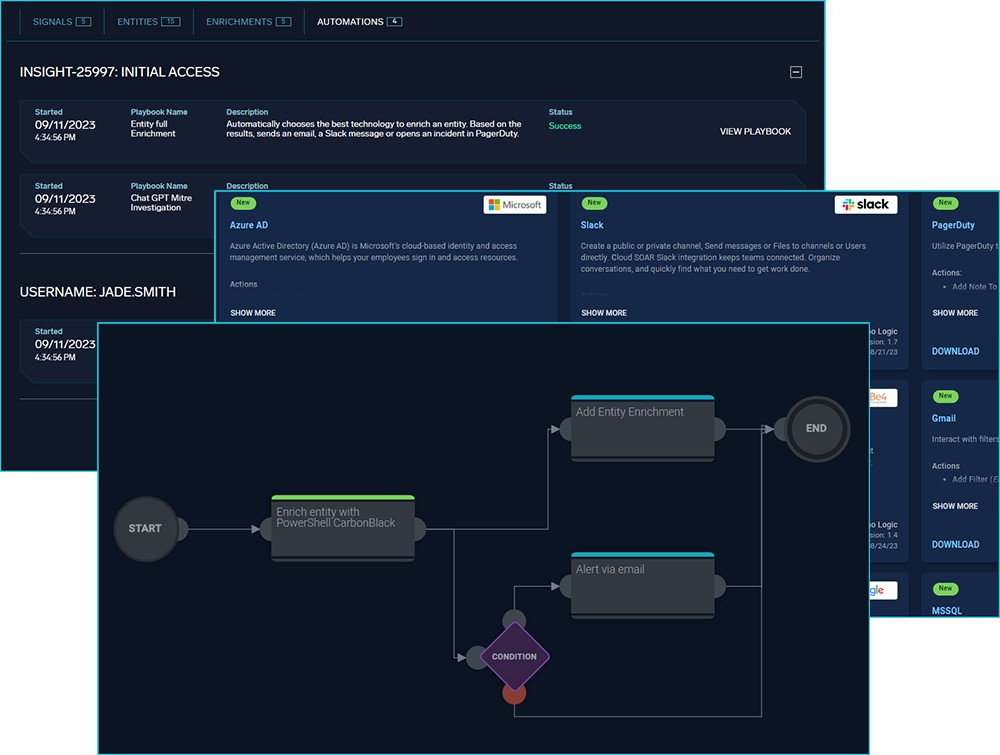
Automations are accessible through the Configuration menu, under Integrations. Automation results are accessible from Insight and Entity detail pages.
The Automation Service does not include the full capabilities of Cloud SOAR. For example, the Automation Service only supports enrichment, nofification, and custom action types, and Automation Service playbooks can only be triggered from Cloud SIEM. There is also a limit to the number of actions you can run per hour. However, if you do have Cloud SOAR, then once you have upgraded to the Fall 2023 release of Cloud SOAR (currently in Beta), Cloud SIEM will use it to run automations instead of the Automation Service, giving Cloud SIEM access to the full capabilities of Cloud SOAR.
Over time, the legacy Insight Actions and Cloud SIEM Enrichment Service features will be deprecated in favor of this new service. (The new service includes integrations and actions corresponding to the legacy Insight Actions and can run existing Enrichment Service PowerShell scripts. The online documentation has more information about migrating.) Note that the Automation Service is not yet available in the FedRAMP environment.
There is much more information about the Automation Service and how to use it in the online documentation.
Minor Changes and Enhancements
- [New] Tag schemas and context actions can now be managed via API (
/tag-schemasand/context-actions). See the API documentation for details. - [Updated] Threat indicator icons will now appear where appropriate in the Active Entities panel on the HUD.
Bug Fixes
- Some records were not being auto-enriched with Network Block data.
- Some internal IP addresses were being marked as external.
- The HUD was not updating Insight status counts in a timely fashion.
- Window size was not saving correctly when defining a new Outlier rule.
September 7, 2023 - Content Release
This release includes new detections for macOS systems and mapping support for Dataminr Alerts. It also includes fixes aimed to reduce false positivity and correct the transposition of description and summary on several rules. Other changes are enumerated below.
Rules
- [New] CHAIN-S00016 macOS - Suspicious Osascript Execution and Network Activity
- [New]* FIRST-S00039 First Seen mdfind Usage from User
- [New]* FIRST-S00041 First Seen networksetup Usage from User
- [New]* FIRST-S00042 First Seen Ioreg Usage from User
- [New]* FIRST-S00043 First Seen pbpaste Usage from User
- [New] MATCH-S00878 macOS - Suspicious Osascript Parent Execution
- [New] MATCH-S00879 macOS - Suspicious Osascript Execution
- [New] MATCH-S00880 macOS - Entitlement Enumeration via Xattr
- [New]* MATCH-S00881 macOS - csrutil status Usage Detected
- [New] MATCH-S00882 macOS - System Preference Enumeration via Security Binary
- [New] MATCH-S00883 macOS - Keychain Enumeration
- [New] MATCH-S00884 macOS - Suspicious Python PIP Execution
- [New] MATCH-S00885 macOS - Screen Sharing Session Established
- [New]* MATCH-S00886 Suspicious chmod Execution
* These rules were originally released September 1, but have been updated in this release.
Log Mappers
- [New] Dataminr Alerts
- [Updated] Squid Proxy - Parser
- Updated mapper to take advantage of additional parsed data (see parser updates)
Parsers
- [Updated] /Parsers/System/Squid/Squid Proxy Syslog
- Updated parser to extract port and protocol information from URL when present
August 22, 2023 - Content Release
This release contains updates to MITRE tags used in several rules that have been deprecated, removed, or were otherwise invalid. Other changes are enumerated below.
Rules
- [New] MATCH-S00886 Suspicious chmod Execution
- This alert looks for a "chmod" execution on a file that is found on the
/tmpdirectory of a Linux or macOS host. Threat actors may download and copy files to this directory and add execution bits or change permissions on these files.
- This alert looks for a "chmod" execution on a file that is found on the
- [Updated] MATCH-S00516 Antivirus Ransomware Detection
- [Updated] MATCH-S00534 MacOS - Re-Opened Applications
- [Updated] MATCH-S00149 PowerShell File Download
- [Updated] MATCH-S00342 Suspicious use of Dev-Tools-Launcher
Log Mappers
- [Updated] Microsoft Defender for Cloud - Security Alerts
- Adds support for Security Alerts via Azure Activity Log
- [Updated] Zscaler - Nanolog Streaming Service - JSON
- Adds alternate values for NSS mappers to ensure proper normalization
- [Updated] Zscaler Firewall
- Adds alternate values for ZScaler Firewall mappers to ensure proper normalization
August 22, 2023 - Application Update
Deprecation Notice
After careful evaluation, we have deprecated Grok patterns immediately for customers who've not used the feature in the last 30 days. Our more robust and configurable solution is already available for customers in the Sumo Logic parsers. More details on how parsing works in Sumo Logic can be found in the Parsing Language Reference Guide.
For customers who are still using Grok, further communication along with a path to migrate to the Sumo Logic parsers will be provided in the coming weeks.
August 4, 2023 - Content Release
This release includes minor updates and a new log mapper for Microsoft Defender.
Rules
- [Updated] MATCH-S00231 Azure - Member Added to Company Administrator Role
- Updated expression to account for parser and vendor schema changes
- [Updated] THRESHOLD-S00097 Impossible Travel - Successful
- Removed vendor/product grouping
- [Updated] THRESHOLD-S00098 Impossible Travel - Unsuccessful
- Removed vendor/product grouping
- [Updated] MATCH-S00167 Recon Using Common Windows Commands
- Bug fix for Qualys path exclusion not working
Log Mappers
- [New] Microsoft Defender for Cloud - Security Alerts
- Support for new log schema
Parsers
- [Updated] /Parsers/System/Microsoft/Microsoft Azure JSON
- Added additional time format
August 3, 2023 - Content Release
This release includes updated MITRE ATT&CK™ technique tags on several rules and added support for Microsoft Graph Security Alert API 1.0 via C2C.
Rules
- [Deleted] OUTLIER-S00012 Spike in AWS New Service Creation or Port Connection from Source Address
- As advised in the advanced notice on July 14th, 2023 - this Outlier rule was deleted due to performance and efficacy findings.
- [Updated] MATCH-S00679 AWS Route 53 Domain Registered
- [Updated] FIRST-S00038 First Seen Wget Usage from User
- [Updated] MATCH-S00830 Office 365 Forwarding Rule Created
- [Updated] LEGACY-S00064 Potentially vulnerable software detected
- [Updated] LEGACY-S00086 SSL Certificate Not Valid Yet
- [Updated] LEGACY-S00087 SSL Heartbleed Attack
- [Updated] LEGACY-S00089 SSL Heartbleed Many Requests
- [Updated] LEGACY-S00090 SSL Heartbleed Odd Length
- [Updated] LEGACY-S00091 SSL Invalid Server Cert
- [Updated] LEGACY-S00096 Shellshock
Log Mappers
- [New] Microsoft Graph Security Alert API C2C
Parsers
- [New] /Parsers/System/Microsoft/Graph Security Alert API
July 21, 2023 - Content Release
This release includes:
- Removal of unused legacy parsers and directly associated mappers and rule content.
- Support for Windows Event Log JSON ingested via Open Telemetry collector. XML and JSON via OTel are now fully supported in Cloud SIEM.
Rules
- [New] FIRST-S00038 First Seen Wget Usage from User
- Observes for execution of Wget from a user for the first time since the baseline period (14 days).
- [Updated] LEGACY-S00009 Bluecoat Proxy - Suspicious or Malicious Categories
- Fix to account for minor difference from legacy parser to current parser.
- [Updated] FIRST-S00016 First Seen Non-Network/Non-System Logon from User
- Excludes LogonTypes for System Startup, Batch, and Service to reduce volume of records matching.
- [Deleted] MATCH-S00073 Palo Alto - Traps Templated Events
Log Mappers
- [Updated] AWS Security Hub
- Lowered normalizedSeverity to reduce false positivity of passthrough signals.
- [Updated] CrowdStrike Falcon Identity Protection (CNC)
- Adjusted IdentityProtectionEvent normalizedSeverity to use INFO, LOW, MEDIUM, and HIGH instead of numeric values to improve consistency.
- [Updated] Windows - Security - 4627
- Added mapping for logonType '0' representing a system startup.
- [Deleted] AD Audit DNS
- [Deleted] AD Audit Comp
- [Deleted] AD Audit LDAP
- [Deleted] AD Audit Local Logon
- [Deleted] AD Audit Server
- [Deleted] AD Audit User
- [Deleted] Blue Coat Proxy 1
- [Deleted] Blue Coat Proxy 3
- [Deleted] Cisco Firepower Malware Event 430005
- [Deleted] Cisco Ironport WSA NOHD 02
- [Deleted] Citrix Xenserver Auth Message
- [Deleted] Cylance_Audit_1
- [Deleted] Cylance_Audit_2
- [Deleted] Ironport Cisco
- [Deleted] LINUX Root Login
- [Deleted] LINUX Root Login with Username
- [Deleted] LINUX User Authenticated
- [Deleted] LINUX User Authenticated no Username
- [Deleted] LINUX User Session Open/Close
- [Deleted] Palo Alto Traps Misc
- [Deleted] Symantec SEP Compressed File
- [Deleted] Symantec SEP MEM System
- [Deleted] Symantec SEP Potential Risk Found 04
- [Deleted] Symantec SEP Security Risk Found 2
- [Deleted] Symantec SEP Sonar Detection Variation 2
- [Deleted] Symantec SEP Virus Found
- [Deleted] Tanium S05 Logs
Parsers
- [New] /Parsers/System/Microsoft/Windows-JSON-Open Telemetry
Legacy Parsers
- [Deleted] ADAUDIT_COMP
- [Deleted] ADAUDIT_DNS
- [Deleted] ADAUDIT_LDAP
- [Deleted] ADAUDIT_LOCAL_LOGON
- [Deleted] ADAUDIT_SERVER
- [Deleted] ADAUDIT_USER
- [Deleted] BLUECOAT_PROXY_1
- [Deleted] BLUECOAT_PROXY_3
- [Deleted] CYLANCE_AUDIT1
- [Deleted] CYLANCE_AUDIT2
- [Deleted] Firepower_Malware_Event_430005
- [Deleted] IRON_PORT_CISCO
- [Deleted] IRON_PORT_WSA_NOHD_02
- [Deleted] LINUX_AUTH
- [Deleted] LINUX_ROOT_GENERIC
- [Deleted] LINUX_ROOT_LOGIN
- [Deleted] LINUX_ROOT_NO_USER
- [Deleted] LINUX_ROOT_USER
- [Deleted] PAN_TRAPS_MISC
- [Deleted] SYMANTEC_SEP_CF
- [Deleted] SYMANTEC_SEP_MEMS
- [Deleted] SYMANTEC_SEP_PRF_04
- [Deleted] SYMANTEC_SEP_SDN_02
- [Deleted] SYMANTEC_SEP_SRF_2
- [Deleted] SYMANTEC_SEP_VF_01
- [Deleted] TANIUM_S05_TYPE_LOGS
- [Deleted] VDM_LOG_SECURE
- [Deleted] citrix_xenserver_auth_message
July 21, 2023 - Application Update
Minor Changes and Enhancements
- [Update] The Cloud SIEM UI has been updated with refreshed fonts and colors to better align with the core Sumo Logic pages. This is the first change in a greater series of updates designed to present a more unified user experience across Sumo Logic feature sets.
