Sumo Logic Connector for AWS PrivateLink (Beta)
Sumo Logic provides the ability to configure private connectivity between your AWS Infrastructure and Sumologic via AWS PrivateLink. This prevents any traffic from being accessible to the public internet.
Following sources are supported for AWS PrivateLink:
- Installed Collector sources. Data collected on Installed collectors deployed on customer VPC and sent to the Sumo Logic.
- HTTPs sources. Data sent by the applications hosted in customers VPC and sent over to Sumologic using HTTP Logs and Metrics Source and Kinesis Firehose Source for Logs and Metrics.
The following sources are not supported for AWS PrivateLink:
- Cloud Syslog
- AWS S3
- AWS Cloudwatch source
- Sumo Logic OpenTelemtry Distro
- OTLP sources
- RUM sources
Enable PrivateLink for ALB
To send data to Sumo Logic through AWS PrivateLink, you'll need to configure an internal endpoint in your VPC for Installed Collectors to send data to.
With the NLB-created and ALB-registered as a target, requests over AWS PrivateLink to the NLB are forwarded to the ALB.
Sumo Logic exposes AWS PrivateLink endpoints to different regions that depend on your Sumo Logic deployment. If you're using the VPC in a different region where the Sumo Logic PrivateLink endpoint service is set up, you need to set up VPC peering. Either way, you need to create an endpoint.
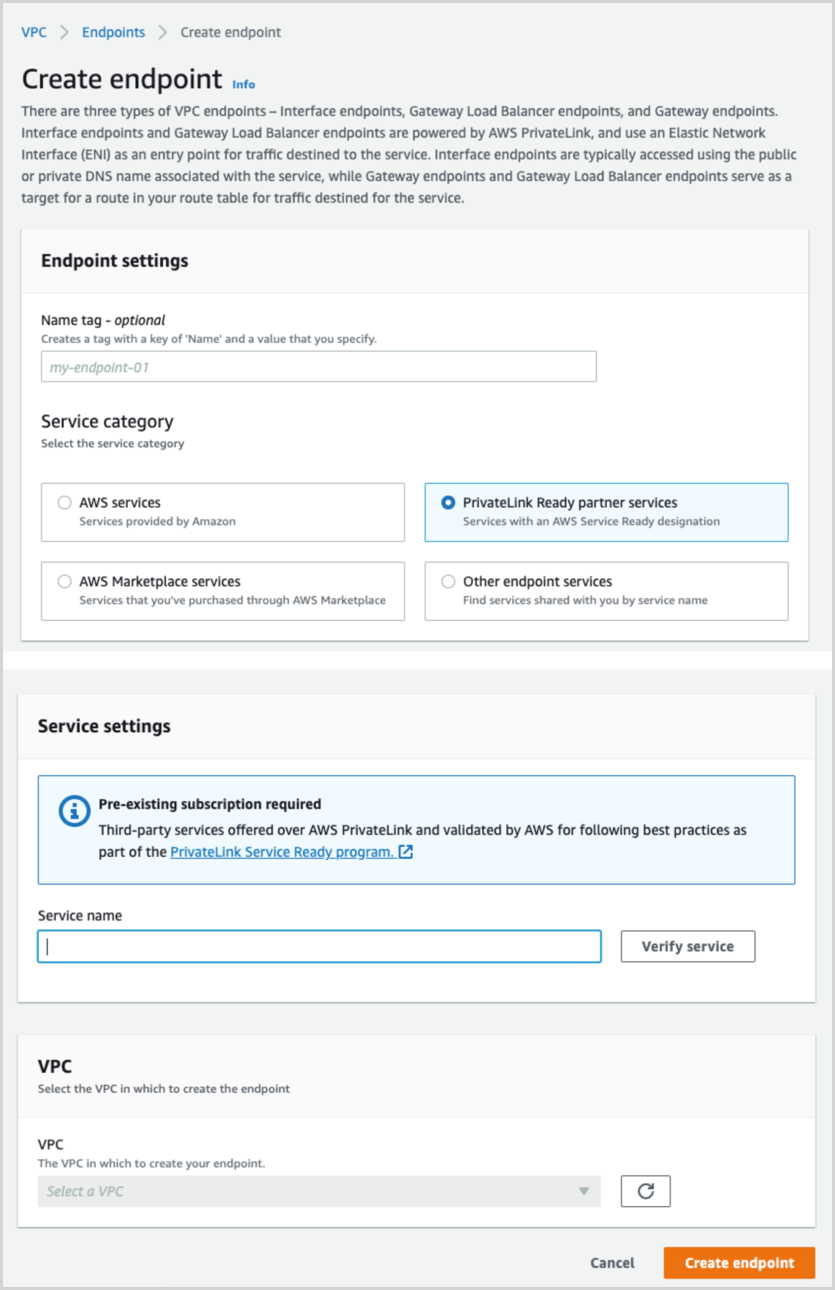
Create an endpoint to connect with the Sumo Logic endpoint service
-
The service name is provided by Sumo Logic and will accept the endpoint connection request once we know you initiated the connection.
