Collect Logs for SentinelOne
This section provides instructions for ingesting SentinelOne logs into Sumo Logic. For more information, on SentinelOne please visit the SentinelOne website.
If you have a SentinelOne account, you can view the contents of this article in the SentinelOne Support knowledge base here.
Although you can use this method for ingesting SentinelOne logs into Sumo Logic, the preferred method is to use the SentinelOne Mgmt API Source.
Step 1. Get a token and certificate from Sumo Logic
You can define a SIEM token to add in the message ID of CEFv2 Syslog messages.
The procedure assumes you have wget installed.
To get a token and certificate from Sumo Logic, do the following:
-
Log in to the Sumo Logic web site.
-
Configure a Cloud Syslog Hosted Collector and Cloud Syslog Source, and generate a Cloud Syslog source token.
-
Download the crt server certificate file from here.
-
Go to the location where the cert file is located and open a terminal window.
-
Run the following two commands:
wget -O digicert_ca.der https://cacerts.digicert.com/DigiCertHighAssuranceEVRootCA.crt.openssl x509 -inform der -in digicert_ca.der -out digicert_ca.crt
Step 2. Configure syslog messages
In this step, you configure syslog messages from the Management Console.
To configure syslog messages, do the following:
-
In the SentinelOne sidebar, click Scope, and then select a scope.
noteIf you are a Site or Account admin, you must select one Site to be able to open Settings.
-
In the sidebar, click Settings.
-
In the Settings toolbar, click Integrations.

-
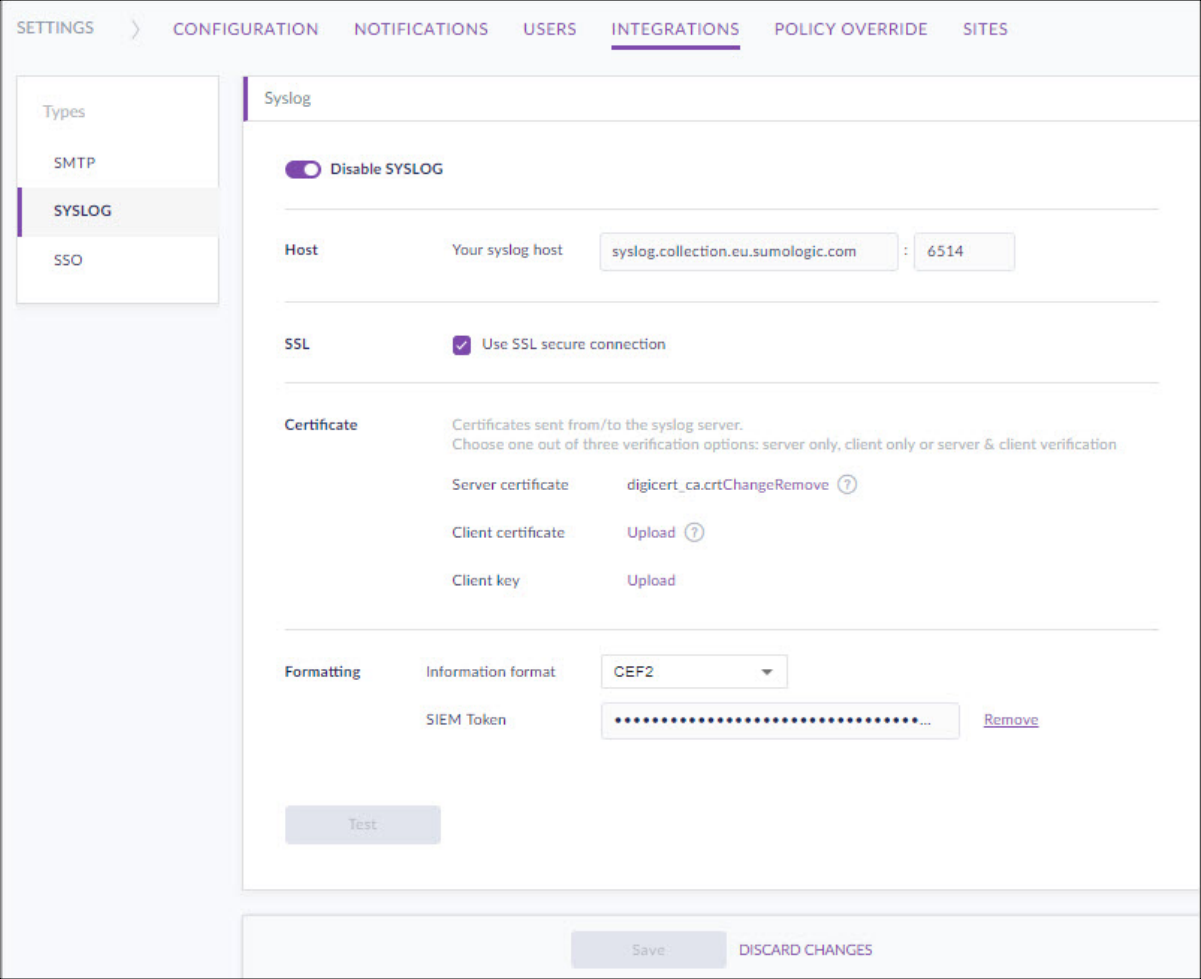
Click SYSLOG. The SYSLOG dialog appears.
-
Click the toggle to Enable SYSLOG.
-
Enter the Syslog Host URL and port number.
-
Click Use SSL secure connection, then click Server certificate > Upload and browse to the location of the downloaded crt certificate file.
-
Specify the following Formatting options:
- Information format: Select CEF2
- SIEM Token: Paste the Cloud Syslog Source Token generated from Sumo Logic.
-
Click Test, and then click Save.
-
In Sumo Logic, verify that the logs are being ingested by running a search against the Cloud Syslog source you configured in Step 1. If you do not see any data coming in after 2-3 minutes, check the following:
- that the Sumo Logic Collector has read access to the logs
- that your time zone is configured correctly.