- [New] The Signal Severity Total, an indication of the activity for an Entity, has been added to the Entity list and details views. The Signal Severity Total is calculated by adding up the severity value for each of the Signals generated against a given Entity during the current detection window (by default 14 days), not including duplicate or suppressed Signals.
Bug Fixes
- With the recent changes to log mapping, some users were seeing an error when attempting to use custom input vendors and/or products.
- Entity lookup normalization was taking place after Entity Groups were processed; normalization now happens first.
July 14, 2023 - Content Release
Starting with this release, the rule type for First Seen rules is now "Anomaly", and Outlier Rules have been promoted from prototype mode.
NOTE: Due to performance and efficacy findings, OUTLIER-S00012 will be deleted on July 28th. If you wish to retain this rule, it must be duplicated in the Cloud SIEM Rules UI.
Rules
- [Updated] OUTLIER-S00001 Spike in login failures from a user
- Removed incorrect match list from expression.
- Will remain in prototype an additional week due to changes made to the rule expression.
- [Updated] OUTLIER-S00002 Spike in Successful Distinct Share Access
- [Updated] OUTLIER-S00003 Spike in Failed Share Access by User
- [Updated] OUTLIER-S00004 Spike in Azure Firewall Deny Events from Source IP
- [Updated] OUTLIER-S00005 Spike in AWS API Call from User
- [Updated] OUTLIER-S00006 Spike in Data Transferred Outbound by User
- [Updated] OUTLIER-S00007 Spike in Windows Administrative Privileges Granted for User
- [Updated] OUTLIER-S00008 Spike in Failed Azure Sign In Attempts Due to Bad Password from IP Address
- [Updated] OUTLIER-S00009 Spike in PowerShell Command Line Length From Host
- [Updated] OUTLIER-S00010 Spike in URL Length from IP Address
- [Updated] OUTLIER-S00011 Spike in AWS AccessDenied Events by assumedrole
Schema
- [New] http_referer_queryParameters
- New queryParameters enrichment/mappable field
- [New] http_url_queryParameters
- New queryParameters enrichment/mappable field
- [New] objectClassification
- Allows objectClassification to be used in Cloud SIEM rule expressions.
July 13, 2023 - Application Update
New RBAC Capabilities
Reminder: Earlier this week, we introduced new RBAC capabilities for Cloud SIEM: View Entities and Manage Entities. Users with the built-in administrator role received these capabilities automatically, but admins must manually add these capabilities to other roles as appropriate. If a user does not have either role, they will not be able to see Entity details or interact with or manage Entities in any way.
Minor Changes and Enhancements
- [Update] The Entity Timeline feature is now available for all Entity types, including custom types.
- [New] When viewing an Entity's detail page, both Entity Groups that apply to that Entity and membership in a suppression list will now be listed.
Bug Fixes
- Some customers were seeing non-blocking errors loading Insight detail pages, and links to Cloud SOAR, when they should not have.
- The number of records ingested into Cloud SIEM was not being reported consistently on the HUD.
July 11, 2023 - Content Release
This content release includes parsing and mapping updates to Fortinet to account for variations in URL information present in the log sometimes leading to malformed URLs being normalized, adjustments to Jamf mappings to account for case variations in certain fields, as well as changes enumerated below.
Rules
- [Updated] OUTLIER-S00010 Spike in URL Length from IP Address
- Narrowed rule expression to NetworkHTTP and NetworkProxy records
Log Mappers
- [Updated] Fortinet App Control Logs
- [Updated] Fortinet DLP Logs
- [Updated] Fortinet Event Logs
- [Updated] Fortinet IPS Logs
- [Updated] Fortinet Traffic Logs
- [Updated] Fortinet Virus Logs
- [Updated] Fortinet Webfilter Logs
- [Updated] Jamf Audit User - Audit
- [Updated] Jamf Audit User - Authentication
- [Updated] Jamf Audit User - Endpoint
- [Updated] Jamf Audit User - Network
- [Updated] SentinelOne Logs - C2C threats
- Adds alternate value for normalizedSeverity lookup
Parsers
- [Updated] /Parsers/System/Cisco/Cisco Meraki
- Support for more variation in content filtering block logs and additional drops for events of limited to no security value.
June 29, 2023 - Content Release
This release includes parsing and mapping updates to Fortinet to account for variations in URL information present in the log sometimes leading to malformed URLs being normalized, adjustments to Jamf mappings to account for case variations in certain fields, as well as changes enumerated below.
Rules
- [Updated] OUTLIER-S00010 Spike in URL Length from IP Address
- Narrowed rule expression to NetworkHTTP and NetworkProxy records
Log Mappers
- [Updated] Fortinet App Control Logs
- [Updated] Fortinet DLP Logs
- [Updated] Fortinet Event Logs
- [Updated] Fortinet IPS Logs
- [Updated] Fortinet Traffic Logs
- [Updated] Fortinet Virus Logs
- [Updated] Fortinet Webfilter Logs
- [Updated] Jamf Audit User - Audit
- [Updated] Jamf Audit User - Authentication
- [Updated] Jamf Audit User - Endpoint
- [Updated] Jamf Audit User - Network
- [Updated] SentinelOne Logs - C2C threats
- Adds alternate value for normalizedSeverity lookup
Parsers
- [Updated] /Parsers/System/Cisco/Cisco Meraki
- Support for more variation in content filtering block logs and additional drops for events of limited to no security value.
- [Updated] /Parsers/System/Fortinet/Fortigate/Fortigate-Syslog
June 29, 2023 - Application Update
New RBAC Capabilities
Starting Thursday, July 6, we're introducing new RBAC capabilities for Cloud SIEM: View Entities and Manage Entities. Users with the built-in administrator role will receive these capabilities automatically, but admins must manually add these capabilities to other roles as appropriate. If a user does not have either role, they will not be able to see Entity details or interact with/manage Entities in any way.
Minor Changes and Enhancements
- [New] Nodes can now be moved around individually on the Insight Related Entities Graph.
- [Update] To align more closely with accepted industry definitions, we are changing the Dwell Time label on Insight metrics in the UI to Detection Time. Note that only the label is changing, not now the metric is calculated (i.e., the period of time between when the first record in an Insight was observed and when the Insight was created).
- [Update] Match list update containing more than 1000 entries are now supported by our Terraform provider.
- [Update] When a custom product or vendor is selected in log mapping, the string entered by the user is now indexed instead of the word "Custom", so that the custom entry can be searchable/filterable. This only applies to mappings configured going forward.
- [New] Custom tag schemas can now be retrieved via API (
GET /tag-schemas). - [New] When viewing Rule Tuning Expressions, if one applies to all rules, it will now say
Allinstead of giving a numerical count. - [Update] The Cloud SIEM UI color palette has been updated to more closely align with the standard Sumo Logic "dark mode" color palette.
Bug Fixes
- Insight sub-resolutions were not being passed to XSOAR correctly in some circumstances.
- Some users were unable to override fields on some Sumo-provided rules.
- When extracting fields in rule expressions, double quotes were not working (
{{fields["<field_name>"]}}).
June 22, 2023 - Content Release
This release includes additional parser and mappers for Aruba ClearPass Syslog events, minor bug fixes to several First Seen type rules, and other specifically enumerated changes below.
Rules
- [Updated] MATCH-S00814 Abnormal Child Process - sdiagnhost.exe - CVE-2022-30190
- Adds requirement that
commandLineis present for a match
- Adds requirement that
- [Updated] FIRST-S00016 First Seen Non-Network Logon from User
- [Updated] FIRST-S00008 First Seen whoami command From User
- [Updated] MATCH-S00815 Threat Intel - Successful Authentication from Threat IP
- Adds
dstDevice_ipto entity selection
- Adds
Log Mappers
- [New] Aruba ClearPass Guest Access
- [New] Aruba ClearPass WiFi Access Tracker
- [New] Aruba ClearPass Wifi Failed Tracker
- [Updated] Aruba ClearPass Syslog
- [Updated] Tenable.io Authentication
- Adds alternative key matches for
vuln_cveanddescriptionfields
- Adds alternative key matches for
Parsers
- [Updated] /Parsers/System/HP/Aruba ClearPass - Syslog
June 20, 2023 - Application Update
Outlier Rules
Sumo Logic is pleased to announce a new rule type for Cloud SIEM: Outlier Rules. This new rule type further enhances Cloud SIEM’s User and Entity Behavioral Analytics (UEBA) capabilities. With these rules, Cloud SIEM can detect events that deviate from the usual behavior of an Entity, such as a spike in login failures from a user, without having to define a static threshold. Once the rule is set, Cloud SIEM automatically builds a normal behavior baseline for each Entity based on the rule expression. It creates a signal only when a deviation from normal behavior is detected (in this case, too many login failures compared to their normal baseline behavior). Other examples include detecting a spike in Windows administrative privileges granted and a spike in AWS calls from a user.
Outlier Rules are defined like any other rule type through the Content menu in Cloud SIEM.