-
Select the VPC where the Sumo Logic collector will be installed or where HTTP requests will be made for HTTP Sources.
No VPC Peering
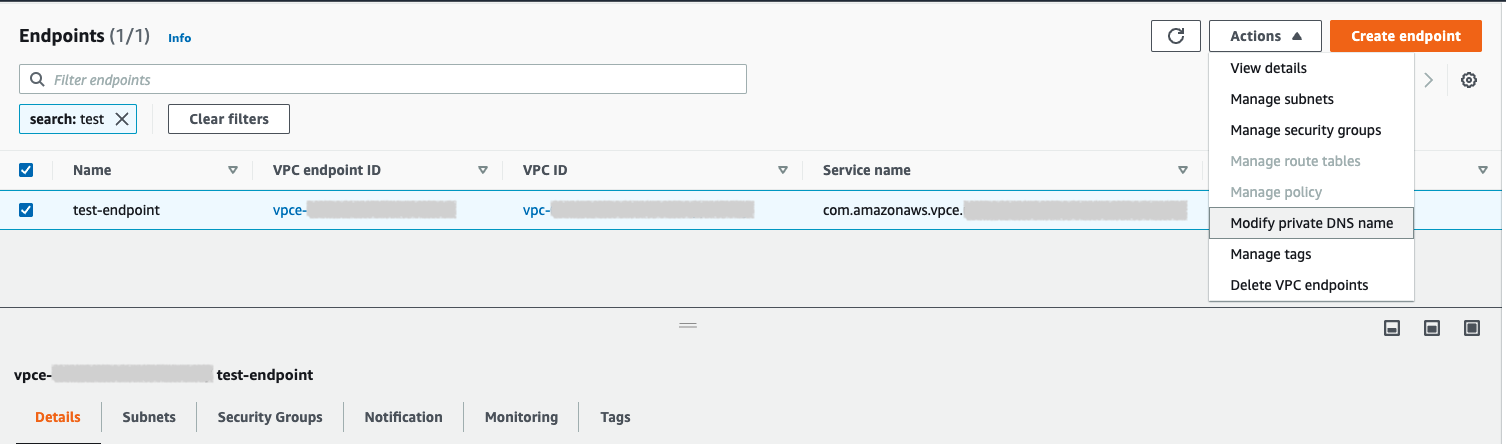
If the VPC is in the same AWS region as your deployment, you do not need to set up VPC peering. Navigate to Actions, then select Modify private DNS name.
