1Password Source
The 1Password Source provides a secure endpoint to receive sign-in attempts, item usage, and audit events from the 1Password Event API. It securely stores the required authentication, scheduling, and state tracking information.
Data collected
| Polling Interval | Data |
|---|---|
| 5 min | Sign-in attempts |
| 5 min | Item usage |
| 5 min | Audit events |
Setup
Vendor configuration
You'll need a 1Password API token and your customer-specific 1Password domain (for example, events.1password.com). To generate a 1Password API token, follow these steps:
- Sign in to your 1Password account and click Integrations in the sidebar.
- Switch to the Directory tab (or use this direct link to the Directory tab).
- Go to the Events Reporting section and click the Sumo Logic integration.
- In the System Name field, enter the name of your choice (default value
Sumo Logicshould be fine in most cases), then click Add Integration. - In the Set up token section:
- Enter a Token Name. This can be any string that will help you recognize tokens generated for different environments like production, staging, and dev.
- Under Events to Report, leave enabled event sources which you want to share using the token.
- When you're done, click Issue Token.
- In the Save token section, click the copy icon (next to the token string) to copy it to your clipboard. You can also click Save in 1Password to store it for your future reference.
- Lastly, click View Integration Details to see the summary, then click Learn More pointing to 1Password App installation manual.
Source configuration
- In the main Sumo Logic menu, select Manage Data > Collection > Collection.
- On the Collectors page, click Add Source next to a Hosted Collector.
- Search for and select 1Password.
- Enter a Name for the Source. The description is optional.
- (Optional) For Source Category, enter any string to tag the output collected from the Source. Category metadata is stored in a searchable field called
_sourceCategory. - Forward to SIEM. Check the checkbox to forward your data to Cloud SIEM. note
Select Forward to SIEM only if you have Cloud SIEM installed.
- (Optional) Fields. Click the +Add link to add custom log metadata Fields.
- Define the fields you want to associate, each field needs a name (key) and value.
A green circle with a check mark is shown when the field exists and is enabled in the Fields table schema.
An orange triangle with an exclamation point is shown when the field doesn't exist, or is disabled, in the Fields table schema. In this case, an option to automatically add or enable the nonexistent fields to the Fields table schema is provided. If a field is sent to Sumo that does not exist in the Fields schema or is disabled it is ignored, known as dropped.
- Define the fields you want to associate, each field needs a name (key) and value.
- Base URL. Provide your 1Password customer-specific domain, for example
events.1password.com. - API Token. Enter the 1Password API token.
- Supported APIs to collect. Select one or more of the available APIs, Item Usage and Sign-in Attempts.
- Processing Rules. Configure any desired filters, such as allowlist, denylist, hash, or mask, as described in Create a Processing Rule.
- When you are finished configuring the Source, click Submit.
Metadata fields
| Field | Value | Description |
|---|---|---|
_siemVendor | 1Password | Set when Forward To SIEM is checked. |
_siemProduct | 1Password | Set when Forward To SIEM is checked. |
_siemFormat | JSON | Set when Forward To SIEM is checked. |
_siemParser | /Parsers/System/1Password/1Password | Set when Forward To SIEM is checked. |
JSON schema
Sources can be configured using UTF-8 encoded JSON files with the Collector Management API. See how to use JSON to configure Sources for more details.
| Parameter | Type | Value | Required | Description |
|---|---|---|---|---|
| schemaRef | JSON Object | {"type":"1Password"} | Yes | Define the specific schema type. |
| sourceType | String | "Universal" | Yes | Type of source. |
| config | JSON Object | Configuration object | Yes | Source type specific values. |
Configuration Object
| Parameter | Type | Required | Default | Description | Example |
|---|---|---|---|---|---|
| name | String | Yes | null | Type a desired name of the source. The name must be unique per Collector. This value is assigned to the metadata field _source. | "mySource" |
| description | String | No | null | Type a description of the source. | "Testing source" |
| category | String | No | null | Type a category of the source. This value is assigned to the metadata field _sourceCategory. See best practices for details. | "mySource/test" |
| fields | JSON Object | No | null | JSON map of key-value fields (metadata) to apply to the Collector or Source. Use the boolean field _siemForward to enable forwarding to SIEM. | {"_siemForward": false, "fieldA": "valueA"} |
| base_url | String | Yes | null | Provide your 1Password customer-specific domain, such as, events.1password.com | "events.1password.com" |
| api_token | String | Yes | null | Provide the 1Password API token you want to use to authenticate collection requests. | "acsac25$" |
| supported_apis | []String | Yes | null | Define one or more of the available APIs to collect | ["sign-in","itemUsage"] |
JSON example
{
"api.version": "v1",
"source": {
"schemaRef": {
"type": "1Password"
},
"config": {
"name": "1Pass",
"base_url": "events.1password.com",
"supported_apis": [
"itemUsage",
"sign-in"
],
"api_token": "********",
"fields": {
"_siemForward": true
}
},
"sourceType": "Universal"
}
}
Terraform example
resource "sumologic_cloud_to_cloud_source" "1password_source" {
collector_id = sumologic_collector.collector.id
schema_ref = {
type = "1Password"
}
config = jsonencode({
"name" : "1Pass",
"base_url" : "events.1password.com",
"supported_apis" : [
"itemUsage",
"sign-in"
],
"api_token" : "********",
"fields" : {
"_siemForward" : true
}
})
}
resource "sumologic_collector" "collector" {
name = "my-collector"
description = "Just testing this"
}
Troubleshooting
After configuring your Source, you should check the status of the source in the Collectors page > Status column. If the Source is not functioning as expected, you may see an error next to the Source Category column as shown below:
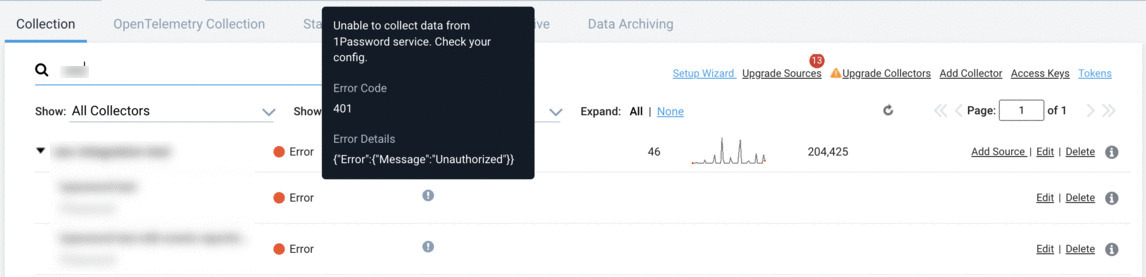
To resolve these errors:
- Make sure the Base URL matches your domain.
- Make sure correct API Token is used to configure the source.
- If you're still seeing the
401 Unauthorized errorin the Status column, regenerate the API Token by following these configuration steps and then updating the API Token for the source.
FAQ
Click here for more information about Cloud-to-Cloud sources.