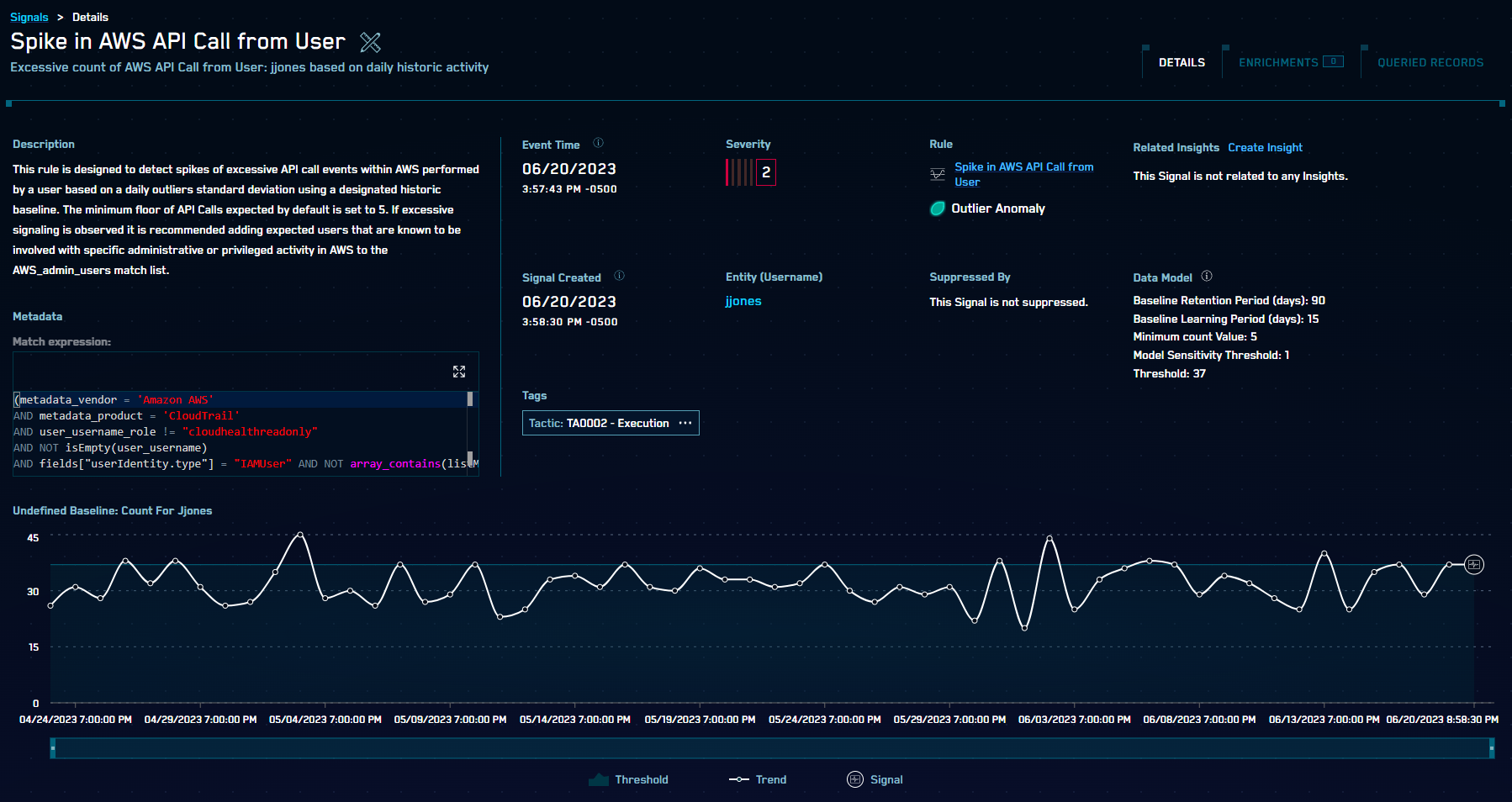
Outlier Rules operate based on a baseline. During this period - typically between 7 and 30 days - the system will learn what normal behavior looks like. After the baseline is established, Cloud SIEM will begin generating Signals when unusual behavior is detected compared to that baseline. (Note that the longer the baseline, the more accurate the model will be.)
Cloud SIEM will include a set of Outlier Rules out of the box. These rules can be tuned and customized like any other rule type, and custom Outlier Rules can also be created.
For more information about how to use Outlier Rules, see the online documentation. You can also see an introduction to the feature by navigating to the Rules page in Cloud SIEM.
Minor Changes and Enhancements
- [New] Users can now customize the global Signal Suppression period. During this period, which is set to 72 hours by default, duplicate signals (with identical names and Entities) are suppressed (for example, they do not “count” towards Insights). With this new feature, this period can be lowered globally (for all rules) to as low as 24 hours. (Note that lowering this value can lead to a higher number of potentially duplicate Insights.) The setting is accessible via the Workflow > Detection option in the Configuration menu.
- [Updated] Cloud SIEM application status will now be published on the main Sumo Logic status page, https://status.sumologic.com/. (Previously it was published on https://cse-status.sumologic.com/.) Existing email subscriptions and status notifications will be moved to the new page automatically.
June 12, 2023 - Application Update
Minor Changes and Enhancements
- [New] The Entity Timeline now supports all Entity types (including custom types).
- [New] The
GetSignalsAPI call now includes an attribute with a timestamp when each Signal wascreated. - [Updated] The log mapping UI has been updated so that if a standard vendor and product is selected, those values will be auto-filled on the record configuration, avoiding an issue where customers were accidentally creating 'custom' values.
Bug Fixes
- An error would occur when sorting entity groups by entity type.
- The control used to select schema tags for Entities was not working properly.
- The "View in Log Search / Normalized Data" button was opening a log search window with an incorrect time frame.
- Global search was not displaying previous searches, and was not returning some Entities.
- The rule tuning expression editor would not scroll for very long expressions.
- Importing a rule via the UI was not working in some scenarios.
June 2, 2023 - Content Release
Within this release, we made modifications to the Threat Intel MATCH-S00815 Rule to include the user_username associated with the 'src_Device_ip' to capture the account the threat IP authenticated with and to correlate on actions by the account. We also made a modification to the Azure Sign in Log mapper so that 'properties.userAgent' is mapped to the entity field 'http_userAgent'.
Rules
- [Updated] MATCH-S00815 Threat Intel - Successful Authentication from Threat IP
Log Mappers
- [Updated] AzureActivityLog 01
May 26, 2023 - Content Release
This release changes Crowdstrike mapper record types from 'Endpoint' to 'Audit' logs to align with Crowdstrike documentation, fixes to Fortinet severity scoring, SentinelOne IP mappings, additional values for Windows mappers for Snare, Snare parser updates for Windows Event 4947, updates to TrendMicro Deep Security CEF parser to allow for additional timestamp formats, and a minor rule update.
Rules
- [Updated] AGGREGATION-S00005 Suspicious System Enumeration Occurring in Quick Succession, Rule no longer in prototype
Log Mappers
- [Updated] CrowdStrike Audit Logs
- [Updated] CrowdStrike Falcon Host API DetectionSummaryEvent
- [Updated] CrowdStrike Falcon Host API IdpDetectionSummaryEvent (CNC)
- [Updated] CrowdStrike Falcon Identity Protection (CNC)
- [Updated] CrowdStrike Remote Response Session (CNC)
- [Updated] CrowdStrike UserActivity Logs
- [Updated] Fortinet DLP Logs
- [Updated] Fortinet IPS Logs
- [Updated] SentinelOne Logs - C2C agents
- [Updated] SentinelOne Logs - C2C threats
- [Updated] Windows - Security - 4947
- [Updated] Windows - Security - 4948
Parsers
- [Updated] /Parsers/System/Trend Micro/Trend Micro Deep Security - CEF
- [Updated] /Parsers/System/Microsoft/Shared/Windows Text Transforms - Security
May 12, 2023 - Content Release
Across the latest content release, the Threat Labs team has made a series of new AWS specific detections and a set of improvements both to the mappers and parser to include proper inbound / outbound network connection directional flow, and port assignments for AWS GuardDuty. Additional context and minor corrections/improvements can found within the list below.
Rules
- [New] MATCH-S00874 AWS Lambda Function Recon
- [New] MATCH-S00875 AWS VPC FLow Log Deletion
- [New] MATCH-S00876 Potential AWS Security Credential Access via curl
- [Updated] MATCH-S00226 Azure - Add Member to Group, TLAB-542 Update Azure Group Add rule and mapper addition, Keys updated:
summary_expression,normalized_summary
Log Mappers
- [Updated] AWS GuardDuty Alerts from Sumo CIP
- [Updated] AWSGuardDuty_Backdoor
- [Updated] AWSGuardDuty_Behavior
- [Updated] AWSGuardDuty_Catch_All
- [Updated] AWSGuardDuty_CryptoCurrency
- [Updated] AWSGuardDuty_Discovery
- [Updated] AWSGuardDuty_Exfiltration
- [Updated] AWSGuardDuty_PenTest
- [Updated] AWSGuardDuty_Trojan
- [Updated] AzureActivityLog AuditLogs
- [Updated] Recon_EC2_PortProbeUnprotectedPort
- [Updated] Recon_EC2_Portscan
- [Updated] Recon_IAMUser
- [Updated] UnauthorizedAccess_EC2_SSHBruteForce
- [Updated] UnauthorizedAccess_EC2_TorClient
- [Updated] UnauthorizedAccess_EC2_TorIPCaller
- [Updated] UnauthorizedAccess_EC2_TorRelay
- [Updated] UnauthorizedAccess_IAMUser
Parsers
- [Updated] /Parsers/System/AWS/AWS S3 Server Access Logs, AWS S3 Server Access Logs Parser Fix Related to New Fields and Wrapper
- [Updated] /Parsers/System/Cisco/Cisco ASA, Modifies ASA header parser to account for additional delimiter variant
- [Updated] /Parsers/System/AWS/GuardDuty
May 5, 2023 - Content Release
The latest iteration of our content release include Office 365 changes that address Mapping, Parsing and Rule changes that better take into account fields that were previously encapsulated within the Parameters field. Additionally, we performed improvements to the Zscaler Nanolog mapping and parsing to more accurately present port data even when extracted from URLs.
Rules
- [Updated] MATCH-S00830 Office 365 Forwarding Rule Created
- [Updated] MATCH-S00831 Office 365 Unified Audit Logging Disabled
Log Mappers
- [Updated] Microsoft Office 365 Exchange Mailbox Audit Events: Keys updated: 'targetUser_username'
- [Updated] Office 365 - Exchange Admin Events: Keys updated: 'user_username', 'targetUser_username'
- [Updated] Zscaler - Nanolog Streaming Service - JSON: Keys updated: 'dstPort'
Parsers
- [Updated] /Parsers/System/Cisco/Cisco Firepower Syslog: REGEX modifications to parse the Firepower Event ID
- [Updated] /Parsers/System/Microsoft/Office 365
- [Updated] /Parsers/System/Zscaler/Zscaler Nanolog Streaming Service/Zscaler Nanolog Streaming Service-CEF
- [Updated] /Parsers/System/Zscaler/Zscaler Nanolog Streaming Service/Zscaler Nanolog Streaming Service-JSON
- [Updated] /Parsers/System/Zscaler/Zscaler Nanolog Streaming Service/Zscaler Nanolog Streaming Service-LEEF
May 3, 2023 - Application Update
Cloud SIEM Insight Trainer
We are excited to announce the release of Cloud SIEM Insight Trainer, a dashboard packaged with the Cloud SIEM Application.
Many security teams spend time every week tuning their SIEM to improve detections and focus SOC analyst attention on the most serious threats. Insight Trainer utilizes machine learning to provide Rule tuning recommendations and severity adjustments to significantly reduce the burden of manual tuning. Insight Trainer learns Rule severity adjustments from your Insights' history that reduces false positive, and optionally, "No Action" Insights.
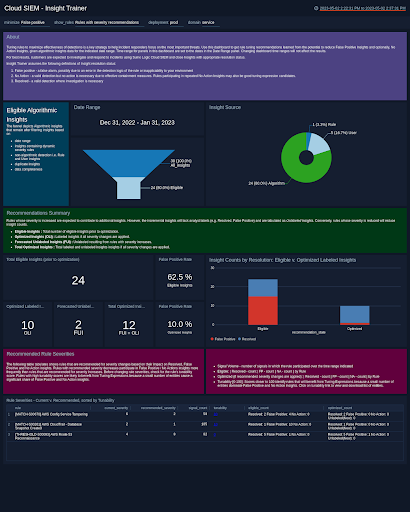
Some of the highlights of Insight Trainer include:
- Customer-Specific Tuning Recommendations - Insight Trainer makes recommendations specific to each customer based on their unique set of Rules, Insight history, and analyst Insight resolutions.
- Improved SOC Efficiency - Insight Trainer automates the manual process of identifying Rules that are candidates for tuning or severity adjustment and provides impact analysis of the changes.
- Machine Learning/AI-Driven Analytics - Insight Trainer leverages machine learning and AI to deliver outcome-based recommendations geared towards the reduction of false positive and non-actionable Insights without compromising the actual detection value or true positive Insights in Cloud SIEM.
- Easy Adoption - The dashboard is available as an update to our already existing Enterprise Audit Cloud SIEM application and can be set up to run with no additional configuration or data science knowledge.
Periodic application of the recommended changes will improve the quality of Insights generated by Cloud SIEM. For more information about the Insight Trainer, see our detailed online documentation.
Bug Fixes
- On the Insight Related Entities list, some of the Signal counts were incorrect.