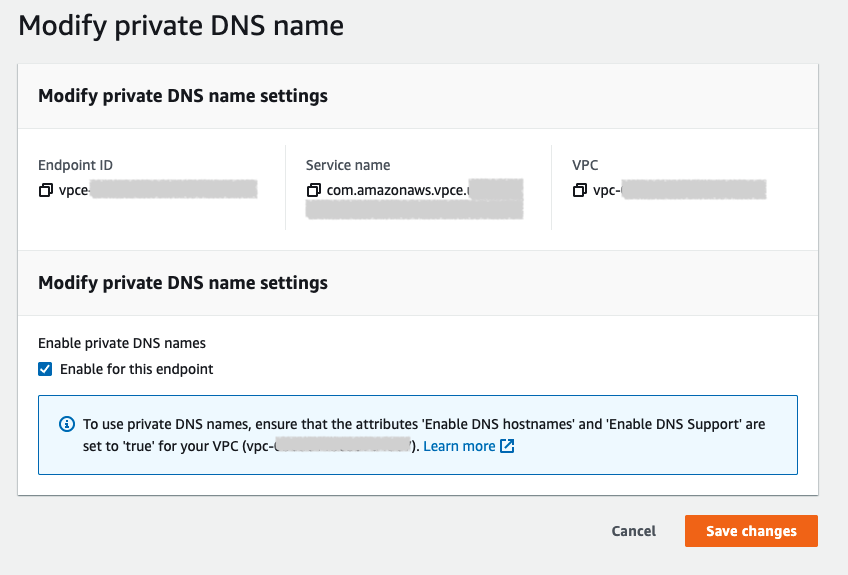
Check the box to enable private DNS names.
VPC Peering
If the VPC is not in the same AWS region as your deployment, you'll need to set up VPC peering.
- Create the VPC peering connection between the region for the client-side VPC and the region where the Sumo Logic PrivateLink service is configured.
- Create a Route53 private hosted zone. Select the VPC peered in the region where our server-side region is located.
- With the created private hosted zone, add an A record. Select the peered VPC in region us-west-2, where the Sumo Logic server-side infrastructure is located.
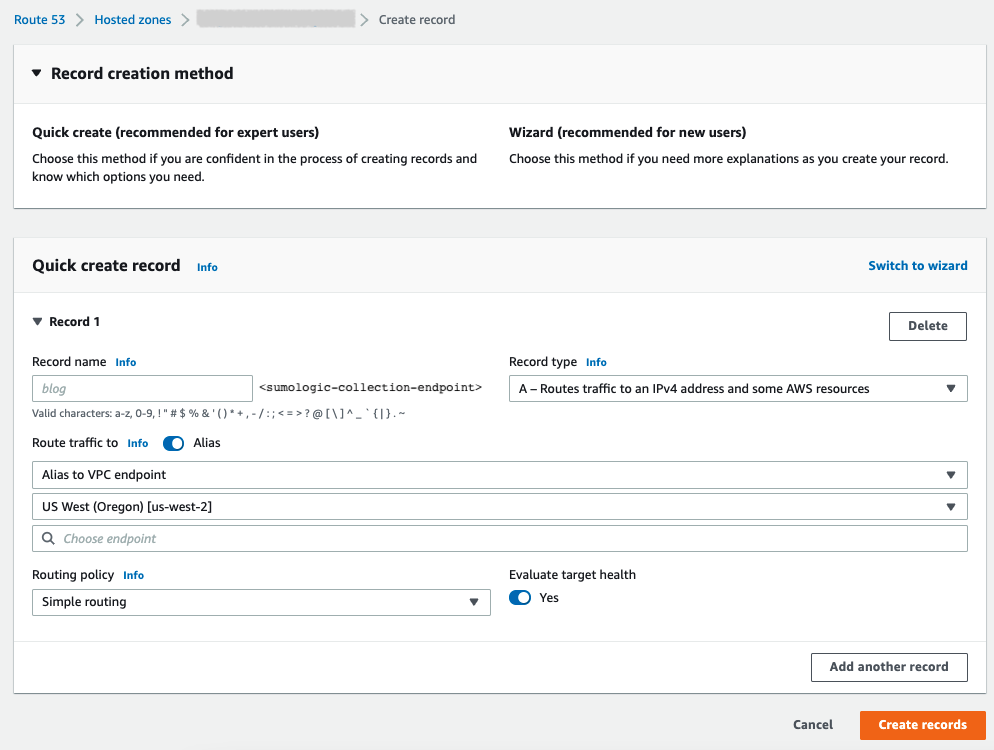
- Add the other peered VPC in the other region into the Route53-hosted zone.