- Whitespace, including new lines, were being stripped from some Enrichments formatted in JSON.
- Indicators not using the proper case were being accepted but displaying as "NotFlagged" in the UI.
April 28, 2023 - Content Release
Rules
Updates several Azure based rules to account for modifications made to normalization mappers.
- [New] MATCH-S00873 AWS EKS Cluster Configuration Updated: AWS EKS clusters contain various configuration options, including for which IP addresses can access the cluster API. Ensure that this change is authorized and expected.
- [New] MATCH-S00872 AWS EKS Failed Curl Authentication Attempt: Failed instances of curl usage within a containerized environment should occur rarely. Investigate the source IP address used to ensure that it is legitimate.
- [New] MATCH-S00871 AWS EKS Pod Shared Object Modification or Creation: A Kubernetes pod was either created, updated or patched with a shared process namespace.
- [New] MATCH-S00870 AWS EKS Secrets Created: Kubernetes secrets may be created for legitimate purposes. Ensure that the secret created is from an IAM account that is expected to manage Kubernetes workloads on EKS.
- [New] MATCH-S00869 AWS EKS Secrets Deleted: Kubernetes secrets may be deleted for legitimate purposes. Ensure that the secret created is from an IAM account that is expected to manage Kubernetes workloads on EKS.
- [New] FIRST-S00036 First Seen AWS EKS API Call via CloudTrail from User: The user
user_usernamehas performed an operation on an EKS cluster for the first time since the baseline period. - [New] FIRST-S00037 First Seen AWS EKS Admission Controller Created by IP Address: First Seen Admission Controllers (submit a new MutatingWebhookConfiguration or ValidatingWebhookConfiguration object via the Kubernetes API, or update an existing one.)
- [New] FIRST-S00035 First Seen AWS EKS Secrets Enumeration from IP Address:
srcDevice_iphas enumerated secrets on an AWS EKS cluster for the first time since the baseline period. - [New] FIRST-S00034 First Seen Session Token Granted to User from New IP: An AWS Session token was issued for the first time since the baseline period to
user_usernameusing the IP address ofsrcDevice_ip. - [New] FIRST-S00033 First Seen Terminal-Attached Pod Deployed to EKS: A pod was deployed with an attached terminal (stdin=true,stdout=true,tty=true) for the first time since the baseline period.
- [New] THRESHOLD-S00114 HTTP Response Error Spike to AWS EKS: HTTP web services provide response codes to client requests. The response code numbers in the 400s are used to indicate a client related error and response code numbers in the 500s represent server related errors. This rule looks for a AWS EKS cluster receiving a large frequency of web errors within a short period of time. It is unusual for a web client to cause this many errors in a short period of time. Common occurrences for this behavior is scanning/probing activity or scripted web clients which are now encountering errors due to a misconfiguration or recent change. This rule alerts when a host on the monitored network triggers the threshold.
- [New] MATCH-S00868 New Binding Role Created on AWS EKS: A role binding grants a resource superuser or administrative access to a Kubernetes cluster. Ensure this action is expected and performed by known Kubernetes administrators.
- [New] MATCH-S00867 New Cluster Admin Binding Role Created on AWS EKS: A cluster-admin role binding grants a resource superuser or administrative access to a Kubernetes cluster. Ensure this action is expected and performed by known Kubernetes administrators.
- [New] MATCH-S00866 Privileged Pod Created on AWS EKS: Privileged containers have all capabilities of the host machine. These privileged containers may perform actions directly on the host that they are running on. Ensure that this event is expected and occurs from a user account or IP address that normally works with privileged containers within the cluster. Customers are encouraged to set up an exclusion list for
spec.securitycontext.capabilitiesfor pods that are frequently going to be managed with privileged escalation. - [Updated] MATCH-S00864 Azure Firewall Rule Modified
- [Updated] MATCH-S00839 Azure Virtual Machine RunCommand Issued
- [Updated] FIRST-S00021 First Seen Azure Virtual Machine Run Command Issued by User
- [Updated] FIRST-S00032 First Seen Kubectl Command From User: Expanded record types considered to include Endpoint.
- [Updated] CHAIN-S00012 Potential Azure Persistence via Automation Accounts
- [Updated] MATCH-S00167 Recon Using Common Windows Commands: Narrowed rule criteria to Windows executables to prevent erroneous matches from *nix based systems
Log Mappers
- [New] Administrator Audit Trail: Modified CyberArk EPM mappers to include alternate field values.
- [New] Administrator Logon
- [New] Darktrace Parser - Anomalous Connection: Modifies Darktrace mappers to include alternate field values and supports additional events.
- [New] Darktrace Parser - Brute Force Attempt
- [New] DocuSign Monitor - Alert
- [New] DocuSign Monitor - Catch All: Adds support for DocuSign Monitor events via C2C.
- [New] Druva inSync - Catch All: Adds support for Druva events via C2C.
- [New] Jamf Audit User - Authentication
- [New] Jamf Audit User - Endpoint
- [New] Jamf Audit User - Network
- [New] Workday - Sign On: Expands mapping support for Workday logs ingested via C2C.
- [Updated] Azure Administrative logs
- [Updated] Cisco Meraki IDS Alert - C2C: Corrects typo in mapper for some IP/port fields
- [Updated] Darktrace Parser - Catch All:
- [Updated] Darktrace Parser - New Device
- [Updated] Darktrace Parser Events
- [Updated] Jamf Audit User - Audit
- [Updated] Sysdig Benchmark JSON: Corrects bug in severity mapping for Sysdig mappers.
- [Updated] Sysdig Policy Detection JSON: Corrects bug in severity mapping for Sysdig mappers.
- [Updated] Sysdig Scanning JSON: Corrects bug in severity mapping for Sysdig mappers.
- [Updated] Workday - Catch All: Expands mapping support for Workday logs ingested via C2C.
- [Updated] Zscaler - Nanolog Streaming Service - JSON: Corrects NSS record type to NetworkProxy instead of NetworkFlow
Parsers
Adds support for DocuSign Monitor and Druva inSync Cloud, and additional support for Meraki, CyberArk, and Workday events.
- [New] /Parsers/System/DocuSign/DocuSign Monitor
- [New] /Parsers/System/Druva/Druva inSync Cloud
- [Updated] /Parsers/System/Cisco/Cisco Meraki: Strip off extraneous … from URLs
- [Updated] /Parsers/System/Cyber-Ark/CyberArk EPM JSON: Corrected time parsing
- [Updated] /Parsers/System/Darktrace/Darktrace JSON
- [Updated] /Parsers/System/Duo Security/Duo Multi-Factor Authentication: Duo Parser Fix for Setting Event ID Correctly
- [Updated] /Parsers/System/Palo Alto/PAN Firewall CEF: Adds support for Network events ingested via a log forwarder or Cortex Data Lake.
- [Updated] /Parsers/System/Workday/Workday
April 21, 2023 - Application Update
Automation Service
Sumo Logic is excited to announce a new feature that integrates functionality previously available only in our Cloud SOAR solution directly into Cloud SIEM. This new feature, the Automation Service, allows you to define and automate smart actions, including enrichments and notifications, enabling your security analysts to address potential security threats faster and more accurately.
You can interact with the service through automations, which execute playbooks. Playbooks are composed of one or more actions with a workflow that can include parallel actions and logic steps. Actions are defined as part of integrations.
The Automation Service includes over 350 integrations out of the box, each including several predefined actions:
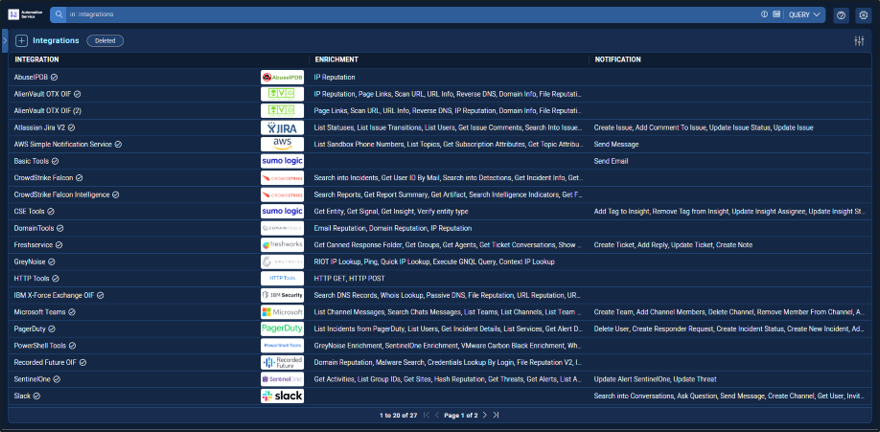
Many playbooks are also included, providing instant value with practically no effort - simply connect the integration to the appropriate endpoint and enable the corresponding automation in Cloud SIEM. Playbooks can be automatically triggered when Insights are created or closed, or triggered manually.
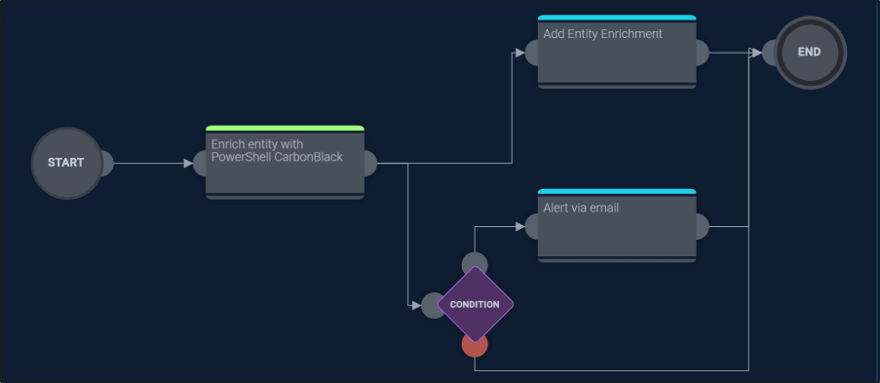
You can also customize these objects or create entirely new ones. While the out of the box actions primarily execute directly from the Sumo Logic cloud, custom actions run through a proxy called a Bridge which runs on a system managed by you.
Automations (and other objects) are accessible through the Configuration menu, under Integrations:
Automation results are accessible from Insight and Entity detail pages.
The Insight Enrichment Server and the Actions functionality in Cloud SIEM, which is replaced by the Automation Service, will be deprecated on November 30, 2023. Until then, they will continue to be fully supported and operational. To aid in migration, all current Enrichment Server examples and Actions have equivalent actions and playbooks in the Automation Service. In addition, through the Bridge, customers can execute any existing PowerShell script currently connected to the Insight Enrichment Server.
The Automation Service currently has Limited Availability. This means that it is fully functional and supported in production environments, but not automatically deployed to every customer. If you would like it deployed to your environment, please contact Sumo Logic and we will enable it for you.
There is much more information about the Automation Service and how to use it in the online documentation.
Threat Indicators
The way enrichments are displayed in Cloud SIEM is also being enhanced to provide important information to security analysts when they need it, without having to look it up.
First, the Enrichment tabs have been reorganized by Entity (instead of by Enrichment) and additional filter controls have been added:
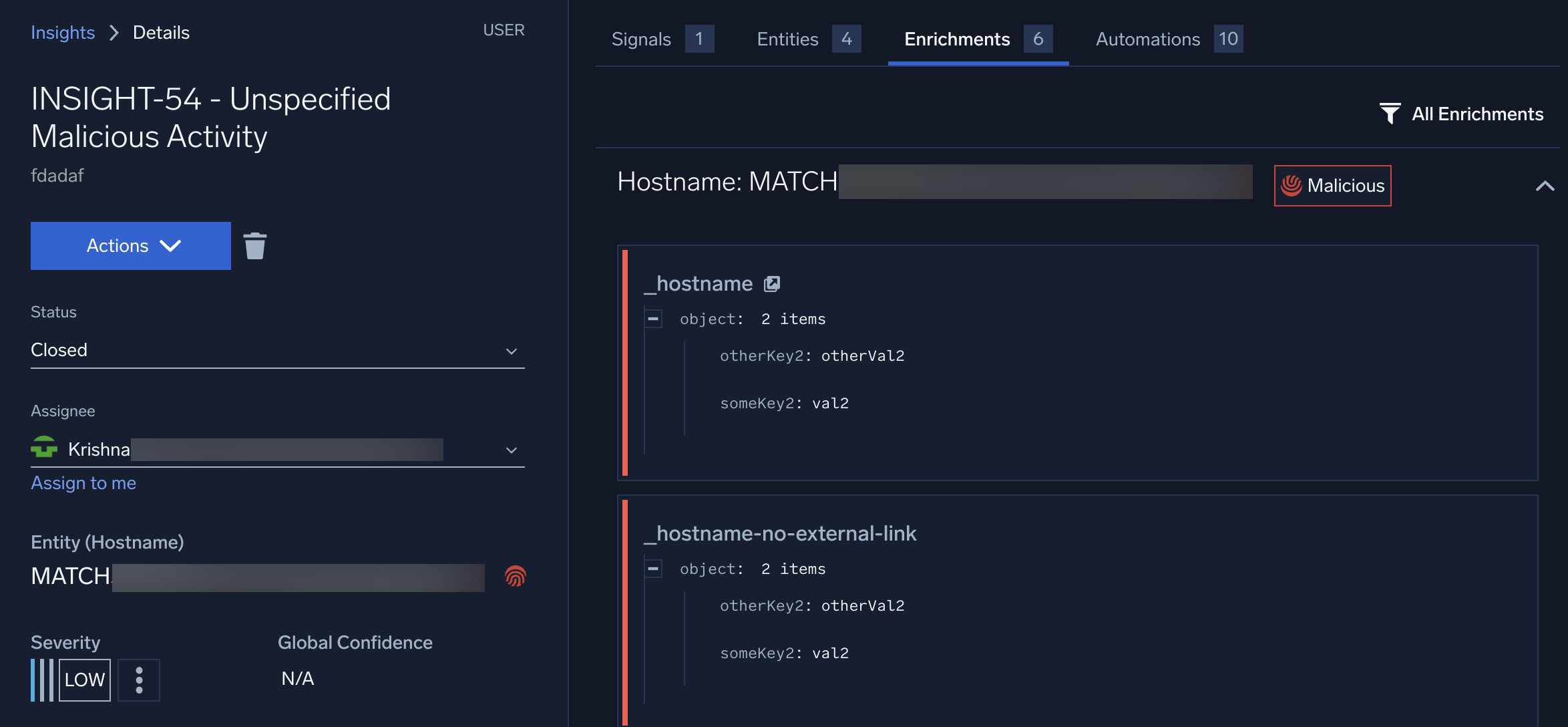
In addition, Entity enrichments will now persist outside of Insights. So, for example, if an Entity is enriched as part of an Insight, those enrichment details will be visible from that Entity’s details page.
This persistence can be controlled by setting an expiration date as part of the enrichment. In addition, URLs can be attached to enrichments (so that users can click on the link to see more detailed information about the enrichment by, for example, going to the VirusTotal web page for that indicator).
Finally, enrichments can now set reputation indicators. These indicators will be visible anywhere in the UI that the Entity is displayed. Where there is sufficient room, a color-coded text label will be displayed (as in the example above); in other situations, an icon will be displayed instead.
The reputation is not set automatically; the enrichment must pass a reputation to Cloud SIEM. More information about this, and the other new features, is available in online documentation.
Minor Changes and Enhancements
- [Updated] The Entity Relationship Graph view on Insights has exited open Beta and is now fully supported.
- [New] When using custom columns with Match Lists, CIDR block matches are now supported with IP address-related fields.
- [New] When referring to Match Lists, specific columns can now be specified in rule conditions for all Match List types. (Previously this functionality was only available for Threat Intelligence lists.)
April 20, 2023 - Content Release
Summary
Within our latest content release we are introducing a new set of rules related to our 5th Threat Research Campaign structured around Docker, Azure, and Linux. We also made Mapper additions to support Cisco Meraki events ingested via C2C, Cyber Ark Mapper improvements, and new Jamf Audit User Event and Jamf Protect Mappers.
Rules
- [New] MATCH-S00864 Azure Firewall Rule Modified Description: The Azure Firewall may provide egress and ingress controls for a variety of Azure services; unexpected or unplanned firewall modifications should be investigated.
- [New] AGGREGATION-S00006 Docker Enumeration Detected on Host Description: Threat actors will aim to enumerate various permissions and settings on hosts with Docker installed; this enumeration can potentially lead to exploitation avenues.
- [New] FIRST-S00031 First Seen IP Address Associated with User for a Successful Azure AD Sign In Event Description: User has successfully signed into an Azure resource with a first seen IP address since the baseline period.
- [New] FIRST-S00032 First Seen Kubectl Command From User Description: User has issued a Kubectl command which was first seen since the baseline period on hostname.
- [New] THRESHOLD-S00112 Multiple Azure Firewall Deny Events for IP Description: An Azure firewall has denied a large number of request from an IP address within a short time window.
- [New] THRESHOLD-S00113 Multiple Azure Firewall Deny Events for URL Description: An Azure firewall has denied a large number of requests to a URL within a short time window.
- [New] MATCH-S00865 Potential Docker Escape via Command Line Description: This rule looks for whether the raw Docker socket was used for container creation as well as a bind mount of /hostfs which could facilitate a container escape and allow command execution on the Docker host.
- [New] CHAIN-S00014 Potential Docker container escape via Cgroups. Description: A Docker container running with the privileged flag may be exploited by threat actors, potentially resulting in an escape from the Docker container to the host that it is running on. This can result in various privilege escalation opportunities.
- [New] CHAIN-S00015 Suspicious Linux Execution Chain Description: This alert looks for a number of search expressions that result in a suspicious Linux execution chain. Specifically, a file that is created in a users' home directory or in /tmp, followed by a chmod and file execution, as well as the process making a network connection.
Log Mappers
- [New] Cisco Meraki File Scanned - C2C
- [New] Cisco Meraki IDS Alert - C2C
- [New] Cisco Meraki Organization Configuration Change - C2C
- [New] Cisco Meraki Wireless Air Marshall - C2C
- [New] Jamf Audit User - Events
- [New] Jamf Protect Analytics - Events
- [Updated] Cisco Meraki 8021x
- [Updated] Cisco Meraki Catch All - Custom Parser
- [Updated] Cisco Meraki Client Association
- [Updated] Cisco Meraki Content Filtering Block - Custom Parser
- [Updated] Cisco Meraki Flow Start_End - Custom Parser
- [Updated] Cisco Meraki Flows - Custom Parser
- [Updated] Cisco Meraki IDS - Custom Parser
- [Updated] Cisco Meraki Security Filtering Disposition Change - Custom Parser
- [Updated] Cisco Meraki Security Filtering File Scanned - Custom Parser
- [Updated] Cisco Meraki URLS - Custom Parser
- [Updated] Cisco Meraki WPA - Custom Parser
- [Updated] Cyber Ark 01
- [Updated] Cyber Ark EPM AggregateEvent
- [Updated] Cyber Ark EPM AuditAdmin
- [Updated] Cyber Ark EPM GetComputer
- [Updated] Cyber Ark EPM Policy
- [Updated] Cyber Ark EPM RawDetails
- [Updated] Cyber Ark EPM RawEvents
- [Updated] Cyber Ark Vault JSON
- [Updated] Jamf Parser - Catch All
Parsers
- [New] /Parsers/System/Cisco/Cisco Meraki C2C
- [New] /Parsers/System/Sophos/Sophos Central C2C JSON
- [Updated] /Parsers/System/Jamf/Jamf
April 13, 2023 - Content Release
Summary
- Updated GuardDuty mappers to use detail.type instead of overly verbose detail.description.
- Added parsing and mapping support for Citrix Cloud C2C.
- Secondary update corrections around Matchlist fix for column specifc filters.
- New Sophos C2C mapper expansion around Event and Alert normalization.
- Net-new OOBB content for Zoom; eight-Match rules, six Mappers, one Parser.
Rules
- [New] MATCH-S00856 Zoom - Account Created
- [New] MATCH-S00857 Zoom - Account Deleted
- [New] MATCH-S00858 Zoom - Group Admin Added
- [New] MATCH-S00859 Zoom - Group Admin Deleted
- [New] MATCH-S00860 Zoom - Group Changes
- [New] MATCH-S00861 Zoom - Information Barrier Policy Changes
- [New] MATCH-S00862 Zoom - Meeting Risk Alert
- [New] MATCH-S00863 Zoom - Recording Modification
- [Updated] THRESHOLD-S00096 Brute Force Attempt
- [Updated] MATCH-S00565 Direct Outbound DNS Traffic
- [Updated] THRESHOLD-S00103 Domain Brute Force Attempt
- [Updated] THRESHOLD-S00102 Domain Password Attack
- [Updated] THRESHOLD-S00095 Password Attack
- [Updated] CHAIN-S00008 Successful Brute Force
Log Mappers
- [New] Citrix Cloud Client Created or Deleted
- [New] Sophos - C2C Alerts
- [New] Sophos - C2C Event Threat Detections
- [New] Zoom - Account Creations or Deletions
- [New] Zoom - Catch All
- [New] Zoom - Group Modifications
- [New] Zoom - Information Barrier Policy Modifications
- [New] Zoom - Meeting Risk Alert
- [New] Zoom - Recording Deleted or Trashed
- [Updated] AWSGuardDuty_PenTest
- [Updated] AWSGuardDuty_Stealth
- [Updated] Recon_EC2_PortProbeUnprotectedPort
- [Updated] Recon_IAMUser
Parsers
- [New] /Parsers/System/Citrix/Citrix Cloud C2C
- [New] /Parsers/System/Zoom/Zoom
April 13, 2023 - Application Update
Minor Changes and Enhancements
- [New] When logs fail to parse or map, a detailed error message will be logged in the
sec_record_failureindex, in thefields.reasonattribute. - [New] Where possible, private domains are now automatically enriched by Cloud SIEM during record processing.
- [Updated] Insight comments can now contain up to 1024 characters (up from 256).
- [New] On the list of Rule Tuning Expressions, each Tuning Expression now lists the number of Rules to which it is currently applied.
- [New] For First Seen Rules, the UI will display the baseline model status (i.e., building, with amount of progress, or complete). (Note it will only display the status on Rules that were created or updated after this feature became available.)
Bug Fixes
- In some cases, inventory data from an AWS EC2 source was not being displayed in Cloud SIEM properly.
- For Yara-based signals with file attachments, users were unable to download the file.
- Occasionally, some related Entities were not visible in the Insight Related Entities graph but were included correctly on the list.
- Entity suppression state was being reported incorrectly on several screens.
- The
Manage Entity Groupspermission was required to view Entity Groups. Now onlyView Entity Groupsis required. - Links to the Cloud SIEM API no longer require a trailing slash.
April 7, 2023 - Content Release
This release includes bug fixes for several rules using match lists using the "column" field in the rule expression.
Rules
- [New] FIRST-S00030 First Seen Outbound Connection to External IP Address on Port 445 from IP Address; External connections over the internet to port 445 could be indictative of hash leak attempts, including exploitation attempts for vulnerabilities such as CVE-2023-2397. This alert looks at a source IP address making a connection to a new external destination IP address since the baseline period.
- [Updated] FIRST-S00029 First Seen Successful Authentication From Unexpected Country; Added additional logic to help reduce false positives
- [Updated] THRESHOLD-S00096 Brute Force Attempt
- [Updated] MATCH-S00565 Direct Outbound DNS Traffic
- [Updated] THRESHOLD-S00103 Domain Brute Force Attempt
- [Updated] THRESHOLD-S00102 Domain Password Attack
- [Updated] THRESHOLD-S00095 Password Attack
- [Updated] CHAIN-S00008 Successful Brute Force
Log Mappers
- [New] OpenVPN Logon Attempt
- [New] OpenVPN Network Event
- [New] Snowflake Catch All
- [New] Snowflake Login
- [New] Windows Defender ATP Alert
- [Updated] Netskope - Audit Authentication Events - Logoff; Made eventID match more permissive
Parsers
- [New] /Parsers/System/Snowflake/Snowflake
- [New] /Parsers/System/Microsoft/Windows Defender ATP Alert JSON
- [Updated] /Parsers/System/Cisco/Cisco ASA; Build/Teardown parsing bug fix
- [Updated] /Parsers/System/OpenVPN/OpenVPN Syslog; Added support for additional format
March 24, 2023 - Content Release
Overall improvements to OOTB First Seen rules include minor baseline tweaks and severity adjustments for the following rules. For corrections involving logic adjustment, additional context is included within the individual rule. This update also adds Alternative Values for ProofPoint TAP Mappers.
Rules
- [Updated] FIRST-S00002 First Seen AWS API Call from User; General logic improvement to filter on valid Identity type
- [Updated] FIRST-S00023 First Seen AWS API Gateway Enumeration by User; General logic improvement to filter on valid application
- [Updated] FIRST-S00024 First Seen AWS SSM RunShellScript SendCommand From User
- [Updated] FIRST-S00026 First Seen Anonymous Logon Change Activity to Domain Controller
- [Updated] FIRST-S00007 First Seen DynamoDB Enumeration from User
- [Updated] FIRST-S00004 First Seen Local Group Addition by User
- [Updated] FIRST-S00009 First Seen RDP Logon From User
- [Updated] FIRST-S00022 First Seen S3 Bucket ACL Enumeration by User
- [Updated] FIRST-S00025 First Seen SMB Allowed Traffic From IP
- [Updated] FIRST-S00029 First Seen Successful Authentication From Unexpected Country
- [Updated] FIRST-S00011 First Seen Sysmon IMPHASH - Global; Reconfigured to be disabled by default
- [Updated] FIRST-S00012 First Seen Sysmon IMPHASH - Host; Reconfigured to be disabled by default
- [Updated] FIRST-S00005 First Seen User Creation From User
- [Updated] FIRST-S00008 First Seen whoami command From User
Log Mappers
- [Updated] Proofpoint Targeted Attack Protection C2C - Click Blocked
- [Updated] Proofpoint Targeted Attack Protection C2C - Click Permitted
- [Updated] Proofpoint Targeted Attack Protection C2C - Message Blocked
- [Updated] Proofpoint Targeted Attack Protection C2C - Message Delivered
- [Updated] Proofpoint Targeted Attack Protection C2C - Message Permitted
March 16, 2023 - Application Update
Minor Changes and Enhancements
- [New] The Entity Timeline can now be filtered by record type:
Bug Fixes
- When an Entity normalization lookup table was deleted and then re-created in the Sumo platform, the configuration in Cloud SIEM was not automatically updated, causing the normalization to fail.
- Match lists with custom columns were not working properly during record processing.
- The Network Blocks section was missing from the Entity details panel.
- Links for schema tags were not displaying in the UI properly.
March 15, 2023 - Content Release
Rules
- [New] CHAIN-S00013 GCP IDS Detection Followed by API Call; Detects a GCP IDS hit followed by an API call, indicating the source IP was able to gain access to GCP.
- [Updated] THRESHOLD-S00087 Slack - Possible Session Hijacking; Adjusts "Slack - Possible Session Hijacking" to use 'sessionId' schema field.
Log Mappers
- [New] GCP IDS; Mapper for GCP IDS events
- [New] Netskope - Catch All; Added 'Catch All' Mapper to account for unavailability of event identifier in all messages.
- [New] Slack Login; Added mapping specific to logon success/failure events
- [Updated] Slack Catch All; Adjusts mapper use new sessionIdschema field in place of sourceUid
Parsers
- [Updated] /Parsers/System/Cisco/Cisco Firepower Syslog; Adjusts Cisco Firepower parser for some FTD events and corrected routing for Snort like and ASA messages which pass through the Firepower parser.
- [Updated] /Parsers/System/Google/GCP; Adds additional time format handling
Schema
- [New] sessionId; An ephemeral and at least semi-unique identifier of a connection between two systems (e.g., HTTP session, user logon session, TCP session identifiers)
March 10, 2023 - Content Release
This release contains a new set of mappers related to AWS CloudTrail Lambda functions, permissions, and sources and how changes related to them can align across our schema. In addition to that we have a correction to the parsing rerouted path 'System' in the parser path for Snort-like formatted messages.
Log Mappers
- [New] CloudTrail - lambda.amazonaws.com - AddLayerVersionPermission
- [New] CloudTrail - lambda.amazonaws.com - AddPermission
- [New] CloudTrail - lambda.amazonaws.com - CreateEventSourceMapping
- [New] CloudTrail - lambda.amazonaws.com - CreateFunction
- [New] CloudTrail - lambda.amazonaws.com - CreateFunctionUrlConfig
- [New] CloudTrail - lambda.amazonaws.com - DeleteEventSourceMapping
- [New] CloudTrail - lambda.amazonaws.com - DeleteFunction
- [New] CloudTrail - lambda.amazonaws.com - DeleteFunctionUrlConfig
- [New] CloudTrail - lambda.amazonaws.com - GetEventSourceMapping
- [New] CloudTrail - lambda.amazonaws.com - GetFunction
- [New] CloudTrail - lambda.amazonaws.com - GetFunctionConfiguration
- [New] CloudTrail - lambda.amazonaws.com - GetFunctionUrlConfig
- [New] CloudTrail - lambda.amazonaws.com - GetLayerVersionPolicy
- [New] CloudTrail - lambda.amazonaws.com - GetPolicy
- [New] CloudTrail - lambda.amazonaws.com - ListEventSourceMappings
- [New] CloudTrail - lambda.amazonaws.com - ListFunctionUrlConfigs
- [New] CloudTrail - lambda.amazonaws.com - ListFunctions
- [New] CloudTrail - lambda.amazonaws.com - PublishLayerVersion
- [New] CloudTrail - lambda.amazonaws.com - RemovePermission
- [New] CloudTrail - lambda.amazonaws.com - UpdateEventSourceMapping
- [New] CloudTrail - lambda.amazonaws.com - UpdateFunctionCode
- [New] CloudTrail - lambda.amazonaws.com - UpdateFunctionConfiguration
- [New] CloudTrail - lambda.amazonaws.com - UpdateFunctionUrlConfig
Parsers
- [Updated] /Parsers/System/Suricata/Suricata Syslog
March 7, 2023 Application Update
Entity Relationship Graph
We are excited to announce the new Entity Relationship Graph. With this feature, you can now see a graphical visualization of all related Entities in an Insight, as well as additional relationships beyond the Insight. This enables you to more quickly understand relationships among Entities and the larger context behind a potential security threat.
This feature is available to all customers but is currently in Beta. If you encounter any issues with this feature, report them to Sumo Logic Support. We appreciate your feedback.
The Entity Relationship Graph (and the Related Entities list) displays all Entities involved in the Insight (those referred to in a record in a Signal in the Insight) as well as additional Entity relationships (for example, if Cloud SIEM detects an IP address may also have had a specific hostname at the time the Insight was generated).
However, unlike the Related Entities list, the graph can visualize additional Entity relationships that existed outside of the Insight during a specified time frame.
Both the list and this new graph are available on the Entities tab of the Insight details page:
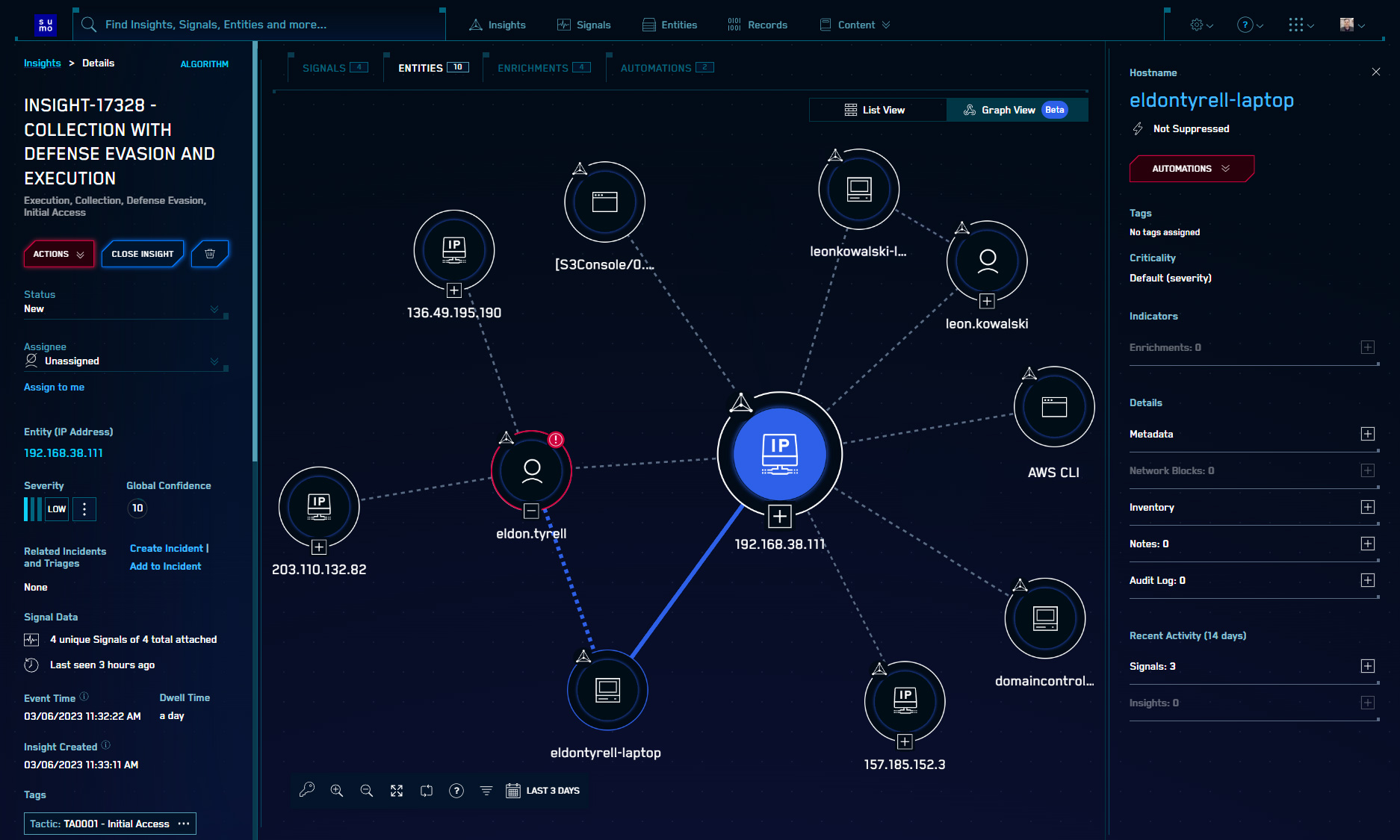
You can toggle between the list view and the graph view using the control in the upper-right corner of the main panel.
Each node in the graph represents a single Entity. The graph also displays the relationship types and any Indicators. Hovering over an Entity will highlight it and all of its relationships to other Entities, and when an Entity is selected, details about the Entity are displayed on the right.
The graph also includes a number of controls for zoom, full screen mode, filtering by Entity type, and adjusting the time frame for relationship detection.
For more information about how to use the Entity Relationship Graph, see the online documentation. You will also see an introduction to the feature the first time you visit an Insight details page.
Minor Changes and Enhancements
- [New] First Seen Rules now support the use of non-normalized record fields.
- [New] When a file is attached to a Signal, it is now available via API (previously it would only be available if part of a Yara Signal or Threat Intel match). The endpoint is
/api/v1/extracted-file?filename= - [Update] The default time frame on the Entity Timeline is now 3 days instead of 24 hours.
- [Update] The http v2 Insight Action payload now includes a numeric severity value (1-4) in addition to the human-readable severity name (LOW, MEDIUM, HIGH, CRITICAL).
- [Update] On the new Active Entities panel on the HUD, if the Entity is a Username, you can now navigate directly to that Entity’s Timeline by hovering over the Entity name and clicking the link.
Bug Fixes
- In some cases, Cloud SIEM was unable to properly extract the user name from an AWS ARN.
- A recent change caused checkboxes to malfunction in Firefox.
- On the Entity Timeline record details, the timestamp wasn’t displaying properly.
March 2, 2023 - Content Release
This release contains changes to how the Palo Alto Firewall CSV parser handles timestamps. Time parsing now relies on _messagetime metadata generated at collection time. This allows individual sources to set timezone information if it is not available in the raw message and as a result, reflect more accurate timestamps for records being created.
Rules
- [New] MATCH-S00844 LastPass - Account Created
- [New] MATCH-S00854 LastPass - Failed Login
- [New] MATCH-S00846 LastPass - Folder Permissions Updated
- [New] MATCH-S00855 LastPass - Login
- [New] MATCH-S00847 LastPass - Master Password Changed
- [New] MATCH-S00848 LastPass - Password Changed
- [New] MATCH-S00849 LastPass - Personal Share
- [New] MATCH-S00850 LastPass - Policy Added
- [New] MATCH-S00851 LastPass - Policy Deleted
- [New] MATCH-S00852 LastPass - Shared Folder Created
- [New] MATCH-S00853 LastPass - Super Admin Password Reset
Log Mappers
- [New] LastPass - Account Created
- [New] LastPass - Failed Login
- [New] LastPass - Folder Permissions Updated
- [New] LastPass - Login
- [New] LastPass - Master Password Changed
- [New] LastPass - Password Changed
- [New] LastPass - Personal Share
- [New] LastPass - Policy Modifications
- [New] LastPass - Shared Folder Created
- [New] LastPass - Super Admin Password Reset
- [New] LastPass Catch All
- [New] Sysdig Audit Trail JSON
- [New] Sysdig Benchmark JSON
- [New] Sysdig Command JSON
- [New] Sysdig Connection JSON
- [New] Sysdig File Access JSON
- [New] Sysdig Kubernetes JSON
- [New] Sysdig Policy Detection JSON
- [New] Sysdig Scanning JSON
- [Updated] Azure Firewall Network Rule
- [Updated] Mimecast Email logs
Parsers
- [New] /Parsers/System/LastPass/LastPass
- [New] /Parsers/System/Sysdig/Sysdig JSON
- [Updated] /Parsers/System/Microsoft/Microsoft Azure JSON
- [Updated] /Parsers/System/Palo Alto/PAN Firewall CSV
- [Updated] /Parsers/System/Microsoft/Shared/Windows Forwarding Headers
- [Updated] /Parsers/System/Microsoft/Shared/Windows Text Transforms - Security
- [Updated] /Parsers/System/Microsoft/Windows-Syslog Snare
February 24, 2023 - Content Release
This release includes small modifications to First Seen rule type baseline and retention periods, and switches rule status from Prototype state, allowing more of these rules to contribute to Cloud SIEM Insights. The Microsoft Office 365 Audit parser now formulates key value pairs from the 'OperationProperties' array included in some messages.
Rules
- [Updated] FIRST-S00002 First Seen AWS API Call from User
- [Updated] FIRST-S00023 First Seen AWS API Gateway Enumeration by User
- [Updated] FIRST-S00024 First Seen AWS SSM RunShellScript SendCommand From User
- [Updated] FIRST-S00003 First Seen AWS Secrets Manager API Call from User
- [Updated] FIRST-S00001 First Seen Administrative Privileges Granted for User
- [Updated] FIRST-S00026 First Seen Anonymous Logon Change Activity to Domain Controller
- [Updated] FIRST-S00019 First Seen Azure Member Addition to Group from User
- [Updated] FIRST-S00020 First Seen Azure OAUTH Application Consent from User
- [Updated] FIRST-S00021 First Seen Azure Virtual Machine Run Command Issued by User
- [Updated] FIRST-S00028 First Seen Common Windows Recon Commands From User
- [Updated] FIRST-S00013 First Seen Driver Load - Global
- [Updated] FIRST-S00014 First Seen Driver Load - Host
- [Updated] FIRST-S00007 First Seen DynamoDB Enumeration from User
- [Updated] FIRST-S00027 First Seen InstallUtil Allow List Bypass From User
- [Updated] FIRST-S00017 First Seen Kerberoasting Attempt from User - Global
- [Updated] FIRST-S00018 First Seen Kerberoasting Attempt from User - Host
- [Updated] FIRST-S00004 First Seen Local Group Addition by User
- [Updated] FIRST-S00015 First Seen Macro Execution from User
- [Updated] FIRST-S00016 First Seen Non-Network Logon from User
- [Updated] FIRST-S00010 First Seen PowerShell Execution from Computer
- [Updated] FIRST-S00009 First Seen RDP Logon From User
- [Updated] FIRST-S00025 First Seen SMB Allowed Traffic From IP
- [Updated] FIRST-S00029 First Seen Successful Authentication From Unexpected Country
- [Updated] FIRST-S00011 First Seen Sysmon IMPHASH - Global
- [Updated] FIRST-S00012 First Seen Sysmon IMPHASH - Host
Parsers
- [Updated] /Parsers/System/Microsoft/Office 365
February 22, 2023 - Content Release
Rules
- [New] FIRST-S00001 First Seen Administrative Privileges Granted for User
- [New] FIRST-S00003 First Seen AWS Secrets Manager API Call from User
- [New] FIRST-S00004 First Seen Local Group Addition by User
- [New] FIRST-S00005 First Seen User Creation From User
- [New] FIRST-S00006 First Seen Weak Kerberos Encryption from User
- [New] FIRST-S00007 First Seen DynamoDB Enumeration from User
- [New] FIRST-S00008 First Seen whoami command From User
- [New] FIRST-S00009 First Seen RDP From User
- [New] FIRST-S00010 First Seen PowerShell Execution from Computer
- [New] FIRST-S00011 First Seen Sysmon IMPHASH - Global
- [New] FIRST-S00012 First Seen Sysmon IMPHASH - Host
- [New] FIRST-S00013 First Seen Driver Load - Global
- [New] FIRST-S00014 First Seen Driver Load - Host
- [New] FIRST-S00015 First Seen Macro Execution from User
- [New] FIRST-S00016 First Seen Non-Network Logon from User
- [New] FIRST-S00017 First Seen Kerberoasting Attempt from User - Global
- [New] FIRST-S00018 First Seen Kerberoasting Attempt from User - Host
- [New] FIRST-S00019 First Seen Azure Member Addition to Group from User
- [New] FIRST-S00020 First Seen Azure OAUTH Application Consent from User
- [New] FIRST-S00021 First Seen Azure Virtual Machine Run Command Issued by User
- [New] FIRST-S00022 First Seen S3 Bucket ACL Enumeration by User
- [New] FIRST-S00023 First Seen AWS API Gateway Enumeration By User
- [New] FIRST-S00024 First Seen AWS SSM RunShellScript SendCommand From User
- [New] FIRST-S00025 First Seen SMB Allowed Traffic From IP
- [New] FIRST-S00026 First Seen Anonymous Logon Change Activity to Domain Controller
- [New] FIRST-S00027 First Seen InstallUtil Allow List Bypass From User
- [New] FIRST-S00028 First Seen Common Windows Recon Commands From User
- [Updated] MATCH-S00534 MacOS - Re-Opened Applications
Log Mappers
- [New] CloudTrail - ecs.amazonaws.com - AwsApiCall-ExecuteCommand
February 22, 2023 Application Update
First Seen Rules
Sumo Logic is pleased to announce new features in Cloud SIEM that deliver enhanced User and Entity Behavioral Analytics (UEBA) capabilities. These new UEBA capabilities enable additional methods to detect and investigate anomalous or unexpected behavior that may signify a security threat.
The first feature is called a First Seen Rule. With this new rule type, Cloud SIEM can detect events such as “the first time a user logs in from a new location” without having to define a rule expression that is unique to each user in your environment (and the location(s) from which he/she usually logs in). Other examples include detecting the unusual granting of administrative privileges, Windows recon command, AWS Secrets Manager API calls, API gateway enumeration, and more.
First Seen Rules are defined like any other rule type, through the Content menu in Cloud SIEM.
First Seen Rules operate based on a baseline. During this period of time - typically between 7 and 30 days - the system will learn what normal and expected behavior looks like. After the baseline is established, Cloud SIEM will begin generating Signals when unusual behavior is detected compared to that baseline. Baselines can be per-entity or global. (Note that the longer the baseline, the more accurate the model will be.)
Cloud SIEM will include a set of more than twenty First Seen Rules out of the box. These rules can be tuned and customized like any other rule type, and custom First Seen Rules can also be created.
For more information about how to use First Seen Rules, see the online documentation. You can also see an introduction to the feature by navigating to a new First Seen Rule in the Cloud SIEM UI.
Entity Timeline
Another new feature that will help analysts investigate unusual activity with user accounts is the Entity Timeline:
This feature visualizes all activity for a user – including all normalized records – in an easy-to-read timeline, eliminating the need to perform manual record searches.
Related actions are grouped together and Signals and Insights generated on that user are also displayed in the timeline with the relevant record(s). Actions can be clicked on to see a more detailed set of information, and full details can be easily opened in a new tab.
The feature can be found on the new Timeline tab on each Username Entity’s Detail page with quick links from Signal and Insight detail pages (located with the Entity summaries). It is only available for the Username Entity type at this time.
For more information about how to use the Entity Timeline, see the online documentation.
Minor Changes and Enhancements
- [Updated] Entities listed in the Signals index (
sec_signal) now includecriticalityandsuppressedattributes (which reflect the state of those Entities when the Signal was generated). - [New] The Cloud SIEM API now supports searching the Threat Intelligence data by
sourceName. - [Updated] The Threat Intelligence API
GetThreatIntelIndicatorsendpoint now supports data sets of more than 10,000 indicators. - [Updated] The Insights API now supports searching (filtering) by confidence score.
- [Updated] Cloud SIEM now supports up to 1000 inventory-based Entity Groups (the previous limit was 50).
- [Updated] When viewing an Insight, a label is displayed that indicates the source. When an Insight is generated by a Custom Insight, it will now say Custom Insight (Rule) (instead of Rule) and Custom Insight (Signal) (instead of Signal) to reduce confusion with Insights generated by the Insight Algorithm through standard Rules and Signals.
- [New] Entity Groups can now be managed in bulk by uploading CSV files from the Entity Groups list page.
Bug Fixes
- The consolidated Insight ‘board’ view was not displaying properly in some instances.
- An improper error message was displayed when attempting to create a rule with the same name as one that already existed.
- The Insight Updates section on the HUD was displaying incorrectly if there were no recent updates.
- The Insight creation source label was not positioned properly when scrolling an Insight Details page.
- Entity notes could not be deleted.
February 17, 2023 - Content Release
Rules
- [New] MATCH-S00842 Suspicious Azure CLI Keys Access on Linux Host
- [New] MATCH-S00843 Suspicious GCP CLI Keys Access on Linux Host
Note that the following updates do not change detection capabilities and are only updates to descriptions and other metadata.
- [Updated] MATCH-S00308 AWS CloudTrail - OpsWorks Describe Permissions Event
- [Updated] MATCH-S00210 AWS CloudTrail - SQS List Queues Event
- [Updated] MATCH-S00238 AWS CloudTrail - sensitive activity in KMS
- [Updated] MATCH-S00594 Alibaba ActionTrail KMS Activity
- [Updated] MATCH-S00417 Attrib.exe use to Hide Files and Folders
- [Updated] MATCH-S00786 Azure - SQL Database Export
- [Updated] MATCH-S00304 External Device Installation Denied
- [Updated] FIRST-S00022 First Seen S3 Bucket ACL Enumeration by User
- [Updated] MATCH-S00614 GCP Audit KMS Activity
- [Updated] MATCH-S00466 MsiExec Web Install
- [Updated] MATCH-S00288 NotPetya Ransomware Activity
- [Updated] MATCH-S00634 Okta Admin App Access Attempt Failed
- [Updated] MATCH-S00633 Okta Admin App Accessed
- [Updated] MATCH-S00756 Outlook Homepage Modification
- [Updated] MATCH-S00465 PXELoot Utility
- [Updated] MATCH-S00200 Potential Pass the Hash Activity
- [Updated] MATCH-S00546 Potential Reconnaissance Obfuscation
- [Updated] MATCH-S00265 QuarksPwDump Dump File Observed
- [Updated] MATCH-S00747 Registry Modification - Active Setup
- [Updated] MATCH-S00754 Registry Modification - Microsoft Office Test Function Registry Entry
- [Updated] MATCH-S00422 Spaces Before File Extension
- [Updated] MATCH-S00196 Successful Overpass the Hash Attempt
- [Updated] MATCH-S00293 Suspicious External Device Installation
- [Updated] MATCH-S00342 Suspicious use of Dev-Tools-Launcher
- [Updated] MATCH-S00279 TAIDOOR RAT DLL Load
Log Mappers
- [Deleted] Sysdig Monitor C2C
- [New] CloudTrail - s3.amazonaws.com - GetBucketAcl
- [Updated] CloudTrail - s3.amazonaws.com - CreateBucket
- [Updated] CloudTrail - s3.amazonaws.com - DeleteBucketCors
- [Updated] CloudTrail - s3.amazonaws.com - DeleteBucketLifecycle
- [Updated] CloudTrail - s3.amazonaws.com - DeleteBucketPolicy
- [Updated] CloudTrail - s3.amazonaws.com - PutBucketAcl
- [Updated] CloudTrail - s3.amazonaws.com - PutBucketCors
- [Updated] CloudTrail - s3.amazonaws.com - PutBucketLifecycle
- [Updated] CloudTrail - s3.amazonaws.com - PutBucketPolicy
- [Updated] CloudTrail - s3.amazonaws.com - PutBucketReplication
- [Updated] Fortinet App Control Logs
- [Updated] Fortinet DLP Logs
- [Updated] Fortinet DNS Logs
- [Updated] Fortinet Event Logs
- [Updated] Fortinet IPS Logs
- [Updated] Fortinet Traffic Logs
- [Updated] Fortinet VOIP Logs
- [Updated] Fortinet Virus Logs
- [Updated] Fortinet Webfilter Logs
Parsers
- [Deleted] /Parsers/System/Sysdig/Sysdig Monitor C2C
- [Updated] /Parsers/System/Fortinet/Fortigate/Fortigate-Syslog
- [Updated] /Parsers/System/Pulse Secure/Pulse Secure Appliance
February 13, 2023 - Application Update
Active Entities Panel
To assist analysts detect potential security issues as early as possible, a new panel has been added to the Heads Up Display (HUD):
This panel lists the top five most active entities, ranked by Signal Severity Total. This metric, which was introduced with the Related Entities enhancement last year, is the total sum of the severities of all unique Signals the Entity appears in during the current Insight detection window (typically, the past 14 days).
The count of Active Signals (Signals within the detection window that have not been included in an Insight) is also listed.
When hovering over the Entity value, the Entity’s type will be displayed. The Entity value is a link to that Entity’s details page.
Analysts can use this tool to investigate what appears to be risky activity and potentially proactively security issues before they are raised to the level of an Insight.
Minor Changes and Enhancements
- [New] When looking at Signals in the new
sec_signalindex, attributes and values in array fields are now properly supported by auto-parsing, syntax likecount by, and features like right-click > filter selected value*. - [New] An attribute
attackStagehas been added to the newsec_signalindex. This attribute summarizes the Mitre attack stage represented by the rule which triggered the signal. The value is defined the same way as theattack_stageattribute included in the older Signal forwarding feature. - [Updated] The
subResolutionattribute is now included in the Insight payload for http v2 actions. - [Updated] The way Release Notes are listed in the Cloud SIEM UI is changing. There is no longer a “bell” item on the top menu; it has been replaced with a link to the Release Notes page in the Help menu. In addition, Release Notes are now directly visible in the UI when they are published.
- [New] When executing a context action on a Signal, fields will now be passed to the context action if they are available based on the record(s) in context.
Bug Fixes
- The “Radar” graph of records, Signals and Insights on the HUD has been updated so that the discontinuity at the top of the Signals section of the graph has been removed.
- When viewing the raw log message corresponding to a normalized record, the wrong message was displayed.
- The Network Block(s) associated with an Entity were not listed on the Entity details page.
- When testing Rule expressions, sometimes the selected Tuning expression was not included.
- Changes to entity tags or Criticality were not being listed on the History section of the Entity.
- Entity Criticality was sometimes not displaying properly on the Insight details page.
February 8, 2023 - Content Release
Rules
- [New] MATCH-S00838 Azure Active Directory Authentication Method Changed
- [New] MATCH-S00836 Azure Conditional Access Policy Disabled
- [New] MATCH-S00839 Azure Virtual Machine RunCommand Issued
- [New] MATCH-S00837 Kubernetes Secrets Enumeration via Kubectl
- [New] MATCH-S00835 Possible Dynamic URL Domain
- [New] CHAIN-S00012 Potential Azure Persistence via Automation Accounts
- [New] MATCH-S00841 Suspicious AWS CLI Keys Access on Linux Host
- [New] MATCH-S00840 Suspicious Lambda Function - IAM Policy Attached
- [Updated] THRESHOLD-S00074 Excessive Firewall Denies
- [Updated] LEGACY-S00008 Possible Dynamic DNS Domain
- [Updated] LEGACY-S00108 Threat Intel - Matched File Hash
Log Mappers
- [New] Airtable Audit C2C
- [New] Cisco Meraki Catch All - Custom Parser
- [Updated] Linux OS Syslog - Process fw - iptables Events
- [Updated] Proofpoint Targeted Attack Protection C2C - Message Blocked
- [Updated] Proofpoint Targeted Attack Protection C2C - Message Delivered
- [Updated] Proofpoint Targeted Attack Protection C2C - Message Permitted
- [Updated] Windows - Security - 4624
Parsers
- [New] /Parsers/System/Airtable/Airtable Audit C2C
- [Updated] /Parsers/System/Cisco/Cisco ASA
- [Updated] /Parsers/System/Cisco/Cisco Meraki
- [Updated] /Parsers/System/Google/G Suite Audit
- [Updated] /Parsers/System/Linux/Linux OS Syslog
- [Updated] /Parsers/System/Linux/Shared/Linux Shared Syslog Headers
- [Updated] /Parsers/System/Okta/Okta
January 20, 2023 - Content Release
Rules
- [New] THRESHOLD-S00111 Sharepoint - Excessive Documents Accessed by External IP
- [New] THRESHOLD-S00110 Sharepoint - External IP Downloaded Excessive Documents
- [Updated] THRESHOLD-S00101 Sharepoint - Excessive Documents Accessed by User
January 19, 2023 Application Update
Minor Changes and Enhancements
- [Updated] On the HUD, the Insight Activity widget has been updated. When selecting the Insight to display, the HUD will now choose based on this order of preference: In “New”, Unassigned, Highest GIS Confidence Score, Highest Severity, Newest. In addition, the design has been updated to improve readability.
- [New] Users who wish to substitute custom Insight status(es) for the built-in “In Progress” status can now do so. After creating and organizing the custom statu(es), the user can now disable the “In Progress” status. (It cannot be deleted.) Note that it can be disabled only if there are no Insights currently set to “In Progress.”
- Changes to Entity tags and criticality now appear in the Entity’s change history list.
- The Sumo Terraform provider now includes support for custom columns in match lists.
- Kubernetes (k8s) attribute fields are now normalized to include the namespace. The normalized fields are:
normalizedPodName,normalizedDeploymentName, andnormalizedReplicaSetName.
Resolved Issues
- Some Insights could not be closed via the UI (though they could via API).
- In the consolidated (parent/child) Insight view, in “Board” mode, scrolling was not working properly. In addition, links to other orgs had an error in the URL (a duplicate “/sec”).
January 13, 2023 - Content Release
Rules
- [New] MATCH-S00825 AWS Secrets Manager Enumeration
- [New] MATCH-S00827 Exposed AWS SNS Topic Created
- [New] MATCH-S00823 Exposed AWS SQS Queue Created
- [New] MATCH-S00828 Office 365 Exchange Transport Rule Created
- [New] MATCH-S00829 Office 365 Exchange Transport Rule Enabled
- [New] MATCH-S00830 Office 365 Forwarding Rule Created
- [New] MATCH-S00833 Office 365 Inbox Rule Created
- [New] MATCH-S00832 Office 365 Inbox Rule Updated
- [New] MATCH-S00831 Office 365 Unified Audit Logging Disabled
- [New] MATCH-S00824 Potential XMRig Execution with Traffic
- [New] MATCH-S00826 SSH Keys Added to EC2 Instance
- [New] MATCH-S00834 Sensitive Registry Key (WDigest) Edit
- [Updated] MATCH-S00480 Solarwinds Suspicious Child Processes
- [Updated] MATCH-S00504 User Added to Local Administrators
Log Mappers
- [New] Windows - Microsoft-Windows-Sysmon/Operational - 22
- [New] Windows - Microsoft-Windows-Sysmon/Operational - 23
- [New] Windows - Microsoft-Windows-Sysmon/Operational - 24
- [New] Windows - Microsoft-Windows-Sysmon/Operational - 25
- [New] Windows - Microsoft-Windows-Sysmon/Operational - 26
- [New] Windows - Microsoft-Windows-Sysmon/Operational - 27
- [New] Windows - Microsoft-Windows-Sysmon/Operational - 28
- [Updated] Cloudflare - Logpush
- [Updated] Microsoft Office 365 AzureActiveDirectory Events
- [Updated] Microsoft Office 365 Exchange Mailbox Audit Events
- [Updated] Microsoft Office 365 Exchange Mailbox Authentication Events
- [Updated] Microsoft Office 365 ExchangeItem Events
- [Updated] Microsoft Office 365 ExchangeItemGroup Events
- [Updated] Microsoft Office 365 RecordType 105
- [Updated] Microsoft Office 365 RecordType 37
- [Updated] Microsoft Office 365 RecordType 57
- [Updated] Office 365 - Exchange Admin Events
Parsers
- [New] /Parsers/System/Microsoft/Windows-Syslog WinCollect
Schema
- [Updated] device_k8s_normalizedDeploymentName
- [Updated] device_k8s_normalizedPodName
- [Updated] device_k8s_normalizedReplicaSetName
- [Updated] dstDevice_k8s_normalizedDeploymentName
- [Updated] dstDevice_k8s_normalizedPodName
- [Updated] dstDevice_k8s_normalizedReplicaSetName
- [Updated] srcDevice_k8s_normalizedDeploymentName
- [Updated] srcDevice_k8s_normalizedPodName
- [Updated] srcDevice_k8s_normalizedReplicaSetName
January 5, 2023 - Content Release
Rules
- [Updated] MATCH-S00556 Outbound Data Transfer Protocol Over Non-standard Port
Log Mappers
- [New] Google G Suite - login-email_forwarding_change
- [New] Laurel Linux Audit - Catch All
- [New] Laurel Linux Audit - System Call
- [New] Laurel Linux Audit - User Logon
- [Updated] Lacework Alert
Parsers
- [New] /Parsers/System/AWS/AWS Security Hub
- [New] /Parsers/System/Laurel/Laurel Linux Audit
- [New] /Parsers/System/Signal Science/Signal Science WAF
- [New] /Parsers/System/Workday/Workday
Schema
- [Updated] device_k8s_deployment
- [Updated] device_k8s_pod
- [Updated] device_k8s_replicaSet
- [Updated] dstDevice_k8s_deployment
- [Updated] dstDevice_k8s_pod
- [Updated] dstDevice_k8s_replicaSet
- [Updated] srcDevice_k8s_deployment
- [Updated] srcDevice_k8s_pod
- [Updated] srcDevice_k8s_replicaSet